 Technology peripherals
Technology peripherals
 AI
AI
 Even if a large area of the image is missing, it can be restored realistically. The new model CM-GAN takes into account the global structure and texture details.
Even if a large area of the image is missing, it can be restored realistically. The new model CM-GAN takes into account the global structure and texture details.
Even if a large area of the image is missing, it can be restored realistically. The new model CM-GAN takes into account the global structure and texture details.
Image restoration refers to completing the missing areas of the image, which is one of the basic tasks of computer vision. This direction has many practical applications, such as object removal, image retargeting, image synthesis, etc.
Early inpainting methods were based on image block synthesis or color diffusion to fill in missing parts of the image. To accomplish more complex image structures, researchers are turning to data-driven approaches, where they utilize deep generative networks to predict visual content and appearance. By training on large sets of images and aided by reconstruction and adversarial losses, generative inpainting models have been shown to produce more visually appealing results on various types of input data, including natural images and human faces.
However, existing works can only show good results in completing simple image structures, and generating image content with complex overall structures and high-detail fidelity is still a huge challenge, Especially when the image holes are large.
Essentially, image inpainting faces two key issues: one is how to accurately propagate global context to incomplete regions, and the other is to synthesize real local parts that are consistent with global cues. detail. To solve the global context propagation problem, existing networks utilize encoder-decoder structures, atrous convolutions, contextual attention, or Fourier convolutions to integrate long-range feature dependencies and expand the effective receptive field. Furthermore, the two-stage approach and iterative hole filling rely on predicting coarse results to enhance the global structure. However, these models lack a mechanism to capture high-level semantics of unmasked regions and effectively propagate them into holes to synthesize an overall global structure.
Based on this, researchers from the University of Rochester and Adobe Research proposed a new generation network: CM-GAN (cascaded modulation GAN), which can be better Geographically synthesize the overall structure and local details. CM-GAN includes an encoder with Fourier convolution blocks to extract multi-scale feature representations from input images with holes. There is also a two-stream decoder in CM-GAN, which sets a novel cascaded global spatial modulation block at each scale layer.
In each decoder block, we first apply global modulation to perform coarse and semantically aware structure synthesis, and then perform spatial modulation to further adjust the feature map in a spatially adaptive manner. . In addition, this study designed an object perception training scheme to prevent artifacts within the cavity to meet the needs of object removal tasks in real-life scenes. The study conducted extensive experiments to show that CM-GAN significantly outperforms existing methods in both quantitative and qualitative evaluations.

- Paper address: https://arxiv.org/pdf/2203.11947.pdf
- Project address: https://github.com/htzheng/CM-GAN-Inpainting
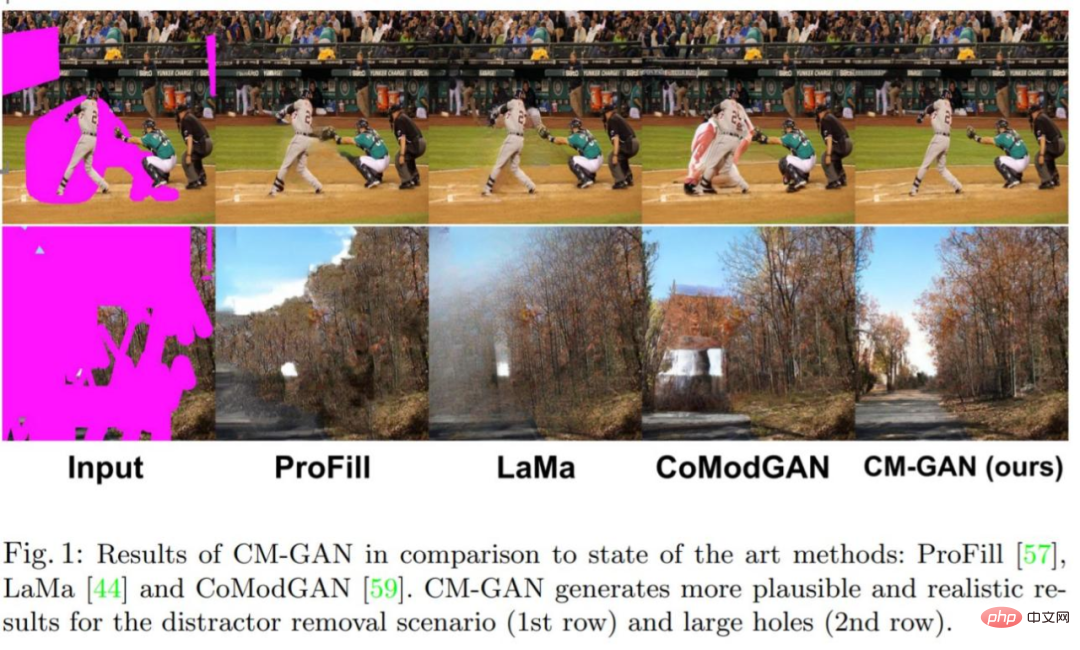
Let’s first look at the image repair effect. Compared with other methods, CM-GAN can reconstruct better textures:


##CM-GAN has better object boundaries:

Let’s take a look at the research methods and experimental results.
