What structure does the current mainstream computer system use?
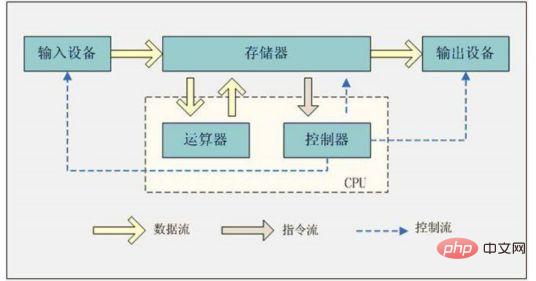
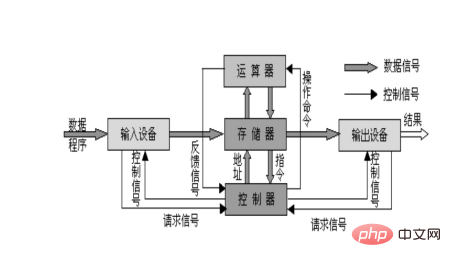
The computer system structure adopts the "Von Neumann" structure. The von Neumann structure, also known as the Princeton structure, is a memory structure that combines program instruction memory and data memory. It uses binary logic, program storage and execution, and the computer is composed of five parts (operator, controller, memory , input device, output device); the characteristics of this structure are "program storage, shared data, sequential execution", which requires the CPU to retrieve instructions and data from the memory to perform corresponding calculations.

The operating environment of this tutorial: Windows 7 system, Dell G3 computer.
The current mainstream computer system structure adopts the "Von Neumann" structure.
The Von Neumann structure, also known as the Princeton structure, is a memory structure that combines program instruction memory and data memory. The program instruction storage address and the data storage address point to different physical locations in the same memory, so the width of the program instructions and data are the same. For example, the program instructions and data of Intel's 8086 central processor are both 16 bits wide.
The mathematician von Neumann proposed three basic principles for computer manufacturing, namely the use of binary logic, program storage and execution, and the computer is composed of five parts (operator, controller, memory, input device, output device), this theory is called the von Neumann architecture.
Development History
Before the birth of computers, people had bottlenecks in the accuracy and quantity of calculations. For computers like this The demand for machines was very strong, and von Neumann's logic and computer ideas guided him to design and build the first general-purpose electronic computer in history. His computer theory is mainly influenced by his own mathematical foundation and is highly mathematical and logical. He generally calls this theory "the logical theory of computers". His idea of computer stored programs was another of his great innovations. By placing stored programs in internal memory, he successfully solved the problems of too small computer storage capacity and too slow computing speed at that time.
During World War II, the U.S. military required laboratories to provide it with computationally intensive calculation results. So there was the idea of developing an electronic computer. Faced with this demand, the United States immediately formed a research and development team, including many engineers and physicists, to try to develop the world's first computer (later called the ENIAC machine). Although the most advanced electronic technology is adopted, there is a lack of principle guidance. At this time, von Neumann appeared. He brought up a crucial aspect: the logical structure of computers. Von Neumann started with logic and led the team to improve ENIAC. His logic design has the following characteristics:
(1) Separate the circuit and logic designs to create optimal conditions for computer construction;
(2) Combine the personal nervous system and computer Combined together, a new concept is proposed, namely biological computers.
Even though the ENIAC machine was realized with the top technology in the United States and even the world at that time, it used temporary storage and determined the arithmetic unit as the foundation. Therefore, it had many shortcomings, such as limited storage space, inability to store programs, etc., and the operation The speed is slow and inherently irrational. Von Neumann formulated the following optimization plan based on this premise:
(1) Use binary to perform operations, which greatly speeds up the computer;
(2) Store the program, that is, through the computer Internal memory stores calculation programs. In this way, programmers only need to write relevant computing instructions through the memory, and the computer can immediately perform computing operations, greatly speeding up computing efficiency.
Von Neumann structural diagram
Features
The basic structural form followed by the development of modern computers It is always a von Neumann machine structure. The characteristics of this structure are "program storage, shared data, and sequential execution", which requires the CPU to retrieve instructions and data from the memory to perform corresponding calculations. The main features are:
(1) Single processor structure, the machine is centered on the arithmetic unit;
(2) Adopts the idea of program storage;
(3 ) Instructions and data can participate in operations;
(4) Data is expressed in binary;
(5) Completely separates software and hardware;
(6) Instructions are represented by Composed of operation codes and operands;
(7) instructions are executed sequentially.
