Introducing the repair of IIS short file name leak vulnerability

1. What is IIS
Internet Information Services (IIS, formerly known as Internet Information Server) Internet Information Services is a Microsoft The scalable web server provided by the company supports HTTP, HTTP/2, HTTPS, FTP, FTPS, SMTP and NNTP, etc. Initially used in the Windows NT series, it was later built into Windows 2000, Windows XP Professional, Windows Server 2003 and subsequent versions, but there is no IIS on the Windows XP Home version. IIS is currently only available for Windows systems and not for other operating systems.
According to data from Netcraft in February 2017, IIS had a market share of 10.19% among the "Millions of Busiest Websites", becoming the third largest network server in the world , behind Apache at 41.41% and Nginx at 28.34%. Currently, the popular Windows versions have the IIS service installed by default. However, the security of IIS has been criticized by the industry. Once a high-risk vulnerability appears in IIS, the threat will be very serious.
Recommended (free): iis
Before touching the IIS vulnerability, let’s first understand the default built-in IIS version under different Windows systems. In order to better understand and distinguish the scope of impact of IIS vulnerabilities:
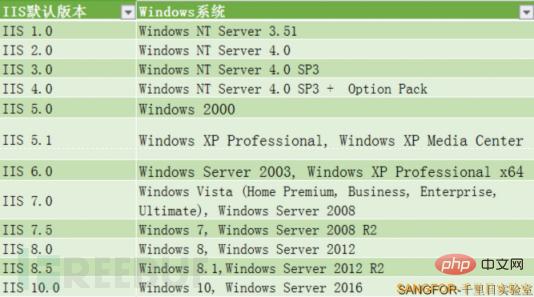 Figure 1 Default IIS version of each Windows version
Figure 1 Default IIS version of each Windows version
2. Complete list of IIS vulnerabilities
Qianlimu Lab has collected IIS-related vulnerabilities in the past fifteen years. There are a total of 39 medium and high-risk vulnerabilities, including the (MS15-034) HTTP.sys remote code execution vulnerability that broke out in 2015 and the 2016 The (MS16-016) WebDAV privilege escalation vulnerability is particularly widespread.
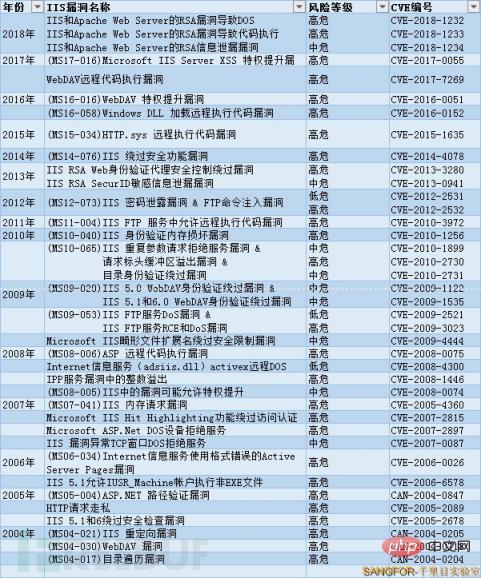
Figure 2 A complete list of IIS vulnerabilities in the past 15 years
After reading the above IIS vulnerabilities in the past ten years, you may ask, why didn’t you see it? What about the protagonist of this article, "IIS Short File Vulnerability"? ! Before understanding the IIS vulnerability family, we first learn about some features of IIS under Windows through IIS short files.
3. IIS short file
1. The origin of the IIS short file vulnerability
Microsoft IIS short file/folder The name information leak was first discovered by Soroush Dalili of the Vulnerability Research Team on August 1, 2010, and the vendor (Microsoft Corporation) was notified on August 3, 2010. Microsoft responded on December 1, 2010 and January 4, 2011 that the next version would be fixed. On June 29, 2012, this vulnerability was publicly disclosed (medium risk).
