Operation and Maintenance
Operation and Maintenance
 Windows Operation and Maintenance
Windows Operation and Maintenance
 How to solve the problem of 100% CPU usage
How to solve the problem of 100% CPU usage
How to solve the problem of 100% CPU usage
Solution to 100% cpu usage: first find the specific process that affects the high CPU usage; then check whether the process that affects the high CPU usage is normal; finally classify and process it.

#The operating environment of this article: Windows Server 2008 system, Dell G3 computer.
How to solve the problem of 100% cpu usage?
Overview
This article mainly introduces the troubleshooting and solutions to the problem of high CPU usage in Windows instances.
Details
Alibaba Cloud reminds you:
- If you perform risky operations such as modifying or changing the instance or data, be sure to pay attention to the content of the instance. disaster and fault tolerance to ensure data security.
- If you make configuration and data modifications to instances (including but not limited to ECS, RDS), etc., it is recommended to create snapshots in advance or enable RDS log backup and other functions.
- If you have authorized or submitted security information such as login account and password on the Alibaba Cloud platform, it is recommended that you modify it in time.
This article mainly introduces the following steps.
Positioning problem. Find the specific process causing high CPU usage.
Analysis and processing. Check whether the processes causing high CPU usage are normal and classify them for processing.
- For normal processes: You need to optimize the program or upgrade the server configuration.
- For abnormal processes: You can manually check and kill the process, or you can use third-party security tools to check and kill the process.
Operation example. Introduce the specific troubleshooting and solution process.
More information. Introduce the use of troubleshooting tools.
Locating the problem
Microsoft has multiple tools to locate the problem of excessive CPU usage, such as Task Manager, Resource Monitor (Resource Monitor), Performance Monitor (Performance Monitor), Process Explorer, Xperf (Windows server 2008 and later), KernRate (Windows server 2003), grab the system Full Memory Dump for inspection. In the case of heavy traffic, you can also use Wireshark to capture network packets for a period of time and analyze traffic usage.
Tips: For Windows Server 2008 and above systems, the resource monitor that comes with the system is usually used to monitor the CPU.
Click the Start menu at the bottom of the desktop and select Run.
After opening the run box, enter
perfmon -resin the box and click OK.
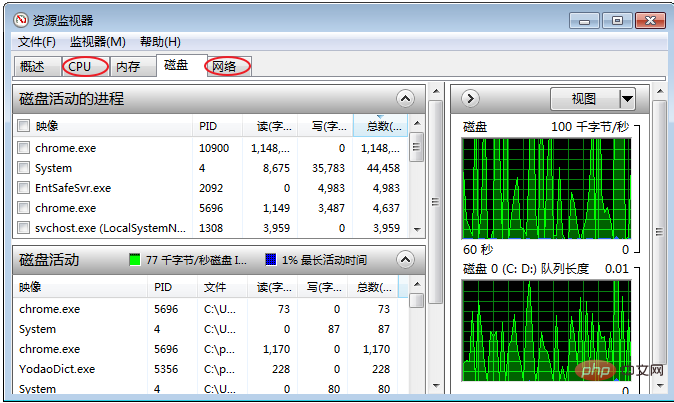
In the resource monitor page, check whether the CPU usage of each process is too high The phenomenon.
For processes that occupy higher resources, check the corresponding process ID and program of the process name.
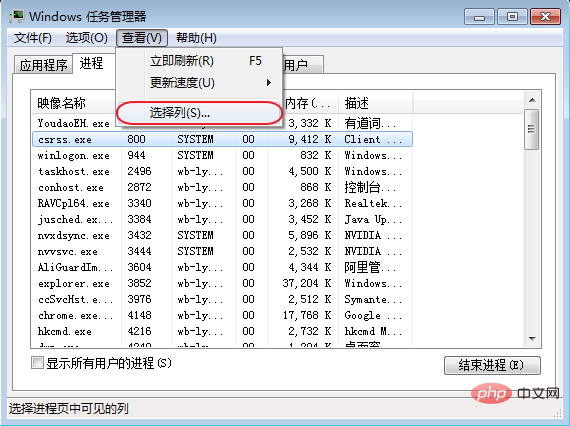
- After locating the process ID, use the task manager to determine whether the program is abnormal and locate the specific location of the program.
