How to keep the web safe

1. Foreword
In the early days of the development of the Internet, it was still the era of the IE browser. At that time, the purpose of everyone surfing the Internet was to share information and obtain news through the browser. With the rapid development of the Internet, web pages can do more and more things. You can not only read news and play games, but also shop and chat. These functions have greatly enriched our lives.
As the functions of web pages gradually increase, some black hats have begun to appear, and they try to make profits through some technical means. For example, Trojan viruses can monitor your keyboard and send the content you type on the keyboard to the hacker's machine. By analyzing the content, the hacker can easily obtain your game account and password. After that, some anti-virus software was born, dedicated to solving various viruses on the Internet. With continuous development, anti-virus software has become an indispensable software for a computer.
Why does such a security problem occur?
Security is ultimately a matter of trust. If everyone goes online according to normal procedures and does not seek personal gain, there will be no security issues to discuss.
The foundation of security lies in trust, but it is easier said than done to make everyone trust each other. At the current stage, what we can do is: continue to improve security protection, make loopholes less and less, and illegal attacks become more and more difficult. This will gradually reduce the number of black hats and reduce virus creators.
1. How to do a good job in security
To do a good job in security, you must first understand the attributes of security issues. Through countless practices, predecessors finally summarized the attributes of security into three elements of security, which are: :
1) Confidentiality
Protect data content from being leaked. Encryption methods are usually used.
2) Integrity
Protect that the data content is complete and has not been tampered with. Usually digital signature method is used.
3) Availability.
Data can be used at any time. Usually defending against DOS.
2. Security Assessment
After having the 3 elements of security, we can evaluate security issues.
1) Asset level classification
Find out the most important data. Find out the hosting space of the most important data, such as in a database, then the database must focus on defense. Find out the hosting space of the database, for example: on a server, then this server must provide secondary defense. Find out the host space of the server, such as: at the OSI network level, then you have to do general defense at the network level.
2) Threat analysis
Find out threats (sources that may cause harm). Find out the risks (possible losses are called risks).
3) Risk analysis
adopts multi-criteria decision-making analysis, that is: risk = threat level * threat feasibility. Calculate all threats, rank the final risks, and prioritize issues with higher risks.
4) Confirm the solution
Find out the unsafe implementation and determine the solution. The solution should not change the original intention of the business requirement. The solution needs to be transparent to users and not change their habits.
After completing the security assessment, we will have a security solution. For subsequent security work, we only need to follow this plan and there will be no problems.
3. Safety principles
After having a safety solution, we can also formulate some safety principles. Following the principles can help us get twice the result with half the effort.
1) Blacklist and whitelist principles
The whitelist solution refers to authorizing safe resources. Blacklisting scheme refers to disabling unsafe resources. We should give priority to using the whitelist solution, because the blacklist usually cannot count all unsafe resources. For example, there are many ways to attack XSS, including script, css, image tags, etc. Even if you add these tags to the blacklist, there is no guarantee that other tags will not have XSS attack risks.
2) Principle of least privilege
Only grant necessary permissions, do not over-authorize, and reduce the chance of errors. For example: Linux users with ordinary permissions can only operate directories under the ~ folder. If someone wants to delete the library and run away, when executing rm -rf /, it will prompt that there is no permission.
3) Defense in depth principle
This principle is similar to the barrel theory. The safety level often depends on the shortest board. That is: don’t leave any shortcomings. Black hats can often use shortcomings as a breakthrough point to dig out larger loopholes.
4) Principle of separation of data and code
When user data is executed as code, the boundaries between data and code are confused, leading to security issues. For example: XSS uses this to attack.
5) Principle of Unpredictability
This principle is to increase the attack threshold and effectively prevent attacks based on tampering and forgery. For example, using uuid instead of number-type auto-incrementing primary key in the database can prevent the id from being guessed by attackers, allowing batch operations to be performed. Token also takes advantage of unpredictability. The attacker cannot construct the token and cannot attack.
