 Technology peripherals
Technology peripherals
 AI
AI
 Understand car-grade security chips and chip security testing technology in one article
Understand car-grade security chips and chip security testing technology in one article
Understand car-grade security chips and chip security testing technology in one article
With the development of intelligence and Internet of Vehicles in the global automotive industry, people in the new era are increasingly enjoying convenient travel and comfortable driving experience. However, various risks brought by the networked environment are also coming quietly, whether it is the Internet, emergency calls, navigation systems, automatic charging, on-demand power supply, or location-based service advertisements, maintenance updates and traffic alerts, they will all become Potential loopholes in hacker attacks and frequent car security incidents make it urgent to build an information security protection system for intelligent connected cars. In the automotive information security protection system, automotive security chips are a very critical link. By adding security chips to vehicle-mounted devices such as central gateways, domain controllers, and ECUs, they can implement encryption of in-vehicle communications, identification of in-vehicle devices, and OBD Secure access to diagnostic devices. It can effectively prevent bus attacks such as CAN Ethernet, prevent illegal OBD devices from reading and writing, identify malicious nodes and send illegal messages, etc., and provide security guarantee for communication between vehicles and between vehicles and things, as well as the operation of vehicle systems. .
This article is based on automotive security chips. It first introduces the relevant standards of automotive-grade security chips, and then lists the main forms of automotive security chips based on different application scenarios, as well as their role in automotive electronic and electrical architecture. Through research and comparison with domestic and foreign mainstream automotive security chip solutions to understand the current situation and future trends, chip security testing technology is introduced as an important guarantee for the development of automotive security chips.
Related Standards for Automotive Security Chips
First of all, the automotive security chip is a car-grade chip. For car-grade chips, it mainly includes standards such as AEC and ISO 26262 .
AEC is the Automotive Electronics Council, which aims to establish common parts qualification and quality system standards. For specific standard details, please refer to Table 1:
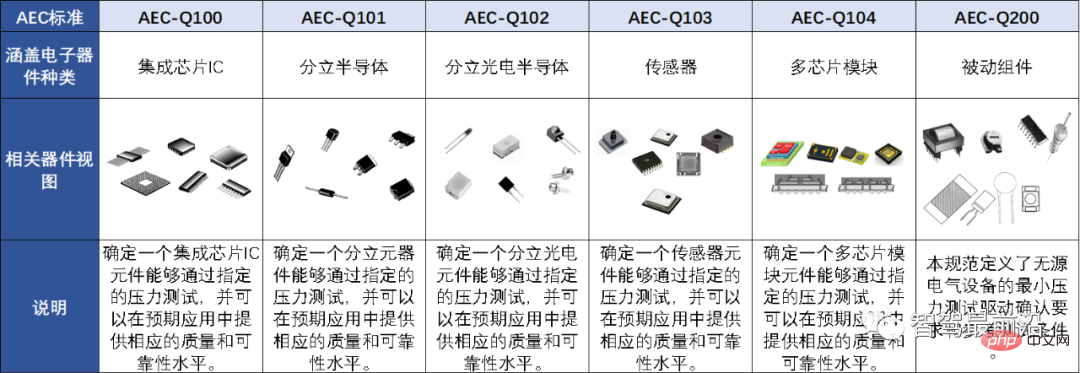
Table 1 Types of AEC standards
Car security chips belong to Integrated circuit chips, which belong to standard AEC-Q100, include grade details as shown in Table 2:
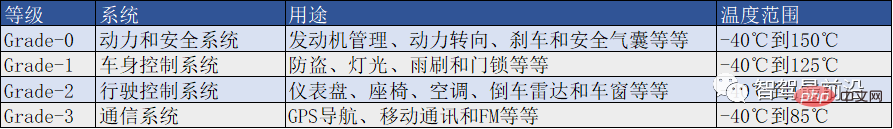
Table 2 AEC-Q100 standard grade description
ISO 26262 is an international standard for road vehicle functional safety. It is mainly aimed at functional safety and is used to determine the automotive safety integrity level ASIL (Automotive Safety Integrity Level). ASIL levels are divided into A, B, C and D. Automotive security chips need to meet this standard and corresponding level requirements.
