Commonly used data structures in Redis (organized and shared)
This article brings you relevant knowledge about Redis, which mainly introduces the relevant content about common data structures. There are five most commonly used ones, namely string, hash, Let’s take a look at lists, sets and ordered sets. I hope it will be helpful to everyone.

Recommended learning: Redis video tutorial
Redis common data structures
Redis provides some data structures for When we access data in Redis, there are five most commonly used ones: String, Hash, list, set, and ordered set (ZSET).
String (String)
The string type is the most basic data structure of Redis. First of all, the keys are all string types, and several other data structures are built on the basis of the string type, so the string type can lay the foundation for the learning of the other four data structures. The value of the string type can actually be a string (simple string, complex string (such as JSON, XML)), number (integer, floating point number), or even binary (picture, audio, video), but the value is the largest Cannot exceed 512MB.
(Although Redis is written in C, there are strings in C which are essentially implemented using char arrays. However, due to various considerations, Redis still implements the string type itself)
Operation command
set set value
set key value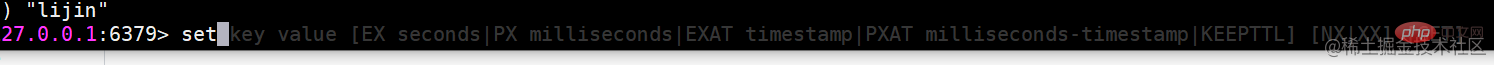
The set command has several options:
ex seconds: Set the second-level expiration time for the key.
px milliseconds: Set the millisecond expiration time for the key.
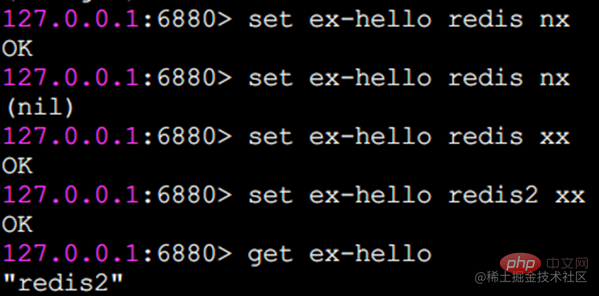
nx: The key must not exist before it can be set successfully and is used for adding (commonly used for distributed locks).
xx: Contrary to nx, the key must exist before it can be set successfully and used for update.
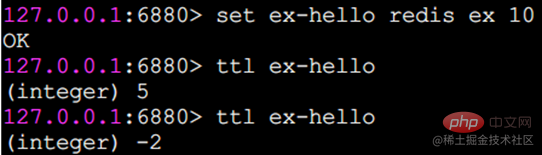
From the execution effect, the ex parameter is basically the same as the expire command. Another thing that needs special attention is that if a string has an expiration time set, and then you call the set method to modify it, its expiration time will disappear.
The execution effects of nx and xx are as follows
In addition to the set option, Redis also provides two commands: setex and setnx:
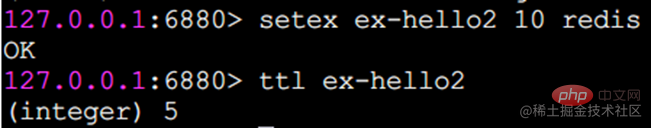
setex key seconds value
setnx key value
The functions of setex and setnx are the same as the ex and nx options. That is, setex sets the second-level expiration time for the key. The key must not exist when setnx is set before it can be set successfully.
setex example:
get Get the value
If the key to be obtained does not exist, return nil (empty):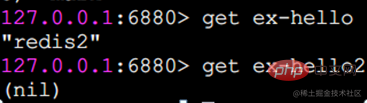
mset Set values in batches
Set 4 key-value pairs at one time through the mset command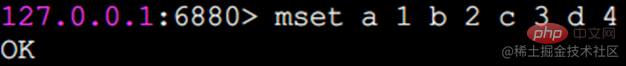
mget Get values in batches
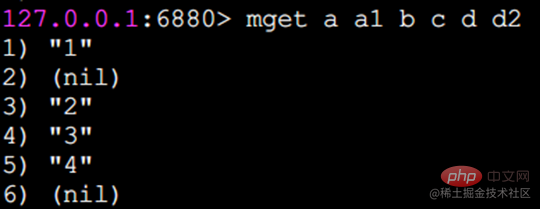
Redis can support tens of thousands of read and write operations per second, but this refers to the processing capability of the Redis server. For the client, in addition to the command time, a command also has network time. Assuming that the network time is 1 millisecond, the command The time is 0.1 milliseconds (based on processing 10,000 commands per second), then it takes 1.1 seconds to execute 1,000 get commands (10001 10000.1=1100ms), and 1 mget command takes 0.101 seconds (1 1 10000.1=101ms).
