What is the cmd command to obtain administrator rights?
cmd The command to obtain administrator rights is "runas /user:administrator cmd". The method of use is: first click "Run" and enter "cmd" in the input field; then enter "runas /user in the window :administrator cmd" and password.

The operating environment of this tutorial: Windows 7 system, Dell G3 computer.
Open the computer search box/or click Run and enter cmd;
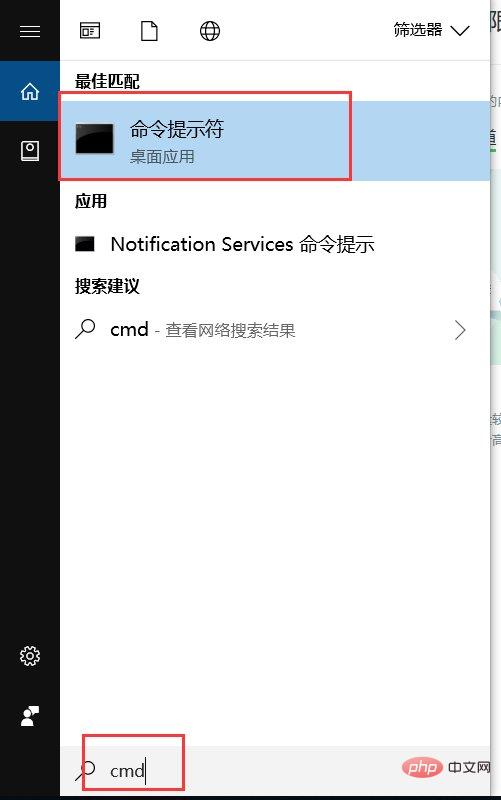
Click the command prompt;
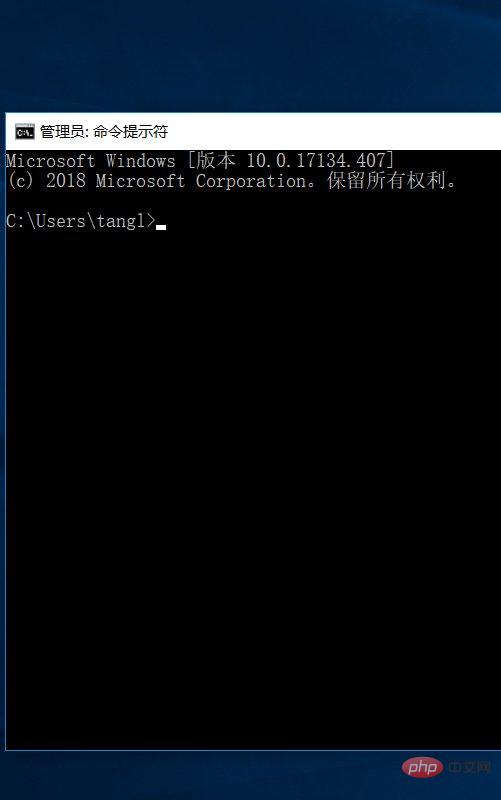
Enter runas /user:administrator cmd in the command prompt;
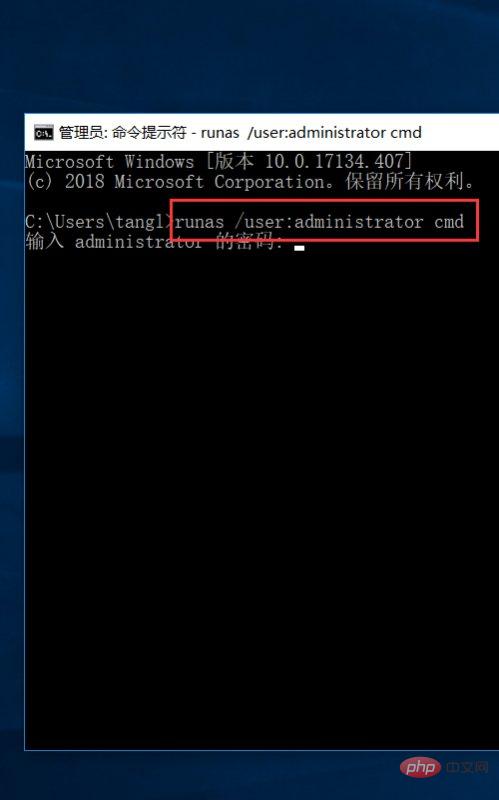
Enter the password to enter the administrator’s cmd permissions;
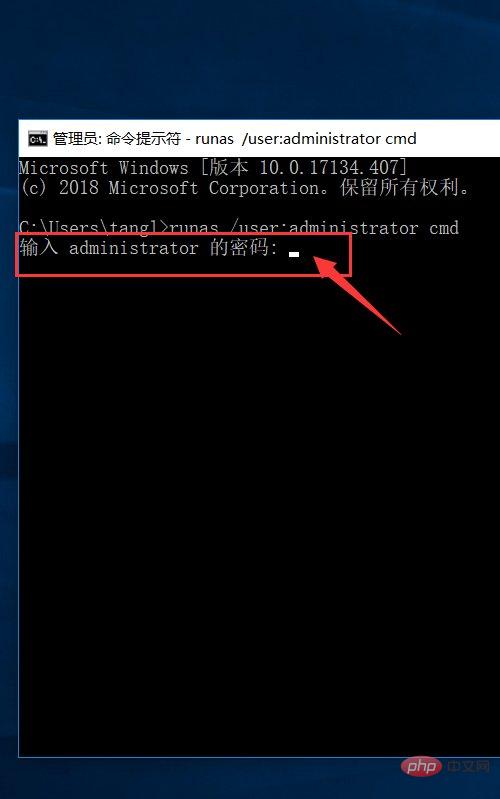
But here you need to know the password of the administrator. It is also possible not to use the administrator user here. You can also use other users in the same management group to start cmd. The permissions are also administrators. For example, there is a user named: abc in the administrators. Then you can use the command: runas / user:abc cmd. At this time, just enter the login password of user abc.
For more computer-related knowledge, please visit the FAQ column!
The above is the detailed content of What is the cmd command to obtain administrator rights?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1386
1386
 52
52
 How to get BitLocker recovery key from CMD without Microsoft account
Feb 19, 2024 pm 09:00 PM
How to get BitLocker recovery key from CMD without Microsoft account
Feb 19, 2024 pm 09:00 PM
This guide will explain how to obtain a BitLocker recovery key to restore access to encrypted data if necessary. BitLocker is a security feature of Windows devices used to protect data from unauthorized access. Recovery keys are a backup method if you can't access your data through regular means. You can obtain a 48-digit BitLocker recovery key without a Microsoft account or via CMD, ensuring you are always able to access and recover your important data. How to get BitLocker recovery key from CMD without Microsoft account? Follow these suggestions to obtain a BitLocker recovery key: Using Command Prompt click Start, search for cmd and click to manage
 How to run SUDO commands in Windows 11/10
Mar 09, 2024 am 09:50 AM
How to run SUDO commands in Windows 11/10
Mar 09, 2024 am 09:50 AM
The sudo command allows users to run commands in elevated privilege mode without switching to superuser mode. This article will introduce how to simulate functions similar to sudo commands in Windows systems. What is the Shudao Command? Sudo (short for "superuser do") is a command-line tool that allows users of Unix-based operating systems such as Linux and MacOS to execute commands with elevated privileges typically held by administrators. Running SUDO commands in Windows 11/10 However, with the launch of the latest Windows 11 Insider preview version, Windows users can now experience this feature. This new feature enables users to