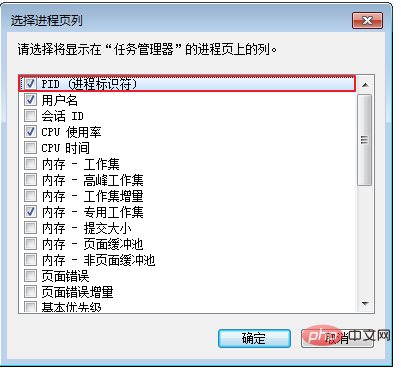
- Before locating the abnormal process, you need to click View (V)> Select Column (S) in the Task Manager.

- Select PID (Process Identifier) in the pop-up box and click OK.

- #In the process page of the task manager, the PID item will be added. Click PID and sort to find the abnormal process previously viewed by the resource monitor. Right-click the process name and select Open File Location to check whether the process is a malicious program.
Analysis and processing
Analysis and processing of excessive CPU usage
You need to determine whether the process that affects the high CPU usage is a normal process or an abnormal process. and classified for processing.
Analysis and processing of excessive normal usage
Under normal circumstances, when customers frequently access the business, or due to Windows' own services (update services, etc.), high network traffic and CPU may be occupied . For high CPU usage caused by normal processes, please troubleshoot one by one in the following order.
Tips: It is recommended that the memory configuration of Windows Server 2008 or Windows Server 2012 instances be 2G or above.
Check whether there is any Windows Update behavior in the background.
It is recommended to install anti-virus software on the server for anti-virus. If you have installed anti-virus software, please check whether the anti-virus software performs scanning operations in the background when the CPU is high. If possible, please upgrade the anti-virus software to the latest version, or delete the anti-virus software.
Check whether the application in the ECS has a large amount of disk access, network access behavior or high computing requirements. Try to increase instance specifications and use more cores or memory specifications to solve resource bottlenecks, such as upgrading configurations.
If your server configuration is high, there is no point in upgrading the configuration. In terms of architecture, it does not mean that the higher the server configuration, the better. At this time, you need to try to separate applications and optimize related programs at the same time. Example instructions are as follows.
Solution: Try application separation and use different servers to host different applications. For example, the database is completely hosted through RDS, which reduces the resource consumption of the server itself and the large number of calls within the server. In terms of program optimization, you can make adjustments according to your own configuration, such as adjusting the number of connections and cache configurations, as well as various parameters for Web and database calls, etc.
Analysis and Processing of Abnormally High Usage
For abnormally high CPU usage, it may be caused by malicious viruses and Trojans. Sometimes third-party malicious programs may use the operating system's svchost.exe or Tcpsvcs.exe to disguise themselves, causing high CPU usage. You need to manually detect and kill abnormal processes.
Tips: If you cannot determine whether the process is a virus or Trojan horse, it is recommended to search the process name online and confirm it. In addition, it is recommended that you create a snapshot in advance to complete the backup before deleting the process.
- Use commercial anti-virus software, or use Microsoft's free security tool Microsoft Safety Scanner to scan and anti-virus in safe mode. The tool link is as follows.
- https://www.microsoft.com/security/scanner/zh-cn/default.aspx
Run Windows Update to install the latest Microsoft Security patches.
Use MSconfig to disable all non-Microsoft service drivers and check whether the problem occurs again. For specific operations, please refer to How to perform a clean boot in Windows systems.
If the server or site suffers a DDoS attack or CC attack, a large number of access demands will be generated in a short period of time. You can log in to Cloud Security Center to check whether the protection threshold for DDoS attacks in Cloud Shield has been adjusted, and verify whether CC protection is enabled. If the attack does not trigger the threshold and Cloud Shield is not cleaned, you can contact after-sales service to help start cleaning.
Operation example
Possible reasons for high CPU usage are as follows.
- Virus Trojan invasion.
- Run third-party anti-virus software.
- Application exceptions, driver exceptions, high I/O usage or high interrupt processing applications.
Tip: When using a 1-core 1GB instance of Windows Server 2012, the Windows Update service will automatically update, and the CPU usage of the instance will suddenly increase. High, this is normal.
Solution
Tips: This article quotes a large number of Microsoft’s official documents and tool links. The copyright and ownership rights belong to Microsoft. Please pay full attention to them. Consider the problems that may arise from Microsoft Windows product iterations or documentation that is not updated in a timely manner.