Method
Cascade Modulation GAN
In order to better model the global context of image completion, this study proposes a new mechanism that cascades global code modulation and spatial code modulation. This mechanism helps to deal with partially invalid features while better injecting global context into the spatial domain. The new architecture CM-GAN can well synthesize the overall structure and local details, as shown in Figure 1 below.
As shown in Figure 2 (left) below, CM-GAN is based on one encoder branch and two parallel cascades Decoder branch to generate visual output. The encoder takes part of the image and mask as input and generates multi-scale feature maps .
.
Different from most encoder-decoder methods, in order to complete the overall structure, this study extracts global style codes from the highest-level features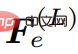 of the fully connected layer, and then
of the fully connected layer, and then 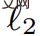 Normalized. Additionally, an MLP-based mapping network generates style codes w from noise to simulate the randomness of image generation. Codes w are combined with s to produce a global code g = [s; w], which is used in subsequent decoding steps.
Normalized. Additionally, an MLP-based mapping network generates style codes w from noise to simulate the randomness of image generation. Codes w are combined with s to produce a global code g = [s; w], which is used in subsequent decoding steps.
Global spatial cascade modulation. To better connect the global context during the decoding stage, this study proposes global spatial cascaded modulation (CM). As shown in Figure 2 (right), the decoding stage is based on two branches: global modulation block (GB) and spatial modulation block (SB), and upsamples global features F_g and local features F_s in parallel.
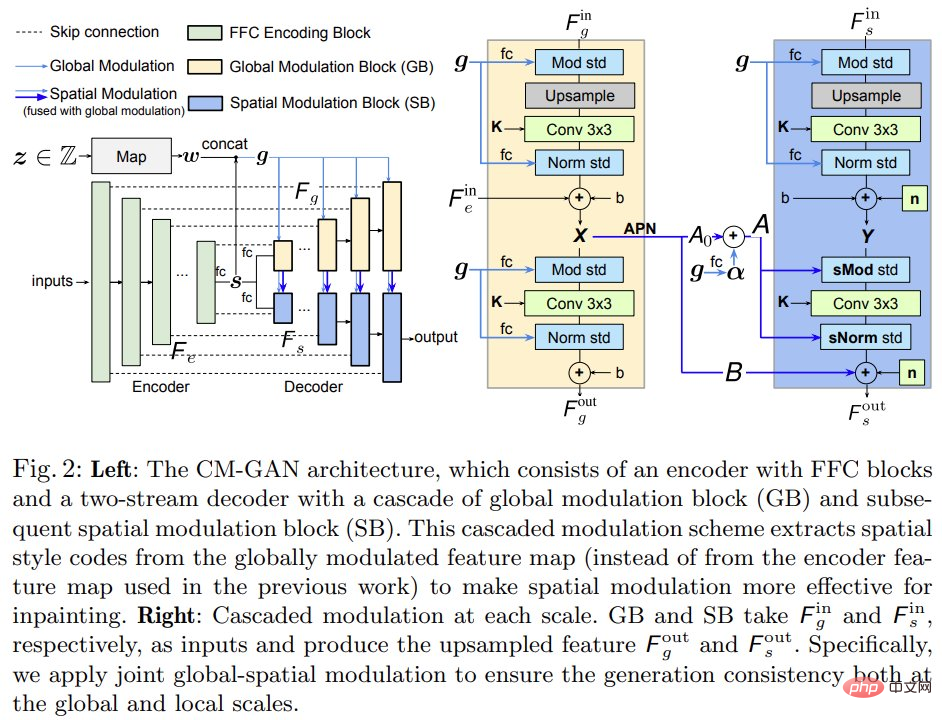
Unlike existing methods, CM-GAN introduces a new method of injecting global context into the hole region. At a conceptual level, it consists of cascaded global and spatial modulations between features at each scale, and naturally integrates three compensation mechanisms for global context modeling: 1) feature upsampling; 2) global modulation; 3 ) spatial modulation.
