What are cryptosystems with different encryption and decryption keys called?
Cryptosystems with different encryption and decryption keys are called public key encryption systems; public key encryption is also called asymmetric encryption. Public key encryption is asymmetric and uses only one key. Compared with symmetric conventional encryption, it involves the use of two independent keys, one key is called the private key, which is kept secret, and the other key is called the public key and does not need to be kept secret.

The operating environment of this tutorial: Windows 10 system, DELL G3 computer.
What is a cryptographic system with different encryption and decryption keys called?
A cryptographic system with different encryption and decryption keys is called a public key encryption system.
Public key cryptography uses different encryption keys and decryption keys. It is a kind of "it is computationally infeasible to derive the decryption key from the known encryption key." Cryptosystem.
The emergence of public key cryptography is mainly due to two reasons. One is due to the key distribution problem of conventional key cryptography, and the other is due to the need for digital signatures.
Public key encryption is also called asymmetric encryption. Public key encryption is asymmetric. Compared with symmetric conventional encryption that uses only one key, it involves the use of two independent keys.
A key is called a private key, which is kept secret. The other key is called the public key and does not need to be kept secret.
Expand knowledge
The traditional encryption method is to use the same key for encryption and decryption, and the sender and receiver respectively Save, used during encryption and decryption. The main problem with this method is that the generation, injection, storage, management, distribution, etc. of keys are complicated, especially as the number of users increases, the demand for keys increases exponentially. In network communication, the distribution of a large number of keys is a difficult problem to solve.
For example, if there are n users in the system, and password communication needs to be established between every two users, then each user in the system must master (n-1) keys, and the system requires The total number of keys is n*(n-1)/2. For the case of 10 users, each user must have 9 keys, and the total number of keys in the system is 45. For 100 users, each user must have 99 keys, and the total number of keys in the system is 4950. This only considers the case where only one session key is used for communication between users. The generation, management, and distribution of such a large number of keys is indeed a difficult problem to handle.
In 1976, two scholars from Stanford University, Diffie and Herman, proposed the concept of public key cryptography.
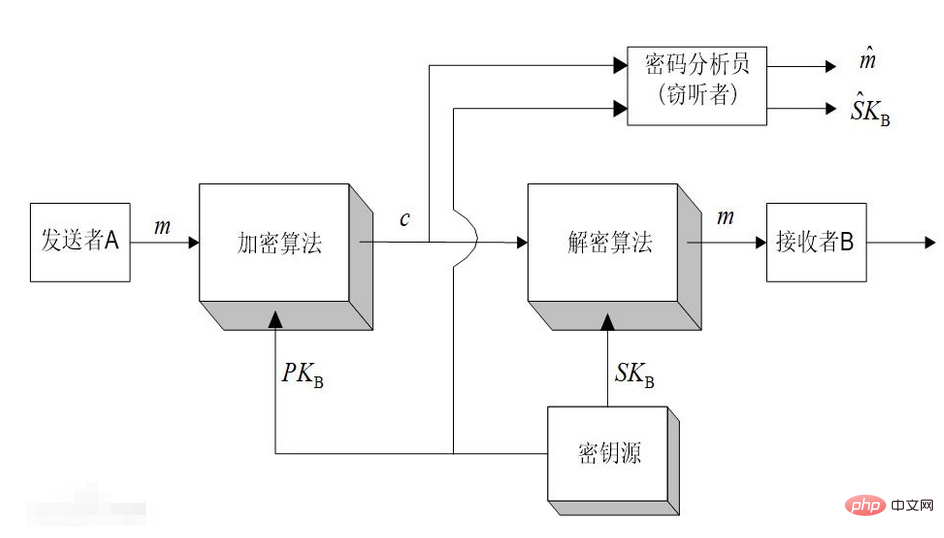
In the public key cryptography system, the encryption key (i.e., the public key) PK is public information, while the decryption key (i.e., the secret key) SK needs to be kept secret. Encryption algorithm E and decryption algorithm D are also public. Although the secret key SK is determined by the public key PK, SK cannot be calculated based on PK.