With these security principles in mind, let’s introduce several common attack and defense cases.
2. Security Attack and Defense Cases
There are many security attack and defense cases. Here we mainly introduce a few security issues with a relatively high appearance rate.
(1) Client attack
Mainly include: XSS attacks, CSRF attacks, and click hijacking.
1.
##As shown in the picture, we registered a user name of <script>alert(document.cookie)</script>, and everyone can see this user name On every page, the cookie of the current browser will pop up. If the logic of the code is to send the cookie to the attacker's website, the attacker can log in pretending to be the current user. 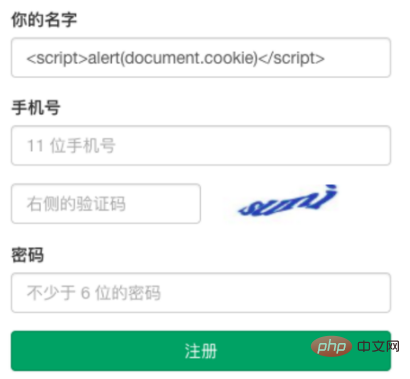
- window.location.
- window.name.
- document.referrer.
- document.cookie.
- localstorage.
- ...
- Since there are so many places on the page to interact with users, there must be some XSS attack methods that have not been discovered. Once discovered by a black hat, it may have serious consequences, so we must pay attention to it.
php video tutorial
)Click hijacking is a visual deception attack method. The attacker embeds the website that needs to be attacked into his own web page through iframe nesting, sets the iframe to transparent, and reveals a button on the page to induce users to click. It’s like a picture with a layer of transparent paper on it. What you see is the attacker’s page, but in fact this page is only at the bottom, and what you actually click on is the attacker’s page. of another web page. 1) Click hijacking defenseSince click hijacking mainly passes through iframe, the defense is mainly based on iframe. Option 1: frame bustingif (self !== top) { // 跳回原页面
top.location = self.location;
}配置 iframe 的 sandbox 属性:sandbox = "allow-same-origin" ,则只能加载与主站同域的资源。
(二)服务端攻击
服务器端的攻击的方式也非常多,这里列举几个常见的。
SQL 注入攻击文件上传漏洞登录认证攻击应用层拒绝服务攻击webServer 配置安全
1、SQL 注入攻击
SQL 注入和 XSS 一样,都是违背了数据和代码分离原则导致的攻击方式。
如图所示,我们利用 SQL 注入,就能在不需要密码的情况下,直接登录管理员的账号。
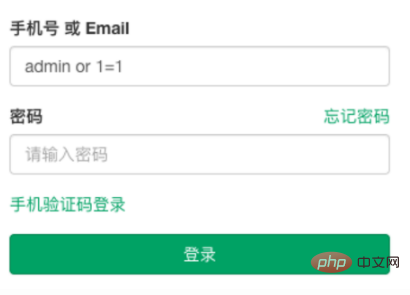
攻击的前提是:后端只用了简单的拼接 SQL 的方式去查询数据。
// 拼接出来的 sql 如下:select * from user where username = 'admin' or 1=1 and password = 'xxx' // 无论密码输入什么,这条 sql 语句都能查询到管理员的信息
