<img src="/static/imghw/default1.png" data-src="https://img.php.cn/upload/article/000/000/052/5ffcf9b492b47340.jpg" class="lazy" alt="Troubleshooting SQL injection issues" >
Recommended (free):<a href="https://www.php.cn/sql/" target="_blank">SQL tutorial</a>
SQL What is injection?
Look at the definition of Baidu Encyclopedia: 
Ah, it’s such a long paragraph. I don’t want to read it. Let’s use an example to explain what SQL injection is. :
Create a new database, create a table, and add two rows of data:
use db1;create table user( id int primary key auto_increment, username varchar(32), password varchar(32));insert into user values(null,'zhangsan','123');insert into user values(null,'lisi','234');
The table is as shown below: 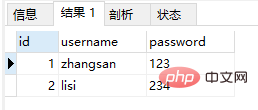
Use it casually JDBCWrite a login operation:
package com.wzq.jdbc;import com.wzq.util.JDBCUtils;import java.sql.Connection;import java.sql.ResultSet;import java.sql.SQLException;import java.sql.Statement;import java.util.Scanner;/*
* 需求:
* 1、通过键盘录入用户名和密码
* 2、判断用户是否登陆成功
* */public class JDBCDemo05 {
public static void main(String[] args) {
Scanner cin = new Scanner(System.in);
System.out.println("请输入用户名:");
String username = cin.nextLine();
System.out.println("请输入密码:");
String password = cin.nextLine();
boolean res = new JDBCDemo05().login(username, password);
if (res) System.out.println("登陆成功!");
else System.out.println("登陆失败!");
}
public boolean login(String username, String password) {
if (username == null || password == null) {
return false;
}
Connection conn = null;
Statement stmt = null;
ResultSet rs = null;
try {
//1、获取数据库连接
conn = JDBCUtils.getConnection(); //JDBCUtils工具类
//2、定义sql
String sql = "select * from user where username = '" + username + "' and password = '" + password + "'";
//3、获取执行sql的对象
stmt = conn.createStatement();
//4、执行sql
rs = stmt.executeQuery(sql);
return rs.next();
} catch (SQLException e) {
e.printStackTrace();
} finally {
JDBCUtils.close(rs, stmt, conn);
}
return false;
}}Test it: 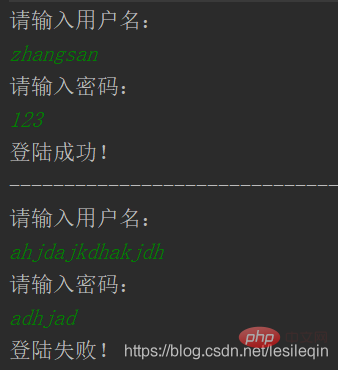
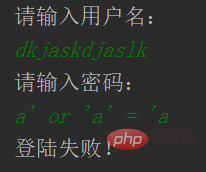
You can see that there is no problem with the ordinary test. Now use SQL injection:
Enter the account name casually, enter the password: a' or 'a'='a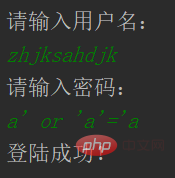
I was surprised to find that the login was successful. Output sql and take a look:
select * from user where username = 'askjdhjksahd' and password = 'a' or 'a' = 'a'
You can see the conditions after where. No matter what result is true, the entire table will be output: 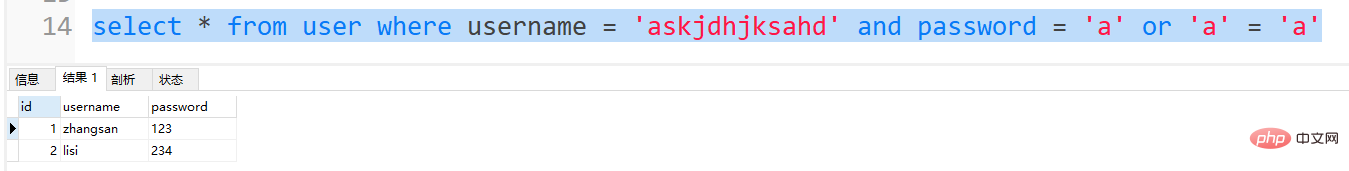
So, to sum up: when splicing sql, some sql special keywords participate in string splicing, which will cause security problems. This This is the reason why the login is successful above.
So how to solve this problem?
Answer: Use the PreparedStatement object instead of the Statement object.
PreparedStatement object is a subclass of Statement object. It is precompiled sql, so it runs faster than StatemnetFaster.
PerpaerdStatementUse ? as a placeholder and use setXxx(index, value) to assign a value## to ?
Statement and write the code:
public boolean login(String username, String password) { if (username == null || password == null) { return false;
}
Connection conn = null;
PreparedStatement pstmt = null;
ResultSet rs = null;
try { //1、获取数据库连接
conn = JDBCUtils.getConnection(); //JDBCUtils类
//2、定义sql
String sql = "select * from user where username = ? and password = ?";
//3、获取执行sql的对象
pstmt = conn.prepareStatement(sql);
pstmt.setString(1,username);
pstmt.setString(2,password);
//4、执行sql
rs = pstmt.executeQuery();
return rs.next();
} catch (SQLException e) {
e.printStackTrace();
} finally {
JDBCUtils.close(rs, pstmt, conn);
} return false;
} Successfully solved!
Successfully solved!
The above is the detailed content of Troubleshooting SQL injection issues. For more information, please follow other related articles on the PHP Chinese website!