Incr Numerical Operations
The incr command is used to perform increment operations on values. The returned results are divided into three situations:
The value is not an integer, Return an error.
The value is an integer, and the result after auto-increment is returned.
The key does not exist. It will be incremented according to the value of 0 and the returned result will be 1.
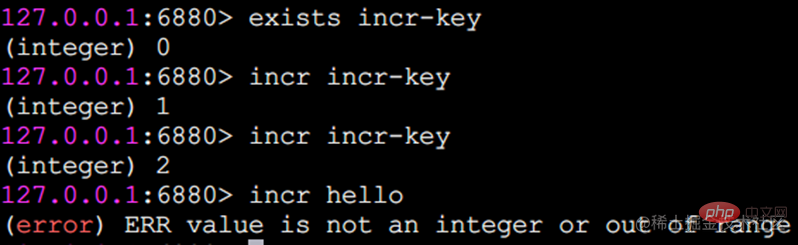
In addition to the incr command, Redis provides decr (self-decrement), incrby (self-increment specified number), decrby (self-decrement specified number), incrbyfloat (self-increasing floating point number) ), students are asked to try it on their own for specific effects.
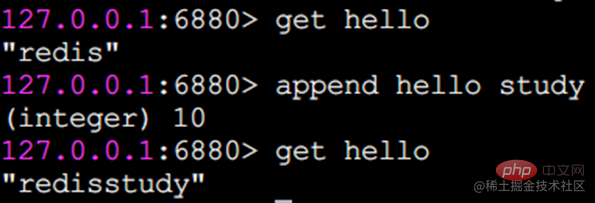
append append command
append can append a value to the end of the string
strlen string Length
Return string length
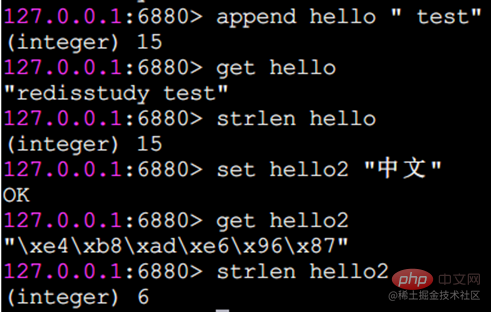
Note: Each Chinese character occupies 3 bytes
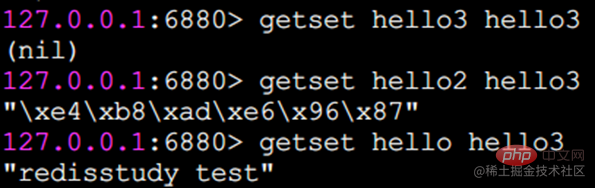
getset setting And return the original value
getset will set the value just like set, but the difference is that it will also return the original value of the key
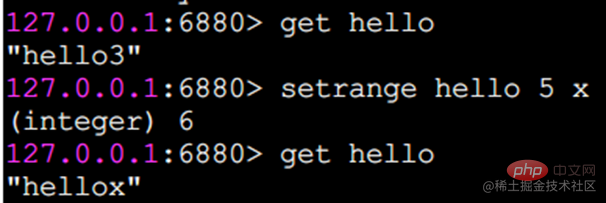
setrange sets the characters at the specified position
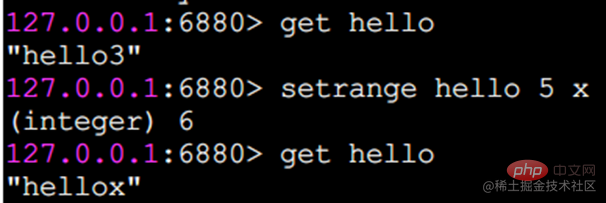
The subscript starts from 0.
getrange intercepts a string
getrange intercepts a part of the string to form a substring. You need to specify the start and end offsets. The intercepted range is a closed interval.
