
The four layers of the TCP/IP protocol architecture are: 1. Data link layer; the network driver that implements the network card interface to handle the transmission of data on the physical media. 2. Network layer; implements routing and forwarding of data packets. 3. Transport layer; provides end-to-end communication for applications on two hosts. 4. Application layer; responsible for processing the logic of the application.

Related recommendations: " Programming Learning"
is talking about the TCP/IP protocol system Before the structure, let's first take a look at the earliest used
OSI seven-layer model: from bottom to top, the physical layer, data link layer, network layer, transport layer, session layer, presentation layer, and application layer.
The following figure shows the process from the OSI seven-layer reference model to the TCP/IP four-layer architecture:
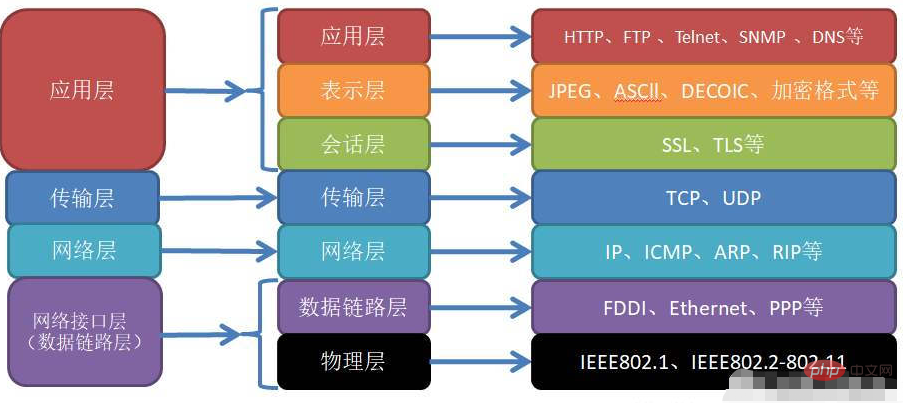
Advantages of TCP/IP architecture:
(1) Simplified the structure of the computer network, from the original seven layers to the current four layers, but its functions are not reduce.
(2) Each layer is independent and connected. The independence is because if there is a problem in that layer, it will not affect the work of other layers. The connection is because the upper layer protocol uses the services provided by the lower layer protocol.
You can also see from the above that the TCP/IP protocol suite is a four-layer protocol system. From bottom to top are the data link layer, network layer, transport layer, and application layer. Each layer completes different functions through several protocols, and the upper layer protocol uses the services provided by the lower layer protocol. Next, I will talk about the functions and common protocols of each layer.
1. Data link layer
Function: Implements the network driver of the network card interface to process data on physical media (such as Ethernet, Token Ring, etc. ) on the transmission.
Corresponding equipment: network cables, network bridges, hubs, switches
Commonly used protocols:
(1) ARP (Address Resolution Protocol): It realizes the conversion of IP address to physical address ( Usually it is the MAC address (the popular understanding is the conversion of the network card address).
(2) RARP (Reverse Address Resolution Protocol): As the name suggests, it is the opposite of ARP. It realizes the conversion from physical address to IP address.
Then someone will ask what is their use? ? ?
ARP purpose: The network layer uses the IP address to find a machine, while the data link layer uses the physical address to find a machine. Therefore, the network layer must first convert the IP address of the target machine into a physical address. In order to use the services provided by the data link layer.
RARP purpose: The RARP protocol is only used by some diskless workstations on the network. Due to the lack of storage devices, the diskless workstation cannot record its own IP address. However, through RARP, you can see the physical address to the IP address. Address mapping.
2. Network layer
Function: implement routing and forwarding of data packets.
Corresponding device: Router
Commonly used protocols:
(1) IP protocol (Internet Protocol) determines how to send the data packet to the destination based on the destination IP address. target host. If the data packet cannot be sent directly to the target host, then the IP protocol finds a suitable next-hop router for it and hands the data packet to the router for forwarding. After many times, the data packet will reach the target host or be discarded due to failure to send. .
(2) ICMP protocol is another important protocol at the network layer. It is an important supplement to the IP protocol and is mainly used to detect network connections.
8-bit type: ICMP messages are divided into two categories: one type is error messages, such as destination unreachable (type value 3) and redirection (type value 5); the other type It is a query message, used to query network information.
Some ICMP messages also use an 8-bit code field to subdivide different conditions. For example, a code value of 0 indicates network redirection, and a code value of 1 indicates host redirection.
16-bit checksum: Perform a cyclic redundancy check (CRC) on the entire message (including header and content parts).
Note: The ICMP protocol is not a network layer protocol in the strict sense, because it uses the services provided by the IP protocol at the same layer. Generally speaking, the upper layer protocol uses the services provided by the lower layer protocol.
3. Transport layer
Function: Provide end-to-end communication for applications on two hosts. Different from the hop-by-hop communication method used by the network layer, the transport layer only cares about the origin and destination of the communication and does not care about the transfer process of the data packet.
Main protocols:
(1) TCP protocol (Transmission Control Protocol): Provides reliable, connection-oriented and streaming services for the application layer.
(2) UDP protocol (User Datagram Protocol): Provides unreliable, connectionless and datagram services for the application layer. (The detailed explanation and difference between TCP and UDP protocols will be discussed in detail in the next article)
(3) SCTP protocol (Stream Control Transmission Protocol) It is designed for transmitting telephone signals on the Internet and will not be discussed here. Elaborate.
4. Application layer
Function: Responsible for processing the logic of the application, such as file transfer, name query and network management.
Note: The data link layer, network layer, and transport layer copy and process network communication details, so these parts must be stable and efficient, so they are all implemented in the kernel space (as shown in Figure 2 above), while the application layer is implemented in the user space , because it is responsible for a lot of logic, if implemented in the kernel, the kernel will become very large. There are also a few server programs that are implemented in the kernel, so that the code does not have to switch back and forth between user space and kernel space (mainly data copying), which improves work efficiency.
Commonly used protocols:
(1) OSPF (Open Shortest Path First) protocol: It is a dynamic routing update protocol used for communication between routers to inform each other of their respective routing information. .
(2) DNS (Domain Name Service) Protocol: Provides conversion of machine domain name to IP address. (For example, if you convert www.baidu.com into Baidu's IP, enter the domain name and you can enter directly. Because it is too troublesome to remember the IP address, just like everyone is uniquely identified by their ID card, but it is just for the sake of easy remembering. Name. DNS is a process of matching names with ID cards)
(3) The telnet protocol is a remote login protocol that allows us to complete remote tasks locally.
(4) HTTP protocol (Hypertext Transfer Protocol) is a stateless, application layer protocol based on request and response mode, often based on TCP connection method.
If you want to read more related articles, please visit PHP Chinese website! !
The above is the detailed content of What are the four layers of the TCP/IP protocol architecture?. For more information, please follow other related articles on the PHP Chinese website!
 Mechanical energy conservation law formula
Mechanical energy conservation law formula
 what is dandelion
what is dandelion
 The function of intermediate relay
The function of intermediate relay
 How to pay with WeChat on Douyin
How to pay with WeChat on Douyin
 All uses of cloud servers
All uses of cloud servers
 How to apply for a business email
How to apply for a business email
 Can Douyin short videos be restored after being deleted?
Can Douyin short videos be restored after being deleted?
 formatter function usage
formatter function usage
 How to use months_between in SQL
How to use months_between in SQL