 Common Problem
Common Problem
 What are the protocols belonging to the application layer in the tcp ip reference model?
What are the protocols belonging to the application layer in the tcp ip reference model?
What are the protocols belonging to the application layer in the tcp ip reference model?
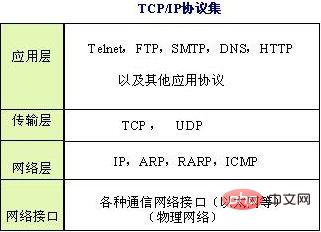
Application layer protocols include: 1. Telnet, which allows users on one machine to log in to a remote machine and perform work; 2. FTP, which provides the ability to move files from one machine to another. method on each machine; 3. SMTP is a protocol that provides email transmission; 4. SNMP is a standard protocol used to manage network nodes in IP networks; 5. DNS is mainly used to transfer familiar The URL is "translated" into an IP address that the computer can understand; 6. HTTP is a request-response protocol used to obtain the home page on the WWW.

The operating environment of this tutorial: Windows 7 system, Dell G3 computer.
TCP/IP is a reference model. It divides the network into four layers based on the OSI reference model, and each layer has its own corresponding protocol.
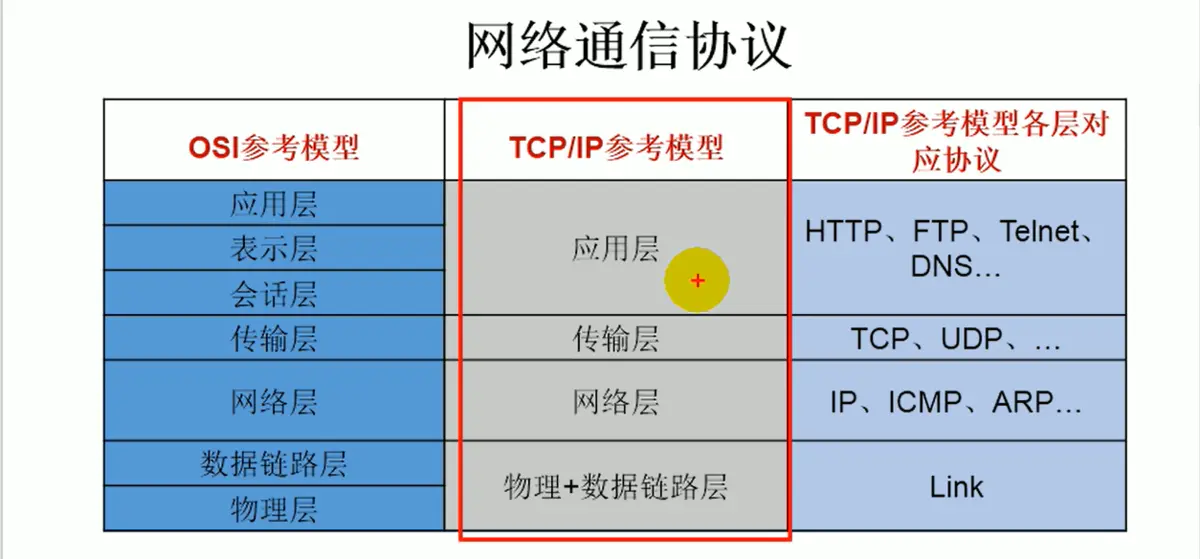
Among them, the application layer deals directly with users and application programs, and is responsible for providing interfaces to software so that programs can use network services. Network services here include file transfer, file management, email message processing, etc.
Typical application layer protocols include Telnet, FTP, SMTP, SNMP, DNS, HTTP, etc.
1. Telnet protocol
The Telnet protocol allows users on one machine to log in to a remote machine and perform work ;
The Telnet protocol is a member of the TCP/IP protocol family and is the standard protocol and main method for Internet remote login services. It provides users with the ability to complete remote host work on their local computer. Use the telnet program on the end user's computer to connect to the server. Terminal users can enter commands into the telnet program, and these commands will be run on the server as if they were entered directly on the server's console. You can control the server locally. To start a telnet session, you must enter your username and password to log into the server. Telnet is a commonly used method to remotely control web servers.
2. FTP protocol
FTP protocol provides a method to move files from one machine to another;
FTP (File Transfer Protocol) is one of the protocols in the TCP/IP protocol group. The FTP protocol consists of two components, one is the FTP server, and the other is the FTP client. The FTP server is used to store files, and users can use the FTP client to access resources located on the FTP server through the FTP protocol. When developing a website, the FTP protocol is usually used to transfer web pages or programs to the web server. In addition, because FTP transmission efficiency is very high, this protocol is generally used when transmitting large files on the network.
By default, the FTP protocol uses TCP ports 20 and 21, of which 20 is used to transmit data and 21 is used to transmit control information. However, whether to use port 20 as the data transmission port is related to the transmission mode used by FTP. If active mode is used, the data transmission port is 20; if passive mode is used, the final port to be used must be decided through negotiation between the server and the client.