At the same time, as a kind of security chip, automobile security chips also need to meet the relevant rating assessment of security chips. The current industry security rating standards for security chips include international, domestic EAL and national secret ratings.
The international evaluation assurance level EAL (Evaluation Assurance Level) includes 7 levels (EAL1 to EAL7). It is a standard that fully complies with the international standard CC (Common Criteria) and is developed to evaluate the security of IT products or systems. Numeric level. The domestic EAL level assessment is conducted by the China Cybersecurity Review Technology and Certification Center and includes 5 levels (EAL1 to EAL5).
The national secret level is evaluated according to the standards set by the State Cryptozoological Security Bureau, and is mainly divided into 3 levels of security. Security level 1 stipulates the minimum security standards that security capabilities need to meet, and provides basic protection measures for keys and sensitive information. Security level 2 is stipulated on the basis of level 1, with logical or physical protection measures to meet medium security level requirements. Security level 3 is the highest security level and requires comprehensive protection capabilities against various security risks.
Automotive security chip applications
There are three main types of application forms for automotive security chips. The first type is embedded in processors such as microcontrollers, microprocessors and ADAS. HSM (Hardware Security Module) hardware security module is mainly used in various controllers in the car to provide support for security functions such as safe startup and security algorithms. The second category is secure memory chips. This type of chip has a secure storage area and provides encrypted read and write functions. It is mainly used in areas with high security requirements for important data storage. The third category is a discrete security controller, including programmable SE (Secure Element) security unit or programmable security eSIM (V2X communication), which is mainly used in areas of vehicle external communication and frequent external access. It is worth mentioning that in the entire scenario of V2X secure communication, not only data encryption, data signature, and identity verification are required, but also end-to-end reliability and security must be ensured. In addition, V2X security chips must be able to achieve high performance. Meet the current requirements of the "new four modernizations". The classification of automotive security chip application forms and the layout of in-car applications are shown in Figure 1.
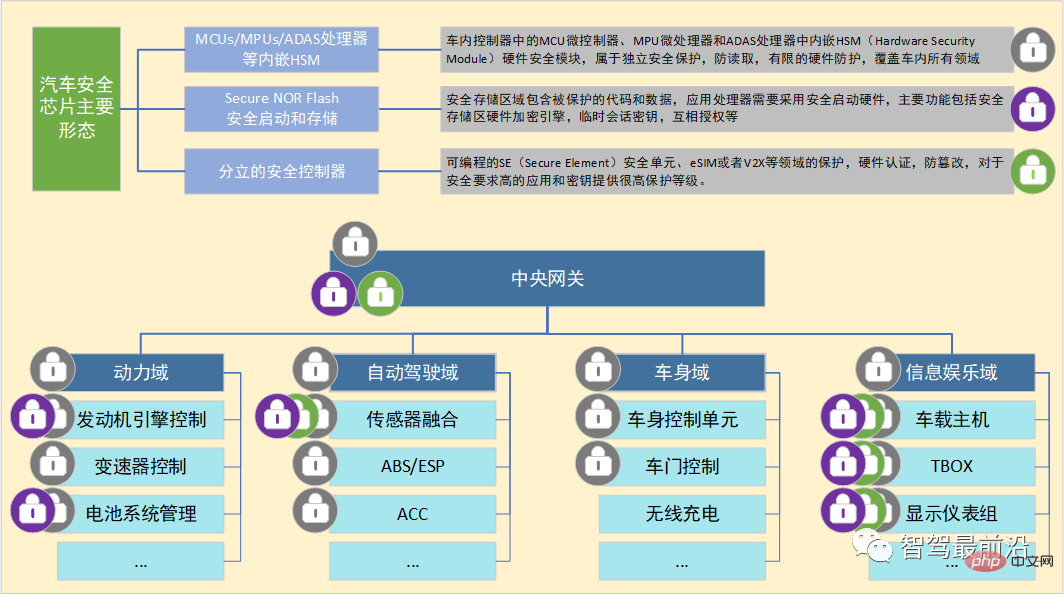
Figure 1 Main forms of automotive security chips and their application layout in automobiles
Automotive security chip products abroad Companies mainly include: ST, NXP, Infineon, Renesas, TI and Microchip, etc. Domestic companies include: Ziguang Tongxin, Huada Microelectronics, Hongsi Electronics, Core Titanium, National Technology, Fudan Microelectronics, Corechi, Black Sesame and Horizon, etc. After market research, relevant products of domestic and foreign manufacturers can be found in Table 3.
