 Common Problem
Common Problem
 What is the role of a firewall? What are the main technologies used to implement firewalls?
What is the role of a firewall? What are the main technologies used to implement firewalls?
What is the role of a firewall? What are the main technologies used to implement firewalls?
The main function of the firewall is to ensure network boundary security. The main technologies used to implement firewalls are: 1. Proxy technology, which is a software module that transmits information from one side of the firewall to the other; 2. Multi-level filtering technology, which is to set up multi-layer filtering rules in the firewall; 3. NAT conversion technology can use NAT technology to transparently convert all internal addresses, so that the external network cannot understand the internal structure of the internal network; 4. Transparent access technology reduces the inherent security risks and error probability of system login.

The operating environment of this tutorial: Windows 7 system, Dell G3 computer.
Firewall (English: Firewall) technology helps computer networks build a relatively isolated protective barrier between internal and external networks by organically combining various software and hardware devices for security management and screening. A technology to protect the security of user data and information.
The main function of firewall technology is to promptly discover and deal with security risks, data transmission and other issues that may exist when computer networks are running. The treatment measures include isolation and protection, and can also control various operations in computer network security. Implement recording and testing to ensure the security of computer network operations, protect the integrity of user data and information, and provide users with a better and safer computer network experience.
The main function of the firewall is to ensure network boundary security. The following technologies are mainly used to implement the firewall:
-
Proxy technology:
The proxy system is a kind of information transfer system A software module that travels from one side of the firewall to the other. The new generation firewall uses two proxy mechanisms, one for proxying connections from the internal network to the external network, and the other for proxying connections from the external network to the internal network. The former is solved by Network Address Translation (NAT) technology, and the latter is solved by non-confidential user-customized proxy or confidential proxy system technology.
-
Multi-level filtering technology:
is to set up multi-layer filtering rules in the firewall. At the network layer, packet filtering technology is used to intercept all fake IP source addresses and source routing packets; according to the filtering rules, the transport layer intercepts all inbound/outbound protocols and data packets; at the application layer, gateways such as FTP and SMTP are used to Monitor and control Internet services.
In order to ensure the security and protection level of the system, the new generation firewall adopts three-level filtering measures, supplemented by identification methods. At the packet filtering level, all source routing packets and fake IP source addresses can be filtered out. At the application-level gateway level, various gateways such as FTP and SMTP can be used to control and monitor all common services provided by the Internet; at the circuit gateway level, transparent connections between internal hosts and external sites are realized, and strict access to services is implemented. control.
-
Multi-port technology:
has two or three independent network cards. The internal and external network cards can be connected in series between the internal network and the external network without IP conversion. During this time, another network card can be dedicated to the security of the server.
-
NAT conversion technology:
Use NAT technology to transparently translate all internal addresses, making the external network unable to understand the internal structure of the internal network, while allowing the internal network to Using its own customized IP address and private network, the firewall can record every host's traffic in detail, ensuring that each packet is sent to the correct address. In a network that also uses NAT, the connection to the external network can only be initiated by the internal network, which greatly improves the security of the internal network. Another obvious use of NAT is to solve the problem of IP address scarcity.
-
Transparent access technology:
The firewall utilizes transparent proxy system technology, thereby reducing the inherent security risks and error probability of system login.
-
Anti-virus technology
Firewall has anti-virus function. In the application of anti-virus technology, it mainly includes virus prevention, removal and detection. As for the anti-virus prevention function of the firewall, during the network construction process, the information data between the computer and the Internet is strictly controlled by installing the corresponding firewall, thereby forming a safe barrier to the computer external network and the internal network. Data enforcement protection. Computer networks are generally connected through the Internet and routers. Therefore, network protection needs to start from the backbone network and control the central resources of the backbone network to prevent illegal access to the server. In order to eliminate external Illegal intrusion steals information. The data connected to the computer connection port must be strictly checked by Ethernet and IP address. The stolen IP address will be discarded. At the same time, important information resources will be comprehensively recorded. Ensure that the information network of its computers has good security.
-
Encryption Technology
In the process of computer information transmission, firewalls can also effectively encrypt information. Through this encryption technology, relevant personnel can effectively encrypt the transmitted information, and the information password is mastered by both parties communicating the information. , the person receiving the information needs to decrypt the encrypted information before they can obtain the transmitted information data. In the application of firewall encryption technology, always pay attention to ensuring the security of information encryption processing. In the application of firewall technology, if you want to achieve safe transmission of information, you also need to verify the user's identity. After encryption, the transmission of information needs to authorize the user, and then the identity of the information receiver and sender needs to be verified. , thereby establishing a channel for secure information transmission to ensure that computer network information has good security during transmission. Criminals do not have the correct identity verification conditions, so they cannot intrude on computer network information.
For more related knowledge, please visit the FAQ column!
