 Common Problem
Common Problem
 What two types of encryption algorithms can be divided according to the type of key?
What two types of encryption algorithms can be divided according to the type of key?
What two types of encryption algorithms can be divided according to the type of key?
Encryption algorithms can be divided into two types according to the type of key: "asymmetric key encryption algorithm" and "symmetric key encryption algorithm". Asymmetric key encryption algorithm refers to an encryption algorithm that uses different keys for encryption and decryption; symmetric key encryption algorithm refers to an encryption algorithm that uses the same key for encryption and decryption.

The operating environment of this tutorial: Windows 7 system, Dell G3 computer.
The basic process of data encryption is to process files or data that were originally plain text according to a certain algorithm, turning it into an unreadable piece of code called "ciphertext", so that it can only be entered when the corresponding password is entered. The original content can be displayed only after the key is obtained. In this way, the purpose of protecting the data from being stolen and read by illegal persons is achieved. The reverse of this process is decryption, the process of converting the encoded information into its original data.
Encryption algorithms can be divided into two types according to the type of key: "asymmetric key encryption algorithm" and "symmetric key encryption algorithm".
The asymmetric encryption algorithm requires two keys: the public key (publickey: referred to as the public key) and the private key (privatekey: referred to as the private key).
The public key and the private key are a pair. If the public key is used to encrypt data, it can only be decrypted with the corresponding private key. Because encryption and decryption use two different keys, this algorithm is called an asymmetric encryption algorithm.
The basic process of asymmetric encryption algorithm to realize the exchange of confidential information is: Party A generates a pair of keys and makes the public key public, and other roles (Party B) who need to send information to Party A use the key (Party A) Party A's public key) encrypts the confidential information before sending it to Party A; Party A then uses its own private key to decrypt the encrypted information.
The opposite is true when Party A wants to reply to Party B. It uses Party B's public key to encrypt the data. Similarly, Party B uses its own private key to decrypt.
The symmetric key encryption algorithm requires only one key: the private key, so it is also called private key encryption. It is an encryption algorithm that uses the same key for encryption and decryption.
Sometimes called traditional cryptographic algorithm, the encryption key can be calculated from the decryption key, and the decryption key can also be calculated from the encryption key. In most symmetric algorithms, the encryption key and decryption key are the same, so this encryption algorithm is also called a secret key algorithm or a single key algorithm.
It requires the sender and receiver to agree on a key before communicating securely.
The security of symmetric algorithms relies on the key. Leaking the key means that anyone can decrypt the messages they send or receive, so the confidentiality of the key is crucial to the security of communication.
For more related knowledge, please visit the FAQ column!
The above is the detailed content of What two types of encryption algorithms can be divided according to the type of key?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1378
1378
 52
52
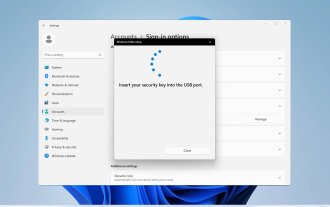 How to create and set up a USB security key on Windows 11
Sep 16, 2023 am 11:29 AM
How to create and set up a USB security key on Windows 11
Sep 16, 2023 am 11:29 AM
Protecting your PC from unauthorized access is crucial if you want to protect your files and personal data, which is why many people want to create a USB security key on Windows 11. This is the most secure authentication method, and in today's guide, we'll show you how to set it up properly on your PC. Benefits of Using USB Security Keys on Windows 11 Physical security keys provide the most secure two-factor authentication. They are immune to phishing attacks because they do not use an internet connection. Security keys protect your Windows accounts and most online accounts. Many security keys are compatible with Windows Hello. How to create mine from scratch on Windows 11
 win7 activation key permanent activation
Jul 12, 2023 pm 02:41 PM
win7 activation key permanent activation
Jul 12, 2023 pm 02:41 PM
