 Web Front-end
Web Front-end
 JS Tutorial
JS Tutorial
 Node learning talks about the working principle of Cookie-Session login verification
Node learning talks about the working principle of Cookie-Session login verification
Node learning talks about the working principle of Cookie-Session login verification

At present, most systems are indispensable for the Login verification function. This is mainly to save the user's status and limit the user's various behaviors. This makes it convenient and effective to control user permissions. For example, when a user logs in to Weibo, the operations of posting, following, and commenting should be performed under the user status after login.
There are two main ways to implement login verification: Cookie&Session and JWT. In this section we will first discuss the Cookie&Session The working principle will be introduced in detail. In subsequent articles, we will successively introduce JWT and how to use Cookie&Session and JWT to improve what we have learned in the previous sections. The simple user management system built is explained. [Related tutorial recommendations: nodejs video tutorial]
1️⃣ Cookie&Session
We know that HTTP is stateless. In other words, the HTTP requester and responder cannot maintain state, it is all one-time, and it does not know what happened in the previous and subsequent requests. But in some scenarios, we need to maintain state. Most typically, when a user logs in to Weibo, posts, follows, and comments should be under the user status after login.
At this time, Cookie and Session can be introduced to save the user's login status.
This article mainly introduces the
working principle of usingCookie-Session for login verification, aboutCookieandFor a detailed introduction to Session, please refer to this guy’s article: Cookie and Session Detailed Explanation
Why not use Cookie alone?
Cookie is stored in the browser. You can open the Console in the browser, select Application, and find#Cookie in storage is viewed:
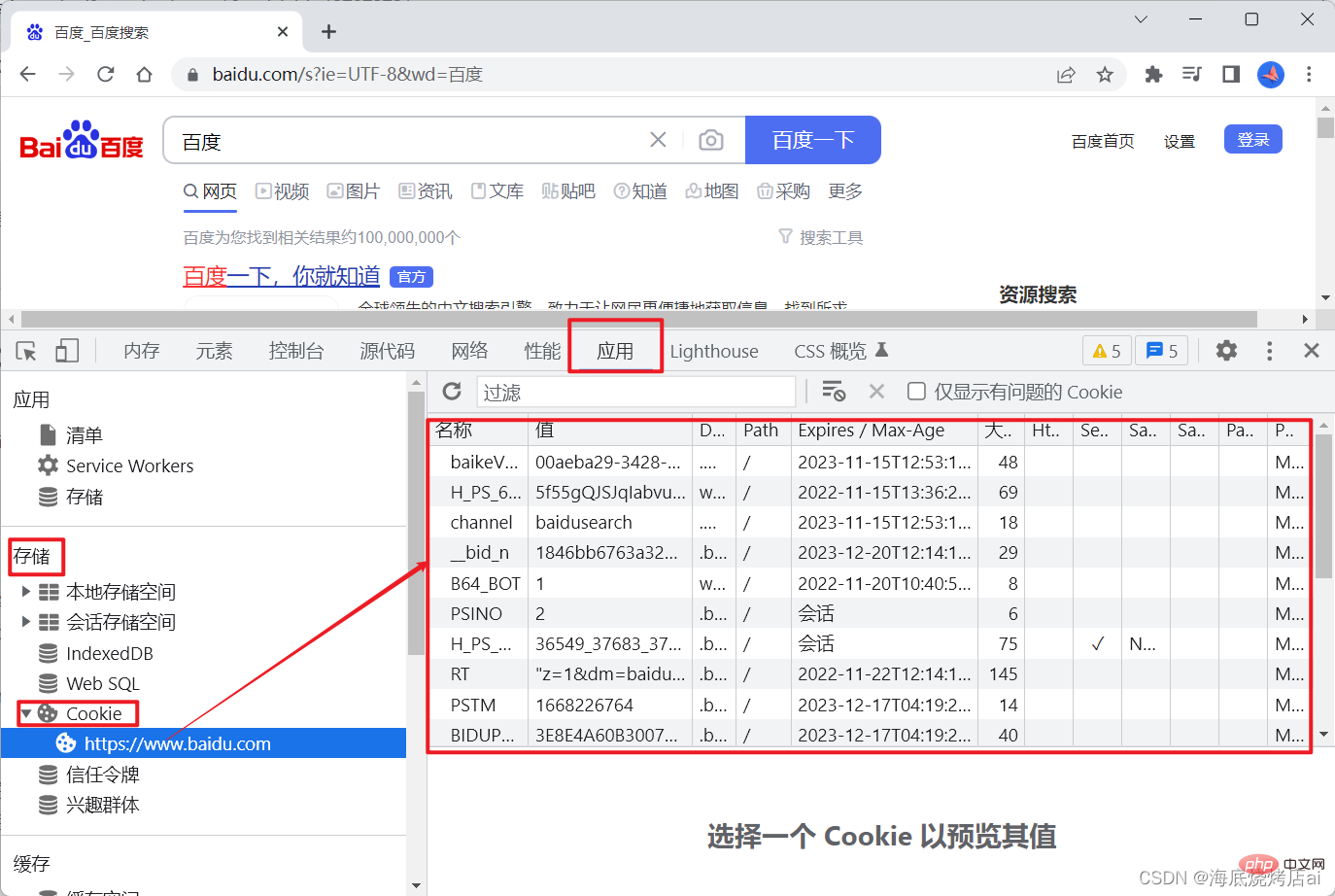
automatically Add Cookie to the request header so that the server can obtain this Cookie, as follows:
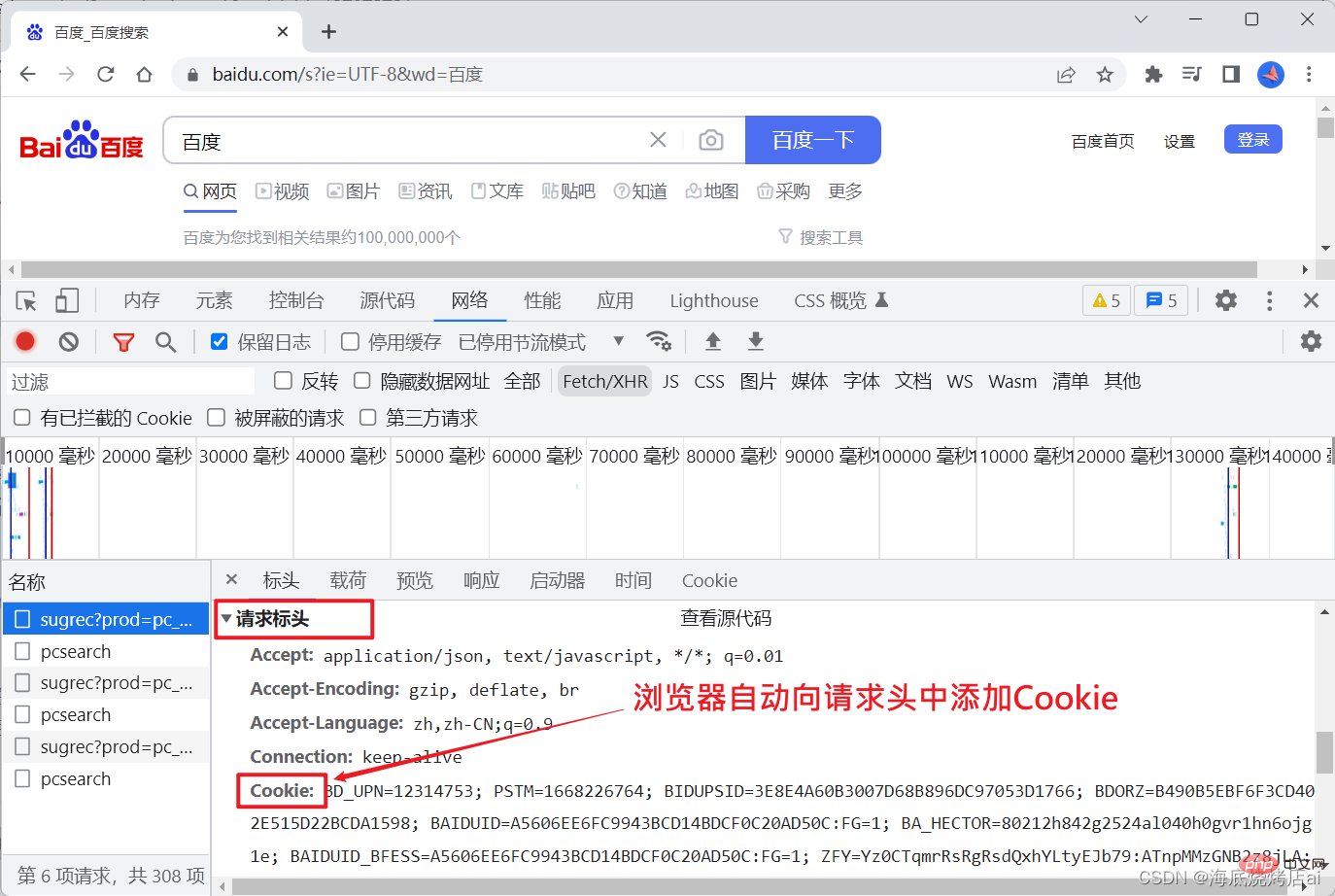
username, id, etc.) Generate a Cookie and store it in the browser, then every subsequent network request will automatically carry the Cookie.
