
In Linux, shell refers to "shell", which is the "command line interpreter" that exists on the operating system. It refers to a user-oriented command interface, which is expressed in a form that can be entered by the user. interface, this interface can also feed back running information. The functions of the shell: 1. Translate the user's commands to the kernel for processing; 2. Translate the core (kernel) processing results to the user.

#The operating environment of this tutorial: linux7.3 system, Dell G3 computer.
The shell program of Linux is called shell (command line interpreter), which refers to a user-oriented command interface. The form is an interface that can be entered by the user. This interface can also feed back running information
The function of shell is:
Translate the command to kernel
Translate the kernl processing result to the user
Generally, the shell we use is bash.
When interpreting a command, bash will not directly participate in the interpretation, but will create a new process to interpret the command. Bash only needs to wait for the result, which ensures the security of the bash process.
1. Reason
When using Linux, we all Compared with windows, linux does not have a graphical interface and uses the command line for operations. However, the command line method is not a direct operation of the computer. We know that the bottom layer of the computer is actually composed of
0 and 1. The transmission of each command will eventually be converted into 0,1 signals and transmitted to the computer to allow the computer to run the corresponding instructions. But if everyone uses computers in this way, it will undoubtedly be very difficult.
2. FunctionThe Linux operating system serves as a
core (kernel), and users cannot directly Its operation. Instead, it communicates with the computer through shell. The English meaning of "shell" is "shell", which is the "command line interpreter" that exists on the operating system and is used to translate user commands Processed by the core (kernel), the core (kernel) then translates the processing results to the userThe shell can actually be regarded as a
translator## between the user and the operating system #, the language barrier between the user and the operating systemcannot communicate directly , but the conversation is conducted through translation through the shell
3. Windows and Linux shells(1)windows
(2) linux
run the results through the kernel, and parse the results to the user through the shell
4. Existential significance(1) Facilitate communication between the user and the operating system
(2) Protect the operating system
avoiding the operating system from performing useless or harmful operations. For example, if we enter a string of garbled characters under Linux, the shell will intercept the command and return
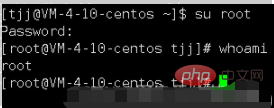
When the shell executes a command, it will execute the user's instructions by
forking a child process, and theshell itself will generally not execute the corresponding instructions . You can think of shell
itself as apresident of a translation dispatch company. When users have translation needs, they make requests to shell, and shell, as the president of a dispatch company, Generally, we will not provide door-to-door services in person, but will send other translators under our command to provide services in order to cope with the numerous and complex needs. These expatriate translators are a child process.
##1. The concept of Linux permissions
Permissions are the permissions for users in the operating system Constraintssuperuser, which is root. The other is ordinary users.
1. Super user (root)
There is only one root user. At the same time, the root user has the highest permissions on the operating system.
It can be considered that the root user in the operating system is like the emperor of an ancient country and is not bound by any legal provisions. Under the root user,executing any command will not be restricted by permissions. You canaccess other ordinary users' files and modify and delete them. You can execute delete the root directory of the operating system, database and other operations that will cause serious damage to the operating system or even crash
Therefore, the password of the root account must be set to a complex one and kept well.The command prompt of root user is“#”
##2. Ordinary userOrdinary users can have multiple
. Ordinary users will be subject to permission constraints. These permission constraints come from the system and root users.
The command prompt for ordinary usersis“$”
## (2) User switchingHere, you need to enter the password of the account you want to log in to. . Therefore, try to set the password for each account to be different 
exit
or use the shortcut key"ctrl d"that is Can
Note:
"su" under the root user, there is no need to enter the corresponding user password
execute an instruction that requires root permissions, and we If you don't want to switch users to execute , you can use the "sudo" command at this time. This command can temporarily elevate the permissions of ordinary users. Note: When entering the password, enter the password of this user, not the password of the root user
But at this time we will have the following error:
This is because 
2.linux permission management
In Linux, permissions are determined by "人"
and" Composed of "thing attributes". 人 refers to the user who performs the operation, Thing attribute refers to the attribute of the file (1) Classification of file visitors (people)
,other. Unlike root users and ordinary users, who are specific people, the three types of file visitors are a relatively abstract concept, which can be regarded as a role. That is The identities of other users under this file. For example, an ordinary user may appear to be the owner and group of files in his own directory, but may appear to other users' files to be other people1.Group to which they belong The reason for existence
Some people may be confused. The owner of the file is easy to understand with other people. The owner is the creator of the file, and
other is except the creator. If you are an external user, what is the significance of the group to which the file belongs? Suppose now we have Team A and Team B developing products on the same Linux machine. At this time, members of Team A have implemented a module, and the team leader wants to view the content of the module. . If owner and other exist in Linux, because owner is ourselves, then when the leader wants to view the code, we need to release other's permissions. But another team is also regarded as other by this document. Letting go of other means that not only the leader can see it, but also the other team can see your code, which can easily cause code leakage. To avoid this situation, you need to belong to a group. We only need to add the leader to the group to which the file belongs and release the permissions of the group, so that we can open the code to the leader without opening other permissions Now we have the above test.c file, you can see , there is a long list of attributes before the file name. Before, we knew at most "Oct 25 16:43" is the last modified time , 100 is the file in bytes. File disk usage . But we don’t know the previous attributes. 