Time complexity of the command
String Among these commands, except del, mset, mget support batches of multiple keys Operation, the time complexity is related to the number of keys, which is O(n). Getrange is related to the string length, which is also O(n). The rest of the commands basically have a time complexity of O(1), in terms of speed. Still very fast.
Usage scenarios
The string type has a wide range of usage scenarios:
Cache function
Redis As the cache layer, MySQL serves as the storage layer, and most of the requested data is obtained from Redis. Since Redis has the characteristics of supporting high concurrency, caching can usually play a role in accelerating reading and writing and reducing back-end pressure.
Counting
Using Redis as the basic tool for counting, it can realize the functions of fast counting and query caching, and the data can be asynchronously landed to other data sources.
Shared Session
A distributed Web service saves the user's Session information (such as user login information) in their respective servers. This will cause a problem. For load balancing considerations, distributed services will balance user access to different servers. Users who refresh their access may find that they need to log in again. This problem is intolerable to users.
In order to solve this problem, you can use Redis to centrally manage the user's Session. In this mode, as long as Redis is highly available and scalable, every time the user updates or queries login information, it will be directly accessed from Centralized acquisition in Redis.
speed limit
For example, for security reasons, many applications will ask users to enter a mobile phone verification code every time they log in to determine whether they are the user. myself. However, in order to prevent the SMS interface from being accessed frequently, the frequency of users obtaining verification codes per minute will be limited, for example, no more than 5 times per minute. Some websites restrict an IP address from being asked more than n times in one second, and a similar idea can be adopted.
Hash
Java provides HashMap, and Redis also has a similar data structure, which is the hash type. But please note that the mapping relationship in the hash type is called field-value. Note that the value here refers to the value corresponding to the field, not the value corresponding to the key.
Operation command
Basically, the hash operation command is very similar to the string operation command. Many commands add the letter h in front of the string type command, which means it is an operation. Greek type, and also specify the value of the field to be operated on.
hset set value
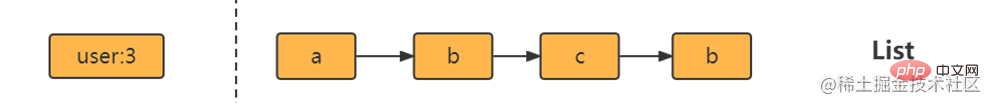
hset user:1 name lijin
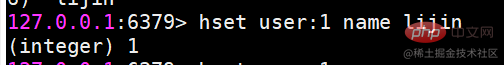
If the setting is successful, 1 will be returned, otherwise 0 will be returned. In addition, Redis provides the hsetnx command. Their relationship is the same as the set and setnx commands, except that the scope changes from key to field.
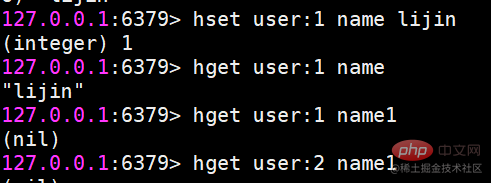
hget value
hget user:1 name
If the key or field does not exist, nil will be returned.
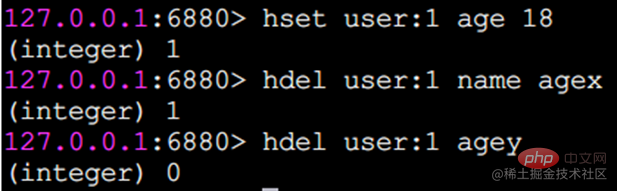
hdel delete field
hdel will delete one or more fields, and the return result is the number of successfully deleted fields.