 How to check the MAC address of the network card in Win11? How to use the command to obtain the MAC address of the network card in Win11
Feb 29, 2024 pm 04:34 PM
How to check the MAC address of the network card in Win11? How to use the command to obtain the MAC address of the network card in Win11
Feb 29, 2024 pm 04:34 PM
This article will introduce readers to how to use the command prompt (CommandPrompt) to find the physical address (MAC address) of the network adapter in Win11 system. A MAC address is a unique identifier for a network interface card (NIC), which plays an important role in network communications. Through the command prompt, users can easily obtain the MAC address information of all network adapters on the current computer, which is very helpful for network troubleshooting, configuring network settings and other tasks. Method 1: Use "Command Prompt" 1. Press the [Win+X] key combination, or [right-click] click the [Windows logo] on the taskbar, and in the menu item that opens, select [Run]; 2. Run the window , enter the [cmd] command, and then
 How to turn off Bitlocker encryption using CMD at the command prompt
Jun 19, 2024 am 11:33 AM
How to turn off Bitlocker encryption using CMD at the command prompt
Jun 19, 2024 am 11:33 AM
Enter the following command in the administrator command prompt to turn off manage-bde-offC: But sometimes the following prompt appears: Error - This volume stores one or more external keys that can automatically unlock other volumes. This type of key must first be deleted before this volume can be unlocked. At this time, you need to execute the following command first: (If the system partition is not C, change the drive letter below) manage-bde-autounlock-ClearAllKeysc: Error 2: This operation cannot be performed because the volume is locked. manage-bde-unlockc:-rp123456789012345678901234567890123456789012345678 Note:
 Where is hyperv enhanced session mode? Tips for enabling or disabling Hyper-V enhanced session mode using commands in Win11
Feb 29, 2024 pm 05:52 PM
Where is hyperv enhanced session mode? Tips for enabling or disabling Hyper-V enhanced session mode using commands in Win11
Feb 29, 2024 pm 05:52 PM
In Win11 system, you can enable or disable Hyper-V enhanced session mode through commands. This article will introduce how to use commands to operate and help users better manage and control Hyper-V functions in the system. Hyper-V is a virtualization technology provided by Microsoft. It is built into Windows Server and Windows 10 and 11 (except Home Edition), allowing users to run virtual operating systems in Windows systems. Although virtual machines are isolated from the host operating system, they can still use the host's resources, such as sound cards and storage devices, through settings. One of the key settings is to enable Enhanced Session Mode. Enhanced session mode is Hyper