3. SMTP protocol
The SMTP protocol is used to send and receive emails;
SMTP is a protocol that provides reliable and effective email transmission. protocol. SMTP is an email service built on the FTP file transfer service. It is mainly used to transfer email information between systems and provide notifications about incoming letters. SMTP is independent of a specific transmission subsystem and only requires the support of a reliable and orderly data flow channel. One of the important features of SMTP is its ability to transmit emails across the network, that is, "SMTP mail relay". Using SMTP, mail transmission can be realized between processing processes on the same network, and mail transmission between a processing process and other networks can also be realized through a relay or gateway.
4. SNMP protocol
SNMP is a standard specially designed for managing network nodes (servers, workstations, routers, switches, HUBS, etc.) in IP networks protocol, which is an application layer protocol. SNMP enables network administrators to manage network performance, identify and resolve network problems, and plan for network growth. Network management systems are notified of network problems by receiving random messages (and event reports) via SNMP.
The predecessor of SNMP is Simple Gateway Monitoring Protocol (SGMP), which is used to manage communication lines. Subsequently, people made great modifications to SGMP, especially adding SMI and MIB that conform to the Internet definition. The improved protocol is the famous SNMP. The SNMP network management framework based on TCP/IP is the current standard in the industry and consists of three main parts, namely the management information structure SMI (Structure of Management Information), the management information base MIB and the management protocol SNMP.
SMI defines the organization and identification of information used by the SNMP framework, and provides templates for MIB to define management objects and use management objects.
MIB defines a collection of management objects that can be accessed through SNMP.
The SNMP protocol is an application layer protocol that defines how the network manager reads and writes the MIB object of the agent process.
MIB in SNMP is a tree-like database. The object managed by MIB is the end node of the tree. Each node has a unique location and unique name. IETF stipulates management information base The object identifier (OID, Object Identifier) is uniquely specified, and its naming rule is that the name of the parent node is used as the prefix of the name of the child node
5, DNS protocol
Domain Name System (Domain Name System, DNS) is a system on the Internet that solves the naming of online machines. Just like when visiting a friend, you first need to know how to get to someone else's house. When a host wants to access another host on the Internet, it must first know its address. The IP address in TCP/IP is composed of four numbers separated by "." The composition is always not as convenient to remember as the name, so the domain name system is used to manage the correspondence between names and IPs.
Although nodes on the Internet can be uniquely identified by IP addresses and can be accessed through IP addresses, even if the 32-bit binary IP address is written as four ten-digit numbers from 0 to 255, Still too long and too difficult to remember. Therefore, people invented the domain name (Domian Name), which can associate an IP address with a group of meaningful characters. When a user visits a website, he or she can enter either the IP address of the website or its domain name. The two are equivalent for access. For example: the IP address of Microsoft's Web server is 207.46.230.229, and its corresponding domain name is www.microsoft.com. Regardless of whether the user enters 207.46.230.229 or www.microsoft.com in the browser, the user can access its Web website.
A company's Web website can be regarded as its online portal, and the domain name is equivalent to its house address. Usually the domain name uses the name or abbreviation of the company. For example, the domain name of Microsoft mentioned above is similar to: IBM's domain name is www.ibm.com, Oracle's domain name is www.oracle.com, Cisco's domain name is www.cisco.com, etc. When people want to visit a company's Web site and don't know its exact domain name, they will always enter the company name first as a test. However, a domain name consisting of a company's name or abbreviation may also be registered by other companies or individuals. There are even some companies or individuals that maliciously register a large number of domain names composed of the names of well-known companies, and then resell them to these companies at high prices to make profits. There are already some arbitration measures for domain name registration disputes, but to control this phenomenon from the source, a complete set of restriction mechanisms is needed, which is not yet available. Therefore, registering a domain name consisting of your own name as early as possible should be something that any company or institution, especially those well-known companies, must pay attention to. Some companies have already made protective registrations for domain names consisting of their own famous brands.
6. HTTP protocol
HTTP protocol is used to obtain the homepage on WWW.
Hyper Text Transfer Protocol (HTTP) is a simple request-response protocol that usually runs on top of TCP. It specifies what kind of messages the client may send to the server and what kind of response it gets. The headers of request and response messages are given in ASCII form; the message contents have a MIME-like format. This simple model was responsible for the early success of the Web because it made development and deployment very straightforward.
For more related knowledge, please visit the FAQ column!
The above is the detailed content of What are the protocols belonging to the application layer in the tcp ip reference model?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1377
1377
 52
52
 What is the full name of tcp/ip?
Nov 29, 2022 pm 04:25 PM
What is the full name of tcp/ip?
Nov 29, 2022 pm 04:25 PM
The full name of tcp/ip is "Transmission Control Protocol/Internet Protocol", which means "Transmission Control Protocol/Internet Protocol" in Chinese. The TCP/IP protocol not only refers to the two protocols TCP and IP, but also refers to a protocol cluster composed of FTP, SMTP, TCP, UDP, IP and other protocols, just because in the TCP/IP protocol, the TCP protocol and the IP protocol The most representative, so it is called TCP/IP protocol.