hlen calculates the number of fields
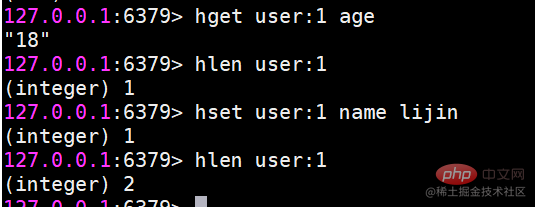
hmset sets values in batches
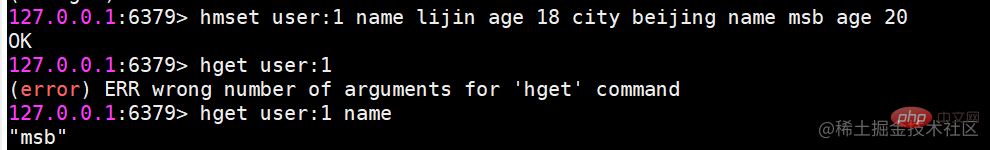
hmget batch value
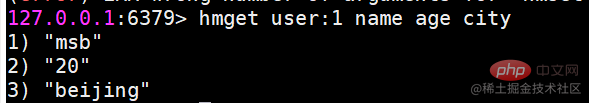
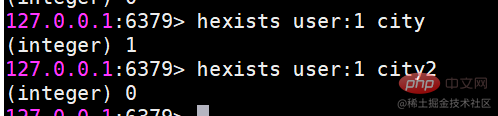
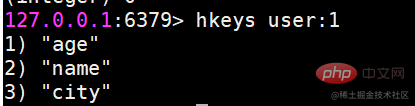
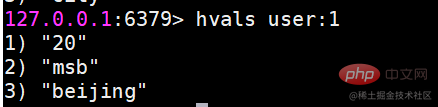
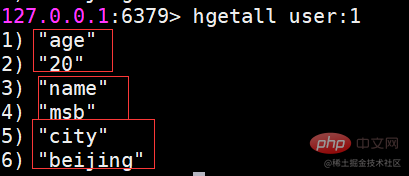
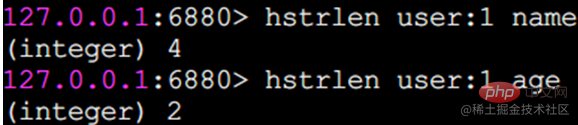
| name | age | |
|---|---|---|
| lijin | 18 | |
| msb | 20 |
The above is the detailed content of Commonly used data structures in Redis (organized and shared). For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1386
1386
 52
52
 How to build the redis cluster mode
Apr 10, 2025 pm 10:15 PM
How to build the redis cluster mode
Apr 10, 2025 pm 10:15 PM
Redis cluster mode deploys Redis instances to multiple servers through sharding, improving scalability and availability. The construction steps are as follows: Create odd Redis instances with different ports; Create 3 sentinel instances, monitor Redis instances and failover; configure sentinel configuration files, add monitoring Redis instance information and failover settings; configure Redis instance configuration files, enable cluster mode and specify the cluster information file path; create nodes.conf file, containing information of each Redis instance; start the cluster, execute the create command to create a cluster and specify the number of replicas; log in to the cluster to execute the CLUSTER INFO command to verify the cluster status; make
 How to clear redis data
Apr 10, 2025 pm 10:06 PM
How to clear redis data
Apr 10, 2025 pm 10:06 PM
How to clear Redis data: Use the FLUSHALL command to clear all key values. Use the FLUSHDB command to clear the key value of the currently selected database. Use SELECT to switch databases, and then use FLUSHDB to clear multiple databases. Use the DEL command to delete a specific key. Use the redis-cli tool to clear the data.
 How to read redis queue
Apr 10, 2025 pm 10:12 PM
How to read redis queue
Apr 10, 2025 pm 10:12 PM
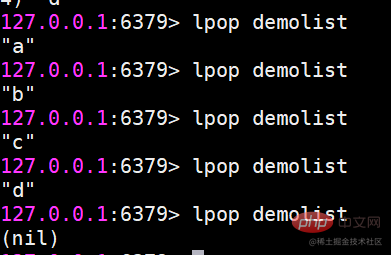
To read a queue from Redis, you need to get the queue name, read the elements using the LPOP command, and process the empty queue. The specific steps are as follows: Get the queue name: name it with the prefix of "queue:" such as "queue:my-queue". Use the LPOP command: Eject the element from the head of the queue and return its value, such as LPOP queue:my-queue. Processing empty queues: If the queue is empty, LPOP returns nil, and you can check whether the queue exists before reading the element.
 How to use the redis command
Apr 10, 2025 pm 08:45 PM
How to use the redis command
Apr 10, 2025 pm 08:45 PM
Using the Redis directive requires the following steps: Open the Redis client. Enter the command (verb key value). Provides the required parameters (varies from instruction to instruction). Press Enter to execute the command. Redis returns a response indicating the result of the operation (usually OK or -ERR).
 How to use redis lock
Apr 10, 2025 pm 08:39 PM
How to use redis lock
Apr 10, 2025 pm 08:39 PM
Using Redis to lock operations requires obtaining the lock through the SETNX command, and then using the EXPIRE command to set the expiration time. The specific steps are: (1) Use the SETNX command to try to set a key-value pair; (2) Use the EXPIRE command to set the expiration time for the lock; (3) Use the DEL command to delete the lock when the lock is no longer needed.