Object Perception Training
The algorithm that generates masks for training is crucial. Essentially, the sampled mask should be similar to the mask that would be drawn in the actual use case, and the mask should avoid covering the entire object or large parts of any new objects. Oversimplified masking schemes can lead to artifacts.
To better support real object removal use cases while preventing the model from synthesizing new objects within holes, this study proposes an object-aware training scheme that generates A more realistic mask, as shown in Figure 4 below.

Specifically, the study first passes the training images to the panoramic segmentation network PanopticFCN to generate highly accurate instance-level The annotations are segmented, then a mixture of free holes and object holes is sampled as an initial mask, and finally the overlap ratio between the hole and each instance in the image is calculated. If the overlap ratio is greater than the threshold, the method excludes the foreground instance from the hole; otherwise, the hole is left unchanged and the simulated object is completed with the threshold set to 0.5. The study randomly expands and translates object masks to avoid overfitting. Additionally, this study enlarges holes on instance segmentation boundaries to avoid leaking background pixels near holes into the inpainted region.
Training objective with Masked-R_1 regularization
The model is trained with a combination of adversarial loss and segmentation-based perceptual loss. Experiments show that this method can also achieve good results when purely using adversarial losses, but adding perceptual losses can further improve performance.
In addition, this study also proposes a masked-R_1 regularization specifically for adversarial training of stable inpainting tasks, where the mask m is utilized to avoid computing the gradient penalty outside the mask.
Experiment
This study conducted an image repair experiment on the Places2 data set at a resolution of 512 × 512, and gave the model's Quantitative and qualitative assessment results.
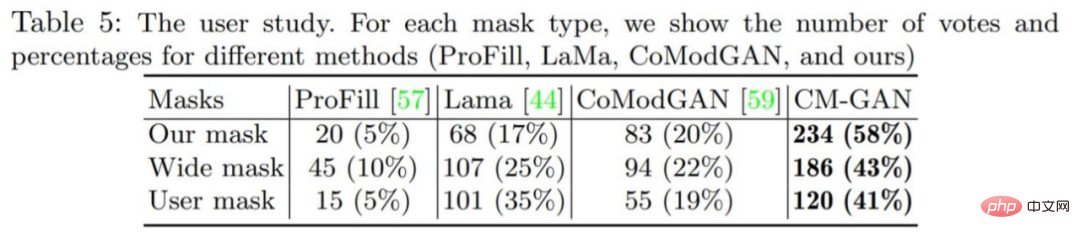
Quantitative evaluation: Table 1 below compares CM-GAN with other masking methods. The results show that CM-GAN significantly outperforms other methods in terms of FID, LPIPS, U-IDS, and P-IDS. With the help of perceptual loss, LaMa, CM-GAN achieves significantly better LPIPS scores than CoModGAN and other methods, thanks to the additional semantic guidance provided by the pre-trained perceptual model. Compared to LaMa/CoModGAN, CM-GAN reduces FID from 3.864/3.724 to 1.628.