Cookie and whether there are valid username and id# in the Cookie ##To determine whether the user has logged in, won't the user's login status be saved? Go back to the Weibo example we mentioned above. According to this process, when the user logs in,
has been saved. At this time, when the user publishes, follows, and comments When we need to log in to use the operation, we can determine in advance whether Cookie exists. If it exists and Cookie contains the user's id, then we can Allow these operations for the user (these operations generally require the user's id, which can be obtained from Cookie). On the contrary, if Cookie does not exist or Cookie is invalid, then these operations of the user are prohibited. Speaking of this, you may ask:
Cookie can achieve the effect we want, why should we use Session? This is because
Cookie is easily forged! , if we know that the information stored in Cookie is username and id (even if we don’t know, we can also make a request to the network after logging in Cookie is found in the body), then we can manually store a fake Cookie in the browser without logging in:
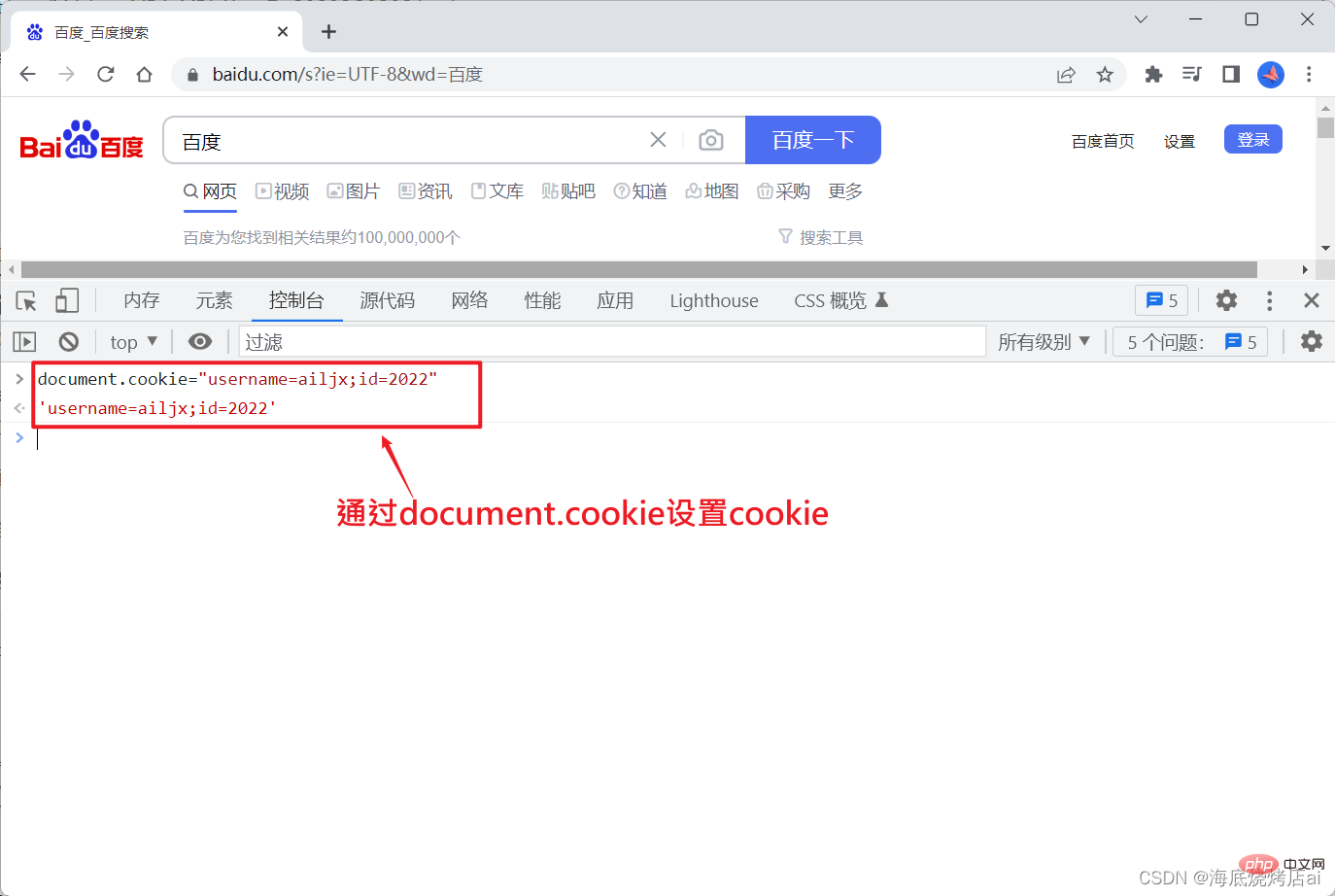 Speaking of this, you should be able to understand why
Speaking of this, you should be able to understand why
cannot be used alone.
