 Common Problem
Common Problem
 What is a common protocol that all computers connected to the internet must adhere to?
What is a common protocol that all computers connected to the internet must adhere to?
What is a common protocol that all computers connected to the internet must adhere to?
All computers connected to the Internet must comply with a common protocol called "TCP/IP protocol"; Internet protocol is a network communication model and an entire network transmission protocol family, which is the basic communication architecture of the Internet and is Collectively called the "TCP/IP protocol suite", the two core protocols are TCP (Transmission Control Protocol) and IP (Internet Protocol).

The operating environment of this tutorial: Windows 10 system, DELL G3 computer.
All computers connected to the internet must comply with a common protocol.
All computers connected to the internet must comply with the TCP/IP protocol.
Internet protocol is a network communication model and an entire network transmission protocol family, which is the basic communication architecture of the Internet. It is often commonly referred to as the TCP/IP protocol suite, or TCP/IP for short. Because the two core protocols of this protocol family: TCP (Transmission Control Protocol) and IP (Internet Protocol), are the earliest standards adopted in the family.
TCP/IP provides a point-to-point link mechanism that standardizes how data should be encapsulated, addressed, transmitted, routed, and received at the destination. It abstracts the software communication process into four abstraction layers, which implement different communication protocols respectively. Various protocols under the protocol family are classified into these four hierarchical structures according to their different functions, and are often regarded as a simplified seven-layer OSI model.
TCP/IP protocol
A protocol cluster that can realize information transmission between multiple different networks
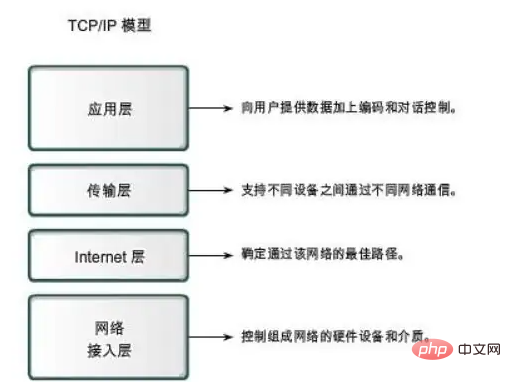
TCP/IP (Transmission Control Protocol/Internet Protocol) refers to a protocol that can transmit information between multiple different networks cluster. TCP/IP protocol not only refers to the two protocols TCP and IP, but refers to a protocol cluster composed of FTP, SMTP, TCP, UDP, IP and other protocols, just because in the TCP/IP protocol, the TCP protocol and IP protocol The most representative, so it is called TCP/IP protocol.
TCP/IP transmission protocol, namely transmission control/network protocol, is also called network communication protocol. It is the most basic communication protocol used in networks. The TCP/IP transport protocol stipulates the standards and methods for communication between various parts of the Internet. Moreover, TCP/IP transmission protocols are two important protocols that ensure timely and complete transmission of network data information. The TCP/IP transmission protocol is strictly a four-layer architecture, including the application layer, transport layer, network layer and data link layer.
TCP/IP protocol is the most basic protocol of the Internet. The main protocols of the application layer include Telnet, FTP, SMTP, etc., which are used to receive data from the transport layer or transmit data according to different application requirements and methods. to the transport layer; the main protocols of the transport layer are UDP and TCP, which are the channels through which users use the platform and the internal data of the computer information network to realize data transmission and data sharing; the main protocols of the network layer are ICMP, IP, and IGMP. Responsible for the transmission of data packets in the network; and the network access layer, also called the network interface layer or data link layer, the main protocols are ARP, RARP, the main function is to provide link management error detection, information details related to different communication media Perform effective processing, etc.
Features:
The TCP/IP protocol can develop rapidly and become a de facto standard because it just meets the needs of data communication around the world. It has the following characteristics:
The protocol standard is completely open, can be used by users for free, and is independent of specific computer hardware and operating systems.
Independent of the network hardware system, it can run on the wide area network and is more suitable for the Internet.
Network addresses are uniformly assigned, and each device and terminal in the network has a unique address.
High-level protocol standardization can provide a variety of reliable network services.
For more related knowledge, please visit the FAQ column!
The above is the detailed content of What is a common protocol that all computers connected to the internet must adhere to?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1386
1386
 52
52
 Which protocol does vivo fast charging belong to?
Sep 06, 2022 pm 02:43 PM
Which protocol does vivo fast charging belong to?
Sep 06, 2022 pm 02:43 PM
There are two main protocols for vivo fast charging: 1. "QC 2.0" fast charging protocol. "QC2.0" is "Quick Charge 2.0" technology. It is version 2.0 of fast charging technology released by Qualcomm. It can output 5V, 9V, and 12V. , 20V four voltage groups; 2. PD fast charging protocol is a fast charging specification formulated by the "USB-IF" organization. It is one of the current mainstream fast charging protocols and can make the current default maximum power "5V/2A" The "type-c" interface is increased to 100W.