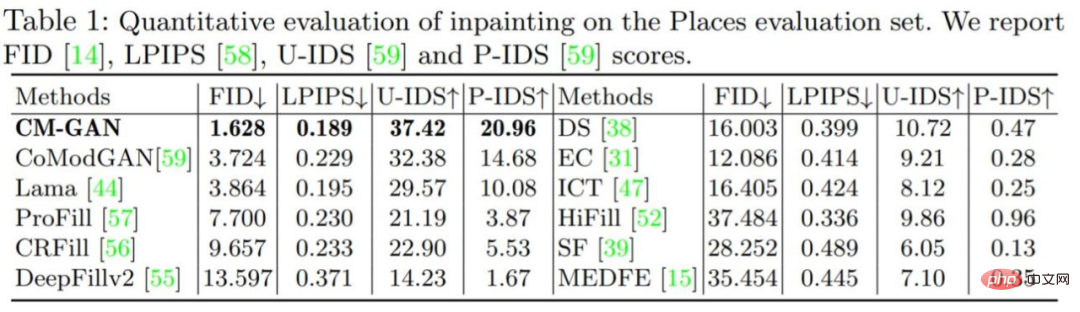
As shown in Table 3 below, with or without fine-tuning, CM-GAN has better performance in LaMa and CoModGAN masks Both have achieved significantly better performance gains than LaMa and CoModGAN, indicating that the model has generalization capabilities. It is worth noting that the performance of CM-GAN trained on CoModGAN mask, object-aware mask is still better than that of CoModGAN mask, confirming that CM-GAN has better generation ability.
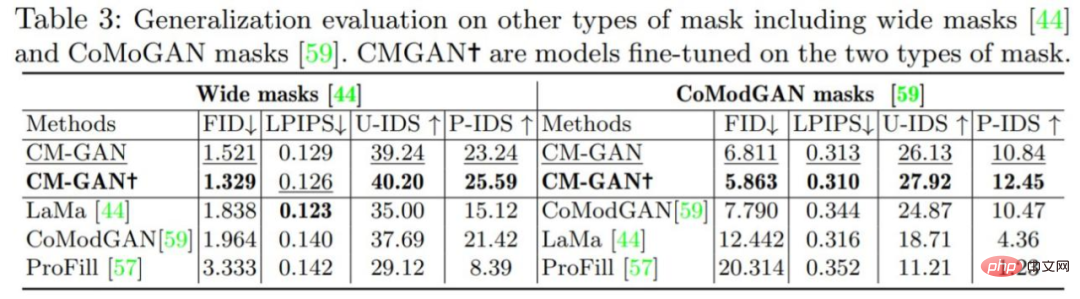



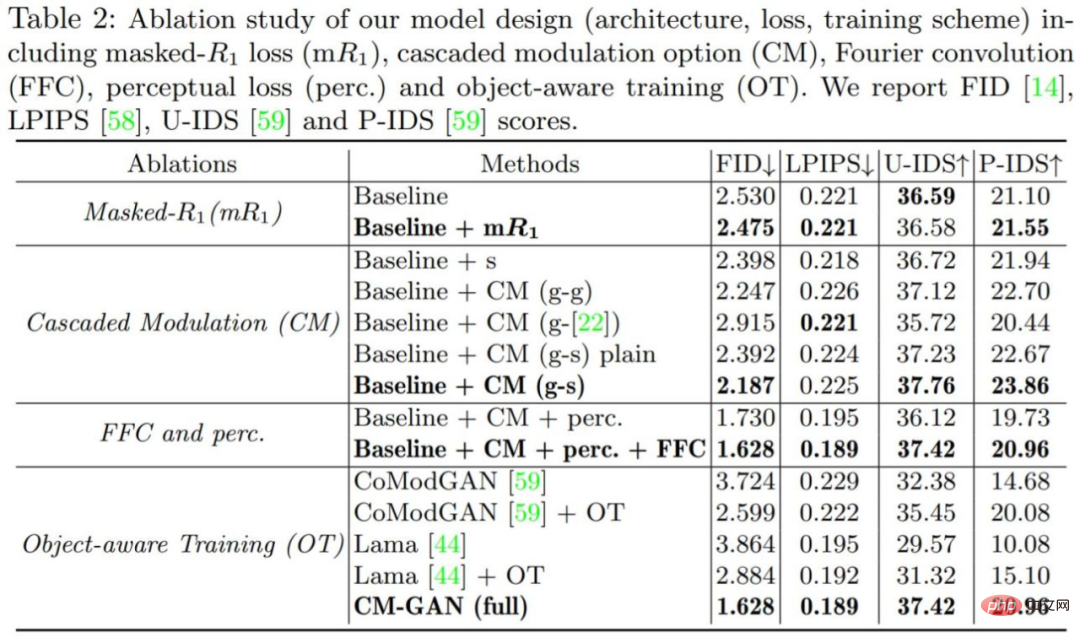
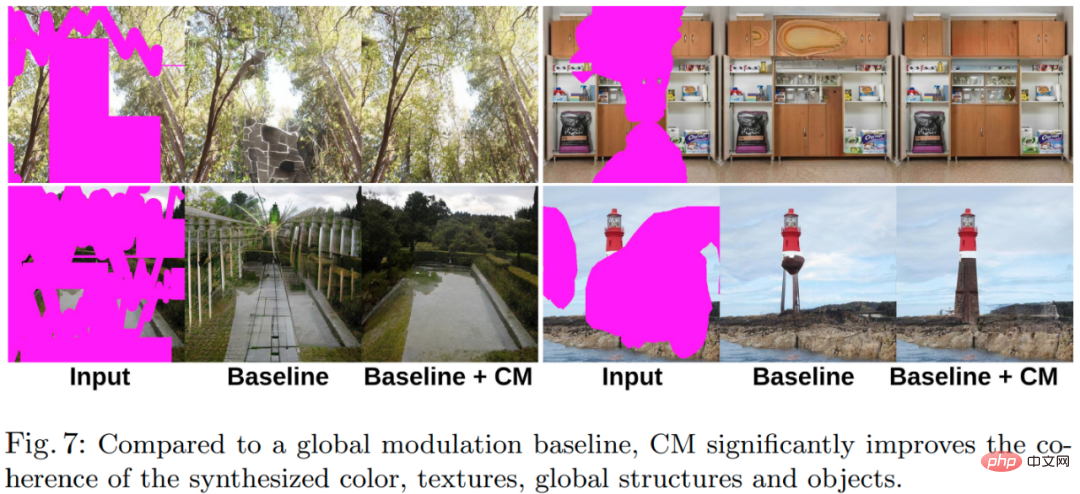
#To verify the importance of each component in the model, this study conducted a set of ablation experiments, and all models were trained and evaluated on the Places2 dataset. The results of the ablation experiment are shown in Table 2 and Figure 7 below.
 ##
##
The above is the detailed content of Even if a large area of the image is missing, it can be restored realistically. The new model CM-GAN takes into account the global structure and texture details.. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 This Apple ID is not yet in use in the iTunes Store: Fix
Jun 10, 2024 pm 05:42 PM
This Apple ID is not yet in use in the iTunes Store: Fix
Jun 10, 2024 pm 05:42 PM
