What is the role of encryption on the Internet?
The role of encryption on the Internet is to prevent useful or private information from being intercepted and stolen on the Internet. The encrypted password is unreadable even if it is obtained by a hacker. The encrypted bidding document cannot be decrypted without the recipient's private key. The bidding document becomes a lot of garbled code without any practical meaning, so even if it is stolen, there will be no trace. loss; so encryption is very important to protect files.

The operating environment of this tutorial: Windows 7 system, Dell G3 computer.
The rapid development of network technology has facilitated our daily lives, accelerated work efficiency, and enhanced communication. The emergence of the Internet has indeed brought us a lot of convenience, but network security issues have always troubled us. Viruses and hackers are rampant, and various threats are constantly coming out. Network security issues have also become a concern of society. Key issues. File transmission security is one of the security issues of public concern. A file may contain many secrets. Once stolen by hackers, the loss will be unimaginable.
What is file encryption:
File encryption is simply to process the original plaintext file according to a certain algorithm to make it an unreadable piece of code. , often called "ciphertext". The original content can only be displayed after entering the corresponding key. In this way, the purpose of protecting the data from being illegally stolen and read is achieved. The reverse of this process is decryption, the process of converting the encoded information into its original data.
Why should we encrypt files:
We know that there are many unsafe factors in file transfer and email business transactions on the Internet, especially for some large companies and Some confidential documents are transmitted over the network. And this insecurity is inherent in the TCP/IP protocol, the foundation of the Internet, including some TCP/IP-based services; so in order to ensure security, we must encrypt files.
The role of encryption on the Internet is to prevent useful or private information from being intercepted and stolen on the Internet. A simple example is the transmission of passwords. Computer passwords are extremely important. Many security protection systems are based on passwords. In a sense, the leakage of passwords means the complete collapse of their security systems. When logging in through the network, the typed password is transmitted to the server in clear text, and eavesdropping on the network is extremely easy, so it is very likely that hackers will steal the user's password. If the user is a Root user or Administrator users, the consequences will be extremely serious.
The solution to the above problem is encryption. The encrypted password is unreadable even if it is obtained by a hacker. The encrypted bidding document cannot be decrypted without the recipient's private key. The bidding document becomes a large pile of unreadable documents. Any garbled code in any practical sense, so there will be no loss even if it is stolen. So encryption is very important to protect files.
Encryption Types
Encryption is based on mathematical encoding and decoding of information. There are two types of encryption, symmetric encryption and asymmetric encryption. Both parties of symmetric encryption use a common key (of course, this key needs to be kept secret).
Here we talk about asymmetric encryption. There are two keys in this encryption method. The key - one is the public key (as the name suggests, this is a public key value), and the other is the public key. The first is the private key (secret to the outside world). When you send information to us, it is encrypted using a public key. Once we receive your encrypted message, we use your private key to decrypt the message (message encrypted by our public key can only be decrypted by our private key), thus technically ensuring that only we can decrypt the message. Interpretation - because others do not have our private key). Information encrypted using the private key can only be decrypted using the public key (this function is applied in the field of digital signatures. The data encrypted by my private key can only be decrypted by my public key. For details, please refer to the information on digital signatures) and vice versa. to ensure the security of your information.
Encryption Tips
The following tips can enhance the security of encryption:
1. Do not use old encryption algorithms
Businesses should stop using older encryption algorithms like DES and its relative 3DES (Triple Data Encryption Standard).
2. Use the longest encryption key supported by the enterprise
It is recommended that enterprises use the largest length key possible, which can make it difficult for those enterprises without access to backdoors to crack the enterprise's encryption. AES 128 is pretty robust these days, but if possible, use AES 512 or longer keys.
3. Multi-layer encryption
It is recommended that enterprises utilize multi-layer encryption as much as possible, which can increase the difficulty for attackers. If possible, encrypt every field, every table, and the entire database.
4. Secure storage of encryption keys
The biggest problem facing enterprises may not be that the encryption algorithm has been left with a backdoor by the US National Security Agency, but that the password itself is only part of the encryption scheme. Other elements of the infrastructure, such as key management systems, must also be secured. Attackers are willing to target the weakest link in a security system. If an attacker can easily steal the key, why go to the trouble of cracking the encryption algorithm?
Some enterprises give the keys to protect their data to third parties, especially when the enterprise stores the data in a public cloud and is encrypted and protected by the cloud provider. The problem here is that the enterprise has no control over the keys and must instead trust the cloud provider's employees to keep the keys securely.