除此之外,SQL 注入还有以下几种方式:
a、使用 SQL 探测,猜数据库表名,列名。
通过 MySQL 内置的 benchmark 探测数据库字段。如:一段伪代码 select database as current if current[0]==='a',benchmark(10000,'猜对了') 如果表明猜对了,就延迟 10 s 并返回成功。
b、使用存储过程执行系统命令
通过内置的方法或存储过程执行 shell 脚本。如:xp_cmdshell、sys_eval、sys_exec 等。
c、字符串截断
如:MySQL 在处理超长的字符串时,会显示警告,但会执行成功。注册一个 admin + 50 个空格的用户,会触发截断,最终新增一个 admin 用户,这样就能拥有管理员权限了。
1)SQL 注入防御
防止 SQL 注入的最好的办法就是,不要手动拼接 SQL 语句。
最佳方案,使用预编译语句绑定变量:通常是指框架提供的拼接 SQL 变量的方法。这样的语义不会发生改变,变量始终被当成变量。严格限制数据类型,如果注入了其他类型的数据,直接报错,不允许执行。使用安全的存储过程和系统函数。
2、CRLF 注入
在注入攻击中,换行符注入也是非常常见的一种攻击方式。
如果在 HTTP 请求头中注入 2 个换行符,会导致换行符后面的所有内容都被解析成请求实体部分。攻击者通常在 Set-Cookie 时,注入换行符,控制请求传递的内容。
3、文件上传漏洞
上传文件是网页开发中的一个常见功能,如果不加处理,很容易就会造成攻击。
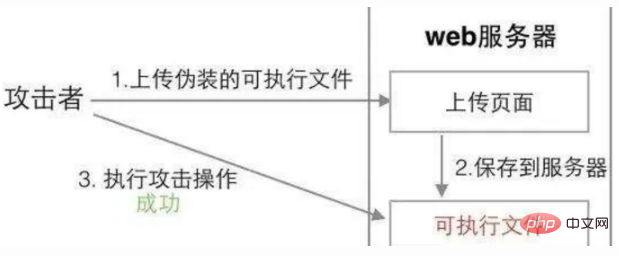
如图所示,攻击者上传了一个木马文件,并且通过返回的 URL 进行访问,就能控制服务器。
通常我们会控制上传文件的后缀名,但也不能完全解决问题,攻击者还可以通过以下方式进行攻击:
伪造正常文件
将木马文件伪装成正常的后缀名进行上传。
如果要避免这个问题,我们可以继续判断上传文件的文件头前 10 个字节。
Apache 解析方式是从后往前解析,直到找到一个认识的后缀名为止
如:上传一个 abc.php.rar.rar.rar 能绕过后缀名检查,但在执行时,被当成一个 php 文件进行执行。
IIS 会截断分号进行解析
如:abc.asp;xx.png 能绕过后缀名检查,但在执行时,被当成一个 asp 文件进行执行。
HTTP PUT 方法允许将文件上传到指定位置
通过 HTTP MOVE 方法,还能修改上传的文件名。
通过二者配合,就能先上传一个正常的后缀名,然后改为一个恶意的后缀名。
PHP CGI 路径问题
执行 http://abc.com/test.png/xxx.php 时,会把 test.png 当做 php 文件去解析。
如果用户正好是把一段恶意的 php 脚本当做一张图片进行上传,就会触发这个攻击。
1)文件上传漏洞防御
防御文件上传漏洞,可以从以下几点考虑:
将文件上传的目录设置为不可执行。判断文件类型检查 MIME Type,配置白名单。检查后缀名,配置白名单。使用随机数改写文件名和文件路径上传文件后,随机修改文件名,让攻击者无法执行攻击。单独设置文件服务器的域名单独做一个文件服务器,并使用单独的域名,利用同源策略,规避客户端攻击。通常做法是将静态资源存放在 CDN 上。
4、登录认证攻击
登录认证攻击可以理解为一种破解登录的方法。攻击者通常采用以下几种方式进行破解:
彩虹表
The attacker collects a large number of correspondences between plaintext and MD5 to crack the MD5 ciphertext to find the original text.
For the MD5 password in the rainbow table, we can add salt and perform secondary encryption to avoid being cracked.
Session Fixation attack
Use the application system’s SessionID fixed mechanism on the server to obtain authentication and authorization with the help of others using the same SessionID.
After the attacker fails to log in, the backend returns the SessionID. The attacker gives the SessionID to a normal user to log in. After the login is successful, the attacker can use this SessionID to pretend to be a normal user to log in. .