Limitations
The speed of information exchange between the CPU and shared memory has become the main factor affecting system performance, and the increase in information exchange speed is restricted by the speed of the storage element , memory performance and structure and many other conditions.
The stored program method of the traditional von Neumann computer architecture makes the system dependent on memory. The speed of the CPU accessing the memory restricts the speed of the system. The technical level of integrated circuit IC chips determines the performance of memory and other hardware. In order to improve the performance of hardware, chip manufacturing companies represented by Intel Corporation have made great efforts in integrated circuit production and have achieved great technical results. Now every 18 months, the integration level of ICs doubles, the performance doubles, and the product price drops by half. This is the so-called "Moore's Law." This pattern has lasted for more than 40 years and is expected to continue for several more years. However, two fundamental limitations faced by electronic products exist objectively: the speed of light and the atomic properties of materials. First of all, the speed of information propagation will ultimately depend on the speed of electron flow. The flow of electronic signals in components and wires will cause time delays. Too high a frequency will cause signal distortion, so the speed of components cannot be infinitely increased until it reaches the speed of light. Second, the electronic signals of the computer are stored in transistors represented by silicon crystal materials. The improvement in integration is that the transistors become smaller, but the transistors cannot be smaller than the volume of one silicon atom. As semiconductor technology gradually approaches the size limit of silicon processes, the rules derived from Moore's Law will no longer apply.
Analysis of the structural flaws of von Neumann computer architecture:
(1) Instructions and data are stored in the same memory, resulting in the system's over-reliance on memory. If the development of storage devices is hindered, the development of systems will also be hindered.
(2) Instructions are stored in the memory in the order of their execution, and the instruction counter PC specifies the unit address where the instruction to be executed is located. Then fetch the instructions to perform the operation task. So the execution of instructions is serial. Affects the speed of system execution.
(3) The memory is linearly addressed according to address access, and the address access is arranged in sequence, which is conducive to storage and execution of machine language instructions, and is suitable for numerical calculations. However, the memory represented by high-level language is a set of named variables. Variables are called by name and not accessed by address. There is a large semantic gap between machine language and high-level language, which is called the von Neumann semantic gap. Eliminating semantic gaps has become a major problem facing the development of computers.
(4) Von Neumann architecture computers were born for arithmetic and logical operations. Currently, they have reached high speed and accuracy in numerical processing, while the development of non-numeric processing applications is slow. A major breakthrough in architecture is required.
(5) The traditional von Neumann type structure belongs to the control drive method. It executes instruction codes to process numerical codes. As long as the instructions are clear and the input data is accurate, it will run automatically after starting the program and the results will be expected. Once there are errors in instructions and data, the machine will not actively modify the instructions and improve the program. However, much information in human life is vague, and the occurrence, development and results of events are unpredictable. The intelligence of modern computers cannot cope with such complex tasks.
For more related knowledge, please visit the FAQ column!