It would be much more secure if businesses could implement an encryption system that controlled the keys in the cloud. Cloud encryption gateways that automatically handle encryption can help companies achieve this security.
5. Ensure encryption is implemented correctly
In fact, implementing an encryption system is not an easy task because it has many dynamic parts, any one of which may become a weak link. You have to do a lot of research to make sure encryption is implemented correctly.
What areas are prone to errors when implementing encryption? In addition to the keys being vulnerable, there is also the implementation of CBC (Cryptoblock Chaining). Using CBC, plain text can be Then, the previously generated ciphertext block is used as an initialization vector to perform an XOR operation on the next plain text block.
Correct implementation of CBC requires that each process be started with a new initialization vector. A common mistake is to implement CBC with a static initialization vector that does not change. If CBC is implemented correctly, then if we encrypt a block of text on two different occasions, the resulting ciphertext block will not be the same.
6. Don’t ignore external factors
External factors that a company has little control over have the potential to undermine the security of an encryption system. For example, SSL relies on digital certificates, and these factors rely on the integrity of the root certificate authority embedded in the browser (such as IE, Firefox, Chrome, etc.). But how do we know if they are trustworthy, or if these certificate authorities are not a front for some foreign intelligence agency? If you think this sounds far-fetched, it could be true.
In addition, DNS is also a weakness that must be taken seriously. Once the DNS is compromised, attackers can use phishing techniques to bypass encryption.
Of course, the emphasis here is on the various possibilities of encryption issues. A properly implemented encryption system can only be broken under one condition, namely by testing the key. It is not impossible to guess the key in a short time, but it is extremely unlikely.
For more related knowledge, please visit the FAQ column!
The above is the detailed content of What is the role of encryption on the Internet?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1386
1386
 52
52
![WLAN expansion module has stopped [fix]](https://img.php.cn/upload/article/000/465/014/170832352052603.gif?x-oss-process=image/resize,m_fill,h_207,w_330) WLAN expansion module has stopped [fix]
Feb 19, 2024 pm 02:18 PM
WLAN expansion module has stopped [fix]
Feb 19, 2024 pm 02:18 PM
If there is a problem with the WLAN expansion module on your Windows computer, it may cause you to be disconnected from the Internet. This situation is often frustrating, but fortunately, this article provides some simple suggestions that can help you solve this problem and get your wireless connection working properly again. Fix WLAN Extensibility Module Has Stopped If the WLAN Extensibility Module has stopped working on your Windows computer, follow these suggestions to fix it: Run the Network and Internet Troubleshooter to disable and re-enable wireless network connections Restart the WLAN Autoconfiguration Service Modify Power Options Modify Advanced Power Settings Reinstall Network Adapter Driver Run Some Network Commands Now, let’s look at it in detail
 What should I do if the earth is displayed in the lower right corner of Windows 10 when I cannot access the Internet? Various solutions to the problem that the Earth cannot access the Internet in Win10
Feb 29, 2024 am 09:52 AM
What should I do if the earth is displayed in the lower right corner of Windows 10 when I cannot access the Internet? Various solutions to the problem that the Earth cannot access the Internet in Win10
Feb 29, 2024 am 09:52 AM
This article will introduce the solution to the problem that the globe symbol is displayed on the Win10 system network but cannot access the Internet. The article will provide detailed steps to help readers solve the problem of Win10 network showing that the earth cannot access the Internet. Method 1: Restart directly. First check whether the network cable is not plugged in properly and whether the broadband is in arrears. The router or optical modem may be stuck. In this case, you need to restart the router or optical modem. If there are no important things being done on the computer, you can restart the computer directly. Most minor problems can be quickly solved by restarting the computer. If it is determined that the broadband is not in arrears and the network is normal, that is another matter. Method 2: 1. Press the [Win] key, or click [Start Menu] in the lower left corner. In the menu item that opens, click the gear icon above the power button. This is [Settings].
