Discuss the loopholes of a group buying website

Foreword:
Last September, my colleague bought a hot pot set meal on a group buying website, and then he bought it almost every day. During New Year's Day, the group buying website launched the "VIP members receive red envelopes for 0 yuan" activity. Who doesn't like receiving red envelopes? So I got involved in that.
So I decisively went in to register, click to buy, entered the shopping cart and clicked to confirm the order, eh? Why does the alert say "This event is limited to VIP members only"? My first reaction was to look at the source code of the page (since the event has ended and I can’t enter the purchase page, I have to use pseudo code to express it here):
//确认订单按钮的点击事件function btn_click(){
ajax获取当前用户的类型
如果不是VIP,alert("本活动仅限VIP会员参与");
否则 form1.submit();
}Then I typed in the address bar :javascript:form1.submit(); Enter! Enter the payment page, then click OK, okay? Purchase successful! I got a 5 yuan red envelope!
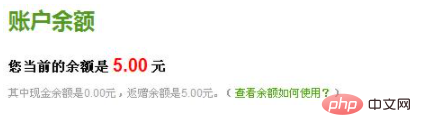
So awesome! ! ! I registered a new account and repeated the above steps, and successfully received a 5 yuan red envelope.
I immediately left a message to customer service to explain this bug, but they haven’t replied to me till today, haha.
The key point of this vulnerability is that the developer forgot to determine whether the current user is a VIP member in the background code of form1.submit() and only relied on javascript verification.
The front-end verification is of no use, you can completely bypass it, the back-end verification is the most important! !
With what I gained in the morning, I continued to look for loopholes in other group buying websites on the night of the 1st, and sure enough, I found a more serious one.
The group buying website also held a New Year's Day lottery to smash golden eggs. It is also free to participate. After purchasing, I found that I had to invite friends to participate in the event to have the chance to smash golden eggs. Inviting a friend will give you one more chance, as shown in the picture :

As soon as I clicked on the golden egg, the alert said "There are no more lottery opportunities, go and invite your friends!", um, it's javascript again? Take a look at the code first:
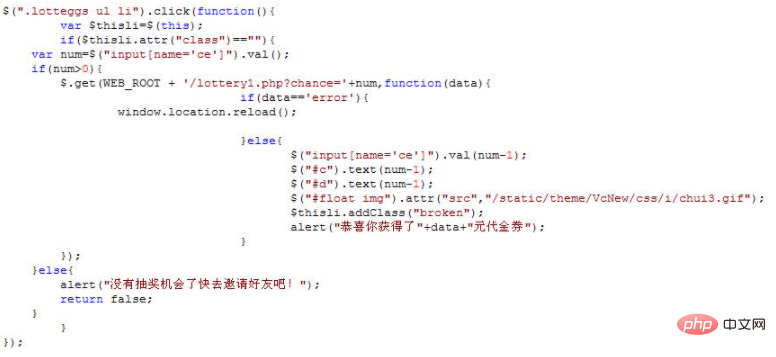
#This is the click event of the golden egg. There is a page lottery1.php accessed using AJAX, and the chance variable to be passed should be It is the opportunity for the current user to smash eggs.
(Learning video sharing: Introduction to Programming)
I tried to access lottery1.php?chance=1 directly, and the error string was returned, lottery1.php?chance= 0 also returns error, lottery1.php?chance=-1, also
returns error, doesn’t it have any effect? I refreshed the Golden Egg Smashing page, wow! !

I passed -1 and it caused an overflow? I tried smashing a few and got vouchers every time! ! So awesome. Then I tried to use the voucher to place an order, and I was able to successfully save a few dollars.
But you can only use one voucher for one order, haha (of course I canceled the test order in the end, and I still Not that evil, wakaka)
I contacted customer service immediately, but it was off duty, QQ was not online, and the phone call could not be reached, so I had to leave a message.
What to do next? Smash the eggs! As for the 4.2 billion golden egg, write a piece of JS and it will be smashed automatically! So far, a total of 3588 golden eggs have been smashed, of which at least more than 2000 were smashed by me. Wow Kaka
got a lot of vouchers:
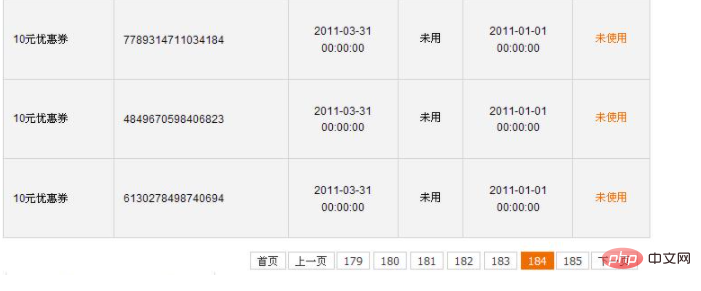
185 pages in total, haha, quite spectacular! ! !