 How to use PHP and TCP/IP protocol for data communication
Jul 29, 2023 pm 01:46 PM
How to use PHP and TCP/IP protocol for data communication
Jul 29, 2023 pm 01:46 PM
How to use PHP and TCP/IP protocol for data communication Introduction: In the modern Internet era, data communication is a very important aspect. Whether it is communication between a client and a server or communication between different servers, the TCP/IP protocol has always been one of the most commonly used communication protocols. This article will introduce how to use PHP language and TCP/IP protocol for data communication, and provide relevant code examples. 1. Introduction to TCP/IP protocol TCP/IP protocol is the basis of the Internet protocol cluster. It defines
 What is the difference and connection between osi and tcp/ip
Aug 15, 2022 pm 01:55 PM
What is the difference and connection between osi and tcp/ip
Aug 15, 2022 pm 01:55 PM
Differences: 1. TCP/IP is a protocol cluster, while OSI is a model; 2. TCP/IP is a five-layer structure, while OSI is a seven-layer structure; 3. The third layer of TCP/IP only supports the IP protocol, and OSI Supports all network layer protocols. Connection: 1. OSI introduces the concepts of services, interfaces, protocols, and layers, while TCP/IP draws on the concepts of OSI; 2. OSI has models first, then protocols, standards first, and then practices, while TCP/IP IP first has protocols and applications and then proposes a model, which is the reference OSI model.
 What is the difference between tcp and ip
Sep 04, 2023 pm 02:19 PM
What is the difference between tcp and ip
Sep 04, 2023 pm 02:19 PM
TCP and IP are two different protocols in the Internet: 1. TCP is a transport layer protocol, while IP is a network layer protocol; 2. TCP provides functions such as segmentation, sorting, confirmation and retransmission of data packets. , and the IP protocol is responsible for providing source and destination addresses for data packets; 3. TCP is a connection-oriented protocol, while the IP protocol is connectionless; 4. TCP also provides flow control and congestion control.
 What are the protocols belonging to the application layer in the tcp ip reference model?
Jul 04, 2022 am 10:09 AM
What are the protocols belonging to the application layer in the tcp ip reference model?
Jul 04, 2022 am 10:09 AM
Application layer protocols include: 1. Telnet, which allows users on one machine to log in to a remote machine and perform work; 2. FTP, which provides a method to move files from one machine to another; 3. SMTP is a protocol that provides email transmission; 4. SNMP is a standard protocol used to manage network nodes in IP networks; 5. DNS is mainly used to "translate" familiar web addresses into An IP address that a computer can understand; 6. HTTP is a request-response protocol used to obtain the home page on the WWW.
 Common TCP/IP error analysis in Go language
May 31, 2023 pm 10:21 PM
Common TCP/IP error analysis in Go language
May 31, 2023 pm 10:21 PM
The Go language is a growing programming language that is designed to be ideal for implementing network applications with high performance, reliability, and concurrency. When using Go to write network programs related to the TCP/IP protocol, we are prone to encounter various errors, and some common TCP/IP errors will also bring certain difficulties to the debugging of the program. This article will focus on the topic of how to solve common TCP/IP errors in the Go language. 1. EOF error EOF (EndOfFile) error usually
 Dialogue with Chang Chai, the founder of Unbounded AI: The entrepreneurial opportunities of AI are at the application layer丨Innovator
Aug 04, 2023 pm 11:21 PM
Dialogue with Chang Chai, the founder of Unbounded AI: The entrepreneurial opportunities of AI are at the application layer丨Innovator
Aug 04, 2023 pm 11:21 PM
Author | Editor Yu Huiru | Liu Yu The lowering of technical barriers has spawned a large number of AI painting startups, which also means fierce competition. Unbounded AI, who is among them, has personal experience of this. Currently, the number of Unbounded AI users is less than 3 million, which is still far from the annual goal of 10 million. Chang Chai, the founder of Wujie AI, said bluntly that user growth has entered a climbing period and will continue to work hard in the second half of the year. The sluggish growth of unbounded AI is a microcosm of the industry. As an emerging field, the AI painting industry is changing rapidly. At the World Artificial Intelligence Conference a week ago, Alibaba Cloud added a new member to its Tongyi series of large models - Tongyi Wanxiang, which is positioned as a large model for AI painting creation. In addition to Alibaba, large models launched by Baidu, iFlytek, SenseTime and other companies all have Wensheng diagrams and many other features.
 What protocol does ip belong to in computer network architecture?
Aug 29, 2022 pm 04:12 PM
What protocol does ip belong to in computer network architecture?
Aug 29, 2022 pm 04:12 PM
IP belongs to the "network layer" protocol of computer network architecture. IP refers to the Internet Interconnection Protocol, which is a network layer protocol in the TCP/IP system. It can provide information of various protocols to the transport layer, such as TCP, UDP, etc.; IP information packets can be placed in the link layer through Various technologies such as Ethernet and Token Ring network are used for transmission.


