What are the characteristics of malware not included?
The characteristics of malware do not include "destroying user data". Malware is software that is between viruses and regular software. Its characteristics are: 1. Forced installation; 2. Difficulty to uninstall; 3. Browser hijacking; 4. Advertising pop-ups; 5. Malicious collection of user information; 6. Malicious Uninstall other software; 7. Malicious bundling; 8. Other malicious behaviors that infringe on the user's right to know and choose.

The operating environment of this tutorial: Windows 7 system, Dell G3 computer.
[Single-choice question] The characteristics of malware do not include ().
A. Forced installation
B. Malicious collection of user information
C . Destroy user data
D. Difficult to uninstall
Correct answer: C. Destroy user data
Malicious software (commonly known as "rogue software") refers to software that is installed and run on the user's computer or other terminal without the user's explicit prompt or permission, infringing upon the user's legitimate rights and interests, but does not include Chinese laws and regulations prescribed computer viruses.
Simply put: malware is software that is between viruses and regular software.
Some rogue software is just to achieve a certain purpose, such as advertising. Although these rogue software will not affect the normal use of the user's computer, an additional web page will pop up when the user starts the browser for promotional purposes.
Malicious software has the following characteristics (characteristics)
1. Forced installation: refers to without explicit prompting from the user Or allow the installation of software on users’ computers or other terminals.
a) Do not prompt the user during the installation process;
b) Do not provide clear options for the user to choose during the installation process;
c) Do not provide the user with the function to exit the installation during the installation process;
d) Prompt the user that the installation process is insufficient and incomplete. Clear; (Clear and sufficient prompt information includes but is not limited to software author, software name, software version, software function, etc.)
2. Difficult to uninstall: Yes This refers to the behavior of a program that is still active after being uninstalled, even if a universal uninstall method is not provided, or it is not affected by other software or destroyed by others.
a) No clear and universal uninstallation interface is provided (such as "Program Group" and "Add or Remove Programs" in "Control Panel" under Windows system);
b) Software uninstallation is additionally mandatory Conditions, such as connecting to the Internet, entering verification code, answering questions, etc.
c) It cannot be completely uninstalled without being affected by other software or artificially damaged, and there are still subprograms or modules running (such as in process mode);
3. Browser hijacking: refers to the behavior of modifying the user's browser or other related settings without the user's permission, forcing the user to access a specific website or causing the user to be unable to access the Internet normally.
a) Restrict users from modifying browser settings;
b) Unauthorized addition, deletion and modification of the content of websites visited by users;
c) Force users to access specific websites or be unable to access the Internet normally.
d) Modifying the relevant settings of the user's browser or operating system causes the above three phenomena.
4. Advertising pop-ups: refers to the use of advertisements installed on the user’s computer or other terminals without explicitly prompting the user or without the user’s permission. The behavior of software pop-up ads.
a) Users were not informed of the pop-up advertising behavior of the software during installation;
b) Pop-up ads cannot be turned off;
c) When an advertisement pops up, the user is not notified of the software information of the pop-up advertisement;
5. Malicious collection of user information: Refers to Maliciously collect user information without the user’s explicit prompts or permission.
a) When collecting user information, do not prompt users to collect information;
b) Do not provide users with the option to choose whether to allow information collection Options;
c) Users cannot view the information they collect;
6. Malicious uninstallation: refers to no The act of uninstalling other software without clearly prompting the user, without the user's permission, or misleading or deceiving the user.
a) False description of other software;
b) Giving error prompts for other software;
c) Delete other software directly.
7. Malicious bundling: refers to the act of bundling software that has been identified as malware.
a) During installation, install identified malware;
b) After installation, install or run other malware that has passed various ways to identify malware.
#8. Other malicious behaviors that infringe on users’ rights to know and choose.
For more related knowledge, please visit the FAQ column!
The above is the detailed content of What are the characteristics of malware not included?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1359
1359
 52
52
 What software is bonjour and can it be uninstalled?
Feb 20, 2024 am 09:33 AM
What software is bonjour and can it be uninstalled?
Feb 20, 2024 am 09:33 AM
Title: Explore the Bonjour software and how to uninstall it Abstract: This article will introduce the functions, scope of use and how to uninstall the Bonjour software. At the same time, it will also be explained how to use other tools to replace Bonjour to meet the needs of users. Introduction: Bonjour is a common software in the field of computer and network technology. Although this may be unfamiliar to some users, it can be very useful in some specific situations. If you happen to have Bonjour software installed but now want to uninstall it, then
 What to do if WPS Office cannot open the PPT file - What to do if WPS Office cannot open the PPT file
Mar 04, 2024 am 11:40 AM
What to do if WPS Office cannot open the PPT file - What to do if WPS Office cannot open the PPT file
Mar 04, 2024 am 11:40 AM
Recently, many friends have asked me what to do if WPSOffice cannot open PPT files. Next, let us learn how to solve the problem of WPSOffice not being able to open PPT files. I hope it can help everyone. 1. First open WPSOffice and enter the homepage, as shown in the figure below. 2. Then enter the keyword "document repair" in the search bar above, and then click to open the document repair tool, as shown in the figure below. 3. Then import the PPT file for repair, as shown in the figure below.
