
Foreword:
I believe that for most programmers, redis middleware should be very familiar to everyone. However, for programmers who often write business code at work, they may only use set value, get value and other operations in actual work, and lack an overall understanding of redis. Now let me introduce redis to you in detail.
What is Redis?
Redis is an open source underlying key-value storage database written in C language. It can be used in scenarios such as caching, event publishing and subscription, and high-speed queues. And supports rich data types: string (string), hash (hash), list (list), set (unordered set), zset (sorted set: ordered set)
Redis is in the project Application scenarios
1. Caching data
is the most commonly used. Data that needs to be queried frequently and changes infrequently is often called hot data.
2. Message Queue
is equivalent to a message subscription system, such as ActiveMQ and RocketMQ. If you have high consistency requirements for data, it is still recommended to use MQ)
3, counter
For example, counting click rate and like rate, redis is atomic and can avoid concurrency problems
4. E-commerce website information
Large e-commerce platforms initialize the cache of page data. For example, when purchasing a flight ticket on Qunar.com, the price on the home page will be different from the price you click on.
5. Hotspot data
For example, real-time hot spots on news websites, hot searches on Weibo, etc. need to be updated frequently. When the total amount of data is relatively large, querying directly from the database will affect performance
Give me a reason to love
We usually do this on a single-node server
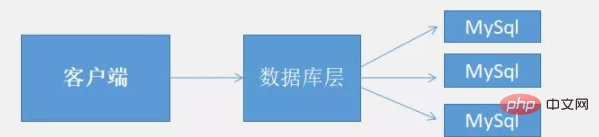
With the development of enterprises and expansion of business. In the face of massive data, using MySql directly will cause performance degradation, and data reading and writing will also be very slow. So we can use caching to process massive data.
So now we are like this:
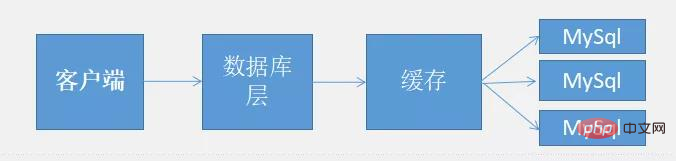
#The above picture only briefly describes the role of cache. When the data continues to increase, we need to use master-slave replication technology. To achieve read-write separation
The database layer interacts directly with the cache. If there is data in the cache, it is directly returned to the client. If not, it will be queried from MySql. This reduces the pressure on the database and improves efficiency.
Usually when a new mobile phone is released, there will be rush sales. During the same period of time, the server will receive many order requests.
We need to use redis's atomic operation to implement this "single thread". First, we store the inventory in a list. Assuming there are 10 items in inventory, we push 10 numbers into the list. This number has no practical meaning and only represents 10 items in inventory. After the rush purchase starts, every time a user arrives, a number will pop up from the list, indicating that the user's rush purchase is successful. When the list is empty, it means it has been taken away. Because the pop operation of the list is atomic, even if many users arrive at the same time, they will be executed sequentially.
Digression: Some rush purchases directly limit requests on the front-end page. These requests are directly intercepted by the front-end and are not To the backend server
Why is Redis so fast?
1. Redis is a pure memory operation. When needed, we need to manually persist it to the hard disk.
2. Redis is single-threaded, thus avoiding the frequent context switching operations in multi-threads. .
3. The Redis data structure is simple, and the operation of data is relatively simple.
4. The underlying models used are different, and the underlying implementation methods and application protocols for communication with the client are different. Similarly, Redis directly builds its own VM mechanism, because if the general system calls system functions, it will waste a certain amount of time to move and request
5. Use a multi-channel I/O multiplexing model, non-blocking I/O O
Multiple I/O multiplexing: I/O multiplexing technology is a technology that appears to solve the problem of processes or threads blocking a certain I/O system call. It can monitor multiple descriptors. Once a certain descriptor is ready (usually read-ready or write-ready, that is, before the file descriptor performs read and write operations), the program can be notified to perform the corresponding read and write operations
(Learning video sharing: redis video tutorial)
Application scenarios of Redis data types
As mentioned earlier, Redis supports five rich data types, so how should we choose in different scenarios?
String
String is the most commonly used data type. It can store any type of string, including binary, JSON-encoded objects, and even base64-encoded images. The maximum capacity of a string in Redis is 512MB, which can be said to be omnipotent.
Hash
It is often used to store structured data. For example, in forum systems, it can be used to store user ID, nickname, avatar, points and other information. If you need to modify the information, you only need to take out the Value through the Key, deserialize it, modify the value of an item, and then serialize and store it in Redis. The Hash structure is stored because the Hash structure will be modified when a single Hash element is less than a certain number. Compressed storage, so you can save a lot of memory. This does not exist in the String structure.
List
List is implemented as a doubly linked list, which can support reverse search and traversal, making it more convenient to operate. However, it brings some additional memory overhead. Many implementations within Redis, Including the send buffer queue, etc., this data structure is also used. In addition, you can use the lrange command to implement Redis-based paging function, which has excellent performance and good user experience.
Set
The external functions provided by set are similar to those of list. The special thing is that set can automatically eliminate duplication. When you need to store a list data, but don’t want to When duplicate data appears, you can choose to use set at this time.
Sort Set
can be sorted according to the weight of a certain condition, for example, a ranking data application can be made based on the number of clicks.
Data consistency of Redis cache
In a true sense, it is impossible for the database data and the cached data to be consistent. The data is divided into two categories: final consistency and strong consistency. If the requirements for data in the business must be strong, caching cannot be used. All the cache can do is ensure the eventual consistency of the data.