#When the CPU usage is high, check whether the Windows Update process is executing in the background.
Check whether the anti-virus software is performing scanning operations in the background. You can upgrade the anti-virus software to the latest version, or delete the anti-virus software.
Click Run, then enter MSCONFIG, disable all non-Microsoft built-in service drivers, and then check whether the problem occurs again. Relevant reference documents are as follows.
Use commercial anti-virus software or Microsoft Security Scanner to safely Scan for viruses in mode. The reference documentation for Microsoft Security Scanner is as follows.
Run Windows Update to install the latest Microsoft security patches.
When the ECS instance has a large amount of disk access, network access and high computing requirements, it is normal for the CPU usage to be high. You can upgrade the instance specifications to deal with the problem of insufficient resources. . For information on how to upgrade instance specifications, please refer to the following documents.
Summary of configuration upgrade and downgrade methods
More information
The following are recommended troubleshooting tools for Windows instances related content.
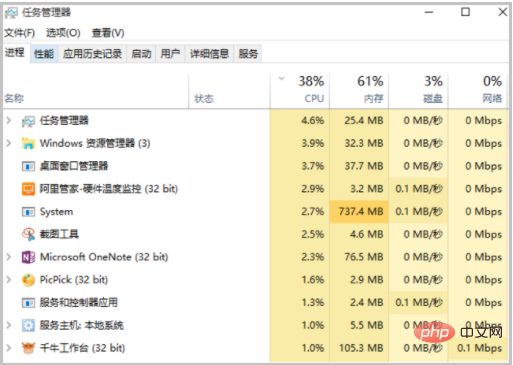
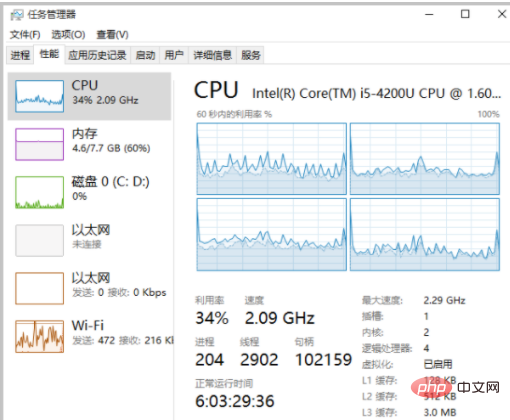
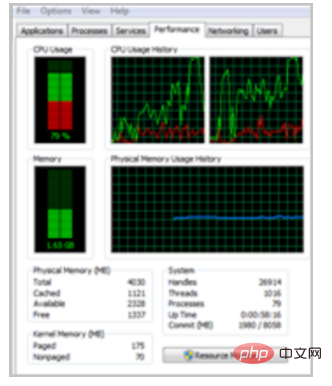
Task Manager
- Visually check the application list and locate applications that occupy higher CPU. The following is the Task Manager page.

- When checking the CPU usage on the performance page, right-click the CPU usage graph and click Change the graph to > Logical Processor. The figure below shows the usage of 4 logical CPUs.

- When the CPU usage of a single process soars to close to 100%, but the CPU usage of other processes does not change much, it may be network I/O caused by processing.
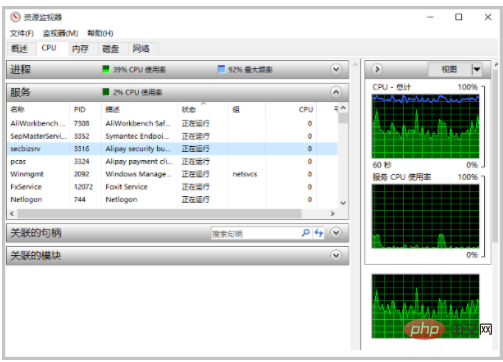
Resource Monitor
Visually check the CPU usage, and you can also search for the corresponding process through handles and modules.
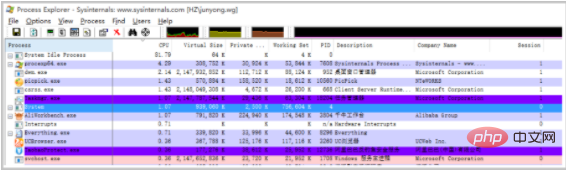
Process Explorer
- Process Explorer is a Microsoft Sysinternals tool. By configuring the correct Symbols, it checks the Call Stack called by the thread of the corresponding application to locate possible problem drivers. The link to download the Process Explorer tool is as follows.
