How to disable sslv3 in apache

Introduction:
ssl 3.0 is considered unsafe because it uses RC4 encryption or CBC mode encryption, and the former is susceptible to bias attacks, while the latter Leads to POODLE attack.
In production environments, this vulnerability is often scanned. The solution is to disable the protocol on the apache server.
(Learning video sharing: Programming video)
1. Environment preparation
Understand SSL and TLS: http is used in the data transmission process. Plain text, in order to solve this problem https came into being, and ssl is an encryption protocol based on https. When SSL was updated to version 3.0, IETF (Internet Engineering Task Force) standardized SSL3.0. The standardized protocol is TLS1.0, so TLS is the standardized product of SSL. TLS currently has 1.0, 1.1, There are three versions of 1.2, and 1.0 is used by default. At this point we have a basic understanding of SSL and TLS.
The server operating environment required for the web server to support TLS1.2:
Apache对应版本应>=2.2.23; OpenSSL对应版本应>= 1.0.1
View the current server apache version
[root@host-192-168-149-10 conf.d]# httpd -v Server version: Apache/2.4.29 (Unix) Server built: Jan 22 2018 16:51:25
openssl version
[root@host-192-168-149-10 conf.d]# openssl version OpenSSL 1.0.1e-fips 11 Feb 2013
2. Environment rectification
Test domain names with security vulnerabilities. Access through sslv3 as follows can return information normally. Attackers may use this vulnerability to harm the system.
[root@host-192-168-149-10 conf.d]# curl --sslv3 https://cs.df230.xyz/test/api/configs/fedch/all
{
"overdue" : false,
"success" : true,
"errorCode" : null,
"message" : "请求成功",
"data" : {
"global" : {
"copyright" : "功能清单",
}apache supports SSLv3, TLSv1, TLSv1.1, TLSv1.2 protocols by default
(Note: the ssl function needs to enable LoadModule ssl_module modules/mod_ssl.so in http.conf)
The default configuration of apache is as follows
SSLProtocol All -SSLv2
Enter the directory /usr/local/apache/conf/extra
vi modify ssl.conf as follows to close the sslv3 protocol
SSLEngine on SSLProtocol all -SSLv2 -SSLv3 SSLProtocol TLSv1.2
After the configuration is saved, service httpd restart is required to restart apache to make the configuration take effect
Test sslv3 access again, unable to access
[root@host-192-168-149-10 conf.d]# curl --sslv3 https://cs.df230.xyz/test/api/configs/fedch/al curl: (35) SSL connect error
Enter development mode through Google browser F12, you can see the browsing The SSL protocol used by the server to access the current domain name is TLS1.2.
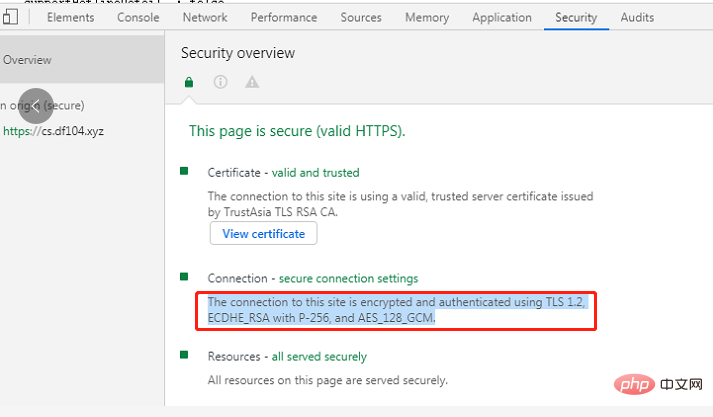
At this point, the vulnerability rectification is completed, so easy!
Related recommendations: apache tutorial
The above is the detailed content of How to disable sslv3 in apache. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1387
1387
 52
52
 How to set the cgi directory in apache
Apr 13, 2025 pm 01:18 PM
How to set the cgi directory in apache
Apr 13, 2025 pm 01:18 PM
To set up a CGI directory in Apache, you need to perform the following steps: Create a CGI directory such as "cgi-bin", and grant Apache write permissions. Add the "ScriptAlias" directive block in the Apache configuration file to map the CGI directory to the "/cgi-bin" URL. Restart Apache.
