
SELinux has three working modes: Disabled, Permissive and Enforcing. In Disable mode, SELinux is turned off and the default DAC access control method is used. In Permissive mode, SELinux is enabled, but security policy rules are not enforced; access is still allowed when security policy rules should deny access. In Enforcing mode, SELinux is started and all security policy rules are enforced.

#The operating environment of this tutorial: linux7.3 system, Dell G3 computer.
SELinux, the abbreviation of Security Enhanced Linux, that is, security-enhanced Linux, is Developed jointly by the U.S. National Security Agency (NSA) and other security agencies (such as SCC), it aims to enhance the security of the traditional Linux operating system and solve various permission issues in the Discretionary Access Control (DAC) system in traditional Linux systems ( Such as root permission is too high, etc.).
The SELinux project was open sourced under the GPL license in 2000. SELinux gradually became popular when Red Hat included SELinux in its Linux distribution. Now, SELinux has been widely used by many organizations, and almost all Linux kernel versions 2.6 and above have integrated SELinux functions.
Beginners can understand SELinux in this way. It is a functional module deployed on Linux to enhance system security.
We know that in traditional Linux systems, the default permissions are to control the read, write and execution permissions of the owner, group and other people of the file or directory. This control method is called Discretionary access control (DAC) method; in SELinux, the mandatory access control (MAC) system is used, which is to control whether a process has access rights to files or directories on a specific file system, and The basis for determining whether a process can access a file or directory depends on many policy rules set in SELinux.
Note that in SELinux, the default permissions of Linux are still effective. That is to say, for a user to be able to access a file, the user's permissions are required to comply with the rwx permissions, and the user is also required to The process complies with SELinux regulations.However, there are so many processes and so many files in the system. If you manually allocate and specify them, the workload will be too large. Therefore, SELinux provides a lot of default policy rules, which are relatively complete. We will learn how to view and manage these policy rules later. In order to give readers a clear understanding of the role played by SELinux, here is an example. Suppose a vulnerability is discovered in apache, allowing a remote user to access sensitive files of the system (such as /etc/shadow). If SELinux is enabled in our Linux, then, because the apache service process does not have the permission to access /etc/shadow, the remote user's access to the /etc/shadow file through apache will be blocked by SELinux, which protects Linux. The role of the system.
1.Subject : It is the process that wants to access file or directory resources. To obtain resources, the basic process is as follows: the user calls a command, the command generates a process, and the process accesses the file or directory resource. In a discretionary access control system (Linux default permissions), the subject controlled by permissions is the user; in a mandatory access control system (SELinux), the subject controlled by policy rules is the process.
2. Object (Object): This concept is relatively clear, it is the file or directory resource that needs to be accessed.
3. Policy: There are a huge number of processes and files in the Linux system, so the number of SELinux rules that limit whether processes can access files is even more cumbersome. If each rule requires the administrator to manually settings, the availability of SELinux will be extremely low. Fortunately, we don't need to manually define the rules. SELinux defines two policies by default. The rules have been written in these two policies. By default, just call the policy and it can be used normally. The two default policies are as follows:
4. Security Context : Each process, file and directory has its own security context. Whether the process can access the file or directory depends on Does this security context match? If the security context of the process matches the security context of the file or directory, the process can access the file or directory. Of course, to determine whether the security context of a process matches the security context of a file or directory, you need to rely on the rules in the policy.
For example, we need to find a partner. Men can be regarded as the subject, and women are the targets. Whether a man can pursue a woman (whether the subject can access the target) mainly depends on whether the two people's personalities are suitable (whether the security context of the subject and the target matches). However, whether the personalities of two people are suitable needs to be judged based on specific conditions such as living habits, behavior, family environment, etc. (Whether the security context matches needs to be determined through the rules in the policy).
We draw a schematic diagram to show the relationship between these concepts, as shown in Figure 1.
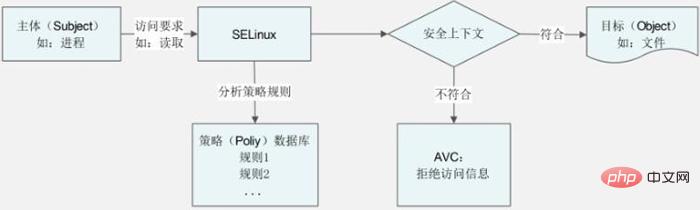
Figure 1 Related concepts of SELinux operating mode
Explain this diagram: When the subject wants to access the target, if SELinux is started in the system, the subject's Access requests first need to match the policies defined in SELinux. If the process complies with the rules defined in the policy, access is allowed. At this time, the security context of the process can be matched with the security context of the target; if the comparison fails, access is denied and the access vector cache is passed through AVC (Access Vector Cache). Mainly used to record all access statistics related to SELinux) and generate access denial information. If the security context matches, the target file can be accessed normally. Of course, whether the target file can be truly accessed in the end depends on whether the user who created the process (subject) has reasonable read, write, and execute permissions on the target file.
When we manage SELinux, we generally only>modify the security context of a file or directory so that it matches or does not match the security context of the accessing process to control the process Whether file or directory resources can be accessed; and the specific rules in the policy are rarely modified because there are too many rules and it is too complicated to modify. However, we can manually define whether the rules take effect to control the activation and deactivation of the rules.
Working modes of SELinux
SELinux provides 3 working modes: Disabled, Permissive and Enforcing, and each mode is suitable for Linux systems. Security provides different benefits.
Disable working mode (off mode)
In Disable mode, SELinux is turned off and default DAC access control method is used. This mode is useful for environments that do not require enhanced security.
For example, if a running application is working fine from your perspective, but is generating a large number of SELinux AVC reject messages, it may eventually fill up the log file and render the system unusable. In this case, the most straightforward solution is to disable SELinux, but you can also set the correct security context on the files your application accesses.
It should be noted that before disabling SELinux, you need to consider whether SELinux may be used again on the system. If you decide to set it to Enforcing or Permissive in the future, the system will automatically pass an SELinux file reprocess marking.
The way to turn off SELinux is also very simple. Just edit the configuration file /etc/selinux/config and change SELINUX= in the text to SELINUX=disabled. After restarting the system, SELinux will be disabled.
Permissive working mode (permissive mode)
In Permissive mode, SELinux is enabled, but the security policy rules and was not enforced. When security policy rules should deny access, access is still allowed. However, a message is sent to the log file indicating that access should be denied.
SELinux Permissive mode is mainly used in the following situations:
Review the current SELinux policy rules;
Test new applications to see what effect the SELinux policy rules will have when applied to these programs. ;
Resolve a problem where a specific service or application no longer works properly under SELinux.
In some cases, the audit2allow command can be used to read the SELinux audit log and generate new SELinux rules to selectively allow denied behavior, and this is also a case where SELinux is not disabled. Here's a quick way to get your application working on a Linux system.
Enforcing working mode (enforcing mode)
As can be seen from the name of this mode, in Enforcing mode , SELinux is started and all security policy rules are enforced.
Related recommendations: "Linux Video Tutorial"
The above is the detailed content of What are the three working modes of SELinux?. For more information, please follow other related articles on the PHP Chinese website!