- The following is the Process Explorer tool usage page.

Performance Monitor
- Performance Monitor (Performance Monitor) is Microsoft’s professional tool for collecting performance counters of various components. . For system CPU resource consumption, there are multiple Counters to check. Open Performance Monitor by clicking Start > Run > perfmon.
- Performance has the following three core parameters. Where
\Processor(_Total)\% Processor Timeis the sum of\Processor(*)\% User Timeand\Processor(*)\% Privileged Time.\Processor(_Total)\% Processor Time\Processor(*)\% User Time\Processor(*)\% Privileged Time
-
\Processor(*)\% Privileged Timeis when the application executes system calls in the kernel ( Such as driver, IRP, context switch, etc.) operation time. If the operating system spends more than 30% of its time inPrivileged Time, as shown in the figure below, it means that the instance is performing operations related to high I/O throughput.
- When
% Privileged Timeis very high, further checks are required% DPC Time,% Interrupt The situation of TimeandContext Switches/sec.- High
% DPC Time,% Interrupt Timemeans that the unknown device has a large number of operations or poor performance problems. Please refer to the following documents.
##高 - Context Switches/sec
means that there are a large number of threads in the Ready state, and the number of threads needs to be reduced to solve the problem. When
- High
- % DPC Time
and% Interrupt Timeare very high, you need to use the Microsoft Xperf tool for further analysis. Please refer to the following document to use the XPerf tool .
When the Context Switch value is very high, please refer to the following document. - \Processor(*)\% User Time
Indicates the time consumed by the processor to execute program code. You can determine which application or function call consumes more time.High - User Time
The situation is shown in the figure below.
- cloud server ECS
The above is the detailed content of How to solve the problem of 100% CPU usage. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 What should the CPU utilization be when gaming?
Feb 19, 2024 am 11:21 AM
What should the CPU utilization be when gaming?
Feb 19, 2024 am 11:21 AM
It's common for games to slow down your computer because they consume a lot of resources. It's crucial to understand your CPU usage when gaming so you can avoid overloading it. Therefore, keeping track of appropriate CPU usage is key to keeping your gaming experience smooth. In this article, we'll look at the appropriate CPU usage you should achieve while your game is running. CPU utilization during gaming CPU utilization is an important indicator of processor workload and depends on the performance specifications of the CPU. More powerful CPUs generally have higher usage. A CPU with more cores and threads can improve the overall performance of your system. Multi-threading support helps unleash the full potential of your CPU. In games, CPU usage depends on processor utilization, which can affect the game
 How to set CPU performance to full in Win11
Feb 19, 2024 pm 07:42 PM
How to set CPU performance to full in Win11
Feb 19, 2024 pm 07:42 PM
Many users find that the computer is not running smoothly enough when using the Win11 system. They want to improve CPU performance, but they don't know how to do it. The following will introduce in detail how to set the CPU performance to the highest level in Win11 system to make your computer more efficient. Setting method: 1. Right-click "This PC" on the desktop and select "Properties" in the option list. 2. After entering the new interface, click "Advanced System Settings" in "Related Links". 3. In the window that opens, click the "Advanced" tab at the top, then click the & at the bottom of "Performance"
 How to increase the clock frequency of your computer's CPU
Feb 20, 2024 am 09:54 AM
How to increase the clock frequency of your computer's CPU
Feb 20, 2024 am 09:54 AM
How to Overclock Computer CPUs With the continuous advancement of technology, people's demand for computer performance is also getting higher and higher. An effective way to improve computer performance is to increase the CPU's operating frequency through overclocking. Overclocking allows the CPU to process data faster, providing higher computing power. So, how to overclock a computer CPU? The following will introduce you to the basic principles and specific operation methods of overclocking. First, let's understand how overclocking works. The operating frequency of the CPU is determined by the crystal oscillator on the motherboard
 How to undervolt and overclock your CPU using Intel XTU
Feb 19, 2024 am 11:06 AM
How to undervolt and overclock your CPU using Intel XTU
Feb 19, 2024 am 11:06 AM
Intel XTU is a powerful application that allows you to easily manage your computer's performance. You can fix overheating issues by adjusting the CPU voltage, or boost performance by overclocking. In this article, we'll look at how you can take advantage of Intel XTU to optimize your computer's performance, whether that's adjusting voltage or overclocking. What effect do undervolting and overclocking have on the CPU? Before we move on to learning how to undervolt and overclock a CPU, we first have to understand what they are. Undervolting refers to gradually reducing the voltage required by the CPU. This process helps reduce heat emissions, as high voltage results in higher temperatures. By reducing the voltage supply to the CPU, the temperature can be effectively reduced. If your laptop starts to slow down after getting hot, you should solve the problem promptly.