On the 2nd, when I re-checked the code of the group purchase website, I found a more serious problem:
There is such a method in JS
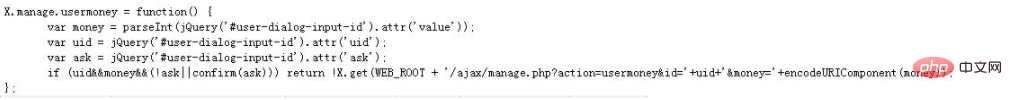
At first glance, it seems to be related to money. Pass in the user ID and the amount of money and try to see what effect it has.
How to get the user ID? Don't worry, there is:
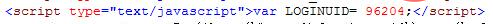
This 96204 is the ID of my current account. After visiting it, it returned "Offline recharge successful", wow, so awesome? There is no permission verification on the recharge page?
Checked the account balance, and sure enough the recharge was successful:
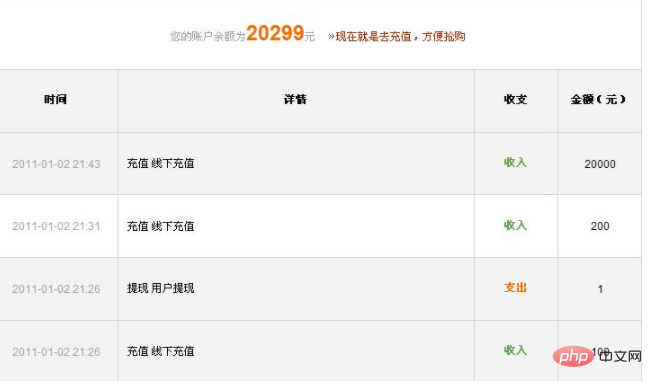
I have a balance of 20,000, wow! ! This vulnerability is too fatal. Leave a message to customer service immediately. Just after I left the message, their developer called me to discuss with me
The vulnerability issue of Smashing the Golden Egg was just right to tell him the newly discovered vulnerability together. Developers have a hard life. During New Year's Day, after 10 o'clock in the evening, he still had to change the code.
After the correction, he said that the boss might give me some gifts. I’m really looking forward to it, haha.
Finally, he cleared my account balance, and I shouted in my heart: No, I want it, my 20,000 yuan~~~~~~~~
To summarize : The front-end verification is unreliable, and the back-end must be verified if necessary; access permissions must be added to the management page; the data passed to the back-end must be
verified for legality; unnecessary parameters passed If you don't pass it, for example, for the egg-breaking one, I just don't understand why the egg-breaking opportunities owned by the current user should be passed to the
background. Can't it be read directly from the database? The user ID should not appear in clear text. In addition, we must guard against XSS cross-site scripting attacks (usually by judging the host header)
My website: http://i.goto327.top:85/
Related recommendations:Website Security
The above is the detailed content of Discuss the loopholes of a group buying website. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1386
1386
 52
52
 Jailbreak any large model in 20 steps! More 'grandma loopholes' are discovered automatically
Nov 05, 2023 pm 08:13 PM
Jailbreak any large model in 20 steps! More 'grandma loopholes' are discovered automatically
Nov 05, 2023 pm 08:13 PM
In less than a minute and no more than 20 steps, you can bypass security restrictions and successfully jailbreak a large model! And there is no need to know the internal details of the model - only two black box models need to interact, and the AI can fully automatically defeat the AI and speak dangerous content. I heard that the once-popular "Grandma Loophole" has been fixed: Now, facing the "Detective Loophole", "Adventurer Loophole" and "Writer Loophole", what response strategy should artificial intelligence adopt? After a wave of onslaught, GPT-4 couldn't stand it anymore, and directly said that it would poison the water supply system as long as... this or that. The key point is that this is just a small wave of vulnerabilities exposed by the University of Pennsylvania research team, and using their newly developed algorithm, AI can automatically generate various attack prompts. Researchers say this method is better than existing
 Buffer overflow vulnerability in Java and its harm
Aug 09, 2023 pm 05:57 PM
Buffer overflow vulnerability in Java and its harm
Aug 09, 2023 pm 05:57 PM
Buffer overflow vulnerabilities in Java and their harm Buffer overflow means that when we write more data to a buffer than its capacity, it will cause data to overflow to other memory areas. This overflow behavior is often exploited by hackers, which can lead to serious consequences such as abnormal code execution and system crash. This article will introduce buffer overflow vulnerabilities and their harm in Java, and give code examples to help readers better understand. The buffer classes widely used in Java include ByteBuffer, CharBuffer, and ShortB
 How to solve common file upload vulnerabilities in PHP language development?
