Is a firewall a hardware or software device?
A firewall is both a hardware device and a software device. It is a combination of software and hardware devices. Firewall is a technology that helps computer networks build a relatively isolated protective barrier between internal and external networks by organically combining various software and hardware devices for security management and screening to protect the security of user data and information. .

The operating environment of this tutorial: Windows 7 system, Dell G3 computer.
What is a firewall?
Firewall refers to a protective barrier composed of software and hardware devices between the internal network and the external network, and between the local area network and the external network. Just like setting up a wall, it can establish a security gateway between networks to protect the internal network from intrusion by illegal users.
Firewall technology helps computer networks build a relatively isolated protective barrier between the internal and external networks by organically combining various software and hardware devices for security management and screening to protect user data and A technology for information security.
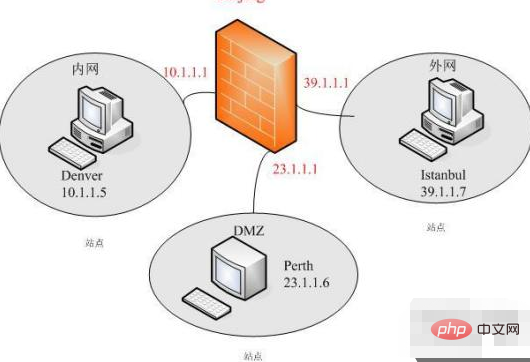
The function of firewall technology is mainly to promptly discover and deal with security risks, data transmission and other problems that may exist when the computer network is running. The treatment measures include isolation and protection, and can also Record and detect various operations in computer network security to ensure the security of computer network operations, protect the integrity of user data and information, and provide users with a better and safer computer network experience.
Friends who are familiar with the Internet must be familiar with firewalls. Whether it is the firewall that comes with the computer, a general software firewall, or a hardware firewall, they are more or less familiar with it. In an age where computer viruses are the norm, how do you stop outside hackers from accessing your systems and sensitive data? The easiest way is through a firewall.
What is the difference between hardware firewall and software firewall?
Hardware firewall embeds the "software firewall" in the hardware, adds the "firewall program" to the chip, and the hardware performs these functions, thereby reducing the CPU burden on the computer or server. The "hardware firewall" provided by the general "software security manufacturer" is to customize the hardware from the "hardware server manufacturer" and then embed the "Linux system" with its own software system.
Software firewalls are generally developed based on a certain operating system platform, and the software is installed and configured directly on the computer. Due to the diversity of operating systems among customers, software firewalls need to support multiple operating systems, such as "Unix, Linux, SCO-Unix, Windows", etc.
Hardware firewalls achieve the purpose of isolating internal and external networks through a combination of hardware and software; software firewalls achieve the purpose of isolating internal and external networks through pure software.
1. Stability
The quality of stability mainly comes from the operating platform of the firewall, that is, the "operating system".
Hardware firewalls generally use Linux systems compiled from the kernel. The high reliability and stability of the Linux system itself ensures the overall stability of the firewall.
Linux system will never crash. Its stability is due to the fact that it does not have a huge kernel and full of loopholes like other operating systems. The stability of the system mainly depends on the structure of the system design. The structure of computer hardware has not been significantly changed since it was designed in 1981, and continuous backward compatibility has forced those application software with extremely poor programming styles to be reluctantly transplanted to the latest version of Windows. This kind of "make do with software development" mode" greatly hinders the development of system stability.
The attention-grabbing Linux open source development model ensures that any system vulnerabilities can be discovered and corrected in a timely manner. The Linux system has adopted many security technical measures, including "permission control for reading and writing", "protected subsystems", "audit tracking", "core authorization", etc., which provide users in multi-user network environments with necessary safety guarantees.
Software firewalls are generally installed on the Windows platform and are simple to implement. However, due to the vulnerabilities and instability of the Windows operating system itself, it also brings security and stability issues to the software firewall. Although Microsoft is also working hard to remedy these problems, compared with the Linux operating system, it still has many loopholes.
In terms of virus infringement, from the development of the Linux system to the present, there has been almost no virus infection. We don’t need to say more about viruses based on vulnerabilities in the Windows operating system. Anyone who has used a PC (personal computer) for a long time will have a general feeling.
2. Main indicators
"Throughput" and "Message Forwarding Rate" are the main indicators related to firewall applications.
