How to view computer operation records?
How to check computer operation records: 1. Check what folders and files you have opened recently, use "win R" to pop up the "Run" window, enter "recent"; 2. Check what has been run Program, find the "C:\windows\Prefetch" directory, which contains the history of your running programs.

Have you ever encountered this situation when you usually use your computer? That is, when you want to find a certain historical file or touch a historical operation, you cannot I started, but I don’t know how to check my past operations. Today, Xiansen, pretending to be confused, will share with you some questions about historical computer operations. This article will involve searching, deleting, and restoring historical operation records, access records, etc. Content, I hope it will be helpful to you
View operation records
1. Check the first running time of the computer
If your system is installed on the c drive, find the c:\windows\SchedLgU.txt file which contains the time you have worked since the system was created, including the day it was turned on, the time it was turned on, and the time it was turned off! (This method is applicable to wein7)
win R pops up the Windows 10 run window, enter the command cmd in the window, and then click the OK button. Enter "systeminfo" in the command input box that opens, and then we can see the system installation time and startup time. Of course, this method can also check some basic information about the computer, including product ID, memory usage, patches, etc. (This method is suitable for wein10)
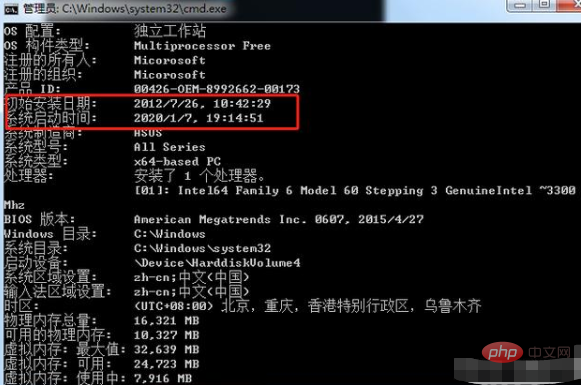
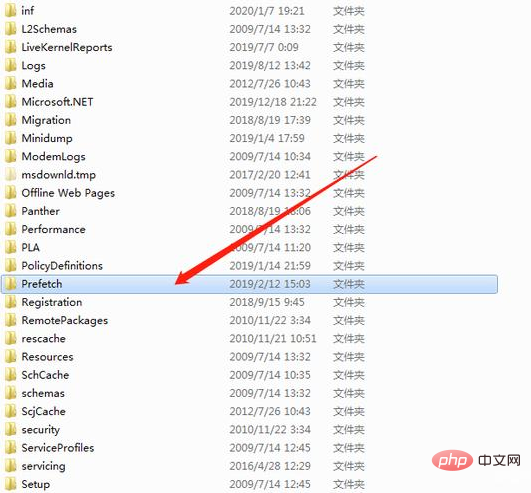
2 .Check what programs you have run
Find the C:\windows\Prefetch directory. What is recorded in it is the history of your running programs. The first part of the file is the name of the program you ran. The premise is that you Not optimized using Security Guard. If optimized, there will be no program running history.
3. Check what folders and files you have opened recently
win R pops up the run window, enter recent
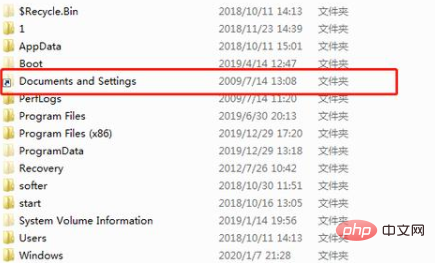
4. Check your Internet access records
First turn on the Show all files option, and then open C:\Documents and Settings\xukunping\ Local Settings directory, in which you can see all your network operation records, including downloaded videos, pictures, files, etc. If you have performed disk cleanup or related optimization, there will be no records.

How to delete records
##Clear running records:
Enter regedit in the start search bar, press Enter to enter the registry editor, and then navigate to HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU You can delete the right All values other than "(default)" can also be deleted selectivelyClear recently used project records:
Enter "%APPDATA" in the address bar of the disk %\Microsoft\Windows\Recent\AutomaticDestinations" and press Enter to open the directory, and then delete all the files in the directory.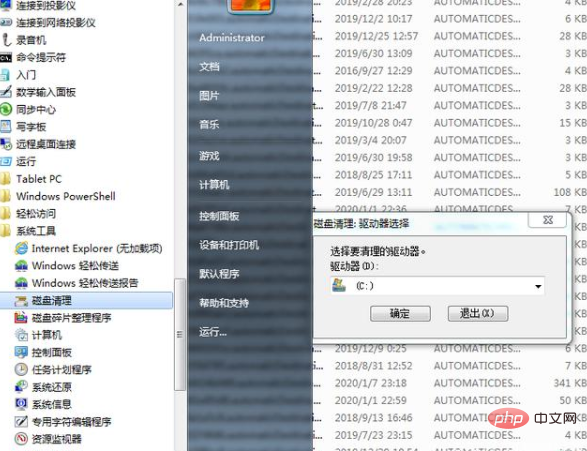