Jun 10, 2023 am 11:10 AM
How to solve common file upload vulnerabilities in PHP language development?
Jun 10, 2023 am 11:10 AM
In the development of web applications, the file upload function has become a basic requirement. This feature allows users to upload their own files to the server and then store or process them on the server. However, this feature also makes developers need to pay more attention to a security vulnerability: the file upload vulnerability. Attackers can attack the server by uploading malicious files, causing the server to suffer varying degrees of damage. PHP language is one of the languages widely used in web development, and file upload vulnerabilities are also one of the common security issues. This article will introduce
 The OpenAI DALL-E 3 model has a vulnerability that generates 'inappropriate content.' A Microsoft employee reported it and was slapped with a 'gag order.'
Feb 04, 2024 pm 02:40 PM
The OpenAI DALL-E 3 model has a vulnerability that generates 'inappropriate content.' A Microsoft employee reported it and was slapped with a 'gag order.'
Feb 04, 2024 pm 02:40 PM
According to news on February 2, Shane Jones, manager of Microsoft’s software engineering department, recently discovered a vulnerability in OpenAI’s DALL-E3 model, which is said to be able to generate a series of inappropriate content. Shane Jones reported the vulnerability to the company, but was asked to keep it confidential. However, he eventually decided to disclose the vulnerability to the outside world. ▲Image source: Report disclosed by ShaneJones. This site noticed that ShaneJones discovered through independent research in December last year that there was a vulnerability in the DALL-E3 model of OpenAI text-generated images. This vulnerability can bypass the AI Guardrail (AIGuardrail), resulting in the generation of a series of NSFW inappropriate content. This discovery attracted widespread attention
 Comma operator vulnerabilities and protective measures in Java
Aug 10, 2023 pm 02:21 PM
Comma operator vulnerabilities and protective measures in Java
Aug 10, 2023 pm 02:21 PM
Overview of Comma Operator Vulnerabilities and Defense Measures in Java: In Java programming, we often use the comma operator to perform multiple operations at the same time. However, sometimes we may overlook some potential vulnerabilities of the comma operator that may lead to unexpected results. This article will introduce the vulnerabilities of the comma operator in Java and provide corresponding protective measures. Usage of comma operator: The syntax of comma operator in Java is expr1, expr2, which can be said to be a sequence operator. Its function is to first calculate ex
 Lenovo has issued a patch in May, Phoenix UEFI firmware vulnerability disclosed: affecting hundreds of Intel PC CPU models
Jun 22, 2024 am 10:27 AM
Lenovo has issued a patch in May, Phoenix UEFI firmware vulnerability disclosed: affecting hundreds of Intel PC CPU models
Jun 22, 2024 am 10:27 AM
According to news from this site on June 21, the Phoenix Secure Core UEFI firmware was exposed to a security vulnerability, affecting hundreds of Intel CPU devices. Lenovo has released a new firmware update to fix the vulnerability. This site learned from reports that the vulnerability tracking number is CVE-2024-0762, known as "UEFICANHAZBUFFEROVERFLOW", which exists in the Trusted Platform Module (TPM) configuration of Phoenix UEFI firmware. It is a buffer overflow vulnerability that can be Exploit to execute arbitrary code on a vulnerable device. The vulnerability was discovered by Eclypsium in Lenovo ThinkPad X1 Carbon 7th generation and X1Yoga 4th generation
 Zerodium announces $400,000 payout for Microsoft Outlook Zero-Click RCE security vulnerability
Apr 29, 2023 pm 09:28 PM
Zerodium announces $400,000 payout for Microsoft Outlook Zero-Click RCE security vulnerability
Apr 29, 2023 pm 09:28 PM
<ul><li><strong>Click to enter:</strong>ChatGPT tool plug-in navigation</li></ul><figureclass="imageimage--expandable"><imgsrc ="/uploads/2023041
 HTTP response splitting vulnerability in Java and its fix
Aug 08, 2023 am 08:19 AM
HTTP response splitting vulnerability in Java and its fix
Aug 08, 2023 am 08:19 AM
Summary of HTTP Response Splitting Vulnerabilities in Java and Their Fixes: In Java Web applications, HTTP response splitting vulnerabilities are a common security threat. This article will introduce the principle and impact of the HTTP response splitting vulnerability, as well as how to fix the vulnerability, and use code examples to help developers better understand and prevent such security threats. Introduction The HTTP protocol is one of the most commonly used protocols in web applications. It communicates through HTTP requests and HTTP responses to provide interaction with the web server.