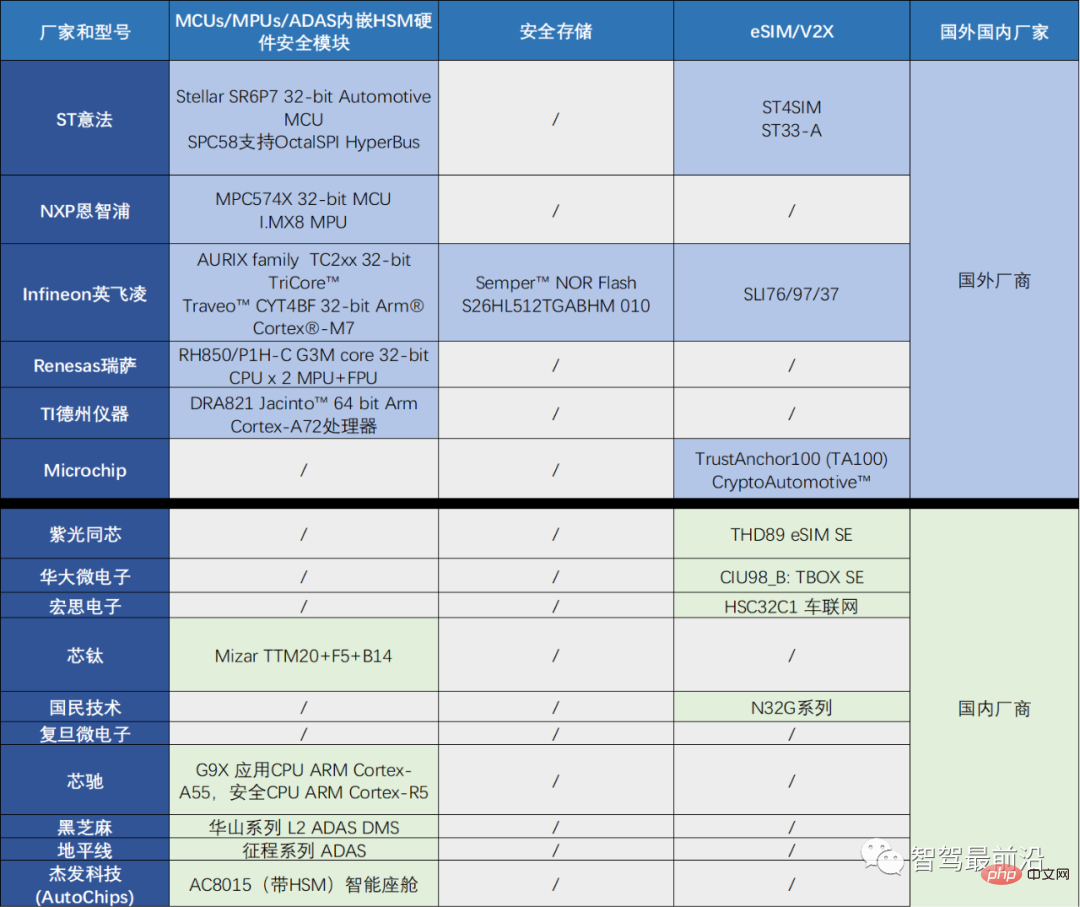
Table 3 Car-grade safety chip solutions from domestic and foreign manufacturers
Chip safety test Technology
There is no doubt that for vehicle-mounted security chips, when applied to vehicle terminal systems, their information security characteristics need to undergo strict and standardized testing and evaluation by third-party organizations. The security testing technology of automotive chips is inherited from the integrated circuit security testing technology. It is mainly performed by simulating hacker security attacks. The actual situation of the chip's resistance to various security attacks is combined with systematic analysis as its security indicator.