#How is Session combined with Cookie?
Session is actually implemented based on When the user logs in successfully, the login verification using is generated by the server The server will store The server will store After receiving Every subsequent network request will automatically bring When the server receives a subsequent request, it obtains the Illustration: Session CSRF is called Cross-site request forgery. Cross-site request forgery, websites that use Cookie website A accountCookie, and Session is stored in the memory or database of the server. Cookie&Session will perform the following operations:
Session and SessionId; Session is generally generated based on the user’s login information, such as user name, id, etc.
If Session is compared to a lock, then SessionId is equivalent to the key of the lock. Session in memory or database; SessionId is stored in the Set-Cookie field in the request's response header (response object) and sent to the client; Set-Cookie, the client will automatically store the value of Set-Cookie (that is, SessionId) into Cookie; Cookie, that is, bring this SessionId;Cookie on the request, that is, it obtains the SessionId, and then passes the SessionId Query and verify the Session stored on the server. If the verification is successful, it means that the SessionId is valid and the request will be passed. Otherwise, the request will be blocked. 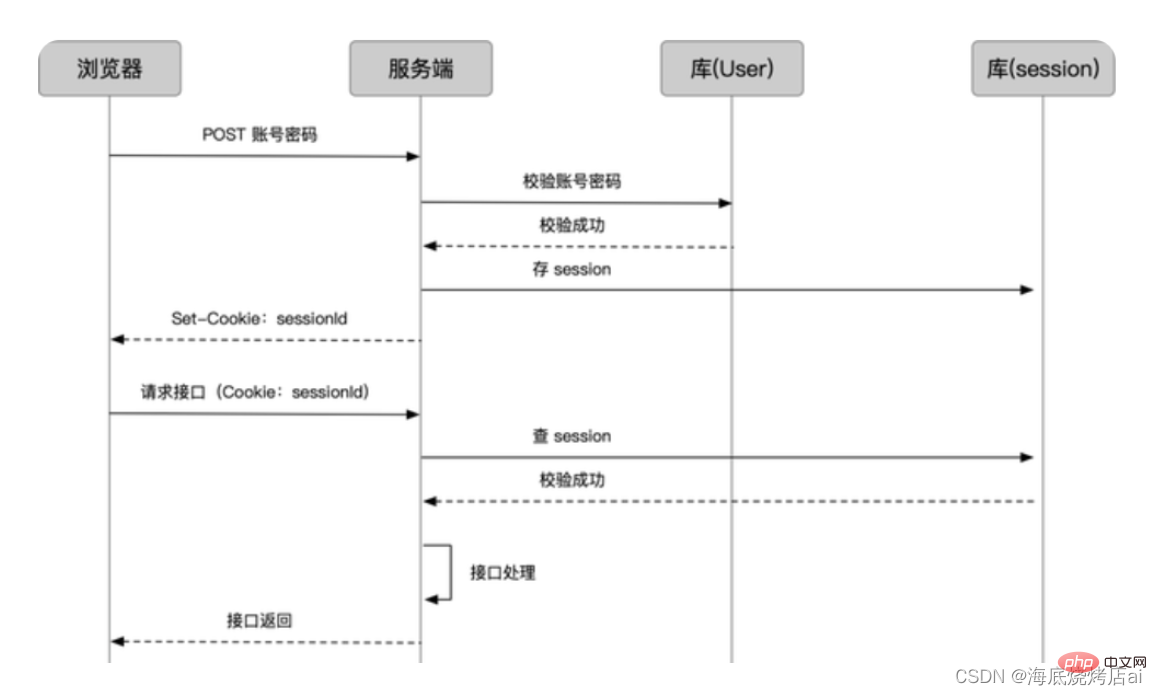
##2️⃣ Cookie&Session defects
Storage issues
In order to save the user's login status, we need to generate and store for each logged in user, which will inevitably cause the following problems : If
is stored in memory, then when the server restarts, the Session in these memories will be cleared, then all users’ The login status will expire, and when the number of users is large, excessive memory usage will inevitably affect the performance of the server.
