Redis cache learning consistent hash and hash slot
This article brings you relevant knowledge about Redis, which mainly introduces issues related to consistent hashing and hash slots. If expansion occurs or nodes are lost, you will encounter a large number of problems. Data migration issues, consistent hashing and hash slots can avoid this problem. I hope it will be helpful to everyone.

Recommended learning: Redis learning tutorial
If we now have x cache devices, we are deciding which one to put the data in When caching on the device, you can key%x, but if expansion occurs or the node is lost, you need key%(x±y). This will encounter a lot of data migration problems. Consistent hashing and hash slots can avoid this problem. .
Principle of consistent hash
Ordinary hash is the remainder of the number of servers, consistent hash is the remainder of a specific number (2^32), which will not change due to the number of servers. First, we take the remainder of the server's IP or other unique identifier to get a value. This value is the server's position on the hash ring. Then we hash the object to be placed in the server to get a value. We replace the hash with the corresponding server and find the value. If there is no server in the location, check whether the server in the next location knows to find a server that can be stored.
1. Ring space
According to the commonly used hash algorithm, hash the corresponding key into a space with 2 to the power of 32 nodes, that is, 0 ~ (2 of 32)-1 in the digital space. We can imagine this thing as biting its tail, forming a closed loop. 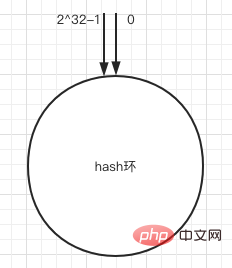
2. Hash the server to the ring
Now that the ring is in place, we need to put the server on the ring. We can do this according to the IP address of the server. Get the number and other unique identifiers, hash them and put them on the ring. 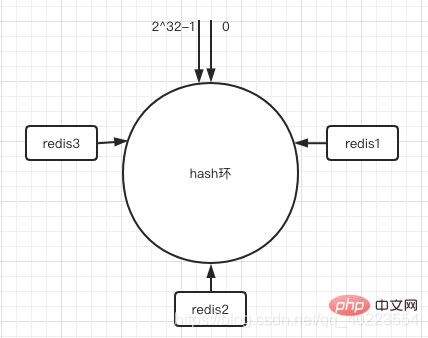
3. Data storage and acquisition
When we need to put a piece of data on the server, we first need to calculate the hash value of the data. Then take the remainder. If the remainder value has a corresponding server on the ring, put it directly. If not, search backwards. 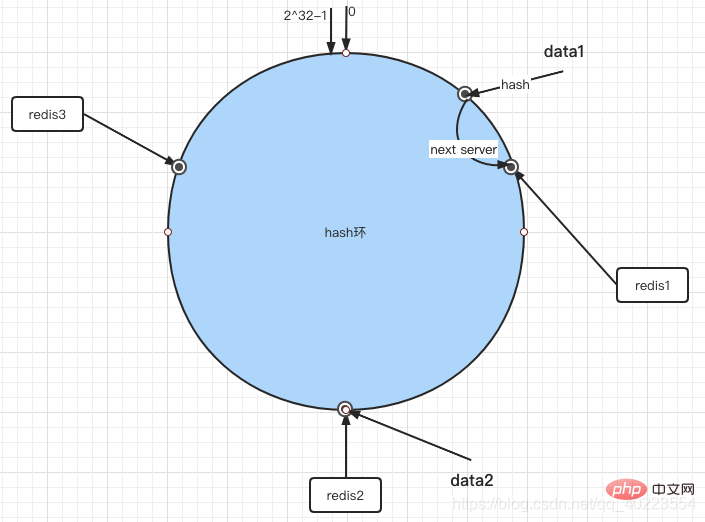
So finally data1 is in redis1 and data2 is in redis2. When we obtain data, we also perform the same process, calculate the hash value of the key, and then obtain the stored server according to the same rules.
4. Deletion and addition of servers
If a redis node hangs up now, then the data in other nodes is still there, and the data in the original node is still there. The data will be redistributed to the next node.
