
This article will talk about three common security precautions in Node. It mainly explains three security aspects when developing the Node server.

1. SQL injection
This is the most primitive and simplest attack. An attack method that has appeared since web2.0 with human-computer interaction.
It mainly involves inputting sql fragments. Finally, Spliced into a piece of attack sql code
When we use node to connect to the database, we usually write sql statements on the node side to query the database, such as the following
-- 这是一个简易的登录判断sql语句, 输入 username 和 password 在 users 表中进行用户登录验证, 然后获取用户的地址和年龄
select address, age from users where username=${username} and password=${password}But if I do something in the username so that he passes in a sql statement, it will be extremely dangerous [Related tutorial recommendations: nodejs video tutorial, programming teaching】
-- username 输入为 ali --
-- 上面这段 sql 就会被解析成这样
select address, age from users where username=ali -- and password=${password}Looking at the above code snippet, you can find that -- is a comment in sql, so if I dynamically obtain user input in sql query In the username field, if it ends with --, the conditional verification of the following password will be removed
That is, no matter what password the user enters, as long as the username field exists in the databaseGet the corresponding information
Of course the attacker can also continue to splice the sql statement to delete the database later, which is actually more dangerous-- username 输入为 ali; delete from users where username="ali" --
-- 就会拼接成下面这种语句 这是极其危险的
select address, age from users where username=ali; delete from users where username="ali" -- and password=${password}using the mysql npm package, so there are also processing functions corresponding to sql injection attacks in this package
You can use themysql.escape function to wrap all data from the front end. This function will escape -- or other special characters , so that it will not There will be comments in the sql statement
2. XSS attack
We should be very familiar with this attack as a front endThe attack method is to mix Js code into the display of the page to obtain web page informationWhen we develop the Node server, the data transmitted from the front end Just process them all, that is, escape special characters
(all escape characters need to be added; this special symbol was removed when I took the screenshot because it could not be demonstrated
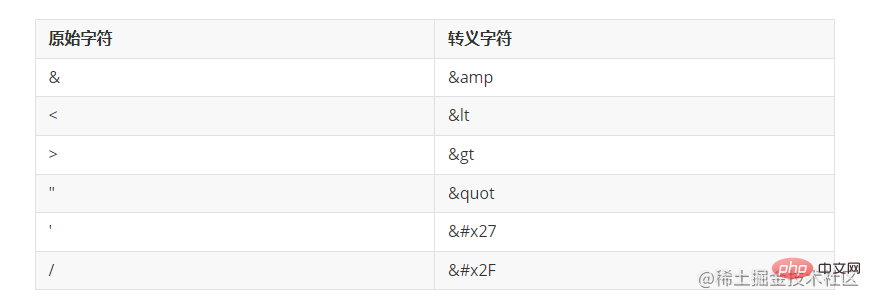
use the xss npm package, and use this package to wrap all the data passed in from the front end Just do it
3. Password encryption
If our database is invaded, the last thing that should not be leaked is the information usedBecause the attacker can use the user's account password to try to log in to other systems
No need to store the user's password in plain textInformation, before storing it in the databaseEncrypt the password with a custom key, of course this key needs to be kept exclusively by you and cannot be leaked
Original address: https://juejin.cn/post/7199329705706324027For more node-related knowledge, please visit:
nodejs tutorial!
The above is the detailed content of A brief analysis of three common security aspects of Node. For more information, please follow other related articles on the PHP Chinese website!
 Is python front-end or back-end?
Is python front-end or back-end?
 node.js debugging
node.js debugging
 How to implement instant messaging on the front end
How to implement instant messaging on the front end
 The difference between front-end and back-end
The difference between front-end and back-end
 Introduction to the relationship between php and front-end
Introduction to the relationship between php and front-end
 mul function usage
mul function usage
 What is a UI designer?
What is a UI designer?
 Usage of ModifyMenu
Usage of ModifyMenu
 The difference between css3.0 and css2.0
The difference between css3.0 and css2.0