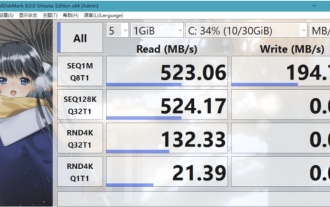 What software is crystaldiskmark? -How to use crystaldiskmark?
Mar 18, 2024 pm 02:58 PM
What software is crystaldiskmark? -How to use crystaldiskmark?
Mar 18, 2024 pm 02:58 PM
CrystalDiskMark is a small HDD benchmark tool for hard drives that quickly measures sequential and random read/write speeds. Next, let the editor introduce CrystalDiskMark to you and how to use crystaldiskmark~ 1. Introduction to CrystalDiskMark CrystalDiskMark is a widely used disk performance testing tool used to evaluate the read and write speed and performance of mechanical hard drives and solid-state drives (SSD). Random I/O performance. It is a free Windows application and provides a user-friendly interface and various test modes to evaluate different aspects of hard drive performance and is widely used in hardware reviews
![Corsair iCUE software not detecting RAM [Fixed]](https://img.php.cn/upload/article/000/465/014/170831448976874.png?x-oss-process=image/resize,m_fill,h_207,w_330) Corsair iCUE software not detecting RAM [Fixed]
Feb 19, 2024 am 11:48 AM
Corsair iCUE software not detecting RAM [Fixed]
Feb 19, 2024 am 11:48 AM
This article will explore what users can do when the CorsairiCUE software does not recognize the RAM in a Windows system. Although the CorsairiCUE software is designed to let users control their computer's RGB lighting, some users have found that the software does not function properly, resulting in an inability to detect RAM modules. Why doesn't ICUE pick up my memory? The main reason why ICUE cannot correctly identify RAM is usually related to background software conflicts. In addition, incorrect SPD write settings may also cause this problem. Fixed issue with CorsairIcue software not detecting RAM If CorsairIcue software is not detecting RAM on your Windows computer, please use the following suggestions.
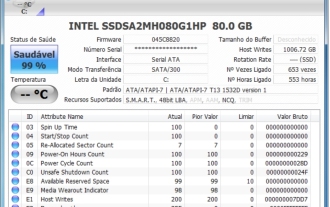 CrystalDiskinfo usage tutorial-What software is CrystalDiskinfo?
Mar 18, 2024 pm 04:50 PM
CrystalDiskinfo usage tutorial-What software is CrystalDiskinfo?
Mar 18, 2024 pm 04:50 PM
CrystalDiskInfo is a software used to check computer hardware devices. In this software, we can check our own computer hardware, such as reading speed, transmission mode, interface, etc.! So in addition to these functions, how to use CrystalDiskInfo and what exactly is CrystalDiskInfo? Let me sort it out for you! 1. The Origin of CrystalDiskInfo As one of the three major components of a computer host, a solid-state drive is the storage medium of a computer and is responsible for computer data storage. A good solid-state drive can speed up file reading and affect consumer experience. When consumers receive new devices, they can use third-party software or other SSDs to
 How to set the keyboard increment in Adobe Illustrator CS6 - How to set the keyboard increment in Adobe Illustrator CS6
Mar 04, 2024 pm 06:04 PM
How to set the keyboard increment in Adobe Illustrator CS6 - How to set the keyboard increment in Adobe Illustrator CS6
Mar 04, 2024 pm 06:04 PM
Many users are using the Adobe Illustrator CS6 software in their offices, so do you know how to set the keyboard increment in Adobe Illustrator CS6? Then, the editor will bring you the method of setting the keyboard increment in Adobe Illustrator CS6. Interested users can take a look below. Step 1: Start Adobe Illustrator CS6 software, as shown in the figure below. Step 2: In the menu bar, click the [Edit] → [Preferences] → [General] command in sequence. Step 3: The [Keyboard Increment] dialog box pops up, enter the required number in the [Keyboard Increment] text box, and finally click the [OK] button. Step 4: Use the shortcut key [Ctrl]
 How to resolve an incompatible software attempt to load with Edge?
Mar 15, 2024 pm 01:34 PM
How to resolve an incompatible software attempt to load with Edge?
Mar 15, 2024 pm 01:34 PM
When we use the Edge browser, sometimes incompatible software attempts to be loaded together, so what is going on? Let this site carefully introduce to users how to solve the problem of trying to load incompatible software with Edge. How to solve an incompatible software trying to load with Edge Solution 1: Search IE in the start menu and access it directly with IE. Solution 2: Note: Modifying the registry may cause system failure, so operate with caution. Modify registry parameters. 1. Enter regedit during operation. 2. Find the path\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Micros
 What kind of software is bonjour? Is it useful?
Feb 22, 2024 pm 08:39 PM
What kind of software is bonjour? Is it useful?
Feb 22, 2024 pm 08:39 PM
Bonjour is a network protocol and software launched by Apple for discovering and configuring network services within a local area network. Its main role is to automatically discover and communicate between devices connected in the same network. Bonjour was first introduced in the MacOSX10.2 version in 2002, and is now installed and enabled by default in Apple's operating system. Since then, Apple has opened up Bonjour's technology to other manufacturers, so many other operating systems and devices can also support Bonjour.



