Avoid the trap! Pitfalls encountered during Gin installation
This article is introduced to you by the go language tutorial column. The theme is about the pitfalls encountered in Gin installation. I hope it will be helpful to friends in need!
Gin initial installation
1. Install the official document executiongo get -u github.com/gin-gonic/gin
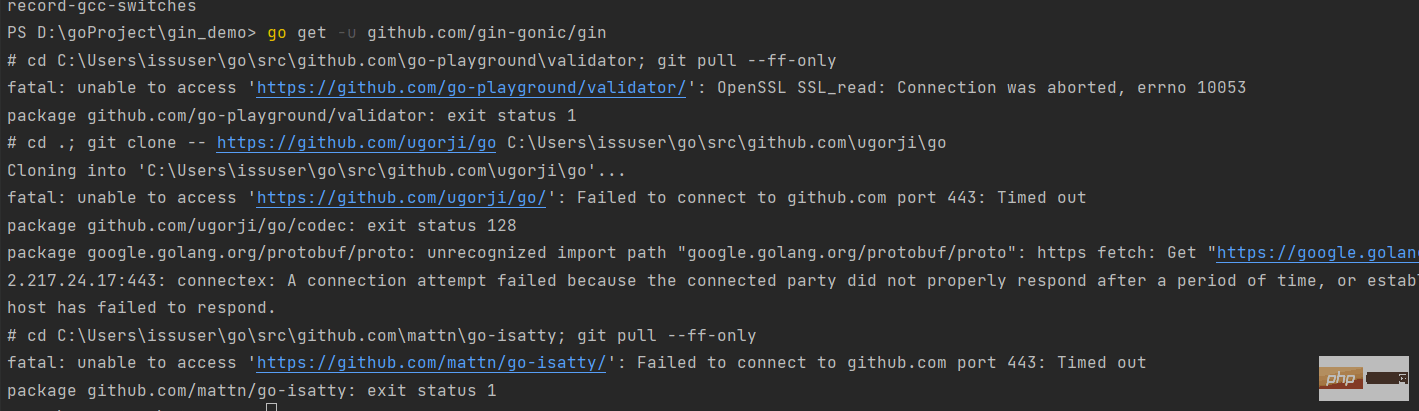
Because I can't circumvent the wall, Baidu said to use gopm to solve it. Friends in the group said that this kind of experiment has long been outdated, and now they use go mod to solve it.
So start go mod
go env -w GOBIN=/Users/youdi/go/bin go env -w GO111MODULE=on go env -w GOPROXY=https://goproxy.cn,direct // 使用七牛云的
Use go mod to manage a new project
mkdir Gone cd Gone go mod init Gone
Check the go.mod file
module Gone go 1.16
Once the go.mod file is created , its content will be fully controlled by the go toolchain. The go toolchain will modify and maintain the go.mod file when various commands are executed, such as go get, go build, go mod, etc.
go.mod provides four commands: module, require, replace and exclude
-
moduleThe statement specifies the name (path) of the package -
requireThe dependency module specified by the statement -
replaceThe statement can replace the dependency module -
excludeThe statement can ignore the dependency Item module
package mainimport (
"github.com/gin-gonic/gin")func main() {
r := gin.Default()
r.GET("/ping", func(c *gin.Context) {
c.JSON(200, gin.H{
"message": "pong",
})
})
r.Run() // listen and serve on 0.0.0.0:8080 (for windows "localhost:8080")}Execute go run main.go. When running the code, you will find that go mod will automatically find dependencies and automatically download
The result is an error
main.go:3:8: no required module provides package github.com/gin-gonic/gin; to add it: go get github.com/gin-gonic/gin
Execute: go mod edit -require github .com/gin-gonic/gin@latest Solution, specify the Gin version
Run go run main.go again and report an error
go: github.com/gin-gonic/gin@v1.7.4: missing go.sum entry; to add it: go mod download github.com/gin-gonic/gin
Then execute go mod tidy and execute go run main.go again. Finally it runs.
For more golang related knowledge, please visit golangtutorial column!
