Recommended learning: Redis video tutorial
Through EXPIRE command or PEXPIRE command, the client can set the survival time for a certain key in the database with seconds or milliseconds precision. After the specified number of seconds or milliseconds, the server will automatically delete the key with a survival time of 0.
The SETEX command can set an expiration time for the key while setting a string key (can only be used for string keys)

With the EXPIRE command and The PEXPIRE command is similar. The client can use the EXPIREAT command or the PEXPIREAT command to set the expiration time for a key in the database with seconds or milliseconds precision.
The expiration time is a UNIX timestamp. When the expiration time of the key comes , the server will automatically delete the key from the database
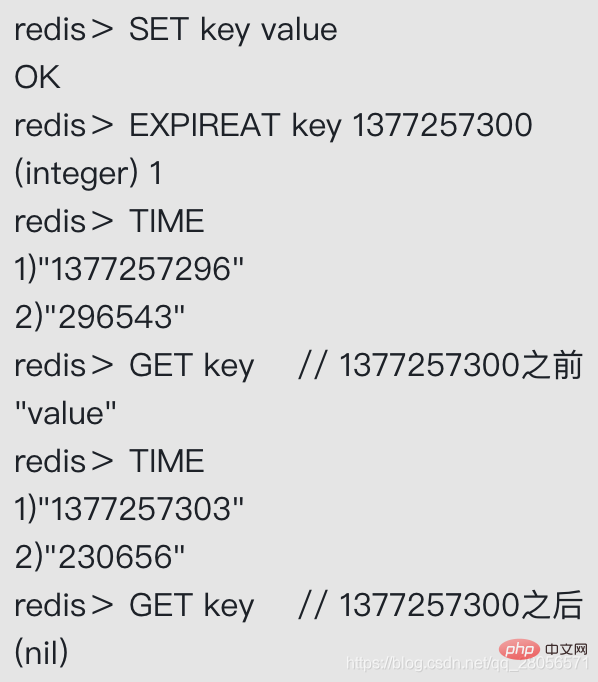
The TTL command and the PTTL command accept a key with a survival time or expiration time, and return the remaining survival time of the key , that is, returns how long it will take before the key is automatically deleted by the server
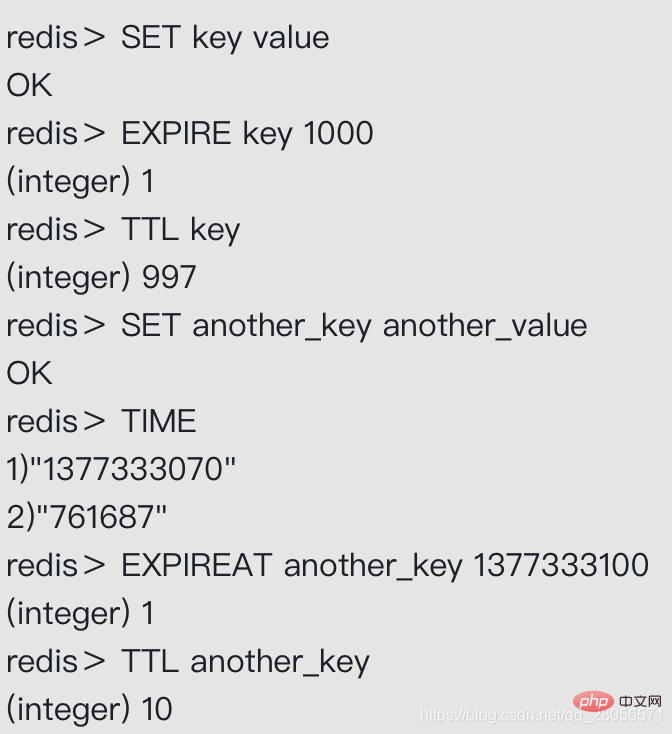
Redis has four different commands that can be used to set the key’s survival time (How long the key can exist) or expiration time (when will the key be deleted):
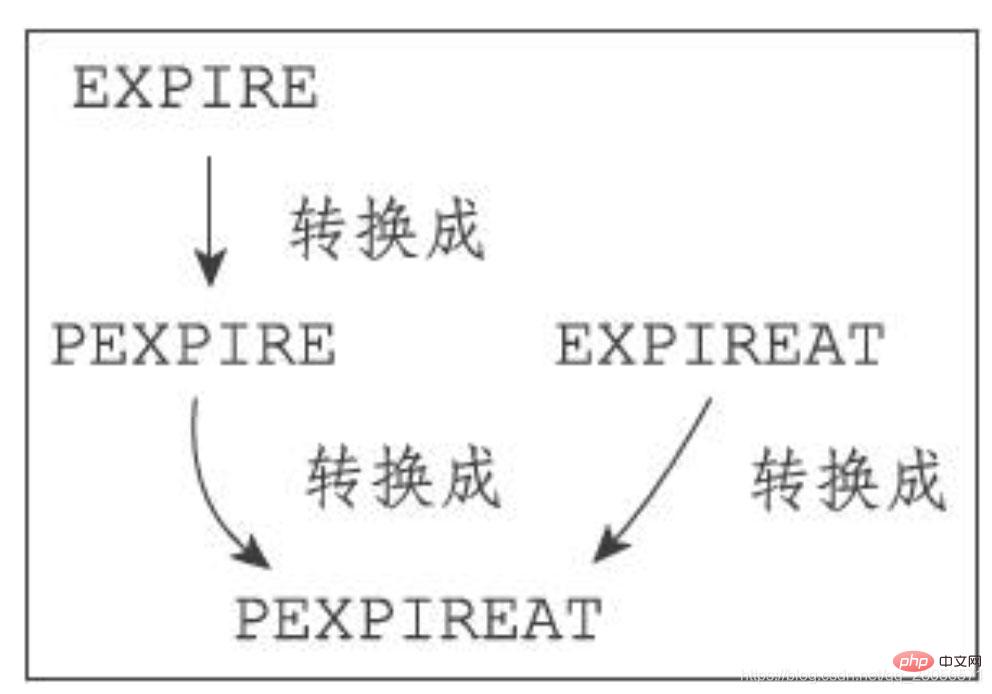