Security attack testing technology for chips mainly includes active and passive categories:
Active attack testing: The tester controls the input or operating environment of the chip to make the security chip operation behavior appear Abnormality, in this case, by analyzing the abnormal behavior of the chip operation, key sensitive information such as keys in the chip can be obtained. Common fault injection methods for active attacks include electromagnetic, laser, infrared, high voltage injection and other testing methods.
Passive attack test: The tester makes cryptographic devices such as chips run according to their specifications in most cases, or even run completely according to their specifications. In this case, by observing the physical characteristics of the chip (such as execution time, energy consumption, etc.), the tester may obtain key sensitive information such as keys. A commonly used method for passive testing is side channel attack, which includes analyzing signal characteristics such as timing, power, and electromagnetic radiation of the chip.
Chip security testing requires professional equipment and professionals. Test execution methods mainly include non-invasive, semi-invasive and intrusive. For details, see Table 4:
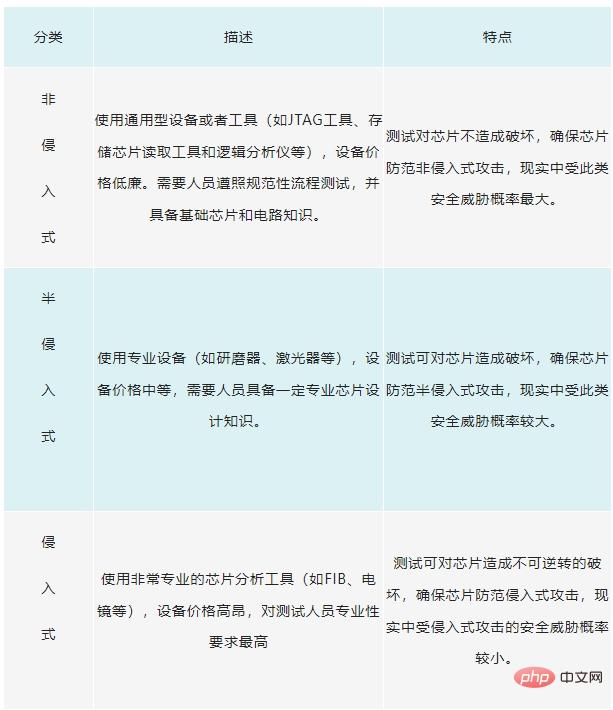
Table 4 Security Chip Security Test Method
The above is the detailed content of Understand car-grade security chips and chip security testing technology in one article. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1378
1378
 52
52
 The Stable Diffusion 3 paper is finally released, and the architectural details are revealed. Will it help to reproduce Sora?
Mar 06, 2024 pm 05:34 PM
The Stable Diffusion 3 paper is finally released, and the architectural details are revealed. Will it help to reproduce Sora?