When logging into iTunesStore using AppleID, this error saying "This AppleID has not been used in iTunesStore" may be thrown on the screen. There are no error messages to worry about, you can fix them by following these solution sets. Fix 1 – Change Shipping Address The main reason why this prompt appears in iTunes Store is that you don’t have the correct address in your AppleID profile. Step 1 – First, open iPhone Settings on your iPhone. Step 2 – AppleID should be on top of all other settings. So, open it. Step 3 – Once there, open the “Payment & Shipping” option. Step 4 – Verify your access using Face ID. step
 How to fix red-eye on iPhone
Feb 23, 2024 pm 04:31 PM
How to fix red-eye on iPhone
Feb 23, 2024 pm 04:31 PM
So, you took some great photos at your last party, but unfortunately, most of the photos you took were of red eyes. The photo itself is great, but the red eyes in it kind of ruin the image. Not to mention, some of those party photos might be from your friends’ phones. Today we'll look at how to remove red eye from photos. What causes the red eyes in the photo? Red-eye often occurs when taking photos with flash. This is because the light from the flash shines directly into the back of the eye, causing the blood vessels under the eye to reflect the light, giving the effect of red eyes in the photo. Fortunately, with the continuous advancement of technology, some cameras are now equipped with red-eye correction functions that can effectively solve this problem. By using this feature, the camera takes pictures
 How to solve the problem of Win11 failing to verify credentials?
Jan 30, 2024 pm 02:03 PM
How to solve the problem of Win11 failing to verify credentials?