This vulnerability is actually caused by the old DOS 8.3 Name Convention (SFN) tilde (~) tilde in HTTP requests. It allows remote attackers to expose file and folder names under the web root (which should not be accessible). An attacker can find important files that are usually not directly accessible from the outside and obtain information about the application infrastructure.
Information disclosure caused by Microsoft IIS tilde is the most common medium-risk vulnerability on the world's networks. This problem has been around since at least 1990, but has proven difficult to detect, difficult to solve, or easy to ignore entirely.
2. IIS short file vulnerability scope and harm
2.1 Affected versions:
##IIS 1.0, Windows NT 3.51(Above data source:IIS 3.0, Windows NT 4.0 Service Pack 2
IIS 7.5, Windows 2008 (Classic Pipeline Mode) Note: IIS is not affected when using .Net Framework 4
IIS 4.0, Windows NT 4.0 Option Pack
IIS 5.0, Windows 2000
IIS 5.1, Windows XP Professional and Windows XP Media Center Edition
IIS 6.0, Windows Server 2003 and Windows XP Professional x64 Edition
IIS 7.0, Windows Server 2008 and Windows Vista
IIS 7.5, Windows 7 (remotely enabledor no web.config)
https://www.securityfocus.com/archive/1/523424)
It has been verified that the above affected scope is mainly for the HTTP GET method, and requires the installation of ASP.NET applications at the same time. The discoverer of this vulnerability disclosed again in 2014: During testing of IIS 7.5 (Windows 2008 R2) and IIS 8.0 (Windows 2012), when OPTIONS is used instead of the GET method, if the short file name in the request exists, IIS A different error message will be returned. Taking advantage of this feature, attackers can implement file or directory scanning based on short file names in the latest IIS version. Currently, IIS supports six HTTP methods for short file name guessing: DEBUG, OPTIONS, GET, POST, HEAD, and TRACE. Verified by Qianlimu Laboratory, the short file names of IIS 8.0, IIS 8.5, and IIS 10.0 File names can be guessed successfully through the OPTIONS and TRACE methods. Therefore, the above affected versions need to be added with the following versions:IIS 8.0, Windows 8, Windows Server 2012IIS 8.5, Windows 8.1, Windows Server 2012 R2IIS 10.0, Windows 10, Windows Server 2016
It can be seen that all versions of IIS have the problem of short file name leakage, and Microsoft seems to have ignored this problem. It can be seen from Microsoft's reply to the discoverer of the vulnerability that the IIS short file vulnerability does not meet security update standards, and it needs to determine when it will be resolved in the next logical version.
2.2 Vulnerability hazards:
2.2.1 Using the "~" character to guess and expose short file/folder names (main hazard)
Windows Support for generating MS-DOS-compatible (short) filenames in 8.3 format to allow MS-DOS or 16-bit Windows-based programs to access these files. Enter the IIS website root directory C:\inetpub\wwwroot under cmd and enter "dir /x" to see the effect of the short file name:
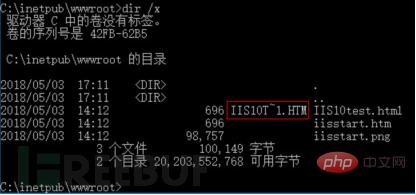
Figure 3 IIS short file Name
The picture above is the default site root directory of IIS 10.0 built in Windows 10. iisstart.htm and iisstart.png are the default files of the website. The length of the file name prefix characters does not reach 9 characters, so there is no short file name. IIS10test.html is a website file added manually. The file name prefix character length reaches 9 characters, and the corresponding short file name is IIS10T~1.HTM. According to this feature, we can indirectly access its corresponding file by accessing the short file name.
Since the length of the short file name is fixed (xxxxxx~xxxx), the attacker can directly brute force the short file name to access the corresponding file.
For example, there is a database backup file backup_20180101.sql, and its corresponding short file name is backup~1.sql. Therefore, the attacker can download the file by brute force cracking backup~1.sql without cracking the complete file name.
