What does computer security mean?
Computer security refers to the security option in BOIS, which refers to the security option and is related to the computer password; if the Security Option is set to System, the system will require a password before booting and entering the BIOS setup program.

#The operating environment of this article: Windows 7 system, Dell G3 computer.
What does computer security mean?
The security option in BOIS refers to the security option, which is related to the computer password.
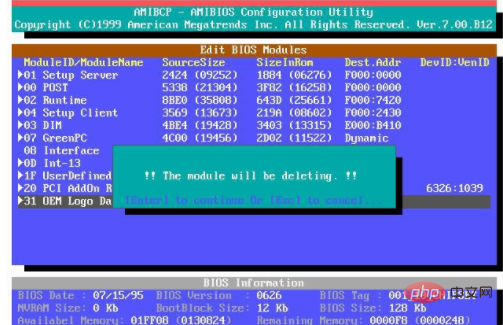
When you select this function, the following message will appear:
Enter the password, up to eight characters, and then press the key. The password you enter now clears all previously entered CMOS passwords. You will be asked to enter your password again. Enter the password again and press the key. You can press the key to abandon this selection without entering a password.
To clear the password, just press the key when the window for entering the password pops up. The screen will display a confirmation message whether to disable the password. Once the password is disabled, after the system restarts, you can enter the setup process directly without entering the password.
Once you use the password function, you will be asked to enter your password each time before entering the BIOS setup program. This prevents any unauthorized person from changing your system's configuration information.
In addition, by enabling the system password feature, you can also make the BIOS require a password before each system boot. This prevents any unauthorized use of your computer. Users can enable this feature in the Security Option in Advanced BIOS Feature Settings. If the Security Option is set to System, the system will ask for a password before booting and entering the BIOS setup program. If set to Setup, the password is only required before entering the BIOS setup program.
Extended information:
BIOS is the abbreviation of the English "Basic Input Output System". The literal translation of the Chinese name is "Basic Input Output System" . On IBM PC-compatible systems, it is an industry-standard firmware interface. The term BIOS first appeared in the CP/M operating system in 1975. BIOS is the first software loaded when a personal computer starts up.
In fact, it is a set of programs solidified on a ROM chip on the motherboard of the computer. It stores the most important basic input and output programs of the computer, the self-test program after power-on, and the system self-startup program. Specific information about system settings can be read and written from CMOS. Its main function is to provide the lowest and most direct hardware settings and control for the computer. In addition, the BIOS also provides some system parameters to the operating system. Changes to system hardware are hidden by the BIOS, and programs use BIOS functions instead of directly controlling the hardware. Modern operating systems ignore the abstraction layer provided by the BIOS and control the hardware components directly.
For more related knowledge, please visit the FAQ column!
The above is the detailed content of What does computer security mean?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1664
1664
 14
14
 1423
1423
 52
52
 1317
1317
 25
25
 1268
1268
 29
29
 1246
1246
 24
24
 17 ways to solve the kernel_security_check_failure blue screen
Feb 12, 2024 pm 08:51 PM
17 ways to solve the kernel_security_check_failure blue screen
Feb 12, 2024 pm 08:51 PM
Kernelsecuritycheckfailure (kernel check failure) is a relatively common type of stop code. However, no matter what the reason is, the blue screen error causes many users to be very distressed. Let this site carefully introduce 17 types to users. Solution. 17 solutions to kernel_security_check_failure blue screen Method 1: Remove all external devices When any external device you are using is incompatible with your version of Windows, the Kernelsecuritycheckfailure blue screen error may occur. To do this, you need to unplug all external devices before trying to restart your computer.
 Flask-Security: Adding user authentication and password encryption to Python web applications
Jun 17, 2023 pm 02:28 PM
Flask-Security: Adding user authentication and password encryption to Python web applications
Jun 17, 2023 pm 02:28 PM
Flask-Security: Adding user authentication and password encryption to Python web applications As the Internet continues to develop, more and more applications require user authentication and password encryption to protect the security of user data. In the Python language, there is a very popular web framework-Flask. Flask-Security is an extension library based on the Flask framework, which can help developers easily
 Nginx Proxy Manager Security Analysis and Protection
Sep 28, 2023 pm 01:30 PM
Nginx Proxy Manager Security Analysis and Protection
Sep 28, 2023 pm 01:30 PM
NginxProxyManager Security Analysis and Protection Introduction: In Internet applications, security has always been a crucial issue. As a powerful reverse proxy and load balancing server software, Nginx plays an important role in ensuring the security of network applications. However, with the continuous development of Internet technology and the increasing number of network attacks, how to ensure the security of NginxProxyManager has become an urgent problem to be solved. This article will start from NginxProxyMana
 Spring Security permission control framework usage guide
Feb 18, 2024 pm 05:00 PM
Spring Security permission control framework usage guide
Feb 18, 2024 pm 05:00 PM
In back-end management systems, access permission control is usually required to limit different users' ability to access interfaces. If a user lacks specific permissions, he or she cannot access certain interfaces. This article will use the waynboot-mall project as an example to introduce how common back-end management systems introduce the permission control framework SpringSecurity. The outline is as follows: waynboot-mall project address: https://github.com/wayn111/waynboot-mall 1. What is SpringSecurity? SpringSecurity is an open source project based on the Spring framework, aiming to provide powerful and flexible security for Java applications.
 BubblePal AI companion toy for kids launches with eerily similar concept to sci-fi flick M3GAN
Aug 15, 2024 pm 12:53 PM
BubblePal AI companion toy for kids launches with eerily similar concept to sci-fi flick M3GAN
Aug 15, 2024 pm 12:53 PM
BubblePal, a newly launched AI-based interactive toy, appears to be something that could have inspired the writers of the 2022 sci-fi/horror flick M3GAN, if it hadn’t just been launched last week. Based on large language model (LLM) technology, the ‘
 BubblePal AI companion toy for kids launches with eerily M3GAN-like concept
Aug 14, 2024 pm 09:58 PM
BubblePal AI companion toy for kids launches with eerily M3GAN-like concept
Aug 14, 2024 pm 09:58 PM
BubblePal, a newly launched AI-based interactive toy, appears to be something that could have inspired the writers of the 2022 sci-fi/horror flick M3GAN, if it hadn’t just been launched last week. Based on large language model (LLM) technology, the ‘
 0.0.0.0 Day exploit reveals 18-year-old security flaw in Chrome, Safari, and Firefox
Aug 09, 2024 pm 12:42 PM
0.0.0.0 Day exploit reveals 18-year-old security flaw in Chrome, Safari, and Firefox
Aug 09, 2024 pm 12:42 PM
An 18-year-old vulnerability, known as the "0.0.0.0 Day" flaw, has been disclosed to allow malicious websites to bypass security protocols in major web browsers, including Google Chrome, Mozilla Firefox, and Apple Safari. The flaw primarily
 How SpringBoot Security implements single sign-out and clears all tokens
May 14, 2023 pm 01:43 PM
How SpringBoot Security implements single sign-out and clears all tokens
May 14, 2023 pm 01:43 PM
It is required that systems A, B, and C use the sso service to log in to systems A, B, and C to obtain three tokens: Atoken, Btoken, and Ctoken respectively. After one of the systems actively logs out, the other two systems also log out. All Atoken, Btoken, and Ctoken invalidation record tokenpom file introduces dependence on Redis database dependence on hutool: used to parse tokenorg.springframework.bootspring-boot-starter-data-rediscn.hutoolhutool-all5.7.13 token storage class to implement AuthJdbcToken