Jan 30, 2024 pm 02:03 PM
When a Win11 user uses credentials to log in, he or she receives an error message stating that your credentials cannot be verified. What is going on? After the editor investigated this problem, I found that there may be several different situations that directly or indirectly cause this problem. Let's take a look with the editor.
 An easy guide to fixing Windows 11 blue screen issues
Dec 27, 2023 pm 02:26 PM
An easy guide to fixing Windows 11 blue screen issues
Dec 27, 2023 pm 02:26 PM
Many friends always encounter blue screens when using computer operating systems. Even the latest win11 system cannot escape the fate of blue screens. Therefore, today I have brought you a tutorial on how to repair win11 blue screens. No matter whether you have encountered a blue screen or not, you can learn it first in case you need it. How to fix win11 blue screen method 1. If we encounter a blue screen, first restart the system and check whether it can start normally. 2. If it can start normally, right-click "Computer" on the desktop and select "Manage" 3. Then expand "System Tools" on the left side of the pop-up window and select "Event Viewer" 4. In the event viewer, we will You can see what specific problem caused the blue screen. 5. Then just follow the blue screen situation and events
 Comprehensive Guide to PHP 500 Errors: Causes, Diagnosis and Fixes
Mar 22, 2024 pm 12:45 PM
Comprehensive Guide to PHP 500 Errors: Causes, Diagnosis and Fixes
Mar 22, 2024 pm 12:45 PM
A Comprehensive Guide to PHP 500 Errors: Causes, Diagnosis, and Fixes During PHP development, we often encounter errors with HTTP status code 500. This error is usually called "500InternalServerError", which means that some unknown errors occurred while processing the request on the server side. In this article, we will explore the common causes of PHP500 errors, how to diagnose them, and how to fix them, and provide specific code examples for reference. Common causes of 1.500 errors 1.
 How to fix the volume cannot be adjusted in WIN10
Mar 27, 2024 pm 05:16 PM
How to fix the volume cannot be adjusted in WIN10
Mar 27, 2024 pm 05:16 PM
1. Press win+r to open the run window, enter [regedit] and press Enter to open the registry editor. 2. In the opened registry editor, click to expand [HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionRun]. In the blank space on the right, right-click and select [New - String Value], and rename it to [systray.exe]. 3. Double-click to open systray.exe, modify its numerical data to [C:WindowsSystem32systray.exe], and click [OK] to save the settings.
 How to fix the problem of being unable to access the Internet due to abnormal network card driver
Jan 06, 2024 pm 06:33 PM
How to fix the problem of being unable to access the Internet due to abnormal network card driver
Jan 06, 2024 pm 06:33 PM
Some friends find that their computers cannot access the Internet because of abnormal network card drivers. They want to know how to fix it. In fact, current systems have built-in driver repair functions, so we only need to manually update the driver. If it doesn’t work, then we can fix it. Driver software can be used. How to fix the problem that the network card driver is abnormal and cannot connect to the Internet: PS: If this problem occurs suddenly, you can try restarting the computer first. If it still doesn't work after restarting, continue with the following operations. Method 1: 1. First, right-click on the taskbar and select "Start Menu" 2. Open "Device Manager" in the right-click menu. 3. Click "Network Adapter", then select "Update Driver" and click "Automatically search for driver". After the update is completed, you can surf the Internet normally. 5. Some users are also affected by the problem.
 Fix aksfridge.sys blue screen error in Windows 11/10
Feb 11, 2024 am 11:30 AM
Fix aksfridge.sys blue screen error in Windows 11/10
Feb 11, 2024 am 11:30 AM
If you encounter aksfridge.sys blue screen error after upgrading to Windows 11 or Windows 10, this article will provide you with solutions. You can try the following methods to successfully resolve this issue. The genuine aksfridge.sys file is the software component of AladdinHASP from AladdinKnowledgeSystems. AladdinHASP (Hardware Anti-Software Piracy) is a suite of digital rights management (DRM) protection and licensing software. Aksfridge.sys is a filter driver necessary for HASP to function properly. This component adds support for specialized external devices. Hardware Anti-Software Piracy, also known as AladdinHAS