Although there are many different units and different forms of setting commands, in fact, the three commands EXPIRE, PEXPIRE, and EXPIREAT are all implemented using the PEXPIREAT command:
No matter which of the above four commands is executed by the client, after conversion, the final execution effect is the same as executing the PEXPIREAT command.
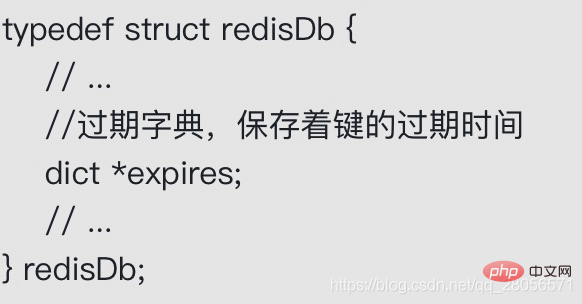
The expires dictionary of the redisDb structure saves the expiration time of all keys in the database. We call this dictionary the expires dictionary
The key of the expires dictionary is a pointer , this pointer points to a key object in the key space (that is, a database key).
The value of the expiration dictionary is an integer of long long type. This integer stores the expiration time of the database key pointed to by the key - a UNIX timestamp with millisecond precision.
The following figure shows an example of a database with an expired dictionary. In this example, the key space stores all key-value pairs in the database, while the expired dictionary stores The expiration time of the database key.
For the convenience of display, the alphabet key object and book key object are repeated twice in the key space and expiration dictionary in the figure. In practice, the keys of the key space and the keys of the expiration dictionary point to the same key object, so there will not be any duplicate objects and no space will be wasted.