 Super practical! Sar commands that will make you a Linux master
Mar 01, 2024 am 08:01 AM
Super practical! Sar commands that will make you a Linux master
Mar 01, 2024 am 08:01 AM
1. Overview The sar command displays system usage reports through data collected from system activities. These reports are made up of different sections, each containing the type of data and when the data was collected. The default mode of the sar command displays the CPU usage at different time increments for various resources accessing the CPU (such as users, systems, I/O schedulers, etc.). Additionally, it displays the percentage of idle CPU for a given time period. The average value for each data point is listed at the bottom of the report. sar reports collected data every 10 minutes by default, but you can use various options to filter and adjust these reports. Similar to the uptime command, the sar command can also help you monitor the CPU load. Through sar, you can understand the occurrence of excessive load
 Artifact in Linux: Principles and Applications of eventfd
Feb 13, 2024 pm 08:30 PM
Artifact in Linux: Principles and Applications of eventfd
Feb 13, 2024 pm 08:30 PM
Linux is a powerful operating system that provides many efficient inter-process communication mechanisms, such as pipes, signals, message queues, shared memory, etc. But is there a simpler, more flexible, and more efficient way to communicate? The answer is yes, that is eventfd. eventfd is a system call introduced in Linux version 2.6. It can be used to implement event notification, that is, to deliver events through a file descriptor. eventfd contains a 64-bit unsigned integer counter maintained by the kernel. The process can read/change the counter value by reading/writing this file descriptor to achieve inter-process communication. What are the advantages of eventfd? It has the following features
 What is the correct way to restart a service in Linux?
Mar 15, 2024 am 09:09 AM
What is the correct way to restart a service in Linux?
Mar 15, 2024 am 09:09 AM
What is the correct way to restart a service in Linux? When using a Linux system, we often encounter situations where we need to restart a certain service, but sometimes we may encounter some problems when restarting the service, such as the service not actually stopping or starting. Therefore, it is very important to master the correct way to restart services. In Linux, you can usually use the systemctl command to manage system services. The systemctl command is part of the systemd system manager