1. File visitors We also mentioned the classification of file visitors above. In fact, in the picture above The first root represents the owner , The second root refers to the group it belongs to . Other is not displayed, because users other than these two users belong to other, and there is no need to display 2. File type We all know that In Linux, the suffix of a file is meaningless . Because linux does not distinguish file types by file suffixes. But that doesn't mean there are no file types in Linux. Linux file types are distinguished by the first character in the first column of the attribute column displayed by "ll" . As you can see in the picture above, the first characters in test and test.c are the characters "d" and "-" respectively. These two characters are actually the file type. 1) Common file types in Linux -: Ordinary files mainly include source code, library files, Executable programs, document compression packages, etc. d: Directory files c: Character device files Mainly hardware , such as keyboard, monitor, etc. b: Block device file For example, disk l: Link file Taking windows as an example, the shortcut on the desktop is actually a link file. The shortcut links to the startup program of the corresponding software. Under linux, we execute the "ln -s a.out test" command: At this time, a # is created for the a.out file ##Link file test, and the beginning of the file is actually "l", which represents Link file p: Pipe file inter-process communication , I won’t go into details here, now you just need to know that such a file exists 3. File permissions file visitors are divided into three categories , and among these 9 characters, every three characters of represent a type of visitor's access rights . (1) File permission classification "r", "w", "x" . "r" stands for read, that is, reads the file. "w" represents writing , that is, modifying the content of the file. '"x" represents execution, that is, executes the corresponding file The visitor permissions of each file are composed of these three permissions. Sort in the manner of "rwx". If the corresponding permission is "-", that is, you do not have the permission As shown in the above picture, the permission "rwx -xr r-x" , means that the owner has read, write, and execute permissions; the group to which belongs has read and write permissions, but no execution permissions;The visitor has read and execute permissions, but no write permissions Permission. The spaces are added here just to facilitate the distinction. There will be no spaces in the actual display (2) Permission modification 1. Modify Permissions in Linux also support modification. When modifying, use the "chomd" command. For example, if we want to change the executor permissions in the picture below to "-wx", we can execute "chomd u-r test": This In this form, "u" represents the owner , "-" represents to remove the corresponding permission . And "g" represents the group to which belongs, and "o" represents other people . If you want to modify the permissions of other visitors, just modify "u" accordingly. If you want toadd some permission, you canchange "-" to "". Of course, when adding or deleting permissions, you can also use the form of multiple visitors and multiple permissions, such as "chmod u-rwx,g-rwx test": If you want to modify the permissions of all visitors , you can also change "u, g, o" to "a ” Bring the corresponding permissions, which will not be demonstrated here. 2. Modify the file owner and group To modify the file owner, you need to have the corresponding permissions, otherwise you need to use "sudo" Elevate rights. The command to modify the file owner is "chown corresponding user file name": If you want to modify the group it belongs to , use "chgrp" Command, The usage method is the same as "chown" , it will not be demonstrated here If you want to modify the owner and group at the same time , just use the "chown username:username file name" command, the usage method is the same: The root user is used here , no need for sudo to use, ordinary users need sudo. For other, there is no need to modify , because users other than the owner and the group they belong to are other 3. Permissions are modified at the same time We have said that in computers, all commands are transmitted in the form of 0,1 signals. Permissions existwith and without two states, which are also composed of 0 and 1. "rwx" can be seen as "111", "---" can be seen as "000". And if these binary are converted to octal, they are "7" and "0". Therefore, the octal range of permissions can be viewed as "[0, 7]". In octal, "r" represents 4, "w" represents 2, "x" represents 1 Thus, when modifying permissions, in addition to using "u-" to modify the permissions, we can alsomodify in octal form. That is"chmod the octal number combination of three visitors file name". For example, "chmod 777 test": This modification method is better than the first method to modify the permissions of multiple visitors one by one. To be convenient Note: If you do not write the whole number in this way, such as "7", "35", the system will work from back to front. That is, modify it from the direction of other->group->owner, because other permissions default to 0 at this time and will not be displayed. As shown below: In fact, the starting permission of the new directory is 777, and the new folder## The starting authority of # is 666. But what we actually see is not like this. The reason is that creating files or directories will be affected by umask (permission mask). that exists in the permission mask, the system will automatically configure it. When generating a file or directory, remove the permissions in the permission mask. "umask" command: first 0 is the permission that each visitor needs to remove. That is, by default in the system, the owner of each newly created file or directory does not need to remove permission , and the group to which belongs needs to remove 2, that is, write permission;Others need to remove 2, that is, write permission ordinary user is 002, and root user is 022 "umask 0 corresponding permissions". For example, "umask 0444": The umask value does not use the initial permission to reduce the permission value, but removes the corresponding permission . For example, the initial permission of the file is 666. At this time, we change the umask value to 0111. If you use subtraction, it will become 555, which is "r-xr-xr-x". But in fact it should beremove the "x" permission corresponding to 1, that is, it is still the "666" permission, that is"rw-rw-rw-": enter a directory, you need execution permissions, that is, "x" permissions: root user# If the above operation is performed under ##, can enter the directory without "x" permission, because the root user is not restricted by permissionsRelated recommendations: "(2) Thing attributes
3. Permission mask
(1) The role of permission mask
umask value, that is, the permission (2) View umask
To view the umask value, directly enter the (3) Modification The umask value
Although the umask value can be generated by the system by default, it can also be modified manually. The modification method is
The above is the detailed content of What does linux shell mean?. For more information, please follow other related articles on the PHP Chinese website!