
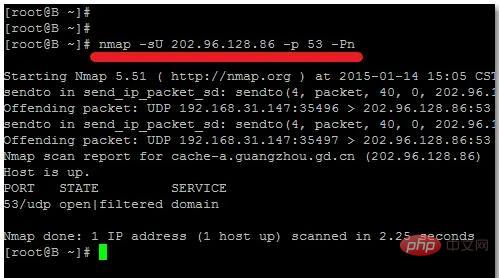
The nmap scan port command is "nmap -sU 202.96.128.86 -p 53 -Pn", where the parameter "-sU" indicates scanning the UDP port, and the parameter "-p 53" specifies the scanned port 53; by As a result of the nmap scan, you can see whether the port is open or closed or whether there are other information reports.

The operating environment of this tutorial: linux7.5 system, Nmap version 7.70, Dell G3 computer.
What is the nmap scan port command?
We can use nmap to scan port UDP. You can use the following command to see
nmap -sU 202.96.128.86 -p 53 -Pn
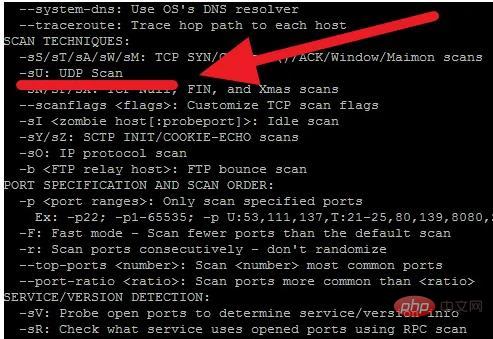
-sU in the nmap command line means scanning UDP port
The parameter in the command line -p 53 specifies the port 53 to scan. If you are scanning other ports, you can define it according to your own requirements, such as -p 1433 This way
-p <port ranges>: Only scan specified ports
Ex: -p22; -p1-65535; -p U:53,111,137,T:21-25,80,139,8080,S:9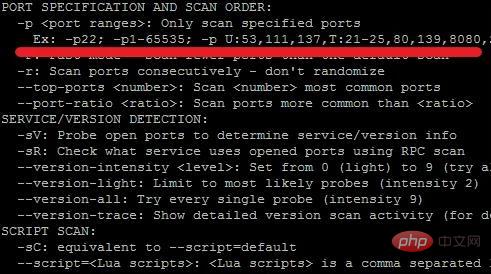
nmap -sU 202.96.128.166 -p 53 -Pn The -Pn parameter included in it is to bypass ping for scanning. If some servers are placed under the firewall If PING is prohibited, it may be skipped. So use -Pn to force scan
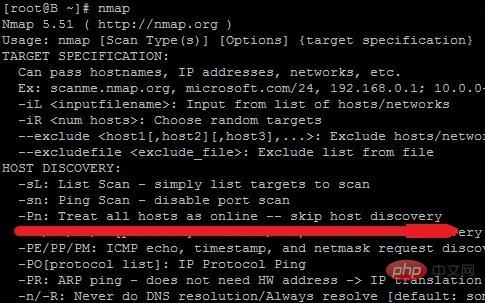
If the server bans PING or puts it under the firewall, without adding the -Pn parameter, it will think that the scanned host is not If it survives, it will not be scanned. If you do not add -Pn, the result will be like the following. It will also prompt you to add the -Pn parameter to try
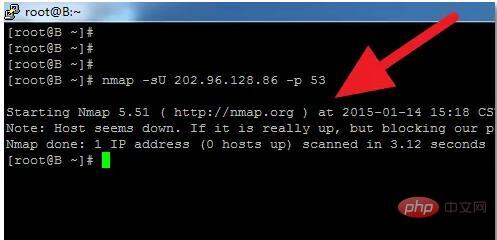
from By analyzing the results of the nmap scan, you can see whether the port is open or closed, or whether there are other information reports, etc.
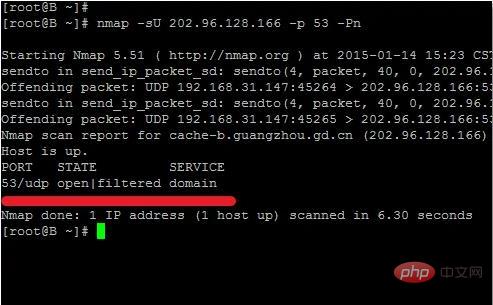
From the above results, we can see that the port is open and there is a filtered display, indicating that there is protection inside, so you need to add -Pn to test normally.
Note:
Testing UDP ports is a relatively rare thing, but it still needs to be used in the IDC industry. If you have a better way to test, please share it, thank you~
Recommended learning: "Linux Video Tutorial"
The above is the detailed content of What is the nmap scan port command?. For more information, please follow other related articles on the PHP Chinese website!