IIS short file names have the following characteristics:
1. Only the first six characters are displayed directly, and subsequent characters are designated by ~1. The number 1 can also be incremented if there are multiple files with similar file names (the first 6 digits of the name must be the same, and the first 3 digits of the suffix name must be the same);
2. The suffix name can only have a maximum of 3 digits, which is redundant are truncated, long files with more than 3 characters will generate short file names;
3. All lowercase letters are converted to uppercase letters;
4. Long file names contain multiple ". ”, use the last “.” in the file name as the short file name suffix;
5. The long file name prefix/folder name character length conforms to the range of 0-9 and Aa-Zz and needs to be greater than or equal to 9 characters. A short file name will be generated. If it contains spaces or other special characters, a short file will be generated regardless of the length;
We can use the GET method to violently enumerate short file names under IIS with .net enabled. The reason is that the attacker uses wildcard characters "*" and "?" to send a request to IIS. When IIS receives a file path containing a "~" request, its response is different, that is, the returned HTTP status code and error message different. Based on this feature, an available or unavailable file can be distinguished based on the HTTP response. As shown in the figure below, the information returned by different IIS versions is different:
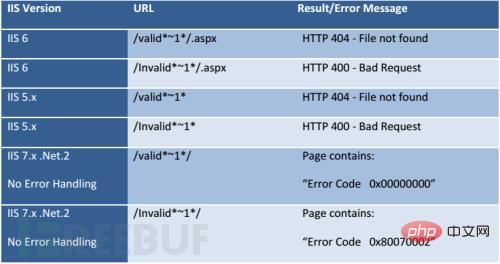
Figure 4 IIS 5.0 ~ IIS 7.X short file guessing HTTP response information
The picture is an illustration of the legal and illegal IIS short file guessing response information given by Soroush Dalili, the discoverer of this vulnerability, in his research report:
Accessing an existing short file name constructed will return 404;
Accessing a constructed short file name that does not exist will return 400;
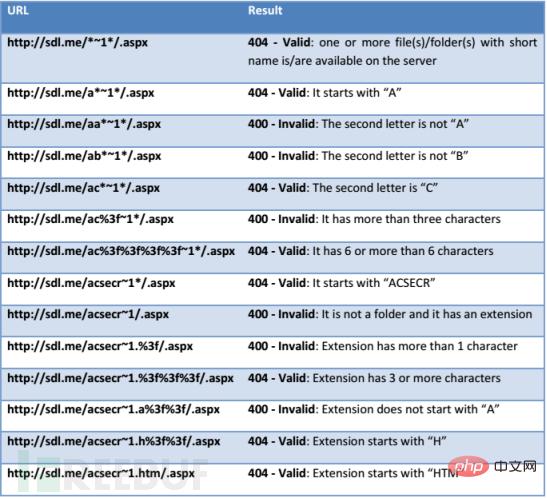
Figure 5 Using IIS status code guessing process
The above method is to use the GET method to guess repeatedly in a lower version of IIS ASP.NET environment until the short file name is guessed.
However, Qianlimu Laboratory verified in the real environment that in higher versions of IIS (such as: IIS 8.0/IIS 8.5/IIS 10.0), even if asp.net is not installed, through the OPTIONS and TRACE methods You can guess successfully. The HTTP status code types returned by these two methods are slightly different from the above screenshots, but they are another way to use them.
2.2.2 .Net Framework Denial of Service Attack (Side Hazard)
According to research by Soroush Dalili, if an attacker sends an illegal .Net file in the folder name request, .NeFramework will recursively search all root directories, consuming website resources and causing DOS problems. Microsoft believes that this hazard is recoverable DOS and will be modified in subsequent SP versions, so it will not be discussed here.