This problem can be avoided if the browser refreshes the SessionID every time you log in.
Session Keep Attack
Sometimes, for the sake of user experience, the backend will not let the user as long as the user is still alive. The Session is invalid.
An attacker can keep this Session alive by constantly making requests.
1) Login authentication defense method
Multi-factor authentication password is used as the first line of defense, but after the password verification is successful, we can continue to verify: dynamic password, Digital certificates, SMS verification codes, etc. to ensure user security. Since SMS and web pages are two completely independent systems, it is difficult for an attacker to obtain the SMS verification code and thus cannot carry out attacks.
5. Application layer denial of service attack
Application layer denial of service attack, also called DDOS attack, refers to the use of a large number of requests to cause resource overload, causing the server to become unavailable.
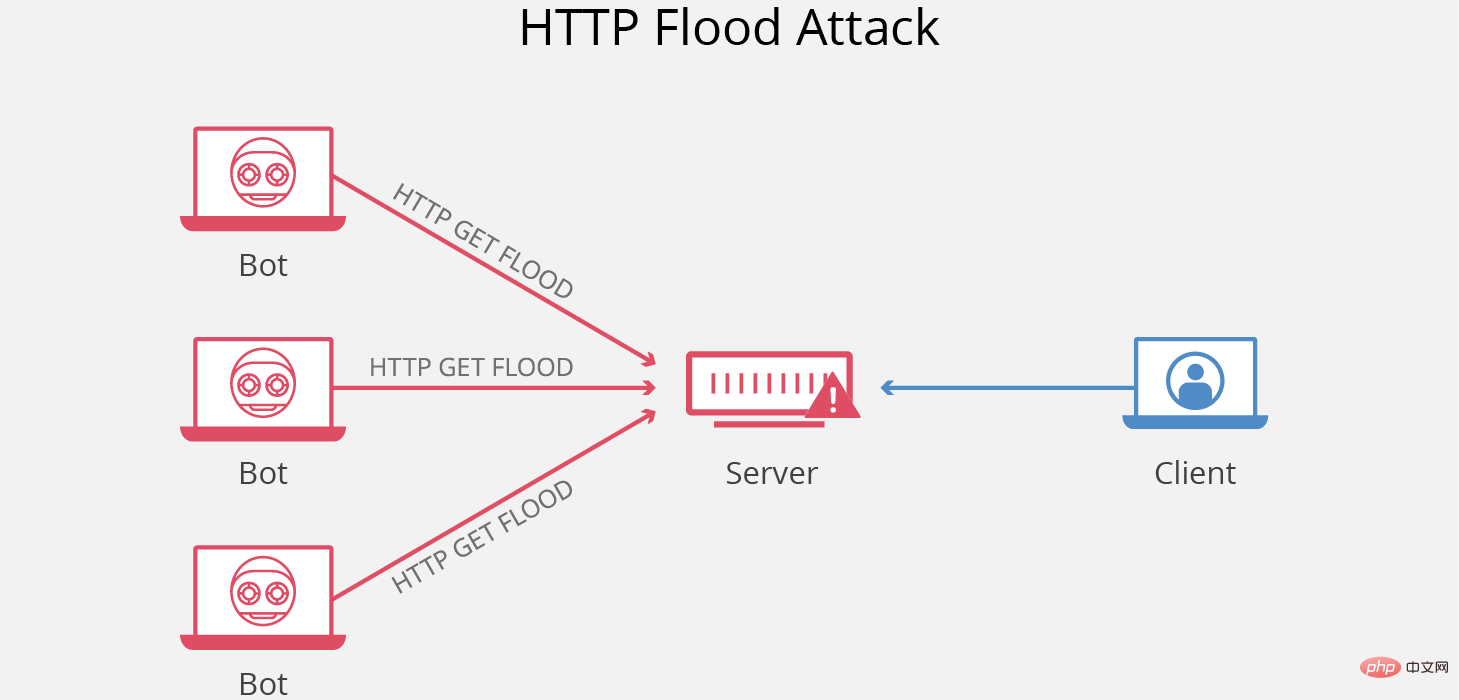
Usually there are the following DDOS attack methods:
SYN Flood flood attack
Use the HTTP 3-way handshake mechanism to consume server connection resources.