is stored in the database, although it can solve the problem of user login status expiration due to server restart, when the number of users is large, the maintenance of this database will also change. relatively difficult.
sharing between the two servers, the Session is usually Stored in a separate database, this makes the entire project more complex and difficult to maintain. 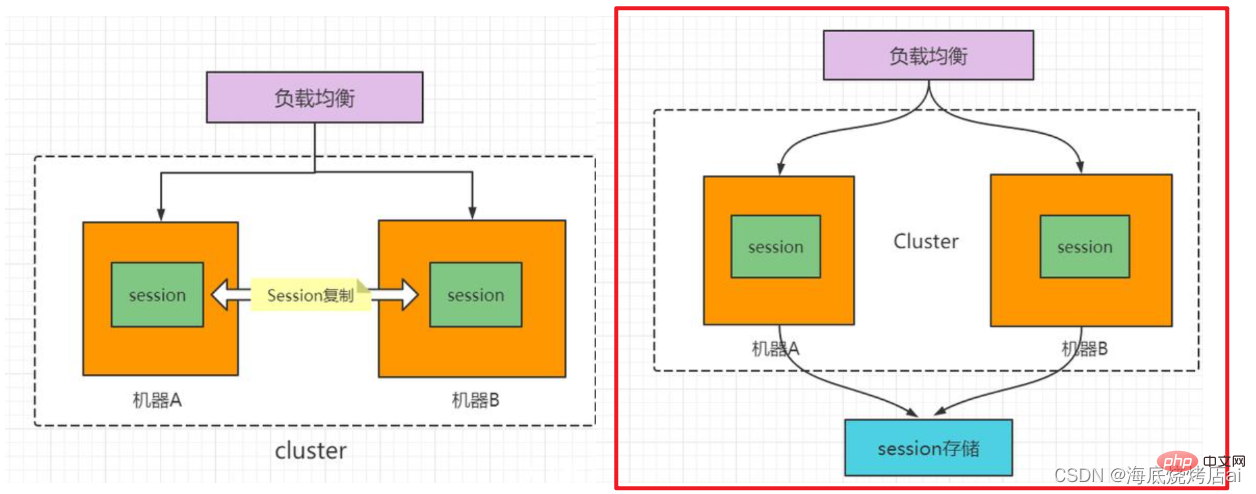
CSRF problem
for verification will face large or small CSRF threats, we use an example of a bank website to introduce CSRF Attack principle: 's login authentication uses Cookie&Session, and the transfer operation is used to run the # on the website ##Api address is: http://www.grillbankapi.com/?account=AccoutName&amount=1000Parameters:
:
represents the account name, amount represents the transfer amount. Then, a malicious attacker can place the following code on another <img src="/static/imghw/default1.png" data-src="http://www.grillbankapi.com/?account=Ailjx&amount=1000" class="lazy" alt="Node learning talks about the working principle of Cookie-Session login verification" >
Note:
Thenot long ago, the login information has not expired (src
website Aof the tag is theapi addressof the transfer operation ofwebsite A, and the parameteraccountis Ailjx, andamountis 1000 , that is to say, thisapi addressis equivalent to theapicalled when the account name is Ailjx and transfers 1000.If a user with the account name Ailjx has just visited
Cookie of website A exists and valid). Then when Ailjx visits this malicious website B
img tag will be loaded, and the browser will automatically request the img tag The src route is the request http://www.grillbankapi.com/?account=Ailjx&amount=1000 (we record this request as requestQ ), and because Cookie is stored in the browser and the browser will automatically bring Cookie when sending a request, so request Q will automatically carry Ailjx in The Cookie certificate on website A, the result is that this request Q will be passed , then Ailjx will lose 1000 funds .