 What is the maximum watt of PD3.0 fast charging protocol?
Nov 08, 2022 pm 04:04 PM
What is the maximum watt of PD3.0 fast charging protocol?
Nov 08, 2022 pm 04:04 PM
The PD3.0 fast charging protocol supports up to “100W”. In November 2015, USB PD fast charging ushered in a major version update, entering the USB PD3.0 fast charging era; the PD3.0 protocol supports 5V3A, 9V3A, 12V3A, 15V3A, 20V5A output, and the maximum power can reach 100W. Not only can It can be used to charge mobile phones, and can also be used to power laptops or monitors.
 What are the 5 industrial communication protocols?
Sep 28, 2022 am 11:52 AM
What are the 5 industrial communication protocols?
Sep 28, 2022 am 11:52 AM
5 types of industrial communication protocols: 1. Modbus protocol, which is a universal language used in electronic controllers; 2. RS-232 protocol, which is a serial physical interface standard; 3. RS-485 protocol, which is based on RS232 Developed on the basis of; 4. HART protocol is a communication protocol used between on-site intelligent instruments and control room equipment; 5. MPI protocol is a cross-language communication protocol used to write parallel computers.
 SOAP Protocol Guide in PHP
May 20, 2023 pm 07:10 PM
SOAP Protocol Guide in PHP
May 20, 2023 pm 07:10 PM
With the continuous development of Internet technology, more and more enterprise-level applications need to provide interfaces to other applications to realize the interaction of data and business. In this case, we need a reliable protocol to transmit data and ensure data integrity and security. SOAP (Simple Object Access Protocol) is an XML-based protocol that can be used to implement communication between applications in a Web environment. As a popular web programming language, PHP
 What is the qc4+ fast charging protocol?
Aug 18, 2022 pm 03:49 PM
What is the qc4+ fast charging protocol?
Aug 18, 2022 pm 03:49 PM
The QC4+ fast charging protocol is a combination of the USB PD PPS protocol and the QC3.0/2.0 fast charging protocol. It is a multi-functional, multi-protocol fast charging technology. The QC4+ charging protocol is compatible with USB PD3.0 (PPS) and is downwardly compatible with USB PD2.0, QC3.0, QC2.0, BC1.2 and other protocols. The first prerequisite for supporting USB PD and QC4+ is the support of USB-C interfaces at both ends and the power negotiation message based on the CC (configuration channel) in the USB-C interface.
 Windows will retire TLS 1.0 and TLS 1.1 in the near future
Aug 12, 2023 am 11:37 AM
Windows will retire TLS 1.0 and TLS 1.1 in the near future
Aug 12, 2023 am 11:37 AM
Microsoft plans to disable Transport Layer Security (TLS) protocol versions 1.0 and 1.1 in Windows. The company announced the news on its technology community website on March 1, 2023. These two protocols date back to 1999 (TLS1.0) and 2006 (TLS1.1) and have since been surpassed by newer versions TLS1.2 and TLS1.3. Microsoft noted that security issues were discovered in older protocol versions, and "Internet standards and regulators have deprecated or disallowed TLS versions 1.0 and 1.1 in response. Over the years, usage of TLS 1.0 and 1.1 has declined significantly. , Microsoft believes the time has come to disable both protocols. Mic
 What technology does the x.25 protocol use?
Jul 18, 2022 pm 04:05 PM
What technology does the x.25 protocol use?
Jul 18, 2022 pm 04:05 PM
The "x.25" protocol uses packet switching technology; the "x.25" protocol is a computer-oriented data communication network, consisting of basic equipment such as transmission lines, packet switches, remote concentrators and packet terminals, and adopts a layered architecture , negotiation, control and information transmission of information exchange are carried out between the peer layers of the interface through the communication protocol between the peer layers.
 Concise and easy to understand: in-depth analysis of the meaning of pip protocol
Feb 02, 2024 pm 01:10 PM
Concise and easy to understand: in-depth analysis of the meaning of pip protocol
Feb 02, 2024 pm 01:10 PM
To deeply analyze the meaning of the pip protocol, specific code examples are required. Introduction: In the Python world, pip (i.e. pipinstall) is our preferred way to install and manage third-party libraries. It is a Python package management tool. It is widely used in the development process because of its simplicity, efficiency, ease of use and convenience. This article will deeply analyze the meaning of the pip protocol, demonstrate the important role and usage of pip through specific code examples, and help readers better understand and use pip. 1. pip protocol