All we can do is ensure data consistency as much as possible. Regardless of whether the database is deleted first and then the cache, or the cache is deleted first and then the database, data inconsistency may occur. Because read and write operations are concurrent, we cannot guarantee their order. The specific response strategy still needs to be determined based on business needs, so I won’t go into details here.
Redis expiration and memory elimination
We can set its expiration time when Redis stores data. But how is this key deleted?
At first I thought it was a scheduled deletion, but later I found out that this is not the case, because if it is scheduled to be deleted, a timer is needed to continuously monitor the key. Although the memory is released, it consumes a lot of CPU resources.
Redis expiration deletion uses regular deletion. The default is to detect once every 100ms. When an expired key is encountered, it will be deleted. The detection here is not a sequential detection, but a random detection. Will any fish slip through the net? Obviously Redis has also taken this into consideration. When we read/write an expired key, Redis's lazy deletion strategy will be triggered and the expired key will be deleted directly.
Memory elimination refers to part of the keys stored by the user It can be automatically deleted by Redis, so the data cannot be found in the cache. The memory of our server is 2G, but with the development of business, the cached data has exceeded 2G. But this does not affect the running of our program, because the visible memory of the operating system is not limited by physical memory. It doesn't matter if the physical memory is not enough. The computer will allocate a space from the hard disk as virtual memory. This is the original intention of Redis to design two application scenarios: cache and persistent storage
Cache breakdown
The cache is just a layer of protection added to relieve the pressure on the database. When the query from the cache cannot When we get the data we need, we have to query it in the database. If hackers are used to frequently access data that is not in the cache, the cache will lose its meaning, and the pressure of all requests will fall on the database in an instant, which will cause database connection abnormalities.
Solution:
1. Set up scheduled tasks in the background to actively update cached data. This solution is easy to understand, but when the keys are relatively scattered, the operation is still relatively complicated.
2. Hierarchical caching. For example, setting up two layers of cache protection, the level 1 cache has a short expiration time, and the level 2 cache has a long expiration time. When a request comes in, it is first searched in the level 1 cache. If the corresponding data is not found in the level 1 cache, the thread is locked. This thread then gets the data from the database and updates it to the level 1 and level 2 caches. Other threads obtain
3 directly from the level 2 thread, provide an interception mechanism, and maintain a series of legal key values internally. When the requested key is invalid, it will be returned directly.
Cache avalanche
Cache avalanche means that the cache crashes due to some reasons (such as downtime, cache service hanging or unresponsiveness), resulting in a large number of requests reaching the back-end database, thus Causing the database to crash, the entire system to crash, and disaster to occur, which is the cache breakdown mentioned above.
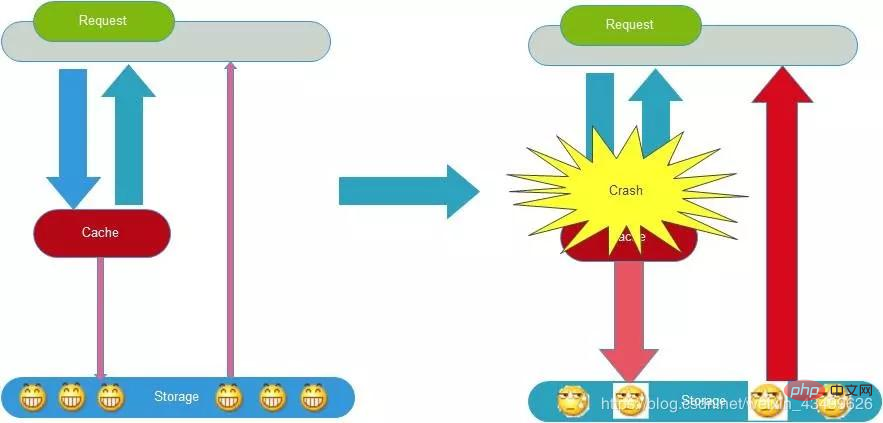
How to avoid avalanches:
1. Add a random effective time within a certain range to the cache, and set different expiration times for different keys. , to avoid collective failure at the same time.
2. Similar to the cache breakdown solution, create a secondary cache and read data from the copy cache when the original cache fails.
3. Use locking or queuing to prevent too many requests from reading and writing to the server at the same time.
Conclusion:
Redis has extremely high performance, with a reading speed of 110,000 times/s and a writing speed of 81,000 times/s. It supports transactions, backups, and rich data types.
Everything has two sides, and Redis also has shortcomings:
1. Since it is an in-memory database, the amount of data stored in a single machine is limited, and developers need to estimate in advance. Unnecessary data needs to be deleted promptly.
2. After modifying the Redis data, the data persisted to the hard disk needs to be re-added to the content. This takes a long time, and Redis cannot run normally at this time.
Original link: https://www.pianshen.com/article/589052263/
Related recommendations: redis database tutorial
The above is the detailed content of Why is it said that redis is very useful?. For more information, please follow other related articles on the PHP Chinese website!
 Commonly used database software
Commonly used database software
 What are the in-memory databases?
What are the in-memory databases?
 Which one has faster reading speed, mongodb or redis?
Which one has faster reading speed, mongodb or redis?
 How to use redis as a cache server
How to use redis as a cache server
 How redis solves data consistency
How redis solves data consistency
 How do mysql and redis ensure double-write consistency?
How do mysql and redis ensure double-write consistency?
 What data does redis cache generally store?
What data does redis cache generally store?
 What are the 8 data types of redis
What are the 8 data types of redis