 Common Problem
Common Problem
 What aspects of security vulnerabilities include looking at the system as a whole?
What aspects of security vulnerabilities include looking at the system as a whole?
What aspects of security vulnerabilities include looking at the system as a whole?
Looking at the overall system, security vulnerabilities include the following aspects: 1. Human factors; 2. Technical factors; 3. Planning, strategy and execution process. A security vulnerability is an unprotected entry point that inadvertently leaves a restricted computer, component, application, or other online resource.

The operating environment of this tutorial: Windows 7 system, Dell G3 computer.
Looking at the system as a whole, security "vulnerabilities" include human factors, technical factors, planning, strategy and execution processes.
A security vulnerability is an inadvertent unprotected entry point into a restricted computer, component, application or other online resource. Vulnerabilities are flaws in hardware, software, or usage strategies that expose computers to viruses and hacker attacks.
Common security vulnerabilities
Code injection. A broad attack including SQL injection, which depends on code being inserted and executed by the application.
Session fixed. This is a session attack that allows an attacker to hijack a valid user session. Session fixation attacks can modify an established session on the victim's browser, thus allowing malicious attacks to be carried out before the user is logged in.
Path access, or "directory access". This vulnerability is designed to access files or directories stored outside the web root file.
Weak password has few characters, short number length and lack of special symbols. This password is relatively easy to crack.
Hardcoded encryption keys, providing a false sense of security. Some believe that decentralizing hardcoded passwords before storing them can help protect information from malicious users. But much of this dispersion is a reversible process.
Vulnerability characteristics
Vulnerabilities are flaws in the specific implementation of hardware, software, protocols, or system security policies, which allow attackers to gain unauthorized access to access or damage the system. Specific examples include logic errors in Intel Pentium chips, programming errors in early versions of Sendmail, weaknesses in the authentication method in the NFS protocol, and improper configuration problems when Unix system administrators set up anonymous Ftp services. May be used by attackers to threaten system security. Therefore, these can be considered as security vulnerabilities in the system.
The relationship between the vulnerability and the specific system environment and its time-related characteristics
The vulnerability will affect a wide range of software and hardware equipment, including the operating system itself and its supporting software, network clients and Server software, network routers and security firewalls, etc. In other words, different security vulnerabilities may exist in these different software and hardware devices. Different types of software and hardware devices, different versions of the same device, different systems composed of different devices, and the same system under different settings will have different security vulnerabilities.
The vulnerability issue is closely related to time. From the day a system is released, as users use it in-depth, the vulnerabilities in the system will be continuously exposed. These vulnerabilities discovered earlier will also be continuously patched by patch software released by the system supplier, or released in the future. corrected in the new version of the system. While the new version of the system corrects the loopholes in the old version, it will also introduce some new loopholes and errors. Therefore, as time goes by, old vulnerabilities will continue to disappear and new vulnerabilities will continue to appear. Vulnerability problems will also persist for a long time.
Therefore, it is meaningless to discuss vulnerability issues without specific time and specific system environment. Possible vulnerabilities and possible solutions can only be discussed in detail based on the actual environment such as the operating system version of the target system, the software version running on it, and the service running settings.
At the same time, it should be noted that research on vulnerability issues must track the latest developments in the latest computer systems and their security issues. This is similar to the study of the development of computer viruses. If you cannot keep track of new technologies at work, you will have no say in talking about system security vulnerabilities, and even the work you have done before will gradually lose value.
More learning recommendations: Programming video
The above is the detailed content of What aspects of security vulnerabilities include looking at the system as a whole?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 Ten limitations of artificial intelligence
Apr 26, 2024 pm 05:52 PM
Ten limitations of artificial intelligence
Apr 26, 2024 pm 05:52 PM
In the field of technological innovation, artificial intelligence (AI) is one of the most transformative and promising developments of our time. Artificial intelligence has revolutionized many industries, from healthcare and finance to transportation and entertainment, with its ability to analyze large amounts of data, learn from patterns, and make intelligent decisions. However, despite its remarkable progress, AI also faces significant limitations and challenges that prevent it from reaching its full potential. In this article, we will delve into the top ten limitations of artificial intelligence, revealing the limitations faced by developers, researchers, and practitioners in this field. By understanding these challenges, it is possible to navigate the complexities of AI development, reduce risks, and pave the way for responsible and ethical advancement of AI technology. Limited data availability: The development of artificial intelligence depends on data
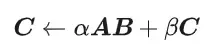 CUDA's universal matrix multiplication: from entry to proficiency!
Mar 25, 2024 pm 12:30 PM
CUDA's universal matrix multiplication: from entry to proficiency!