The above is the detailed content of Avoid the trap! Pitfalls encountered during Gin installation. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 How to safely read and write files using Golang?
Jun 06, 2024 pm 05:14 PM
How to safely read and write files using Golang?
Jun 06, 2024 pm 05:14 PM
Reading and writing files safely in Go is crucial. Guidelines include: Checking file permissions Closing files using defer Validating file paths Using context timeouts Following these guidelines ensures the security of your data and the robustness of your application.
 How to configure connection pool for Golang database connection?
Jun 06, 2024 am 11:21 AM
How to configure connection pool for Golang database connection?
Jun 06, 2024 am 11:21 AM
How to configure connection pooling for Go database connections? Use the DB type in the database/sql package to create a database connection; set MaxOpenConns to control the maximum number of concurrent connections; set MaxIdleConns to set the maximum number of idle connections; set ConnMaxLifetime to control the maximum life cycle of the connection.
 Comparison of advantages and disadvantages of golang framework
Jun 05, 2024 pm 09:32 PM
Comparison of advantages and disadvantages of golang framework
Jun 05, 2024 pm 09:32 PM
The Go framework stands out due to its high performance and concurrency advantages, but it also has some disadvantages, such as being relatively new, having a small developer ecosystem, and lacking some features. Additionally, rapid changes and learning curves can vary from framework to framework. The Gin framework is a popular choice for building RESTful APIs due to its efficient routing, built-in JSON support, and powerful error handling.
 What are the best practices for error handling in Golang framework?
Jun 05, 2024 pm 10:39 PM
What are the best practices for error handling in Golang framework?
Jun 05, 2024 pm 10:39 PM
Best practices: Create custom errors using well-defined error types (errors package) Provide more details Log errors appropriately Propagate errors correctly and avoid hiding or suppressing Wrap errors as needed to add context
 How to save JSON data to database in Golang?
Jun 06, 2024 am 11:24 AM
How to save JSON data to database in Golang?
Jun 06, 2024 am 11:24 AM
JSON data can be saved into a MySQL database by using the gjson library or the json.Unmarshal function. The gjson library provides convenience methods to parse JSON fields, and the json.Unmarshal function requires a target type pointer to unmarshal JSON data. Both methods require preparing SQL statements and performing insert operations to persist the data into the database.
 How to solve common security problems in golang framework?
Jun 05, 2024 pm 10:38 PM
How to solve common security problems in golang framework?
Jun 05, 2024 pm 10:38 PM
How to address common security issues in the Go framework With the widespread adoption of the Go framework in web development, ensuring its security is crucial. The following is a practical guide to solving common security problems, with sample code: 1. SQL Injection Use prepared statements or parameterized queries to prevent SQL injection attacks. For example: constquery="SELECT*FROMusersWHEREusername=?"stmt,err:=db.Prepare(query)iferr!=nil{//Handleerror}err=stmt.QueryR
 Golang framework vs. Go framework: Comparison of internal architecture and external features
Jun 06, 2024 pm 12:37 PM
Golang framework vs. Go framework: Comparison of internal architecture and external features
Jun 06, 2024 pm 12:37 PM
The difference between the GoLang framework and the Go framework is reflected in the internal architecture and external features. The GoLang framework is based on the Go standard library and extends its functionality, while the Go framework consists of independent libraries to achieve specific purposes. The GoLang framework is more flexible and the Go framework is easier to use. The GoLang framework has a slight advantage in performance, and the Go framework is more scalable. Case: gin-gonic (Go framework) is used to build REST API, while Echo (GoLang framework) is used to build web applications.
 What are the common dependency management issues in the Golang framework?
Jun 05, 2024 pm 07:27 PM
What are the common dependency management issues in the Golang framework?
Jun 05, 2024 pm 07:27 PM
Common problems and solutions in Go framework dependency management: Dependency conflicts: Use dependency management tools, specify the accepted version range, and check for dependency conflicts. Vendor lock-in: Resolved by code duplication, GoModulesV2 file locking, or regular cleaning of the vendor directory. Security vulnerabilities: Use security auditing tools, choose reputable providers, monitor security bulletins and keep dependencies updated.






