
The following phpmyadmin tutorial column will introduce you to phpmyadmin penetration tips. I hope it will be helpful to friends in need!

##Just record it for yourself, if you all Don’t dislike it when you see itSome website building software or fool-like building software phpmyadmin often uses ports 888 and 999
<br>
We can try to use nikto to detect the corresponding unauthorized Vulnerability<br>nikto -host http://Test domain name address: 999/
<br>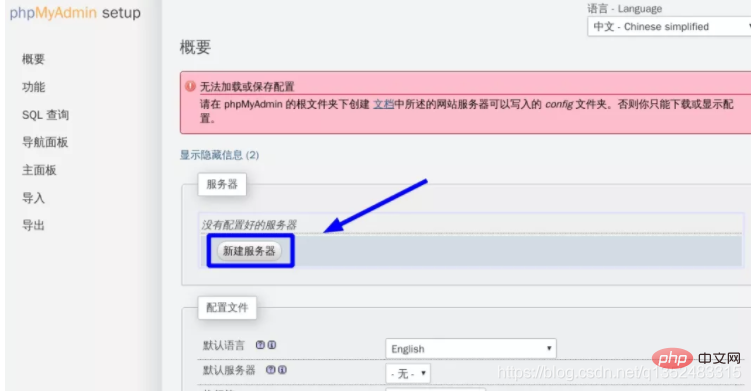

<br>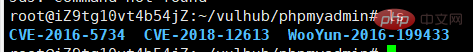
show variables like "%dir%";
<br>
The above is the detailed content of Record phpmyadmin penetration tips. For more information, please follow other related articles on the PHP Chinese website!
 Commonly used mysql management tools
Commonly used mysql management tools
 What to do if phpmyadmin fails to import sql file
What to do if phpmyadmin fails to import sql file
 How to change phpmyadmin to Chinese
How to change phpmyadmin to Chinese
 What's going on when phpmyadmin can't access it?
What's going on when phpmyadmin can't access it?
 How to reference css in html
How to reference css in html
 What skills are needed to work in the PHP industry?
What skills are needed to work in the PHP industry?
 Oracle database recovery method
Oracle database recovery method
 Basic building blocks of presentations
Basic building blocks of presentations
 The purpose of level
The purpose of level