Different from traditional encryption methods, this technology uses two different keys to encrypt and decrypt information. It is also called an "asymmetric encryption method. Each user has an encryption algorithm that is disclosed to the outside world. E and the externally confidential decryption algorithm D, they must meet the conditions: (1) D is the inverse of E, that is, D[E(X)]=X; (2) Both E and D are easy to calculate. (3) Starting from E It is very difficult to solve D. From the above conditions, it can be seen that under the public key cryptography system, the encryption key is not equal to the decryption key. The encryption key can be made public, so that any user can use the public key to publicize the information transmitted to this user. The key is encrypted and sent, and the only private key saved by the user is confidential, and only it can restore and decrypt the ciphertext. Although the decryption key can theoretically be calculated from the encryption key, in practice this algorithm design It is impossible, or although it can be calculated, it will take a long time and become infeasible. Therefore, making the encryption key public will not endanger the security of the key. The characteristics of the mathematical one-way trapdoor function are It is easy to evaluate in one direction, but its reverse calculation is very difficult. For many functions of the form Y=f(x), for a given independent variable x value, it is easy to calculate the value of the function Y; and from the given Y value, in many cases it is very difficult to calculate the x value according to the functional relationship f(x). For example, it is easier to calculate the product n obtained by multiplying two large prime numbers p and q, but their product n is decomposed into two large prime numbers p and q are very difficult. If n is large enough, the current algorithm cannot be implemented in an effective time.
For more related knowledge, please visit the FAQ column!
The above is the detailed content of What are cryptosystems with different encryption and decryption keys called?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1387
1387
 52
52
 How to solve the problem that Windows 11 prompts you to enter the administrator username and password to continue?
Apr 11, 2024 am 09:10 AM
How to solve the problem that Windows 11 prompts you to enter the administrator username and password to continue?
Apr 11, 2024 am 09:10 AM
When using Win11 system, sometimes you will encounter a prompt that requires you to enter the administrator username and password. This article will discuss how to deal with this situation. Method 1: 1. Click [Windows Logo], then press [Shift+Restart] to enter safe mode; or enter safe mode this way: click the Start menu and select Settings. Select "Update and Security"; select "Restart Now" in "Recovery"; after restarting and entering the options, select - Troubleshoot - Advanced Options - Startup Settings -&mdash
 How to set router WiFi password using mobile phone (using mobile phone as tool)
Apr 24, 2024 pm 06:04 PM
How to set router WiFi password using mobile phone (using mobile phone as tool)
Apr 24, 2024 pm 06:04 PM
Wireless networks have become an indispensable part of people's lives in today's digital world. Protecting the security of personal wireless networks is particularly important, however. Setting a strong password is key to ensuring that your WiFi network cannot be hacked by others. To ensure your network security, this article will introduce in detail how to use your mobile phone to change the router WiFi password. 1. Open the router management page - Open the router management page in the mobile browser and enter the router's default IP address. 2. Enter the administrator username and password - To gain access, enter the correct administrator username and password in the login page. 3. Navigate to the wireless settings page - find and click to enter the wireless settings page, in the router management page. 4. Find the current Wi
 How to use Passkey for your Microsoft account
Feb 19, 2024 am 11:03 AM
How to use Passkey for your Microsoft account
Feb 19, 2024 am 11:03 AM
Passkey is a more advanced and secure way to log in and can be used with a Microsoft account. This article will guide you how to use Passkey in your Microsoft account, introduce its advantages and the differences with passwords. Before we get into the details, we emphasize that if you frequently forget your passwords or need to log in quickly, Passkey will generally be better for you. What is Passkey? How are they different from passwords? Passwords are an advanced and secure authentication method that can replace traditional password logins. Each application has a unique key, ensuring security and preventing threats like phishing. Users can confirm their identity via email and password, or use facial recognition, fingerprint or security key
 Incorrect password, beware BitLocker warning
Mar 26, 2024 am 09:41 AM