Many people use the win7 ISO image to install win7 but don't know how to activate the win7 activation key permanently. Win7 has an activation period. If it cannot be activated after 30 days, it will restart every hour, which seriously affects our work efficiency. But if you want to activate wn7, you need a win7 activation key. Next, the editor will share with you the win7 permanent activation key compiled by the editor. The win7 versions that everyone usually uses include Home Premium, Home Basic, Professional, and Ultimate. However, some win7 users are very distressed without activation keys. Therefore, the following are the more reliable win7 activation keys on the Internet that the editor has compiled for you. key. The win7 activation key is as follows win7 home premium activation key:
 Learn how to view your Windows 11 product key
Dec 24, 2023 pm 01:35 PM
Learn how to view your Windows 11 product key
Dec 24, 2023 pm 01:35 PM
Some friends don’t know how to check the win11 key. In fact, if you activate win11, you can check the win11 key directly in the system. If you have not activated it, you can also check it in the win11 box or email you purchased. How to check the win11 key: 1. Activated 1. If it has been activated, just right-click the start menu and open "Run" 2. Enter "regedit" and press Enter to open the registry. 3. Then enter "Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsNT\CurrentVersion\SoftwareProtectionPlatfo
 How to use PowerToys on Windows 11 to disable keyboard keys from Microsoft
Aug 15, 2023 pm 02:01 PM
How to use PowerToys on Windows 11 to disable keyboard keys from Microsoft
Aug 15, 2023 pm 02:01 PM
Once learned, typing is an unconscious task. You know what you want to type and your fingers dance across the keyboard to get it out. However, if your keyboard configuration doesn't match your typing habits, or certain keys consistently get in the way, you might benefit from disabling those keys entirely. Windows has no native way to disable a key. Fortunately, it's easy when using the PowerToys utility. Here's everything you need to know about disabling keyboard keys and keyboard shortcuts on Windows 11. How to Disable a Key Using PowerToys’ Keyboard Manager The PowerToys utility provides the easiest way to disable problematic keys on Windows. First, from Microsoft’s website
 The latest available win7 ultimate version key 2021 version
Jul 08, 2023 pm 02:37 PM
The latest available win7 ultimate version key 2021 version
Jul 08, 2023 pm 02:37 PM
The main method to activate the win7 ultimate system is through win7 activation code or win7 activation tool. Generally, the genuine win7 activation code requires money, so where can I find the free win7 ultimate key? Today I will share with you some of the latest available win7 ultimate keys for activating the system. 1. Win7 Ultimate Edition activation key: FJGCP-4DFJD-GJY49-VJBQ7-HYRR2VQ3PY-VRX6D-CBG4J-8C6R2-TCVBD2Y4WT-DHTBF-Q6MMK-KYK6X-VKM6G342DG-6YJR8-X92GV-V7DCV-P4K279CW99-
 The latest free win10 professional version key in 2021
Jul 10, 2023 am 08:17 AM
The latest free win10 professional version key in 2021
Jul 10, 2023 am 08:17 AM
The win10 professional version system is a relatively complete version of the win10 system and is also a relatively popular system. However, after downloading and installing the win10 professional version system, it generally needs to be activated before it can be used normally. So how to activate the win10 professional version? We can activate it with the help of win10 professional version activation code. Below, the editor will share with you some of the latest free win10 professional version keys in 2021. 1. Activation key 1. Win10 Professional Edition activation key: W269N-WFGWX-YVC9B-4J6C9-T83GXMH37W-N47XK-V7XM9-C7227-GCQG92X7P3-NGJTH-Q9TJF-8XDP9-T83GTJ2
 Revealing the method to solve PyCharm key failure
Feb 23, 2024 pm 10:51 PM
Revealing the method to solve PyCharm key failure
Feb 23, 2024 pm 10:51 PM
PyCharm is a powerful Python integrated development environment that is widely loved by developers. However, sometimes we may encounter key invalidation problems when using PyCharm, resulting in the inability to use the software normally. This article will reveal the solution to PyCharm key failure and provide specific code examples to help readers quickly solve this problem. Before we start solving the problem, we first need to understand why the key is invalid. PyCharm key failure is usually due to network problems or the software itself
 How to obtain Windows 10 activation key and precautions
Mar 27, 2024 pm 09:09 PM
How to obtain Windows 10 activation key and precautions
Mar 27, 2024 pm 09:09 PM
The Windows 10 activation key is a set of serial numbers that need to be entered when installing the Windows 10 operating system. It is used to verify the legitimacy of the system and unlock all functions in the operating system. For many users, activating Windows 10 systems may encounter some difficulties, so this article will introduce some methods and precautions for obtaining Windows 10 activation keys. How to get the Windows 10 activation key 1. Purchase the genuine key Purchase the genuine Windows 10 activation key