Throughput: The data in the network is composed of data packets. The firewall consumes resources to process each data packet. Throughput refers to the number of data packets passing through the firewall per unit time without packet loss. This is an important metric for measuring firewall performance.
The hardware equipment of the hardware firewall is customized by professional manufacturers. The issue of "throughput" is fully considered at the beginning of customization. It is far better than the software firewall in this regard, because the hardware of the software firewall , users choose and configure themselves when purchasing computers. In many cases, they do not consider the issue of "throughput". Moreover, the Windows system itself consumes a lot of hardware resources, and its throughput and ability to process large data streams are far less than that of the hardware. Firewall.
If the throughput is too small, the firewall will become the bottleneck of the network, which will cause problems such as "slow network speed and insufficient Internet bandwidth."
3. Working principle
Software firewalls are generally "packet filtering mechanisms" with simple filtering rules. They can only detect the third layer of "network layer". To check the source or destination IP, the ability of the firewall is far less than that of the hardware firewall. Even the most basic hacker attack method: "IP masquerading" cannot solve it, and all the data packets passing through must be checked, so the speed is relatively slow.
Hardware firewall mainly uses the fourth generation "state detection mechanism". "State detection" checks whether the rules allow the establishment of a connection when the communication initiates a connection, and then adds a record to the cached state detection table. , there is no need to check the rules in the future, just check the status detection table, and the speed has been greatly improved.
Because the level of work has been improved, the anti-hacker function of hardware firewalls is much stronger than that of software firewalls. The "status detection mechanism" of the hardware firewall not only tracks the information contained in the "data packet". In order to track the status of the "data packet", the firewall also records useful information to help identify the "data packet", such as "existing Network connections, outgoing requests for data" etc.
For example, if the incoming data packet contains a video data stream, the firewall may have recorded the relevant information and matched it, and the data packet may be allowed to pass. .
Hardware firewalls and software firewalls are very different in their implementation mechanisms. Therefore, there are also great differences in the anti-hacking capabilities of software and hardware firewalls.
4. Intranet control
Software firewall, due to its own working principle, does not have specific control and management of the intranet. For example: "QQ cannot be banned, virus intrusion cannot be well prevented, and Internet access control cannot be based on specific IPs and MACs." Its main function is external.
Hardware firewalls are based on the "status detection" mechanism. Security vendors can develop "application layer" filtering rules according to different needs of the market to meet the control of the intranet, so that they can be implemented at a high level. Filtering can do many things that software firewalls cannot. Especially for the popular ARP virus, the hardware firewall has implemented corresponding strategies based on its intrusion principle, completely eliminating the harm of the ARP virus.
Firewalls are no longer limited to preventing external hacker attacks, but also include problems in corporate internal networks, such as "slow Internet speed, intermittent Internet access, and abnormal email sending and receiving."
Analysis of the main reason lies in the usage problems of intranet users. For example, many users use BT downloads and browse some irregular websites during working hours, which will cause many insecurities in the intranet. For example: viruses. The spread of many viruses is caused by the bad behavior of users. Therefore, the control and management of intranet users is very necessary.

The core technology of firewall
Firewalls are generally divided into packet filtering, application-level gateways and proxies Servers and other major types. It includes the following core technologies:
1. Packet filtering technology
Packet filtering technology is a simple and effective security control technology that works at the network layer. By loading rules that allow or prohibit certain source addresses, destination addresses, TCP port numbers, etc. on the devices connected to each other, the data packets passing through the devices are checked and the data packets are restricted from entering and exiting the internal network.
The biggest advantage of packet filtering is that it is transparent to users and has high transmission performance. However, since the security control level is at the network layer and transport layer, the intensity of security control is limited to the source address, destination address and port number. Therefore, only relatively preliminary security control can be carried out. For malicious congestion attacks, memory overwrite attacks or viruses, etc. High-level attack methods are powerless.
2. Application proxy technology
The application proxy firewall works on the seventh layer of OSI. It checks all application layer information packets and checks the content information. into the decision-making process to improve the security of the network.
Application Gateway Firewall is implemented by breaking the client/server model. Each client/server communication requires two connections: one from the client to the firewall and one from the firewall to the server. In addition, each agent requires a different application process, or a service program running in the background. For each new application, a service program for this application must be added, otherwise the service cannot be used. Therefore, application gateway firewalls have the disadvantage of poor scalability.