Mar 06, 2024 pm 05:34 PM
StableDiffusion3’s paper is finally here! This model was released two weeks ago and uses the same DiT (DiffusionTransformer) architecture as Sora. It caused quite a stir once it was released. Compared with the previous version, the quality of the images generated by StableDiffusion3 has been significantly improved. It now supports multi-theme prompts, and the text writing effect has also been improved, and garbled characters no longer appear. StabilityAI pointed out that StableDiffusion3 is a series of models with parameter sizes ranging from 800M to 8B. This parameter range means that the model can be run directly on many portable devices, significantly reducing the use of AI
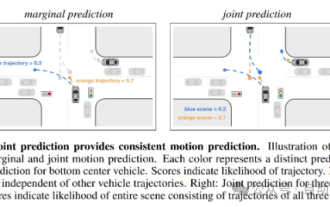 This article is enough for you to read about autonomous driving and trajectory prediction!
Feb 28, 2024 pm 07:20 PM
This article is enough for you to read about autonomous driving and trajectory prediction!
Feb 28, 2024 pm 07:20 PM
Trajectory prediction plays an important role in autonomous driving. Autonomous driving trajectory prediction refers to predicting the future driving trajectory of the vehicle by analyzing various data during the vehicle's driving process. As the core module of autonomous driving, the quality of trajectory prediction is crucial to downstream planning control. The trajectory prediction task has a rich technology stack and requires familiarity with autonomous driving dynamic/static perception, high-precision maps, lane lines, neural network architecture (CNN&GNN&Transformer) skills, etc. It is very difficult to get started! Many fans hope to get started with trajectory prediction as soon as possible and avoid pitfalls. Today I will take stock of some common problems and introductory learning methods for trajectory prediction! Introductory related knowledge 1. Are the preview papers in order? A: Look at the survey first, p
 First in China: Changxin Memory launches LPDDR5 DRAM memory chip
Nov 28, 2023 pm 09:29 PM
First in China: Changxin Memory launches LPDDR5 DRAM memory chip
Nov 28, 2023 pm 09:29 PM
News from this site on November 28. According to the official website of Changxin Memory, Changxin Memory has launched the latest LPDDR5DRAM memory chip. It is the first domestic brand to launch independently developed and produced LPDDR5 products, achieving a breakthrough in the domestic market and also making Changxin Storage's product layout in the mobile terminal market is more diversified. This website noticed that Changxin Memory LPDDR5 series products include 12Gb LPDDR5 particles, POP packaged 12GBLPDDR5 chips and DSC packaged 6GBLPDDR5 chips. The 12GBLPDDR5 chip has been verified on models of mainstream domestic mobile phone manufacturers such as Xiaomi and Transsion. LPDDR5 is a product launched by Changxin Storage for the mid-to-high-end mobile device market.
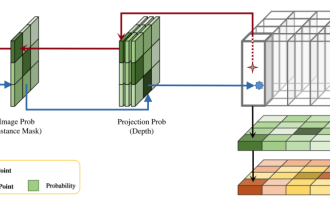 DualBEV: significantly surpassing BEVFormer and BEVDet4D, open the book!
Mar 21, 2024 pm 05:21 PM
DualBEV: significantly surpassing BEVFormer and BEVDet4D, open the book!
Mar 21, 2024 pm 05:21 PM
This paper explores the problem of accurately detecting objects from different viewing angles (such as perspective and bird's-eye view) in autonomous driving, especially how to effectively transform features from perspective (PV) to bird's-eye view (BEV) space. Transformation is implemented via the Visual Transformation (VT) module. Existing methods are broadly divided into two strategies: 2D to 3D and 3D to 2D conversion. 2D-to-3D methods improve dense 2D features by predicting depth probabilities, but the inherent uncertainty of depth predictions, especially in distant regions, may introduce inaccuracies. While 3D to 2D methods usually use 3D queries to sample 2D features and learn the attention weights of the correspondence between 3D and 2D features through a Transformer, which increases the computational and deployment time.