 How to read the source code of redis
Apr 10, 2025 pm 08:27 PM
How to read the source code of redis
Apr 10, 2025 pm 08:27 PM
The best way to understand Redis source code is to go step by step: get familiar with the basics of Redis. Select a specific module or function as the starting point. Start with the entry point of the module or function and view the code line by line. View the code through the function call chain. Be familiar with the underlying data structures used by Redis. Identify the algorithm used by Redis.
 How to solve data loss with redis
Apr 10, 2025 pm 08:24 PM
How to solve data loss with redis
Apr 10, 2025 pm 08:24 PM
Redis data loss causes include memory failures, power outages, human errors, and hardware failures. The solutions are: 1. Store data to disk with RDB or AOF persistence; 2. Copy to multiple servers for high availability; 3. HA with Redis Sentinel or Redis Cluster; 4. Create snapshots to back up data; 5. Implement best practices such as persistence, replication, snapshots, monitoring, and security measures.
 How to use the redis command line
Apr 10, 2025 pm 10:18 PM
How to use the redis command line
Apr 10, 2025 pm 10:18 PM
Use the Redis command line tool (redis-cli) to manage and operate Redis through the following steps: Connect to the server, specify the address and port. Send commands to the server using the command name and parameters. Use the HELP command to view help information for a specific command. Use the QUIT command to exit the command line tool.




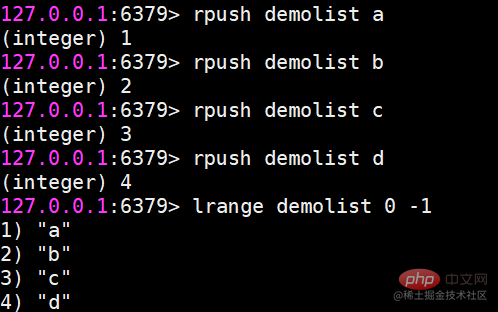
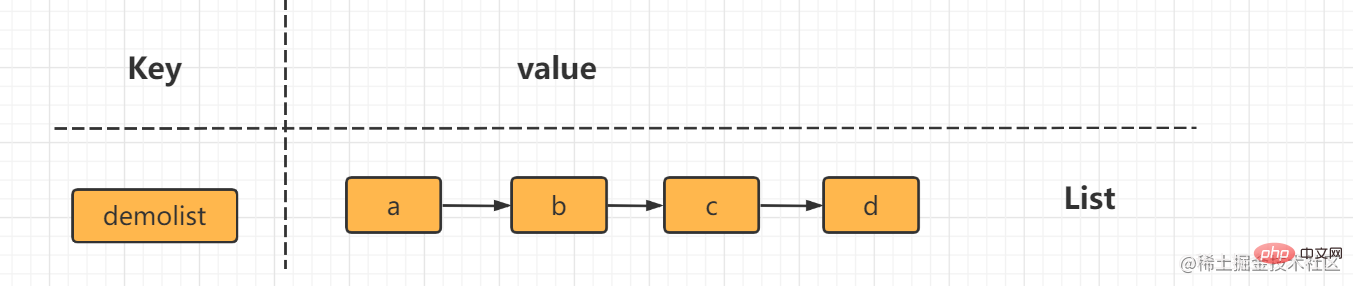
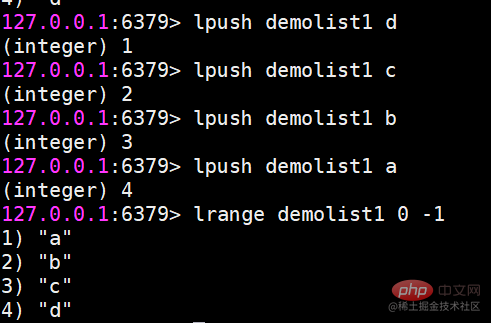
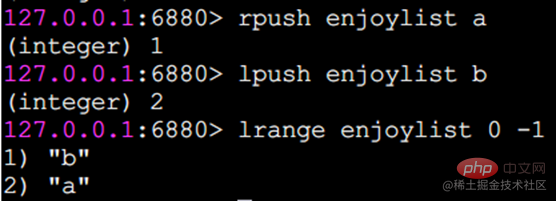
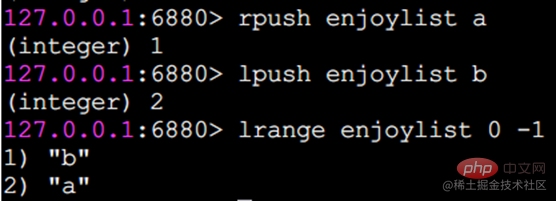
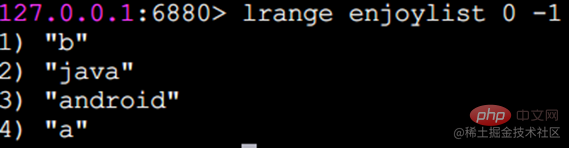
 r
r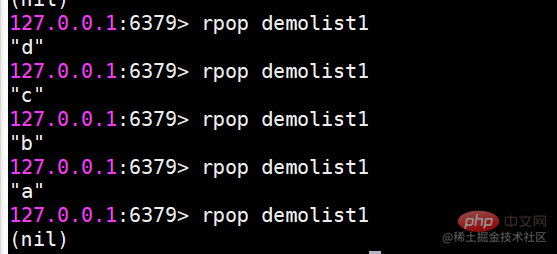

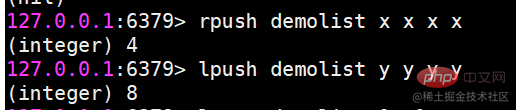
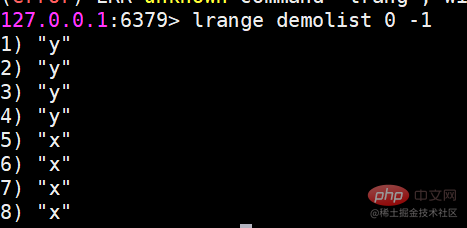
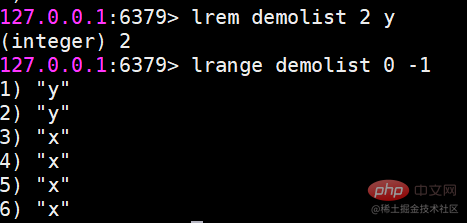
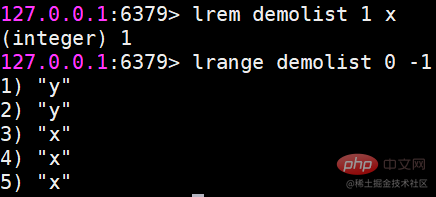
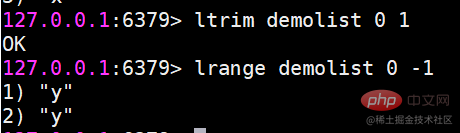 ls
ls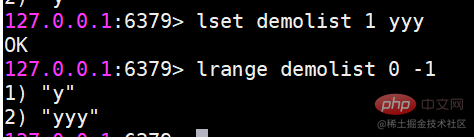
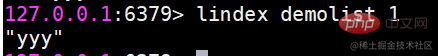 l
l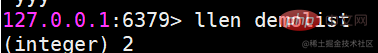
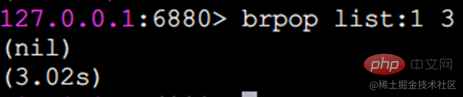
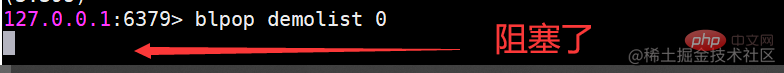
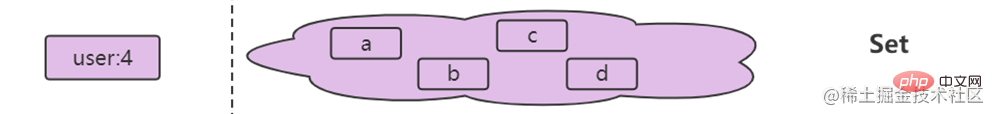
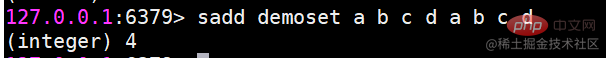
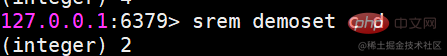
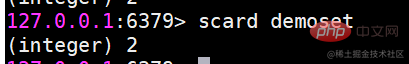
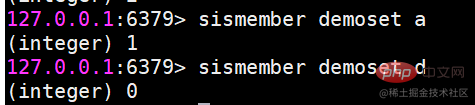
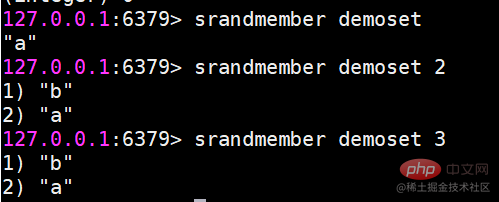