For example: an attacker initiates a large number of HTTP requests, but does not complete 3 handshakes, but only 2 handshakes. At this time, the server will continue to wait until timeout. At this time, the server will be busy processing a large number of garbage requests and has no time to take care of normal requests.
Slowloris attack
Sends HTTP request headers at a very slow rate, consuming server connection resources.
For example: an attacker sends a large number of HTTP requests, but each request header is sent very slowly, sending one character every 10 seconds. In order to wait for data, the server must not always maintain the connection, so As soon as it started, the number of server connections was quickly taken up.
HTTP POST DOS
When sending HTTP, specify a very large Content-Length and then send it at long intervals, consuming server connections resource.
CC attack
Continuously initiates requests for some very resource-consuming pages.
For example: Some pages in the page require a lot of calculations on the back end, or very time-consuming database queries. Under a large number of requests, the server's CPU, memory and other resources may be occupied.
Server Limit DOS
Inject an overly long cookie through XSS, causing the Request Header length to exceed the capacity of the web server. The server side This service will be denied.
ReDOS
Aiming at some defective regular expressions, a large number of requests are initiated and system resources are consumed.
1) Application layer denial of service attack defense
There is currently no particularly perfect solution for application layer denial of service attacks, but we can still make some optimizations.
Optimize the performance of the application code and rationally use caching solutions such as Redis and Memcache to reduce CPU resource usage. Optimize the network architecture and build load balancing on the backend. Static resources are managed using a CDN. Limiting the request frequency The server calculates the request frequency of all IP addresses and filters out abnormal IPs for disabling. You can use the LRU algorithm to cache the IP addresses of the first 1,000 requests. If an IP request frequency is too high, disable it.
In fact, the core idea of dealing with DDOS is to disable untrusted users and ensure that resources are used by normal users.
3. WebServer configuration security
When we deploy web applications, we often use Nginx, Apache, IIS, Tomcat, Jboss and other web servers. These servers themselves also have some security risks. , if configured improperly, it is easy to be attacked.
When configuring the Web server, you can refer to the following points:
1. Run the Web server with user permissions
Follow the principle of least privileges and run the Web server with the least privileges , restrict the permissions after being invaded.
2. Delete the visual backend
When running Web servers such as Tomcat and Jboss, a visual operation backend will be enabled by default, running on port 8080, and the first access will not be authenticated.
An attacker can use the visual background to remotely load a war package or upload a Trojan file for control, so we need to delete the visual platform.
3. Update the version in time
Major web servers will fix some vulnerabilities every once in a while, so remember to update the version in time.
Related recommendations: web server security
The above is the detailed content of How to keep the web safe. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1385
1385
 52
52
 Tips for turning off real-time protection in Windows Security Center
Mar 27, 2024 pm 10:09 PM
Tips for turning off real-time protection in Windows Security Center
Mar 27, 2024 pm 10:09 PM
In today's digital society, computers have become an indispensable part of our lives. As one of the most popular operating systems, Windows is widely used around the world. However, as network attack methods continue to escalate, protecting personal computer security has become particularly important. The Windows operating system provides a series of security functions, of which "Windows Security Center" is one of its important components. In Windows systems, "Windows Security Center" can help us
 How should the Java framework security architecture design be balanced with business needs?
Jun 04, 2024 pm 02:53 PM
How should the Java framework security architecture design be balanced with business needs?