 It is reported that TSMC's advanced packaging customers are chasing orders significantly, and monthly production capacity is planned to increase by 120% next year
Nov 13, 2023 pm 12:29 PM
It is reported that TSMC's advanced packaging customers are chasing orders significantly, and monthly production capacity is planned to increase by 120% next year
Nov 13, 2023 pm 12:29 PM
News from this site on November 13, according to Taiwan Economic Daily, TSMC’s CoWoS advanced packaging demand is about to explode. In addition to NVIDIA, which has confirmed expanded orders in October, heavyweight customers such as Apple, AMD, Broadcom, and Marvell have also recently pursued orders significantly. According to reports, TSMC is working hard to accelerate the expansion of CoWoS advanced packaging production capacity to meet the needs of the above-mentioned five major customers. Next year's monthly production capacity is expected to increase by about 20% from the original target to 35,000 pieces. Analysts said that TSMC's five major customers have placed large orders, which shows that artificial intelligence applications have become widely popular, and major manufacturers are interested in artificial intelligence chips. The demand has increased significantly. Inquiries on this site found that the current CoWoS advanced packaging technology is mainly divided into three types - CoWos-S
 'Minecraft' turns into an AI town, and NPC residents role-play like real people
Jan 02, 2024 pm 06:25 PM
'Minecraft' turns into an AI town, and NPC residents role-play like real people
Jan 02, 2024 pm 06:25 PM
Please note that this square man is frowning, thinking about the identities of the "uninvited guests" in front of him. It turned out that she was in a dangerous situation, and once she realized this, she quickly began a mental search to find a strategy to solve the problem. Ultimately, she decided to flee the scene and then seek help as quickly as possible and take immediate action. At the same time, the person on the opposite side was thinking the same thing as her... There was such a scene in "Minecraft" where all the characters were controlled by artificial intelligence. Each of them has a unique identity setting. For example, the girl mentioned before is a 17-year-old but smart and brave courier. They have the ability to remember and think, and live like humans in this small town set in Minecraft. What drives them is a brand new,
 Sources say NVIDIA is developing China-specific versions of AI chips HGX H20, L20 PCle and L2 PCle
Nov 09, 2023 pm 03:33 PM
Sources say NVIDIA is developing China-specific versions of AI chips HGX H20, L20 PCle and L2 PCle
Nov 09, 2023 pm 03:33 PM
The latest news shows that according to reports from the Science and Technology Innovation Board Daily and Blue Whale Finance, industry chain sources revealed that NVIDIA has developed the latest version of AI chips suitable for the Chinese market, including HGXH20, L20PCle and L2PCle. As of now, NVIDIA has not commented. People familiar with the matter said that these three chips are all based on improvements from NVIDIA H100. NVIDIA is expected to announce them as soon as November 16, and domestic manufacturers will get samples as soon as these days. After checking public information, we learned that NVIDIAH100TensorCoreGPU adopts the new Hopper architecture, which is based on TSMC N4 process and integrates 80 billion transistors. Compared with the previous generation product, it can provide multi-expert (MoE)
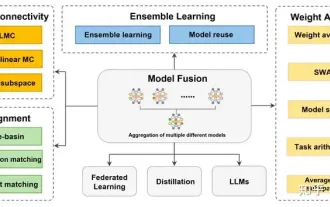 Review! Deep model fusion (LLM/basic model/federated learning/fine-tuning, etc.)
Apr 18, 2024 pm 09:43 PM
Review! Deep model fusion (LLM/basic model/federated learning/fine-tuning, etc.)
Apr 18, 2024 pm 09:43 PM
In September 23, the paper "DeepModelFusion:ASurvey" was published by the National University of Defense Technology, JD.com and Beijing Institute of Technology. Deep model fusion/merging is an emerging technology that combines the parameters or predictions of multiple deep learning models into a single model. It combines the capabilities of different models to compensate for the biases and errors of individual models for better performance. Deep model fusion on large-scale deep learning models (such as LLM and basic models) faces some challenges, including high computational cost, high-dimensional parameter space, interference between different heterogeneous models, etc. This article divides existing deep model fusion methods into four categories: (1) "Pattern connection", which connects solutions in the weight space through a loss-reducing path to obtain a better initial model fusion