If a new server RedisNeo is added to the environment, RedisNeo is mapped to the ring through the hash algorithm, and according to the clockwise migration rule, the data with the previous hash value between Redis2 and RedisNeo will be migrated to RedisNeo (below) In the figure, RedisNeo is next to Redis2), and other objects still maintain their original storage locations. Through the analysis of the addition and deletion of nodes, the consistent hashing algorithm maintains monotonicity while minimizing data migration. Such an algorithm is very suitable for distributed clusters and avoids a large amount of data migration. , reducing the pressure on the server. 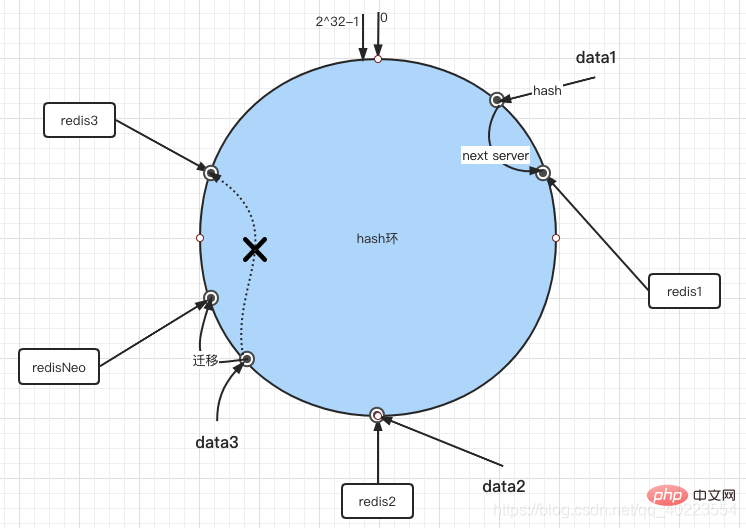
So after redisNeo is added, data3 goes into redisNeo.
5. Balance
So far, consistent hashing can be considered completed, but there is one problem that still needs to be solved, and that is balance. From the figure below, we can see that when there are relatively few server nodes, a problem will arise, that is, a large amount of data will inevitably be concentrated on one node. For example, if you only have two nodes, one at 1 and the other at 10, then it will be very difficult. Obviously the pressure on node 1 is infinite, because only those with hash values between [2,10] will go to node 10, and the others will all go to node 1. In order to solve this data skew problem, consistent hashing The algorithm introduces a virtual node mechanism, that is, multiple hashes are calculated for each service node, and one service node is placed at each calculation result position, which is called a virtual node. The specific method can be to first determine the number of virtual nodes associated with each physical node, and then add the number after the IP or host name. At the same time, the data positioning algorithm remains unchanged, except for the mapping of virtual nodes to actual nodes.
hash slot
The hash slot is used in the redis cluster cluster scheme. The redis cluster cluster does not use a consistent hash scheme, but uses hashing in data sharding. Slots are used for data storage and reading. Redis cluster uses hash slots of data shards for data storage and data reading. The redis cluster has a total of 2^14 (16384) slots. All master nodes will have a slot area such as 0~1000. The number of slots can be migrated. The slave node of the master node does not assign slots and only has read permissions. But note that in the code, the redis cluster performs read and write operations on the master node. It is not the slave node for reading and the master node for writing. When a redis cluster is created for the first time, 16384 slots are evenly distributed by the master node. 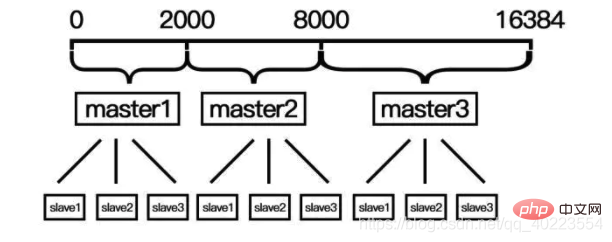
Compared with consistent hashing, you need to manually allocate hash slots when expanding and shrinking, and when deleting the master node, you must give its slave nodes and hash slots to other masters. Node; the hash slot is based on the value of CRC-16 (key) 384 to determine which slot it belongs to.