Mar 25, 2024 pm 12:30 PM
General Matrix Multiplication (GEMM) is a vital part of many applications and algorithms, and is also one of the important indicators for evaluating computer hardware performance. In-depth research and optimization of the implementation of GEMM can help us better understand high-performance computing and the relationship between software and hardware systems. In computer science, effective optimization of GEMM can increase computing speed and save resources, which is crucial to improving the overall performance of a computer system. An in-depth understanding of the working principle and optimization method of GEMM will help us better utilize the potential of modern computing hardware and provide more efficient solutions for various complex computing tasks. By optimizing the performance of GEMM
 Huawei's Qiankun ADS3.0 intelligent driving system will be launched in August and will be launched on Xiangjie S9 for the first time
Jul 30, 2024 pm 02:17 PM
Huawei's Qiankun ADS3.0 intelligent driving system will be launched in August and will be launched on Xiangjie S9 for the first time
Jul 30, 2024 pm 02:17 PM
On July 29, at the roll-off ceremony of AITO Wenjie's 400,000th new car, Yu Chengdong, Huawei's Managing Director, Chairman of Terminal BG, and Chairman of Smart Car Solutions BU, attended and delivered a speech and announced that Wenjie series models will be launched this year In August, Huawei Qiankun ADS 3.0 version was launched, and it is planned to successively push upgrades from August to September. The Xiangjie S9, which will be released on August 6, will debut Huawei’s ADS3.0 intelligent driving system. With the assistance of lidar, Huawei Qiankun ADS3.0 version will greatly improve its intelligent driving capabilities, have end-to-end integrated capabilities, and adopt a new end-to-end architecture of GOD (general obstacle identification)/PDP (predictive decision-making and control) , providing the NCA function of smart driving from parking space to parking space, and upgrading CAS3.0
 Which version of Apple 16 system is the best?
Mar 08, 2024 pm 05:16 PM
Which version of Apple 16 system is the best?
Mar 08, 2024 pm 05:16 PM
The best version of the Apple 16 system is iOS16.1.4. The best version of the iOS16 system may vary from person to person. The additions and improvements in daily use experience have also been praised by many users. Which version of the Apple 16 system is the best? Answer: iOS16.1.4 The best version of the iOS 16 system may vary from person to person. According to public information, iOS16, launched in 2022, is considered a very stable and performant version, and users are quite satisfied with its overall experience. In addition, the addition of new features and improvements in daily use experience in iOS16 have also been well received by many users. Especially in terms of updated battery life, signal performance and heating control, user feedback has been relatively positive. However, considering iPhone14
 Methods to solve localstorage security vulnerabilities
Jan 13, 2024 pm 01:43 PM
Methods to solve localstorage security vulnerabilities
Jan 13, 2024 pm 01:43 PM
Security vulnerabilities in localstorage and how to solve them With the development of the Internet, more and more applications and websites are beginning to use WebStorage API, of which localstorage is the most commonly used one. Localstorage provides a mechanism to store data on the client side, persisting data across page sessions regardless of session end or page refresh. However, just because of the convenience and wide application of localstorage, it also has some security vulnerabilities.
 Always new! Huawei Mate60 series upgrades to HarmonyOS 4.2: AI cloud enhancement, Xiaoyi Dialect is so easy to use
Jun 02, 2024 pm 02:58 PM
Always new! Huawei Mate60 series upgrades to HarmonyOS 4.2: AI cloud enhancement, Xiaoyi Dialect is so easy to use
Jun 02, 2024 pm 02:58 PM
On April 11, Huawei officially announced the HarmonyOS 4.2 100-machine upgrade plan for the first time. This time, more than 180 devices will participate in the upgrade, covering mobile phones, tablets, watches, headphones, smart screens and other devices. In the past month, with the steady progress of the HarmonyOS4.2 100-machine upgrade plan, many popular models including Huawei Pocket2, Huawei MateX5 series, nova12 series, Huawei Pura series, etc. have also started to upgrade and adapt, which means that there will be More Huawei model users can enjoy the common and often new experience brought by HarmonyOS. Judging from user feedback, the experience of Huawei Mate60 series models has improved in all aspects after upgrading HarmonyOS4.2. Especially Huawei M
 What are the computer operating systems?
Jan 12, 2024 pm 03:12 PM
What are the computer operating systems?
Jan 12, 2024 pm 03:12 PM
A computer operating system is a system used to manage computer hardware and software programs. It is also an operating system program developed based on all software systems. Different operating systems have different users. So what are the computer systems? Below, the editor will share with you what computer operating systems are. The so-called operating system is to manage computer hardware and software programs. All software is developed based on operating system programs. In fact, there are many types of operating systems, including those for industrial use, commercial use, and personal use, covering a wide range of applications. Below, the editor will explain to you what computer operating systems are. What computer operating systems are Windows systems? The Windows system is an operating system developed by Microsoft Corporation of the United States. than the most
 Detailed explanation of how to modify system date in Oracle database
Mar 09, 2024 am 10:21 AM
Detailed explanation of how to modify system date in Oracle database
Mar 09, 2024 am 10:21 AM
Detailed explanation of the method of modifying the system date in the Oracle database. In the Oracle database, the method of modifying the system date mainly involves modifying the NLS_DATE_FORMAT parameter and using the SYSDATE function. This article will introduce these two methods and their specific code examples in detail to help readers better understand and master the operation of modifying the system date in the Oracle database. 1. Modify NLS_DATE_FORMAT parameter method NLS_DATE_FORMAT is Oracle data