The above is the detailed content of How to view computer operation records?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1393
1393
 52
52
 1209
1209
 24
24
 What is the reason why PS keeps showing loading?
Apr 06, 2025 pm 06:39 PM
What is the reason why PS keeps showing loading?
Apr 06, 2025 pm 06:39 PM
PS "Loading" problems are caused by resource access or processing problems: hard disk reading speed is slow or bad: Use CrystalDiskInfo to check the hard disk health and replace the problematic hard disk. Insufficient memory: Upgrade memory to meet PS's needs for high-resolution images and complex layer processing. Graphics card drivers are outdated or corrupted: Update the drivers to optimize communication between the PS and the graphics card. File paths are too long or file names have special characters: use short paths and avoid special characters. PS's own problem: Reinstall or repair the PS installer.
 How to solve the problem of loading when PS is always showing that it is loading?
Apr 06, 2025 pm 06:30 PM
How to solve the problem of loading when PS is always showing that it is loading?
Apr 06, 2025 pm 06:30 PM
PS card is "Loading"? Solutions include: checking the computer configuration (memory, hard disk, processor), cleaning hard disk fragmentation, updating the graphics card driver, adjusting PS settings, reinstalling PS, and developing good programming habits.
 How to speed up the loading speed of PS?
Apr 06, 2025 pm 06:27 PM
How to speed up the loading speed of PS?
Apr 06, 2025 pm 06:27 PM
Solving the problem of slow Photoshop startup requires a multi-pronged approach, including: upgrading hardware (memory, solid-state drive, CPU); uninstalling outdated or incompatible plug-ins; cleaning up system garbage and excessive background programs regularly; closing irrelevant programs with caution; avoiding opening a large number of files during startup.
 Is slow PS loading related to computer configuration?
Apr 06, 2025 pm 06:24 PM
Is slow PS loading related to computer configuration?
Apr 06, 2025 pm 06:24 PM
The reason for slow PS loading is the combined impact of hardware (CPU, memory, hard disk, graphics card) and software (system, background program). Solutions include: upgrading hardware (especially replacing solid-state drives), optimizing software (cleaning up system garbage, updating drivers, checking PS settings), and processing PS files. Regular computer maintenance can also help improve PS running speed.
 How to solve the problem of loading when the PS opens the file?
Apr 06, 2025 pm 06:33 PM
How to solve the problem of loading when the PS opens the file?
Apr 06, 2025 pm 06:33 PM
"Loading" stuttering occurs when opening a file on PS. The reasons may include: too large or corrupted file, insufficient memory, slow hard disk speed, graphics card driver problems, PS version or plug-in conflicts. The solutions are: check file size and integrity, increase memory, upgrade hard disk, update graphics card driver, uninstall or disable suspicious plug-ins, and reinstall PS. This problem can be effectively solved by gradually checking and making good use of PS performance settings and developing good file management habits.
 Is PS slow loading related to other programs that are running?
Apr 06, 2025 pm 06:03 PM
Is PS slow loading related to other programs that are running?
Apr 06, 2025 pm 06:03 PM
The secrets to mastering Office software include: understanding different versions and platforms, correctly installing and configuring, proficient in using the software interface, in-depth understanding of feature operations, application collaboration and sharing functions, utilizing templates and styles, mastering advanced skills, and solving common problems. In addition, you need to choose a version that suits your needs, make good use of templates and styles, develop backup habits, and learn shortcut keys and advanced techniques to improve efficiency.
 How to solve the problem of loading when PS is started?
Apr 06, 2025 pm 06:36 PM
How to solve the problem of loading when PS is started?
Apr 06, 2025 pm 06:36 PM
A PS stuck on "Loading" when booting can be caused by various reasons: Disable corrupt or conflicting plugins. Delete or rename a corrupted configuration file. Close unnecessary programs or upgrade memory to avoid insufficient memory. Upgrade to a solid-state drive to speed up hard drive reading. Reinstalling PS to repair corrupt system files or installation package issues. View error information during the startup process of error log analysis.
 How to use mysql after installation
Apr 08, 2025 am 11:48 AM
How to use mysql after installation
Apr 08, 2025 am 11:48 AM
The article introduces the operation of MySQL database. First, you need to install a MySQL client, such as MySQLWorkbench or command line client. 1. Use the mysql-uroot-p command to connect to the server and log in with the root account password; 2. Use CREATEDATABASE to create a database, and USE select a database; 3. Use CREATETABLE to create a table, define fields and data types; 4. Use INSERTINTO to insert data, query data, update data by UPDATE, and delete data by DELETE. Only by mastering these steps, learning to deal with common problems and optimizing database performance can you use MySQL efficiently.