Jun 04, 2024 pm 02:53 PM
Java framework design enables security by balancing security needs with business needs: identifying key business needs and prioritizing relevant security requirements. Develop flexible security strategies, respond to threats in layers, and make regular adjustments. Consider architectural flexibility, support business evolution, and abstract security functions. Prioritize efficiency and availability, optimize security measures, and improve visibility.
 PHP Microframework: Security Discussion of Slim and Phalcon
Jun 04, 2024 am 09:28 AM
PHP Microframework: Security Discussion of Slim and Phalcon
Jun 04, 2024 am 09:28 AM
In the security comparison between Slim and Phalcon in PHP micro-frameworks, Phalcon has built-in security features such as CSRF and XSS protection, form validation, etc., while Slim lacks out-of-the-box security features and requires manual implementation of security measures. For security-critical applications, Phalcon offers more comprehensive protection and is the better choice.
 Golang's browser support: building an interactive web
Apr 07, 2024 pm 04:03 PM
Golang's browser support: building an interactive web
Apr 07, 2024 pm 04:03 PM
Go builds interactive web applications that run in the browser. Steps: Create Go project and main.go file, add HTTP handler to display messages. Add forms using HTML and JavaScript for user input and submission. Add handling of POST requests in your Go application, receive user messages and return responses. Use FetchAPI to send POST requests and handle server responses.
 Security configuration and hardening of Struts 2 framework
May 31, 2024 pm 10:53 PM
Security configuration and hardening of Struts 2 framework
May 31, 2024 pm 10:53 PM
To protect your Struts2 application, you can use the following security configurations: Disable unused features Enable content type checking Validate input Enable security tokens Prevent CSRF attacks Use RBAC to restrict role-based access
 AI's new world challenges: What happened to security and privacy?
Mar 31, 2024 pm 06:46 PM
AI's new world challenges: What happened to security and privacy?
Mar 31, 2024 pm 06:46 PM
The rapid development of generative AI has created unprecedented challenges in privacy and security, triggering urgent calls for regulatory intervention. Last week, I had the opportunity to discuss the security-related impacts of AI with some members of Congress and their staff in Washington, D.C. Today's generative AI reminds me of the Internet in the late 1980s, with basic research, latent potential, and academic uses, but it's not yet ready for the public. This time, unchecked vendor ambition, fueled by minor league venture capital and inspired by Twitter echo chambers, is rapidly advancing AI’s “brave new world.” The "public" base model is flawed and unsuitable for consumer and commercial use; privacy abstractions, if present, leak like a sieve; security structures are important because of the attack surface
 Implementing Machine Learning Algorithms in C++: Security Considerations and Best Practices
Jun 01, 2024 am 09:26 AM
Implementing Machine Learning Algorithms in C++: Security Considerations and Best Practices
Jun 01, 2024 am 09:26 AM
When implementing machine learning algorithms in C++, security considerations are critical, including data privacy, model tampering, and input validation. Best practices include adopting secure libraries, minimizing permissions, using sandboxes, and continuous monitoring. The practical case demonstrates the use of the Botan library to encrypt and decrypt the CNN model to ensure safe training and prediction.
 Which wallet is safer for SHIB coins? (Must read for newbies)
Jun 05, 2024 pm 01:30 PM
Which wallet is safer for SHIB coins? (Must read for newbies)
Jun 05, 2024 pm 01:30 PM
SHIB coin is no longer unfamiliar to investors. It is a conceptual token of the same type as Dogecoin. With the development of the market, SHIB’s current market value has ranked 12th. It can be seen that the SHIB market is hot and attracts countless investments. investors participate in investment. In the past, there have been frequent transactions and wallet security incidents in the market. Many investors have been worried about the storage problem of SHIB. They wonder which wallet is safer for SHIB coins at the moment? According to market data analysis, the relatively safe wallets are mainly OKXWeb3Wallet, imToken, and MetaMask wallets, which will be relatively safe. Next, the editor will talk about them in detail. Which wallet is safer for SHIB coins? At present, SHIB coins are placed on OKXWe