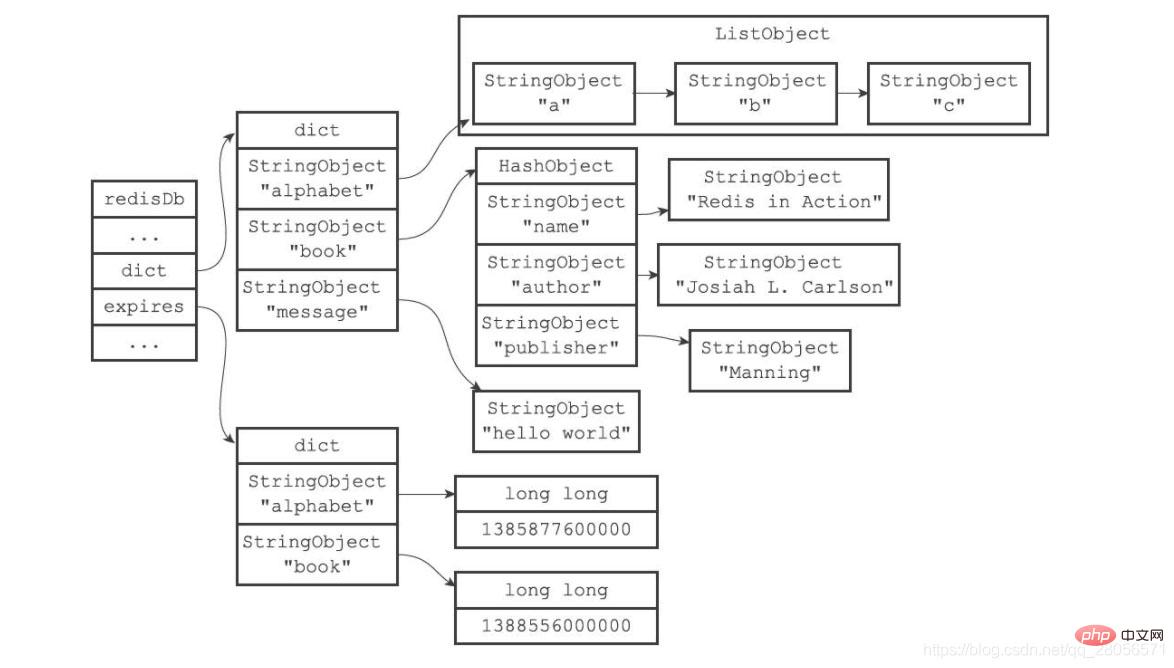
The expired dictionary in the figure saves two key-value pairs:
The key of the first key-value pair is alphabet The key object has a value of 1385877600000, which means that the expiration time of the database key alphabet is 1385877600000 (0:00 on December 1, 2013).
The key of the second key-value pair is the book key object, and the value is 1388556000000, which means that the expiration time of the database key book is 1388556000000 (0:00 on January 1, 2014). When the client executes the PEXPIREAT command (or the other three commands that are converted into PEXPIREAT commands) to set an expiration time for a database key, the server associates the given database key and expiration time in the database's expiration dictionary.
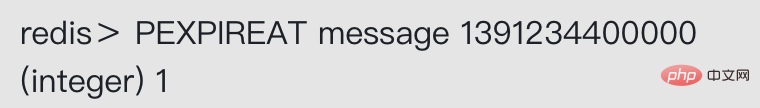
After the server executes the following command
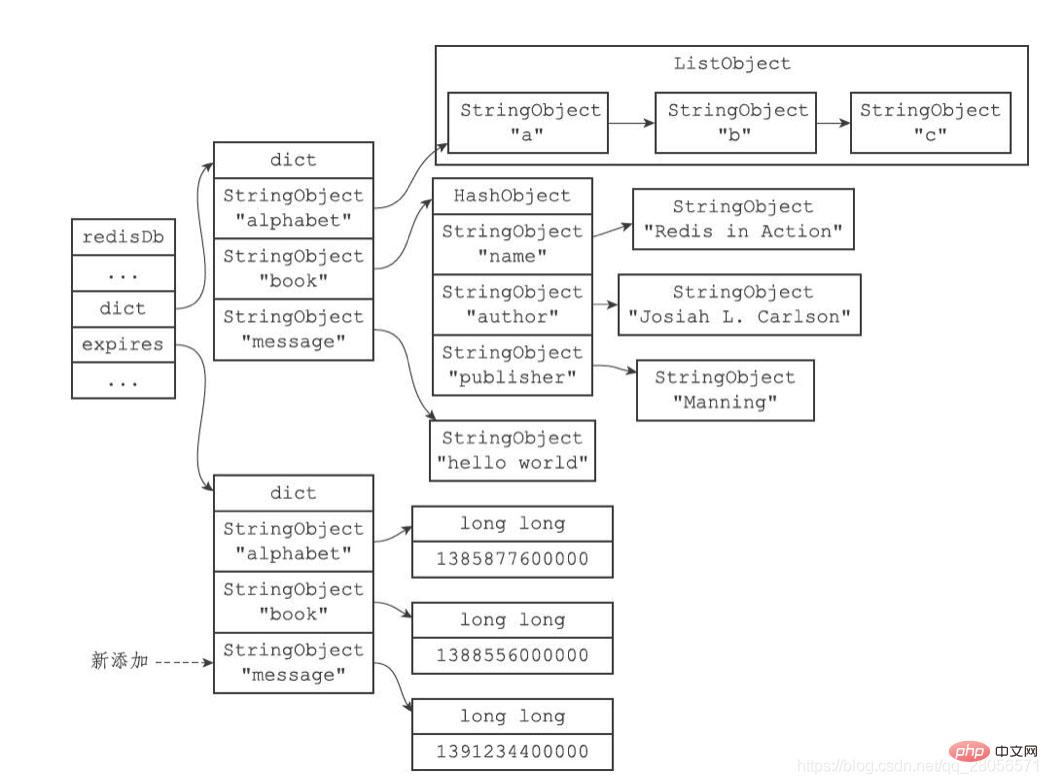
The expired dictionary will add a key-value pair, where the key is the message key object and the value is 1391234400000 (0:00 on February 1, 2014), as shown in the figure
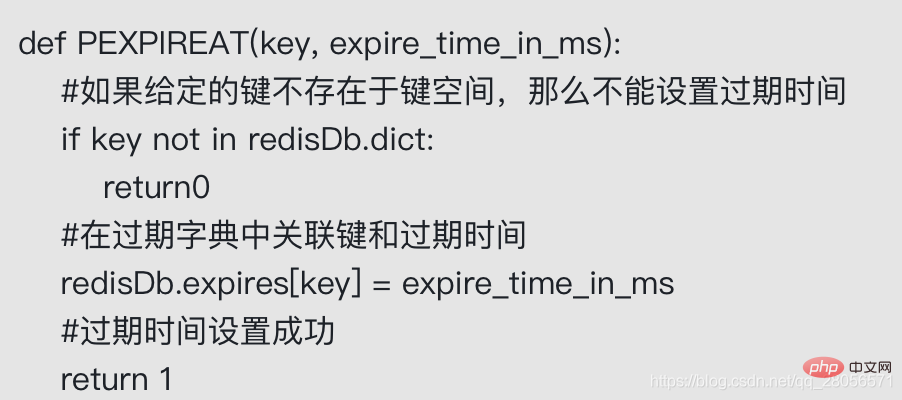
The following is the pseudocode definition of the PEXPIREAT command
The PERSIST command can remove the expiration time of a key
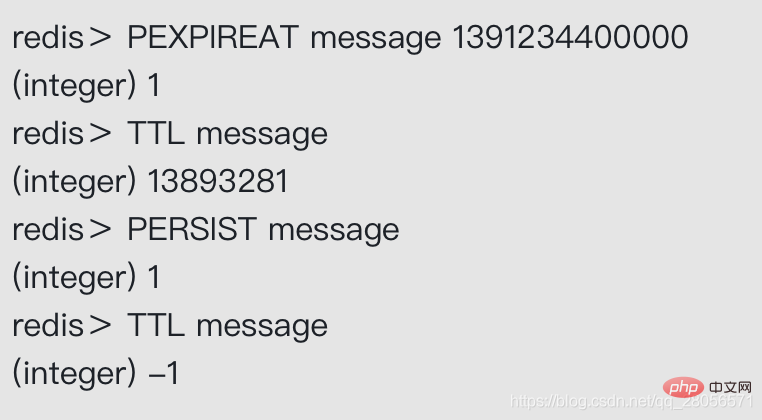
The PERSIST command is the reverse operation of the PEXPIREAT command: the PERSIST command searches for a given key in the expiration dictionary and disassociates the key and value (expiration time) in the expiration dictionary.
Through the expiration dictionary, the program can use the following steps to check whether a given key has expired:
1) Check whether the given key exists in the expiration dictionary : If it exists, get the expiration time of the key.
2) Check whether the current UNIX timestamp is greater than the expiration time of the key: if so, then the key has expired; otherwise, the key has not expired. This process can be described with pseudocode:

For a key alphabet with an expiration time of 1385877600000 (0:00 on December 1, 2013):
If the current time is 1383282000000 (0:00 on November 1, 2013), then calling is_expired(alphabet) will return False because the current time is less than the expiration time of the alphabet key.
On the other hand, if the current time is 1385964000000 (0:00 on December 2, 2013), then calling is_expired(alphabet) will return True because the current time is greater than the expiration time of the alphabet key.
Recommended learning: Redis video tutorial
The above is the detailed content of Analysis of the principle of setting survival and expiration time in Redis. For more information, please follow other related articles on the PHP Chinese website!
 Commonly used database software
Commonly used database software
 What are the in-memory databases?
What are the in-memory databases?
 Which one has faster reading speed, mongodb or redis?
Which one has faster reading speed, mongodb or redis?
 How to use redis as a cache server
How to use redis as a cache server
 How redis solves data consistency
How redis solves data consistency
 How do mysql and redis ensure double-write consistency?
How do mysql and redis ensure double-write consistency?
 What data does redis cache generally store?
What data does redis cache generally store?
 What are the 8 data types of redis
What are the 8 data types of redis