3. IIS Short File Vulnerability Recurrence and Exploitation
##3.1 IIS Short File Vulnerability Recurrence
3.1.1 Vulnerability environment constructionInstall the default IIS 10.0 based on Win 10 (APS.NET is not installed)IIS short file vulnerability scanning Java program (Java environment needs to be configured Variables)3.1.2 Vulnerability environment debugging preparationAfter IIS is successfully installed, the intpub directory will be generated in the C drive directory by default. The root directory of the website is located in C:\inetpub\ wwwroot. At this time, check whether there is a short file name in the root directory:
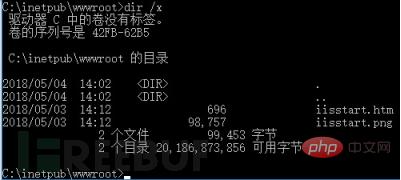
As can be seen from the above figure, the default IIS 10.0 website root directory does not have short file names, only default htm and png files, and the name length does not meet the requirements for generating short files. The following uses the IIS short file scanner to detect whether there is a short file information leakage vulnerability:
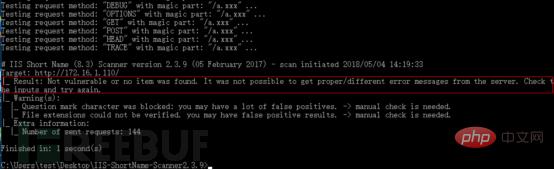
3.1.3 Vulnerability environment reproduction
Manually create website long files Name "IIS10test.html", automatically generate the corresponding short file name "IIS10T~1.HTM"
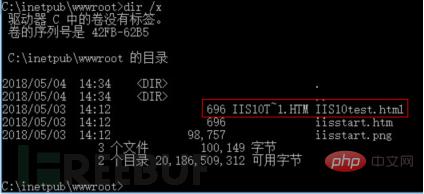
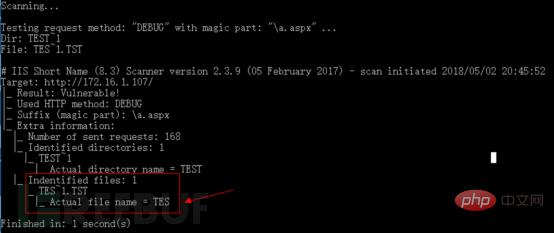
Use the IIS short file scanner to scan again, and the scan found that there is a short file vulnerability. , and successfully guessed the short file name through the HTTP OPTIONS method: IIS10T.HTM
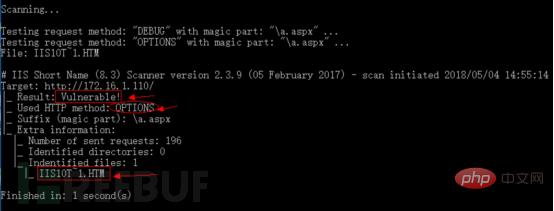
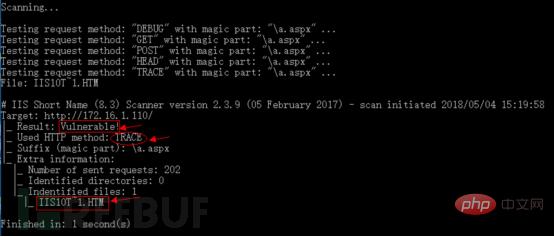
TRACE method can also successfully guess the short file name.