 Check network connection: lol cannot connect to the server
Feb 19, 2024 pm 12:10 PM
Check network connection: lol cannot connect to the server
Feb 19, 2024 pm 12:10 PM
LOL cannot connect to the server, please check the network. In recent years, online games have become a daily entertainment activity for many people. Among them, League of Legends (LOL) is a very popular multiplayer online game, attracting the participation and interest of hundreds of millions of players. However, sometimes when we play LOL, we will encounter the error message "Unable to connect to the server, please check the network", which undoubtedly brings some trouble to players. Next, we will discuss the causes and solutions of this error. First of all, the problem that LOL cannot connect to the server may be
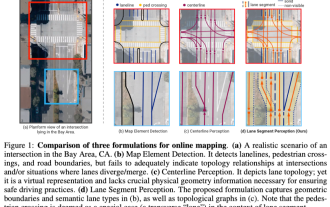 ICLR'24 new ideas without pictures! LaneSegNet: map learning based on lane segmentation awareness
Jan 19, 2024 am 11:12 AM
ICLR'24 new ideas without pictures! LaneSegNet: map learning based on lane segmentation awareness
Jan 19, 2024 am 11:12 AM
Written above & The author’s personal understanding of maps as key information for downstream applications of autonomous driving systems is usually represented by lanes or center lines. However, the existing map learning literature mainly focuses on detecting geometry-based topological relationships of lanes or sensing centerlines. Both methods ignore the inherent relationship between lane lines and center lines, that is, lane lines bind center lines. Although simply predicting two types of lanes in one model are mutually exclusive in the learning objective, this paper proposes lanesegment as a new representation that seamlessly combines geometric and topological information, thus proposing LaneSegNet. This is the first end-to-end mapping network that generates lanesegments to obtain a complete representation of road structure. LaneSegNet has two levels
 What's going on when the network can't connect to the wifi?
Apr 03, 2024 pm 12:11 PM
What's going on when the network can't connect to the wifi?
Apr 03, 2024 pm 12:11 PM
1. Check the wifi password: Make sure the wifi password you entered is correct and pay attention to case sensitivity. 2. Confirm whether the wifi is working properly: Check whether the wifi router is running normally. You can connect other devices to the same router to determine whether the problem lies with the device. 3. Restart the device and router: Sometimes, there is a malfunction or network problem with the device or router, and restarting the device and router may solve the problem. 4. Check the device settings: Make sure the wireless function of the device is turned on and the wifi function is not disabled.
 Windows 11 Folder Sharing Guide: Easily Share Your Files and Data
Mar 13, 2024 am 11:49 AM
Windows 11 Folder Sharing Guide: Easily Share Your Files and Data
Mar 13, 2024 am 11:49 AM
In daily life and work, we often need to share files and folders between different devices. Windows 11 system provides convenient built-in folder sharing functions, allowing us to easily and safely share the content we need with others within the same network while protecting the privacy of personal files. This feature makes file sharing simple and efficient without worrying about leaking private information. Through the folder sharing function of Windows 11 system, we can cooperate, communicate and collaborate more conveniently, improving work efficiency and life convenience. In order to successfully configure a shared folder, we first need to meet the following conditions: All devices (participating in sharing) are connected to the same network. Enable Network Discovery and configure sharing. Know the target device
 Windows 10 Home Edition public network changed to private network
Feb 12, 2024 pm 10:27 PM
Windows 10 Home Edition public network changed to private network
Feb 12, 2024 pm 10:27 PM
In order to use our computer, in addition to some hardware, it also needs to be connected to a stable network. Many friends have discovered that the network in the computer is divided into public network and private network. Many people are curious about how to convert the public network into a private network. . Win10 Home Edition public network is changed to a private network 1. Advanced settings of the Advanced Sharing Center 1. First, we directly press the win+R shortcut key combination to summon the run pop-up window, then enter "control panel" here, and click OK to open the control panel . 2. Then we select Network and Internet--Network and Sharing Center--Change advanced sharing settings. 3. Then we click on the dedicated option in the more advanced sharing settings interface and check the "Enable
 How to set up encryption of photo album on Apple mobile phone
Mar 02, 2024 pm 05:31 PM
How to set up encryption of photo album on Apple mobile phone
Mar 02, 2024 pm 05:31 PM
In Apple mobile phones, users can encrypt photo albums according to their own needs. Some users don't know how to set it up. You can add the pictures that need to be encrypted to the memo, and then lock the memo. Next, the editor will introduce the method of setting up the encryption of mobile photo albums for users. Interested users, come and take a look! Apple mobile phone tutorial How to set up iPhone photo album encryption A: After adding the pictures that need to be encrypted to the memo, go to lock the memo for detailed introduction: 1. Enter the photo album, select the picture that needs to be encrypted, and then click [Add to] below. 2. Select [Add to Notes]. 3. Enter the memo, find the memo you just created, enter it, and click the [Send] icon in the upper right corner. 4. Click [Lock Device] below