Recommended learning: Redis tutorial
The above is the detailed content of Redis cache learning consistent hash and hash slot. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1655
1655
 14
14
 1413
1413
 52
52
 1306
1306
 25
25
 1252
1252
 29
29
 1226
1226
 24
24
 How to build the redis cluster mode
Apr 10, 2025 pm 10:15 PM
How to build the redis cluster mode
Apr 10, 2025 pm 10:15 PM
Redis cluster mode deploys Redis instances to multiple servers through sharding, improving scalability and availability. The construction steps are as follows: Create odd Redis instances with different ports; Create 3 sentinel instances, monitor Redis instances and failover; configure sentinel configuration files, add monitoring Redis instance information and failover settings; configure Redis instance configuration files, enable cluster mode and specify the cluster information file path; create nodes.conf file, containing information of each Redis instance; start the cluster, execute the create command to create a cluster and specify the number of replicas; log in to the cluster to execute the CLUSTER INFO command to verify the cluster status; make
 How to clear redis data
Apr 10, 2025 pm 10:06 PM
How to clear redis data
Apr 10, 2025 pm 10:06 PM
How to clear Redis data: Use the FLUSHALL command to clear all key values. Use the FLUSHDB command to clear the key value of the currently selected database. Use SELECT to switch databases, and then use FLUSHDB to clear multiple databases. Use the DEL command to delete a specific key. Use the redis-cli tool to clear the data.
 How to read redis queue
Apr 10, 2025 pm 10:12 PM
How to read redis queue
Apr 10, 2025 pm 10:12 PM
To read a queue from Redis, you need to get the queue name, read the elements using the LPOP command, and process the empty queue. The specific steps are as follows: Get the queue name: name it with the prefix of "queue:" such as "queue:my-queue". Use the LPOP command: Eject the element from the head of the queue and return its value, such as LPOP queue:my-queue. Processing empty queues: If the queue is empty, LPOP returns nil, and you can check whether the queue exists before reading the element.
 How to configure Lua script execution time in centos redis
Apr 14, 2025 pm 02:12 PM
How to configure Lua script execution time in centos redis
Apr 14, 2025 pm 02:12 PM
On CentOS systems, you can limit the execution time of Lua scripts by modifying Redis configuration files or using Redis commands to prevent malicious scripts from consuming too much resources. Method 1: Modify the Redis configuration file and locate the Redis configuration file: The Redis configuration file is usually located in /etc/redis/redis.conf. Edit configuration file: Open the configuration file using a text editor (such as vi or nano): sudovi/etc/redis/redis.conf Set the Lua script execution time limit: Add or modify the following lines in the configuration file to set the maximum execution time of the Lua script (unit: milliseconds)
 How to set the redis expiration policy
Apr 10, 2025 pm 10:03 PM
How to set the redis expiration policy
Apr 10, 2025 pm 10:03 PM
There are two types of Redis data expiration strategies: periodic deletion: periodic scan to delete the expired key, which can be set through expired-time-cap-remove-count and expired-time-cap-remove-delay parameters. Lazy Deletion: Check for deletion expired keys only when keys are read or written. They can be set through lazyfree-lazy-eviction, lazyfree-lazy-expire, lazyfree-lazy-user-del parameters.
 How to use the redis command line
Apr 10, 2025 pm 10:18 PM
How to use the redis command line
Apr 10, 2025 pm 10:18 PM
Use the Redis command line tool (redis-cli) to manage and operate Redis through the following steps: Connect to the server, specify the address and port. Send commands to the server using the command name and parameters. Use the HELP command to view help information for a specific command. Use the QUIT command to exit the command line tool.
 How to implement redis counter
Apr 10, 2025 pm 10:21 PM
How to implement redis counter
Apr 10, 2025 pm 10:21 PM
Redis counter is a mechanism that uses Redis key-value pair storage to implement counting operations, including the following steps: creating counter keys, increasing counts, decreasing counts, resetting counts, and obtaining counts. The advantages of Redis counters include fast speed, high concurrency, durability and simplicity and ease of use. It can be used in scenarios such as user access counting, real-time metric tracking, game scores and rankings, and order processing counting.
 How to optimize the performance of debian readdir
Apr 13, 2025 am 08:48 AM
How to optimize the performance of debian readdir
Apr 13, 2025 am 08:48 AM
In Debian systems, readdir system calls are used to read directory contents. If its performance is not good, try the following optimization strategy: Simplify the number of directory files: Split large directories into multiple small directories as much as possible, reducing the number of items processed per readdir call. Enable directory content caching: build a cache mechanism, update the cache regularly or when directory content changes, and reduce frequent calls to readdir. Memory caches (such as Memcached or Redis) or local caches (such as files or databases) can be considered. Adopt efficient data structure: If you implement directory traversal by yourself, select more efficient data structures (such as hash tables instead of linear search) to store and access directory information