This kind of malicious URL can take many forms and be hidden in many places on the web page. Additionally, the attacker does not need to control the website where the malicious URL is placed. For example, he can hide this address in forums, blogs, or any other website with user-generated content. This means that if there are no appropriate defense measures on the server side, users are still at risk of being attacked even if they visit familiar and trusted websites.
As can be seen from the example, the attacker cannot directly obtain the user's account control through CSRF attacks, nor can he directly steal any user information. What they can do is trick the user's browser into running operations on the user's behalf.
These are the problems with using Cookie&Session for login verification, so how do we solve these problems? This requires introducing the concept of JWT and using token for login verification, which we will explain in subsequent articles.
For more node-related knowledge, please visit: nodejs tutorial!
The above is the detailed content of Node learning talks about the working principle of Cookie-Session login verification. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 An article about memory control in Node
Apr 26, 2023 pm 05:37 PM
An article about memory control in Node
Apr 26, 2023 pm 05:37 PM
The Node service built based on non-blocking and event-driven has the advantage of low memory consumption and is very suitable for handling massive network requests. Under the premise of massive requests, issues related to "memory control" need to be considered. 1. V8’s garbage collection mechanism and memory limitations Js is controlled by the garbage collection machine
 Detailed graphic explanation of the memory and GC of the Node V8 engine
Mar 29, 2023 pm 06:02 PM
Detailed graphic explanation of the memory and GC of the Node V8 engine
Mar 29, 2023 pm 06:02 PM
This article will give you an in-depth understanding of the memory and garbage collector (GC) of the NodeJS V8 engine. I hope it will be helpful to you!
 How to use express to handle file upload in node project
Mar 28, 2023 pm 07:28 PM
How to use express to handle file upload in node project
Mar 28, 2023 pm 07:28 PM
How to handle file upload? The following article will introduce to you how to use express to handle file uploads in the node project. I hope it will be helpful to you!
 Let's talk in depth about the File module in Node
Apr 24, 2023 pm 05:49 PM
Let's talk in depth about the File module in Node
Apr 24, 2023 pm 05:49 PM
The file module is an encapsulation of underlying file operations, such as file reading/writing/opening/closing/delete adding, etc. The biggest feature of the file module is that all methods provide two versions of **synchronous** and **asynchronous**, with Methods with the sync suffix are all synchronization methods, and those without are all heterogeneous methods.
 An in-depth analysis of Node's process management tool 'pm2”
Apr 03, 2023 pm 06:02 PM
An in-depth analysis of Node's process management tool 'pm2”
Apr 03, 2023 pm 06:02 PM
This article will share with you Node's process management tool "pm2", and talk about why pm2 is needed, how to install and use pm2, I hope it will be helpful to everyone!
 Pi Node Teaching: What is a Pi Node? How to install and set up Pi Node?
Mar 05, 2025 pm 05:57 PM
Pi Node Teaching: What is a Pi Node? How to install and set up Pi Node?
Mar 05, 2025 pm 05:57 PM
Detailed explanation and installation guide for PiNetwork nodes This article will introduce the PiNetwork ecosystem in detail - Pi nodes, a key role in the PiNetwork ecosystem, and provide complete steps for installation and configuration. After the launch of the PiNetwork blockchain test network, Pi nodes have become an important part of many pioneers actively participating in the testing, preparing for the upcoming main network release. If you don’t know PiNetwork yet, please refer to what is Picoin? What is the price for listing? Pi usage, mining and security analysis. What is PiNetwork? The PiNetwork project started in 2019 and owns its exclusive cryptocurrency Pi Coin. The project aims to create a one that everyone can participate
 What should I do if node cannot use npm command?
Feb 08, 2023 am 10:09 AM
What should I do if node cannot use npm command?
Feb 08, 2023 am 10:09 AM
The reason why node cannot use the npm command is because the environment variables are not configured correctly. The solution is: 1. Open "System Properties"; 2. Find "Environment Variables" -> "System Variables", and then edit the environment variables; 3. Find the location of nodejs folder; 4. Click "OK".
 Let's talk about the event loop in Node
Apr 11, 2023 pm 07:08 PM
Let's talk about the event loop in Node
Apr 11, 2023 pm 07:08 PM
The event loop is a fundamental part of Node.js and enables asynchronous programming by ensuring that the main thread is not blocked. Understanding the event loop is crucial to building efficient applications. The following article will give you an in-depth understanding of the event loop in Node. I hope it will be helpful to you!