The above is the detailed content of What is the role of a firewall? What are the main technologies used to implement firewalls?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1386
1386
 52
52
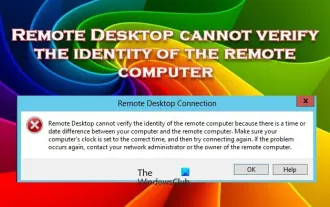 Remote Desktop cannot authenticate the remote computer's identity
Feb 29, 2024 pm 12:30 PM
Remote Desktop cannot authenticate the remote computer's identity
Feb 29, 2024 pm 12:30 PM
Windows Remote Desktop Service allows users to access computers remotely, which is very convenient for people who need to work remotely. However, problems can be encountered when users cannot connect to the remote computer or when Remote Desktop cannot authenticate the computer's identity. This may be caused by network connection issues or certificate verification failure. In this case, the user may need to check the network connection, ensure that the remote computer is online, and try to reconnect. Also, ensuring that the remote computer's authentication options are configured correctly is key to resolving the issue. Such problems with Windows Remote Desktop Services can usually be resolved by carefully checking and adjusting settings. Remote Desktop cannot verify the identity of the remote computer due to a time or date difference. Please make sure your calculations
 2024 CSRankings National Computer Science Rankings Released! CMU dominates the list, MIT falls out of the top 5
Mar 25, 2024 pm 06:01 PM
2024 CSRankings National Computer Science Rankings Released! CMU dominates the list, MIT falls out of the top 5
Mar 25, 2024 pm 06:01 PM
The 2024CSRankings National Computer Science Major Rankings have just been released! This year, in the ranking of the best CS universities in the United States, Carnegie Mellon University (CMU) ranks among the best in the country and in the field of CS, while the University of Illinois at Urbana-Champaign (UIUC) has been ranked second for six consecutive years. Georgia Tech ranked third. Then, Stanford University, University of California at San Diego, University of Michigan, and University of Washington tied for fourth place in the world. It is worth noting that MIT's ranking fell and fell out of the top five. CSRankings is a global university ranking project in the field of computer science initiated by Professor Emery Berger of the School of Computer and Information Sciences at the University of Massachusetts Amherst. The ranking is based on objective
 What is e in computer
Aug 31, 2023 am 09:36 AM
What is e in computer
Aug 31, 2023 am 09:36 AM
The "e" of computer is the scientific notation symbol. The letter "e" is used as the exponent separator in scientific notation, which means "multiplied to the power of 10". In scientific notation, a number is usually written as M × 10^E, where M is a number between 1 and 10 and E represents the exponent.
 Win11 firewall advanced settings gray solution
Dec 24, 2023 pm 07:53 PM
Win11 firewall advanced settings gray solution
Dec 24, 2023 pm 07:53 PM
When setting up the firewall, many friends found that their win11 firewall advanced settings were grayed out and unable to be clicked. This may be caused by not adding a control unit, or by not opening the advanced settings in the correct way. Let’s take a look at how to solve it. Win11 firewall advanced settings gray method one: 1. First, click the start menu below, search and open "Control Panel" at the top 2. Then open "Windows Defender Firewall" 3. After entering, you can open "Advanced Settings" in the left column . Method 2: 1. If the above method cannot be opened, you can right-click "Start Menu" and open "Run" 2. Then enter "mmc" and press Enter to confirm opening. 3. After opening, click on the upper left
 What does computer cu mean?
Aug 15, 2023 am 09:58 AM
What does computer cu mean?
Aug 15, 2023 am 09:58 AM
The meaning of cu in a computer depends on the context: 1. Control Unit, in the central processor of a computer, CU is the component responsible for coordinating and controlling the entire computing process; 2. Compute Unit, in a graphics processor or other accelerated processor, CU is the basic unit for processing parallel computing tasks.
 Unable to open the Group Policy object on this computer
Feb 07, 2024 pm 02:00 PM
Unable to open the Group Policy object on this computer
Feb 07, 2024 pm 02:00 PM
Occasionally, the operating system may malfunction when using a computer. The problem I encountered today was that when accessing gpedit.msc, the system prompted that the Group Policy object could not be opened because the correct permissions may be lacking. The Group Policy object on this computer could not be opened. Solution: 1. When accessing gpedit.msc, the system prompts that the Group Policy object on this computer cannot be opened because of lack of permissions. Details: The system cannot locate the path specified. 2. After the user clicks the close button, the following error window pops up. 3. Check the log records immediately and combine the recorded information to find that the problem lies in the C:\Windows\System32\GroupPolicy\Machine\registry.pol file
 How to enable or disable firewall on Alpine Linux?
Feb 21, 2024 pm 12:45 PM
How to enable or disable firewall on Alpine Linux?
Feb 21, 2024 pm 12:45 PM
On AlpineLinux, you can use the iptables tool to configure and manage firewall rules. Here are the basic steps to enable or disable the firewall on AlpineLinux: Check the firewall status: sudoiptables -L If the output shows rules (for example, there are some INPUT, OUTPUT, or FORWARD rules), the firewall is enabled. If the output is empty, the firewall is currently disabled. Enable firewall: sudoiptables-PINPUTACCEPTsudoiptables-POUTPUTACCEPTsudoiptables-PFORWARDAC
 How to fix UFW status showing as inactive in Linux
Mar 20, 2024 pm 01:50 PM
How to fix UFW status showing as inactive in Linux
Mar 20, 2024 pm 01:50 PM
UFW, also known as Uncomplex Firewall, is adopted by many Linux distributions as their firewall system. UFW is designed to make it easy for novice users to manage firewall settings through both the command line interface and the graphical user interface. A UFW firewall is a system that monitors network traffic according to set rules to protect the network from network sniffing and other attacks. If you have UFW installed on your Linux system but its status shows as inactive, there could be several reasons. In this guide, I will share how to resolve the UFW firewall inactive issue on Linux systems. Why UFW Shows Inactive Status on Linux Why UFW Is Inactive by Default on Linux How to Inactive on Linux