3. Stateful detection technology
Stateful detection firewall works on the second to fourth layers of OSI. It adopts stateful detection packet filtering technology and is an extension of traditional packet filtering function. Come. Stateful inspection firewalls have an inspection engine at the network layer that intercepts data packets and extracts information related to the application layer status, and uses this as a basis to decide whether to accept or reject the connection. This technology provides a highly secure solution while being adaptable and scalable. Stateful inspection firewalls typically also include proxy-level services that provide additional support for application-specific data content.
Stateful inspection firewall basically maintains the advantages of simple packet filtering firewall, has relatively good performance, and is transparent to applications. On this basis, security has been greatly improved. This kind of firewall abandons the shortcomings of simple packet filtering firewalls that only examine the data packets entering and leaving the network and do not care about the status of the data packets. It establishes a state connection table in the core part of the firewall, maintains the connection, and treats the data entering and leaving the network as events one by one. deal with. The main feature is that due to the lack of in-depth detection of application layer protocols, it is unable to completely identify a large number of spam, advertisements, Trojans, etc. in the data packets.
4. Complete content detection technology
Complete content detection technology The firewall integrates state detection and application proxy technology, and on this basis, it is further based on the multi-layer detection architecture. Anti-virus, content filtering, application identification and other functions are integrated into the firewall, which also includes IPS functions. Multiple units are integrated into one, scanning the application layer at the network interface, combining anti-virus, content filtering and firewall, which embodies the network and new ideas for information security (so it is also called "next generation firewall technology"). It implements OSI layer 7 content scanning at the network edge, enabling real-time deployment of application layer service measures such as virus protection and content filtering at the network edge. Complete content inspection technology firewalls can inspect the entire data packet content, establish connection status tables as needed, have strong network layer protection, and fine application layer control. However, due to the high degree of functional integration, the requirements for product hardware are relatively high.
For more related knowledge, please visit the FAQ column!
The above is the detailed content of Is a firewall a hardware or software device?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1382
1382
 52
52
 How to fix 'Error: 0x80070185, Cloud operation was unsuccessful” in OneDrive
May 16, 2023 pm 04:26 PM
How to fix 'Error: 0x80070185, Cloud operation was unsuccessful” in OneDrive
May 16, 2023 pm 04:26 PM
OneDrive is a popular cloud storage application provided by Microsoft. Most of us use OneDrive to store our files, folders, documents, etc. But some users complained that when they try to access shared files on OneDrive, it gives an error stating “Error: 0x80070185, Cloud operation was unsuccessful”. Therefore, they cannot perform any operations on OneDrive such as copying files, pasting, downloading shared files, etc. Nowadays, it is necessary to use these operations in our daily work. This error can be easily solved and for this we have some methods that we can apply and try to solve the problem. let's start! Method 1 – Sign out and sign back in to OneDrive app steps
 8 Big Fixes if Grammarly Not Working on Windows 10 Browser
May 05, 2023 pm 02:16 PM
8 Big Fixes if Grammarly Not Working on Windows 10 Browser
May 05, 2023 pm 02:16 PM
If you have syntax issues on your Windows 10 or 11 PC, this article will help you solve the problem. Grammarly is one of the most popular typing assistants for fixing grammar, spelling, clarity, and more. It has become an essential part of writing professionals. However, if it doesn't work properly, it can be a very frustrating experience. Many Windows users have reported that this tool does not work well on their computers. We did an in-depth analysis and found the cause and solution of this problem. Why doesn't Grammarly work on my PC? Grammarly on PC may not work properly due to several common reasons. It includes the following
 Win11 firewall advanced settings gray solution
Dec 24, 2023 pm 07:53 PM
Win11 firewall advanced settings gray solution
Dec 24, 2023 pm 07:53 PM
When setting up the firewall, many friends found that their win11 firewall advanced settings were grayed out and unable to be clicked. This may be caused by not adding a control unit, or by not opening the advanced settings in the correct way. Let’s take a look at how to solve it. Win11 firewall advanced settings gray method one: 1. First, click the start menu below, search and open "Control Panel" at the top 2. Then open "Windows Defender Firewall" 3. After entering, you can open "Advanced Settings" in the left column . Method 2: 1. If the above method cannot be opened, you can right-click "Start Menu" and open "Run" 2. Then enter "mmc" and press Enter to confirm opening. 3. After opening, click on the upper left
 Fix: Windows 11 Firewall blocks printer
May 01, 2023 pm 08:28 PM
Fix: Windows 11 Firewall blocks printer
May 01, 2023 pm 08:28 PM
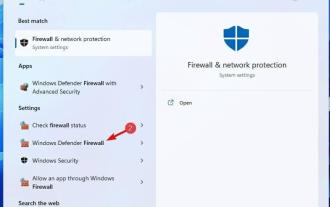
Firewalls monitor network traffic and can block network connections for certain programs and hardware. Windows 11 includes its own Windows Defender Firewall, which may block printers from accessing the web. Therefore, affected users cannot use their Brother printers when the firewall blocks it. Keep in mind that this issue affects other brands as well, but today we’ll show you how to fix it. Why is my Brother printer blocked by the firewall? There are several causes for this issue, and you will most likely need to open certain ports before your printer can access the network. Printer software can also cause problems, so be sure to update it as well as your printer driver. Read on to learn how
 How to enable or disable firewall on Alpine Linux?