3.1.4 IIS vulnerability OPTIONS and TRACE method guessing analysisOPTIONS method guessing analysisBecause the above OPTIONS method requested 196 times to guess the short file name, If the guess is successful, 404 will be returned. If the guess is failed, 200 will be returned. There are many failed combinations, so the following mainly analyzes how the request with successful 404 guess can obtain the short file name IIS10T.HTM through the OPTIONS method. As shown below: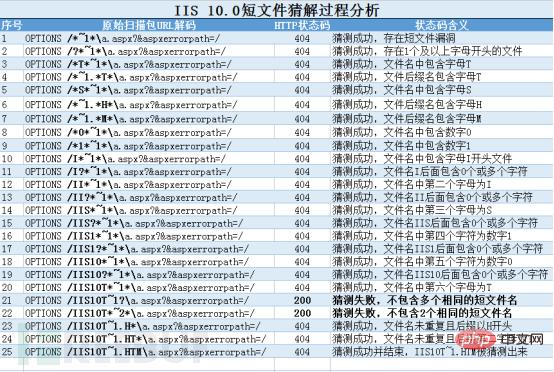
501 (not executed).
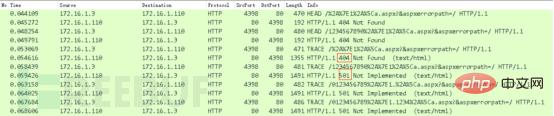 3.2 IIS short file vulnerabilityExploit
3.2 IIS short file vulnerabilityExploit
IIS short file vulnerability limitations
This vulnerability There are several limitations: 1) This vulnerability can only determine the first 6 characters. If the following characters are too long or contain special characters, it is difficult to guess; 2) If The file name itself is too short (no short file name) and cannot be guessed; 3) If the first 6 digits of the file name contain spaces, the short file name in the 8.3 format will be supplemented and does not match the real file name;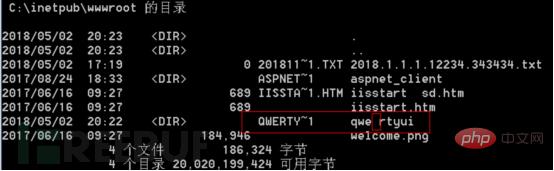
4) If the first 6 characters of the folder name are dotted with ".", the scanner will think it is a file instead of a folder, and eventually a false alarm will appear;
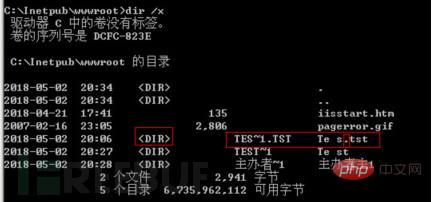
5) Chinese file names are not supported, including Chinese files and Chinese folders. One Chinese character is equivalent to two English characters, so more than 4 Chinese characters will generate a short file name, but IIS does not support Chinese guessing.
5. IIS short file vulnerability solution
5.1 General vulnerability repair solution
1) CMD closes NTFS 8.3 files Format support
Example: (1 means off, 0 means on)
Windows Server 2008 R2:
Windows Server 2003:Query whether the short file name function is turned on:fsutil 8##dot3name query
Turn off this function:fsutil 8dot3name set 1
Turn off this feature:The shutdown commands of different systems are slightly different. This function is enabled by default and does not need to be enabled for most users. 2) Modify the registry to disable the short file name functionShortcut key Win R to open the command window, enter regedit to open the registry windowFind the path:HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\FileSystem, set the value of NtfsDisable8dot3NameCreation to 1, 1 means not to create a short file name formatAfter the modification is completed, you need to restart the system to take effectNote: This method can only prohibit the creation of NTFS8.3 format file names. The short file names of existing files cannot be removed and need to be copied again before they disappear. The following two methods are only suitable for mitigating the GET method, other methods can still be guessed. 3) Turn off the Web service extension - ASP.NET4) Upgrade netFramework to version 4.0 or abovefsutil behavior set disable8dot3 1
The above is the detailed content of Introducing the repair of IIS short file name leak vulnerability. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 How to install nginx1.10.1 reverse proxy in Windows to access IIS website
May 23, 2023 pm 05:40 PM
How to install nginx1.10.1 reverse proxy in Windows to access IIS website
May 23, 2023 pm 05:40 PM
First, go to the official website to download the software package and unzip it. It is best not to have the path problem with the Chinese nginx configuration. Under Windows, the file path can be separated by "\", "\\", or "/". symbol. But "\" is the most likely to cause problems, so try to avoid using it. Do not add path, otherwise it will cause an error. The config file path cannot be found. For example, I decompressed the cmd command on the e drive to locate the folder where nginx.exe is located, cde:\worksoftware\nginx-1.10.1 and then execute it. First ensure the nginx.conf file There is no problem with the configuration. In fact, the most important and main job of nginx is the configuration file, and there is nothing else.