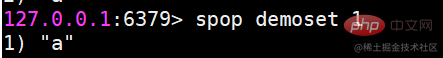
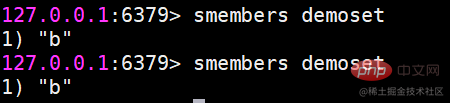
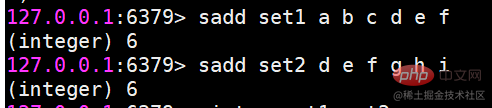 ##sinter Find the intersection of multiple sets
##sinter Find the intersection of multiple sets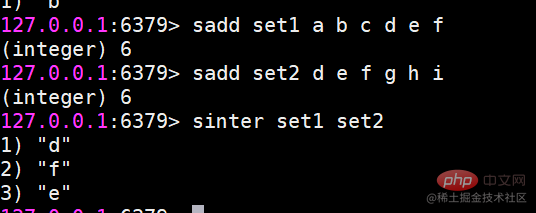 suinon Find the union of multiple sets
suinon Find the union of multiple sets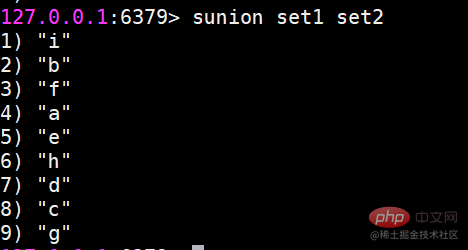 sdiff Find the difference of multiple sets
sdiff Find the difference of multiple sets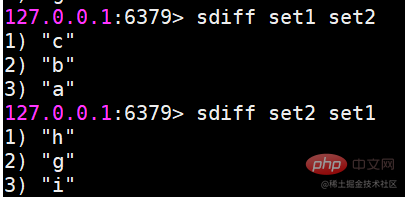 Save the results of intersection, union, and difference sets
Save the results of intersection, union, and difference sets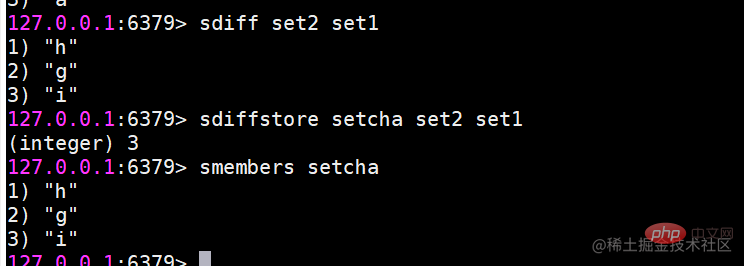 Usage scenario
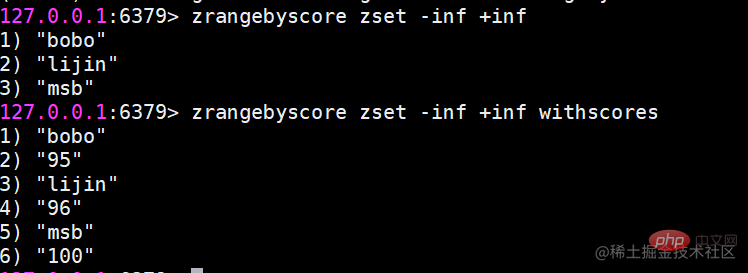
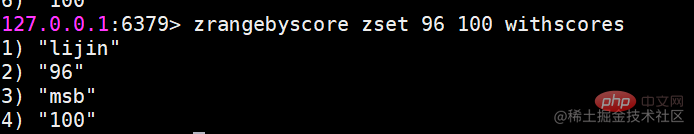
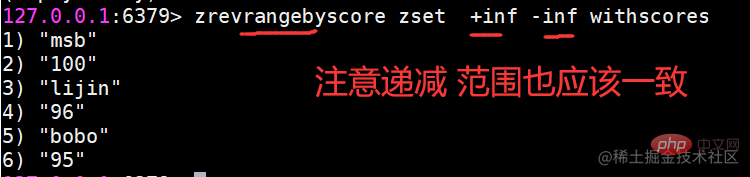
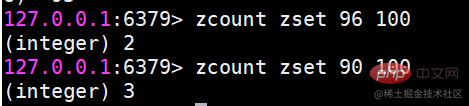
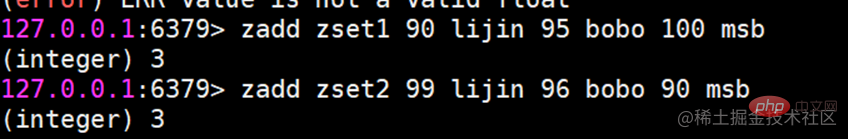
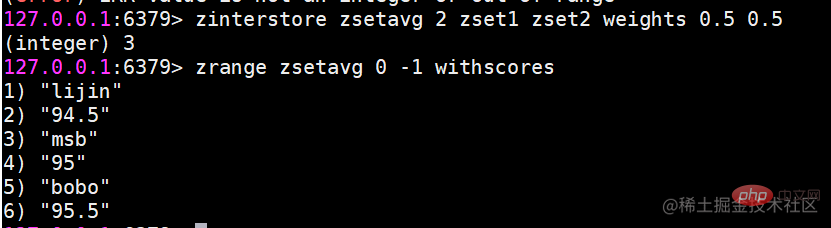
Usage scenario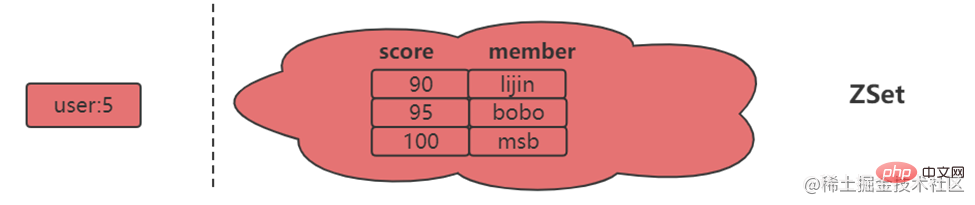 Ordered sets are a little unfamiliar compared to hashes, lists, and sets, but since they are called If an ordered set is an ordered set, then it must be related to the set. It retains the feature that the set cannot have duplicate members, but the difference is that the elements in the ordered set can be sorted. But unlike the list that uses index subscripts as the basis for sorting, it sets a score for each element as the basis for sorting.