 The difference between boxed and bulk cpu
Jan 23, 2024 am 09:46 AM
The difference between boxed and bulk cpu
Jan 23, 2024 am 09:46 AM
The differences between boxed and bulk CPUs: 1. Quality; 2. Warranty period; 3. Fan; 4. Price; 5. Packaging; 6. Sales channels. Detailed introduction: 1. Quality, whether it is boxed or bulk, there is no difference in the quality of the CPU itself. They are all manufactured by the same manufacturer and undergo the same quality testing and quality control process; 2. Warranty period, boxed CPU A longer warranty period is usually provided, usually three years, while bulk CPUs usually only have a one-year warranty, this is because boxed CPUs are usually sold by official or authorized dealers, etc.
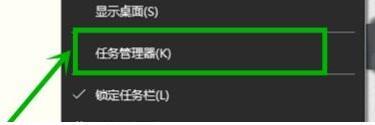 The operation process of WIN10 service host occupying too much CPU
Mar 27, 2024 pm 02:41 PM
The operation process of WIN10 service host occupying too much CPU
Mar 27, 2024 pm 02:41 PM
1. First, we right-click the blank space of the taskbar and select the [Task Manager] option, or right-click the start logo, and then select the [Task Manager] option. 2. In the opened Task Manager interface, we click the [Services] tab on the far right. 3. In the opened [Service] tab, click the [Open Service] option below. 4. In the [Services] window that opens, right-click the [InternetConnectionSharing(ICS)] service, and then select the [Properties] option. 5. In the properties window that opens, change [Open with] to [Disabled], click [Apply] and then click [OK]. 6. Click the start logo, then click the shutdown button, select [Restart], and complete the computer restart.
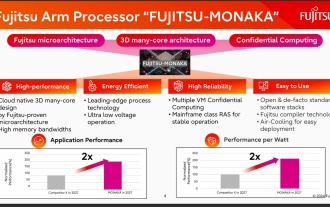 144-core, 3D-stacked SRAM: Fujitsu details next-generation data center processor MONAKA
Jul 29, 2024 am 11:40 AM
144-core, 3D-stacked SRAM: Fujitsu details next-generation data center processor MONAKA
Jul 29, 2024 am 11:40 AM
According to news from this website on July 28, foreign media TechRader reported that Fujitsu introduced in detail the FUJITSU-MONAKA (hereinafter referred to as MONAKA) processor planned to be shipped in 2027. MONAKACPU is based on the "cloud native 3D many-core" architecture and adopts the Arm instruction set. It is oriented to the data center, edge and telecommunications fields. It is suitable for AI computing and can realize mainframe-level RAS1. Fujitsu said that MONAKA will achieve a leap in energy efficiency and performance: thanks to technologies such as ultra-low voltage (ULV) technology, the CPU can achieve 2 times the energy efficiency of competing products in 2027, and cooling does not require water cooling; in addition, the application performance of the processor It can also reach twice as much as your opponent. In terms of instructions, MONAKA is equipped with vector
 Leak reveals key specs of Intel Arrow Lake-U, -H, -HX and -S
Jun 15, 2024 pm 09:49 PM
Leak reveals key specs of Intel Arrow Lake-U, -H, -HX and -S
Jun 15, 2024 pm 09:49 PM
IntelArrowLakeisexpectedtobebasedonthesameprocessorarchitectureasLunarLake,meaningthatIntel'sbrandnewLionCoveperformancecoreswillbecombinedwiththeeconomicalSkymontefficiencycores.WhileLunarLakeisonlyavailableasava