 Can iis be used on linux?
Mar 23, 2023 am 09:24 AM
Can iis be used on linux?
Mar 23, 2023 am 09:24 AM
iis cannot be used on Linux because iis is a basic Internet service provided by Microsoft based on running Microsoft Windows. It was developed under the Windows operating system platform, so it is restricted to run under the Windows operating system.
 Process cannot access file error fix on Windows 11/10
May 12, 2023 pm 07:10 PM
Process cannot access file error fix on Windows 11/10
May 12, 2023 pm 07:10 PM
As we all know, when any file is in use, no other process can access/change it. In this case, when a process attempts to open a file, the operating system locks the file to prevent it from being modified by another process. “The process cannot access the file because it is in use by another process” is such an error message observed by many users on their Windows computers. This error is known to occur in different versions of WindowsOS and WindowsServer. Usually, this error message is observed during using Netsh command on the user’s Windows PC. Another situation where this error occurs is when trying to run the Internet Information Services (IIS) M
 How to solve the problem when the php station uses iis with garbled characters but apache is fine?
Mar 23, 2023 pm 02:48 PM
How to solve the problem when the php station uses iis with garbled characters but apache is fine?
Mar 23, 2023 pm 02:48 PM
When using PHP for website development, you may encounter character encoding issues. Especially when using different web servers, you may find that IIS and Apache handle character encoding differently. When you use IIS, you may find that garbled characters appear when using UTF-8 encoding; but when using Apache, everything works fine without any problems. How should this situation be resolved?
 How to open iis application pool
Apr 09, 2024 pm 07:48 PM
How to open iis application pool
Apr 09, 2024 pm 07:48 PM
To open an application pool in IIS: 1. Open IIS Manager; 2. Navigate to the "Application Pools" node; 3. Right-click the target application pool and select "Manage"; 4. Click "Advanced Settings" Tab; 5. Application pool configuration can be viewed and modified here.
 How to solve iis cannot start
Dec 06, 2023 pm 05:07 PM
How to solve iis cannot start
Dec 06, 2023 pm 05:07 PM
Solutions to iis failure to start: 1. Check the integrity of the system files; 2. Check the port occupancy; 3. Start related services; 4. Reinstall IIS; 5. Reset the Windows system; 6. Check the metabase file; 7. Check file permissions; 8. Update the operating system and applications; 9. Avoid installing too many unnecessary software; 10. Back up important data regularly. Detailed introduction: 1. Check the integrity of system files, run system file checking tools, check the integrity of system files, etc.
 iis cannot start solution
Oct 24, 2023 pm 03:04 PM
iis cannot start solution
Oct 24, 2023 pm 03:04 PM
Solution: 1. Check whether the IIS service has been installed; 2. Check dependent services; 3. Check port conflicts; 4. Check configuration files and permissions; 5. Re-register IIS related components; 6. Check log files.
 Can iis log files be deleted? How to delete them?
Apr 09, 2024 pm 07:45 PM
Can iis log files be deleted? How to delete them?
Apr 09, 2024 pm 07:45 PM
Yes, it is possible to delete IIS log files. Removal methods include selecting the website or application pool through IIS Manager and deleting the log file in the Log Files tab. Use a command prompt to go to the log file storage directory (usually %SystemRoot%\System32\LogFiles\W3SVC1) and use the del command to delete the log file. Use third-party tools such as Log Parser to automatically delete log files.






