How to install php7.2 on linux
How to install php7.2 on Linux: 1. Change the yum source through "sudo rpm -Uvh https://mirror.webtatic.com/yum/el7/webtatic-release.rpm"; 2. Through " sudo yum install yum-utils –y" to install PHP and check the PHP version; 3. Set the service to automatically start at boot and start the service; 4. Configure the PHP service running account.

The operating environment of this tutorial: linux5.9.8 system, php7.2 version, DELL G3 computer
How to install php7 on linux. 2 ?
Linux installation PHP7.2
The yum source of Linux does not exist for php7.x, so you need to change the yum source
sudo rpm -Uvh https://dl.fedoraproject.org/pub/epel/epel-release-latest-7.noarch.rpm sudo rpm -Uvh https://mirror.webtatic.com/yum/el7/webtatic-release.rpm
yum installation PHP
sudo yum -y install php72w-cli php72w-common php72w-devel php-mysqli php72w-fpm php72w php72w-cli php72w-fpm php72w-curl php72w-gd php72w-mysql php72w-xml php72w-mbstring sudo yum install yum-utils –y
Check PHP version
Output the following results, indicating successful installation
app@matomo:~$ php --version PHP 7.2.34 (cli) (built: Oct 1 2020 13:37:37) ( NTS ) Copyright (c) 1997-2018 The PHP Group Zend Engine v3.2.0, Copyright (c) 1998-2018 Zend Technologies
Set the service to automatically start at boot and start the service
[app@matomo ~]# sudo systemctl start php-fpm.service [app@matomo ~]# sudo systemctl enable php-fpm.service
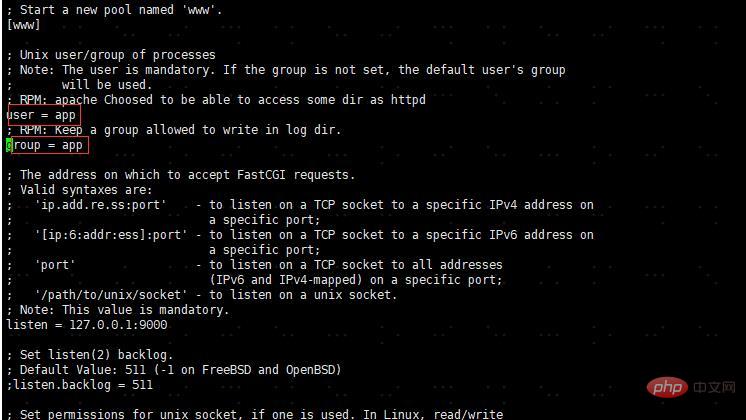
Configure PHP service Running account and group
app@matomo:~$sudo vim /etc/php-fpm.d/www.conf
As shown in the figure, modify user and group to your own definition
Restart the php-fpm service
Use sudo systemctl restart php-fpm.service or sudo service php-fpm restart
app@matomo:~$sudo service php-fpm restart Redirecting to /bin/systemctl restart php-fpm.service
Recommended learning: "PHP Video Tutorial"
The above is the detailed content of How to install php7.2 on linux. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1376
1376
 52
52
 Explain JSON Web Tokens (JWT) and their use case in PHP APIs.
Apr 05, 2025 am 12:04 AM
Explain JSON Web Tokens (JWT) and their use case in PHP APIs.
Apr 05, 2025 am 12:04 AM
JWT is an open standard based on JSON, used to securely transmit information between parties, mainly for identity authentication and information exchange. 1. JWT consists of three parts: Header, Payload and Signature. 2. The working principle of JWT includes three steps: generating JWT, verifying JWT and parsing Payload. 3. When using JWT for authentication in PHP, JWT can be generated and verified, and user role and permission information can be included in advanced usage. 4. Common errors include signature verification failure, token expiration, and payload oversized. Debugging skills include using debugging tools and logging. 5. Performance optimization and best practices include using appropriate signature algorithms, setting validity periods reasonably,
 Explain late static binding in PHP (static::).
Apr 03, 2025 am 12:04 AM
Explain late static binding in PHP (static::).
Apr 03, 2025 am 12:04 AM
Static binding (static::) implements late static binding (LSB) in PHP, allowing calling classes to be referenced in static contexts rather than defining classes. 1) The parsing process is performed at runtime, 2) Look up the call class in the inheritance relationship, 3) It may bring performance overhead.
 What are PHP magic methods (__construct, __destruct, __call, __get, __set, etc.) and provide use cases?
Apr 03, 2025 am 12:03 AM
What are PHP magic methods (__construct, __destruct, __call, __get, __set, etc.) and provide use cases?
Apr 03, 2025 am 12:03 AM
What are the magic methods of PHP? PHP's magic methods include: 1.\_\_construct, used to initialize objects; 2.\_\_destruct, used to clean up resources; 3.\_\_call, handle non-existent method calls; 4.\_\_get, implement dynamic attribute access; 5.\_\_set, implement dynamic attribute settings. These methods are automatically called in certain situations, improving code flexibility and efficiency.
 Explain the match expression (PHP 8 ) and how it differs from switch.
Apr 06, 2025 am 12:03 AM
Explain the match expression (PHP 8 ) and how it differs from switch.
Apr 06, 2025 am 12:03 AM
In PHP8, match expressions are a new control structure that returns different results based on the value of the expression. 1) It is similar to a switch statement, but returns a value instead of an execution statement block. 2) The match expression is strictly compared (===), which improves security. 3) It avoids possible break omissions in switch statements and enhances the simplicity and readability of the code.
 Four ways to implement multithreading in C language
Apr 03, 2025 pm 03:00 PM
Four ways to implement multithreading in C language
Apr 03, 2025 pm 03:00 PM
Multithreading in the language can greatly improve program efficiency. There are four main ways to implement multithreading in C language: Create independent processes: Create multiple independently running processes, each process has its own memory space. Pseudo-multithreading: Create multiple execution streams in a process that share the same memory space and execute alternately. Multi-threaded library: Use multi-threaded libraries such as pthreads to create and manage threads, providing rich thread operation functions. Coroutine: A lightweight multi-threaded implementation that divides tasks into small subtasks and executes them in turn.
 How to open web.xml
Apr 03, 2025 am 06:51 AM
How to open web.xml
Apr 03, 2025 am 06:51 AM
To open a web.xml file, you can use the following methods: Use a text editor (such as Notepad or TextEdit) to edit commands using an integrated development environment (such as Eclipse or NetBeans) (Windows: notepad web.xml; Mac/Linux: open -a TextEdit web.xml)
 Describe the purpose and usage of the ... (splat) operator in PHP function arguments and array unpacking.
Apr 06, 2025 am 12:07 AM
Describe the purpose and usage of the ... (splat) operator in PHP function arguments and array unpacking.
Apr 06, 2025 am 12:07 AM
The... (splat) operator in PHP is used to unpack function parameters and arrays, improving code simplicity and efficiency. 1) Function parameter unpacking: Pass the array element as a parameter to the function. 2) Array unpacking: Unpack an array into another array or as a function parameter.
 What is Cross-Site Request Forgery (CSRF) and how do you implement CSRF protection in PHP?
Apr 07, 2025 am 12:02 AM
What is Cross-Site Request Forgery (CSRF) and how do you implement CSRF protection in PHP?
Apr 07, 2025 am 12:02 AM
In PHP, you can effectively prevent CSRF attacks by using unpredictable tokens. Specific methods include: 1. Generate and embed CSRF tokens in the form; 2. Verify the validity of the token when processing the request.