The above is the detailed content of What structure does the current mainstream computer system use?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1393
1393
 52
52
 1205
1205
 24
24
 Remote Desktop cannot authenticate the remote computer's identity
Feb 29, 2024 pm 12:30 PM
Remote Desktop cannot authenticate the remote computer's identity
Feb 29, 2024 pm 12:30 PM
Windows Remote Desktop Service allows users to access computers remotely, which is very convenient for people who need to work remotely. However, problems can be encountered when users cannot connect to the remote computer or when Remote Desktop cannot authenticate the computer's identity. This may be caused by network connection issues or certificate verification failure. In this case, the user may need to check the network connection, ensure that the remote computer is online, and try to reconnect. Also, ensuring that the remote computer's authentication options are configured correctly is key to resolving the issue. Such problems with Windows Remote Desktop Services can usually be resolved by carefully checking and adjusting settings. Remote Desktop cannot verify the identity of the remote computer due to a time or date difference. Please make sure your calculations
 2024 CSRankings National Computer Science Rankings Released! CMU dominates the list, MIT falls out of the top 5
Mar 25, 2024 pm 06:01 PM
2024 CSRankings National Computer Science Rankings Released! CMU dominates the list, MIT falls out of the top 5
Mar 25, 2024 pm 06:01 PM
The 2024CSRankings National Computer Science Major Rankings have just been released! This year, in the ranking of the best CS universities in the United States, Carnegie Mellon University (CMU) ranks among the best in the country and in the field of CS, while the University of Illinois at Urbana-Champaign (UIUC) has been ranked second for six consecutive years. Georgia Tech ranked third. Then, Stanford University, University of California at San Diego, University of Michigan, and University of Washington tied for fourth place in the world. It is worth noting that MIT's ranking fell and fell out of the top five. CSRankings is a global university ranking project in the field of computer science initiated by Professor Emery Berger of the School of Computer and Information Sciences at the University of Massachusetts Amherst. The ranking is based on objective
 What is e in computer
Aug 31, 2023 am 09:36 AM
What is e in computer
Aug 31, 2023 am 09:36 AM
The "e" of computer is the scientific notation symbol. The letter "e" is used as the exponent separator in scientific notation, which means "multiplied to the power of 10". In scientific notation, a number is usually written as M × 10^E, where M is a number between 1 and 10 and E represents the exponent.
 Fix: Microsoft Teams error code 80090016 Your computer's Trusted Platform module has failed
Apr 19, 2023 pm 09:28 PM
Fix: Microsoft Teams error code 80090016 Your computer's Trusted Platform module has failed
Apr 19, 2023 pm 09:28 PM
<p>MSTeams is the trusted platform to communicate, chat or call with teammates and colleagues. Error code 80090016 on MSTeams and the message <strong>Your computer's Trusted Platform Module has failed</strong> may cause difficulty logging in. The app will not allow you to log in until the error code is resolved. If you encounter such messages while opening MS Teams or any other Microsoft application, then this article can guide you to resolve the issue. </p><h2&
 What does computer cu mean?
Aug 15, 2023 am 09:58 AM
What does computer cu mean?
Aug 15, 2023 am 09:58 AM
The meaning of cu in a computer depends on the context: 1. Control Unit, in the central processor of a computer, CU is the component responsible for coordinating and controlling the entire computing process; 2. Compute Unit, in a graphics processor or other accelerated processor, CU is the basic unit for processing parallel computing tasks.
 Unable to open the Group Policy object on this computer
Feb 07, 2024 pm 02:00 PM
Unable to open the Group Policy object on this computer
Feb 07, 2024 pm 02:00 PM
Occasionally, the operating system may malfunction when using a computer. The problem I encountered today was that when accessing gpedit.msc, the system prompted that the Group Policy object could not be opened because the correct permissions may be lacking. The Group Policy object on this computer could not be opened. Solution: 1. When accessing gpedit.msc, the system prompts that the Group Policy object on this computer cannot be opened because of lack of permissions. Details: The system cannot locate the path specified. 2. After the user clicks the close button, the following error window pops up. 3. Check the log records immediately and combine the recorded information to find that the problem lies in the C:\Windows\System32\GroupPolicy\Machine\registry.pol file
 What should I do if steam cannot connect to the remote computer?
Mar 01, 2023 pm 02:20 PM
What should I do if steam cannot connect to the remote computer?
Mar 01, 2023 pm 02:20 PM
Solution to the problem that steam cannot connect to the remote computer: 1. In the game platform, click the "steam" option in the upper left corner; 2. Open the menu and select the "Settings" option; 3. Select the "Remote Play" option; 4. Check Activate the "Remote Play" function and click the "OK" button.
 Python script to log out of computer
Sep 05, 2023 am 08:37 AM
Python script to log out of computer
Sep 05, 2023 am 08:37 AM
In today's digital age, automation plays a vital role in streamlining and simplifying various tasks. One of these tasks is to log off the computer, which is usually done manually by selecting the logout option from the operating system's user interface. But what if we could automate this process using a Python script? In this blog post, we'll explore how to create a Python script that can log off your computer with just a few lines of code. In this article, we'll walk through the step-by-step process of creating a Python script for logging out of your computer. We'll cover the necessary prerequisites, discuss different ways to log out programmatically, and provide a step-by-step guide to writing the script. Additionally, we will address platform-specific considerations and highlight best practices