Ordered sets are a little unfamiliar compared to hashes, lists, and sets, but since they are called If an ordered set is an ordered set, then it must be related to the set. It retains the feature that the set cannot have duplicate members, but the difference is that the elements in the ordered set can be sorted. But unlike the list that uses index subscripts as the basis for sorting, it sets a score for each element as the basis for sorting. 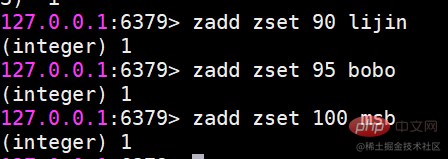 The return result represents the number of successfully added members
The return result represents the number of successfully added members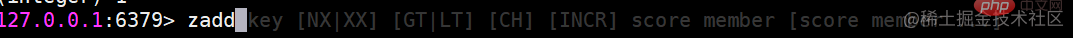 zadd command also has four options nx, xx, ch, incr. Four options
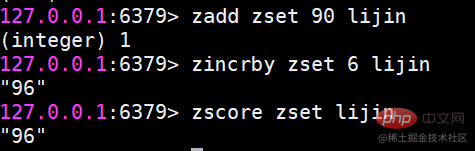
zadd command also has four options nx, xx, ch, incr. Four options zscore Calculate the score of a member
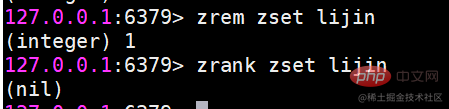
zscore Calculate the score of a member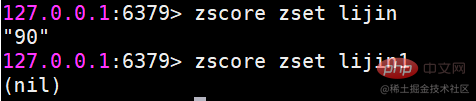 If the member does not exist, return nil
If the member does not exist, return nil