Incorrect password, beware BitLocker warning
Mar 26, 2024 am 09:41 AM
This article will explore how to solve the problem of wrong password, especially the need to be careful when dealing with BitLocker warnings. This warning is triggered when an incorrect password is entered multiple times in BitLocker to unlock the drive. Usually, this warning occurs because the system has a policy that limits incorrect login attempts (usually three login attempts are allowed). In this case, the user will receive an appropriate warning message. The complete warning message is as follows: The password entered is incorrect. Please note that continuously entering incorrect passwords will cause the account to be locked. This is to protect the security of your data. If you need to unlock your account, you will need to use a BitLocker recovery key. The password is incorrect, beware the BitLocker warning you receive when you log in to your computer
 How to Remove Windows 10 Lock Screen Password Now
Jan 09, 2024 pm 03:33 PM
How to Remove Windows 10 Lock Screen Password Now
Jan 09, 2024 pm 03:33 PM
After upgrading the win101909 system, some friends may want to cancel their computer lock screen password. If you don’t know what to do, I think we can find the account options in the computer’s settings window. Let’s take a look at the specific methods. How to cancel the lock screen password in win101909: 1. First press Win+I to open the settings interface. 2. Then find the account--login option, and then set it as shown. How to cancel power-on password login in win101909: 1. Execute regedit during running to open the registry and navigate to the following path: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsNT\Cu
 Tutorial on changing wifi password on mobile phone (simple operation)
Apr 26, 2024 pm 06:25 PM
Tutorial on changing wifi password on mobile phone (simple operation)
Apr 26, 2024 pm 06:25 PM
Wireless networks have become an indispensable part of our lives with the rapid development of the Internet. In order to protect personal information and network security, it is very important to change your wifi password regularly, however. To help you better protect your home network security, this article will introduce you to a detailed tutorial on how to use your mobile phone to change your WiFi password. 1. Understand the importance of WiFi passwords. WiFi passwords are the first line of defense to protect personal information and network security. In the Internet age, understanding its importance can better understand why passwords need to be changed regularly. 2. Confirm that the phone is connected to wifi. First, make sure that the phone is connected to the wifi network whose password you want to change before changing the wifi password. 3. Open the phone’s settings menu and enter the phone’s settings menu.
 What should I do if my Win10 password does not meet the password policy requirements? What to do if my computer password does not meet the policy requirements?
Jun 25, 2024 pm 04:59 PM
What should I do if my Win10 password does not meet the password policy requirements? What to do if my computer password does not meet the policy requirements?
Jun 25, 2024 pm 04:59 PM
In the Windows 10 system, the password policy is a set of security rules to ensure that the passwords set by users meet certain strength and complexity requirements. If the system prompts that your password does not meet the password policy requirements, it usually means that your password does not meet the requirements set by Microsoft. standards for complexity, length, or character types, so how can this be avoided? Users can directly find the password policy under the local computer policy to perform operations. Let’s take a look below. Solutions that do not comply with password policy specifications: Change the password length: According to the password policy requirements, we can try to increase the length of the password, such as changing the original 6-digit password to 8-digit or longer. Add special characters: Password policies often require special characters such as @, #, $, etc. I
 How to hash passwords in Python?
Aug 26, 2023 pm 06:57 PM
How to hash passwords in Python?
Aug 26, 2023 pm 06:57 PM
Protecting user passwords is an important aspect of application development. One of the best ways to protect your passwords is to utilize hashing. Hashing is the process of converting a plain text password into an inconvertible, fixed-length sequence of characters. In this article, we will look at how to hash passwords in Python, discussing the language constructs and calculations involved. We will also provide two real executable code examples to demonstrate different password hashing methods. Syntax In order to hash passwords in Python, we will make use of the hashlib module, which provides different hashing algorithms. The basic sentence structure for hashing a secret phrase using hashlib is as follows - importhashlibpassword="my_pa