Feb 21, 2024 pm 12:45 PM
How to enable or disable firewall on Alpine Linux?
Feb 21, 2024 pm 12:45 PM
On AlpineLinux, you can use the iptables tool to configure and manage firewall rules. Here are the basic steps to enable or disable the firewall on AlpineLinux: Check the firewall status: sudoiptables -L If the output shows rules (for example, there are some INPUT, OUTPUT, or FORWARD rules), the firewall is enabled. If the output is empty, the firewall is currently disabled. Enable firewall: sudoiptables-PINPUTACCEPTsudoiptables-POUTPUTACCEPTsudoiptables-PFORWARDAC
 Resolve error code 0xc004f074 when activating Windows 11.
May 08, 2023 pm 07:10 PM
Resolve error code 0xc004f074 when activating Windows 11.
May 08, 2023 pm 07:10 PM
After installing the latest operating system on your PC, activating your copy of Windows 11 is the main job. Not only does it unlock the true potential of the Windows 11 operating system, but it also gets rid of the annoying "Activate your Windows 11" message. However, for some users, Windows 11 activation error 0xc004f074 hinders the smooth progress of activation. This bug apparently prevents users from activating Windows 11 and forces them to use an operating system with limited functionality. Windows 11 activation error code 0xc004f074 is related to the Key Management Service. You will encounter this problem when KMS is unavailable. Okay, that's it for this tutorial
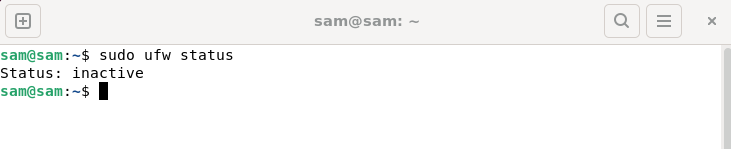 How to fix UFW status showing as inactive in Linux
Mar 20, 2024 pm 01:50 PM
How to fix UFW status showing as inactive in Linux
Mar 20, 2024 pm 01:50 PM
UFW, also known as Uncomplex Firewall, is adopted by many Linux distributions as their firewall system. UFW is designed to make it easy for novice users to manage firewall settings through both the command line interface and the graphical user interface. A UFW firewall is a system that monitors network traffic according to set rules to protect the network from network sniffing and other attacks. If you have UFW installed on your Linux system but its status shows as inactive, there could be several reasons. In this guide, I will share how to resolve the UFW firewall inactive issue on Linux systems. Why UFW Shows Inactive Status on Linux Why UFW Is Inactive by Default on Linux How to Inactive on Linux
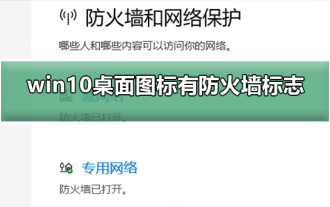 How to remove the firewall logo on the Win10 desktop icon?
Jan 01, 2024 pm 12:21 PM
How to remove the firewall logo on the Win10 desktop icon?
Jan 01, 2024 pm 12:21 PM
Many friends who use win10 system find that there is a firewall logo on the icon on the computer desktop. What is going on? This makes many friends with obsessive-compulsive disorder particularly uncomfortable. In fact, we only need to open the control panel and click " It can be solved by changing "Change User Account Control Settings". Let's take a look at the specific tutorial. How to cancel the firewall logo on the desktop icon in Windows 10 1. First, right-click the Start menu button next to the computer startup screen, and then select the Control Panel function from the pop-up menu. 2. Then select the "User Account" option and select the "Change User Account Control Settings" item from the new interface that appears. 3. After adjusting the slider in the window to the bottom, click Confirm to exit.