 How to start apache
Apr 13, 2025 pm 01:06 PM
How to start apache
Apr 13, 2025 pm 01:06 PM
The steps to start Apache are as follows: Install Apache (command: sudo apt-get install apache2 or download it from the official website) Start Apache (Linux: sudo systemctl start apache2; Windows: Right-click the "Apache2.4" service and select "Start") Check whether it has been started (Linux: sudo systemctl status apache2; Windows: Check the status of the "Apache2.4" service in the service manager) Enable boot automatically (optional, Linux: sudo systemctl
 How to use Debian Apache logs to improve website performance
Apr 12, 2025 pm 11:36 PM
How to use Debian Apache logs to improve website performance
Apr 12, 2025 pm 11:36 PM
This article will explain how to improve website performance by analyzing Apache logs under the Debian system. 1. Log Analysis Basics Apache log records the detailed information of all HTTP requests, including IP address, timestamp, request URL, HTTP method and response code. In Debian systems, these logs are usually located in the /var/log/apache2/access.log and /var/log/apache2/error.log directories. Understanding the log structure is the first step in effective analysis. 2. Log analysis tool You can use a variety of tools to analyze Apache logs: Command line tools: grep, awk, sed and other command line tools.
 How to delete more than server names of apache
Apr 13, 2025 pm 01:09 PM
How to delete more than server names of apache
Apr 13, 2025 pm 01:09 PM
To delete an extra ServerName directive from Apache, you can take the following steps: Identify and delete the extra ServerName directive. Restart Apache to make the changes take effect. Check the configuration file to verify changes. Test the server to make sure the problem is resolved.
 What to do if the apache80 port is occupied
Apr 13, 2025 pm 01:24 PM
What to do if the apache80 port is occupied
Apr 13, 2025 pm 01:24 PM
When the Apache 80 port is occupied, the solution is as follows: find out the process that occupies the port and close it. Check the firewall settings to make sure Apache is not blocked. If the above method does not work, please reconfigure Apache to use a different port. Restart the Apache service.
 How Debian improves Hadoop data processing speed
Apr 13, 2025 am 11:54 AM
How Debian improves Hadoop data processing speed
Apr 13, 2025 am 11:54 AM
This article discusses how to improve Hadoop data processing efficiency on Debian systems. Optimization strategies cover hardware upgrades, operating system parameter adjustments, Hadoop configuration modifications, and the use of efficient algorithms and tools. 1. Hardware resource strengthening ensures that all nodes have consistent hardware configurations, especially paying attention to CPU, memory and network equipment performance. Choosing high-performance hardware components is essential to improve overall processing speed. 2. Operating system tunes file descriptors and network connections: Modify the /etc/security/limits.conf file to increase the upper limit of file descriptors and network connections allowed to be opened at the same time by the system. JVM parameter adjustment: Adjust in hadoop-env.sh file
 How to view your apache version
Apr 13, 2025 pm 01:15 PM
How to view your apache version
Apr 13, 2025 pm 01:15 PM
There are 3 ways to view the version on the Apache server: via the command line (apachectl -v or apache2ctl -v), check the server status page (http://<server IP or domain name>/server-status), or view the Apache configuration file (ServerVersion: Apache/<version number>).
 How to check Debian OpenSSL configuration
Apr 12, 2025 pm 11:57 PM
How to check Debian OpenSSL configuration
Apr 12, 2025 pm 11:57 PM
This article introduces several methods to check the OpenSSL configuration of the Debian system to help you quickly grasp the security status of the system. 1. Confirm the OpenSSL version First, verify whether OpenSSL has been installed and version information. Enter the following command in the terminal: If opensslversion is not installed, the system will prompt an error. 2. View the configuration file. The main configuration file of OpenSSL is usually located in /etc/ssl/openssl.cnf. You can use a text editor (such as nano) to view: sudonano/etc/ssl/openssl.cnf This file contains important configuration information such as key, certificate path, and encryption algorithm. 3. Utilize OPE




