 Technology peripherals
Technology peripherals
 AI
AI
 This article takes you through the communication security architecture of smart car in-vehicle networks
This article takes you through the communication security architecture of smart car in-vehicle networks
This article takes you through the communication security architecture of smart car in-vehicle networks
At present, intelligence, networking, and electrification are the major trends in automobile development. Major automobile companies and Internet companies are actively cooperating to jointly open a new era of cloud. At the same time, attacks on intelligent connected cars occur frequently, making automotive network information security issues increasingly prominent.
In response to automotive network information security issues, Mercedes-Benz Cars established a cooperative relationship with 360 Group in 2017. 360 Group’s Intelligent Connected Vehicle Security Laboratory Sky- The Go team discovered 19 security vulnerabilities in Mercedes-Benz intelligent connected cars and fixed them. At the 2018 BYD Global Developers Conference, BYD and 360 Group formally signed a strategic cooperation agreement to jointly discuss and solve information security and network security issues for smart cars. Ju et al. studied the application of Ethernet in automotive in-vehicle networks and expectations for future automotive electrical and electronic (E/E) architectures. Wampler et al. proposed a corresponding universal security solution for the CAN bus. Lee et al. conducted attack experiments on cars to verify the network vulnerability of cars and the urgency of establishing security solutions. Chen et al. established a vehicle information system classification security protection assessment system with reference to the classification security protection evaluation standards of traditional information systems. Research by Haas and others uses artificial neural networks to establish an intrusion detection model for connected cars to filter attack data.
The above-mentioned studies are all conducted on automotive network information security, but a network information security protection solution for intelligent connected vehicle systems has not yet been proposed. From the perspective of automotive network information security, this paper proposes an automotive network communication security architecture solution. This solution builds a multi-domain hierarchical intrusion detection model to achieve a complete security protection system of prevention-detection-early warning.
1 Domain centralized electronic and electrical architecture
Nowadays, intelligent networked cars have more and more functions, and the corresponding electronic control units are equipped with The number of (electronic control units, ECUs) has also increased, and the remote communication that interacts with information such as the cloud and third-party APPs has also increased, which also increases the possibility of using the cloud and third-party software to carry out attacks. If the traditional automotive distributed electronic and electrical architecture is adopted, an excessive number of ECUs will not only cause complex wiring harness design and logic control problems, but also add hidden dangers to automotive network information security. The emergence of these problems shows that the distributed electronic and electrical architecture of modern automobiles needs to be reformed. The Society of Automotive Engineers has launched J3061TM Cybersecurity Guidelines for Cyber-Physical Integrated Systems, which aims to promote the establishment of security processes between automotive electrical systems and other interconnected systems through unified global standards. This article refers to the process defined by the "Vehicle Traditional System Functional Safety Standard ISO26262" to formulate a vehicle information security architecture diagram as shown in Figure 1.
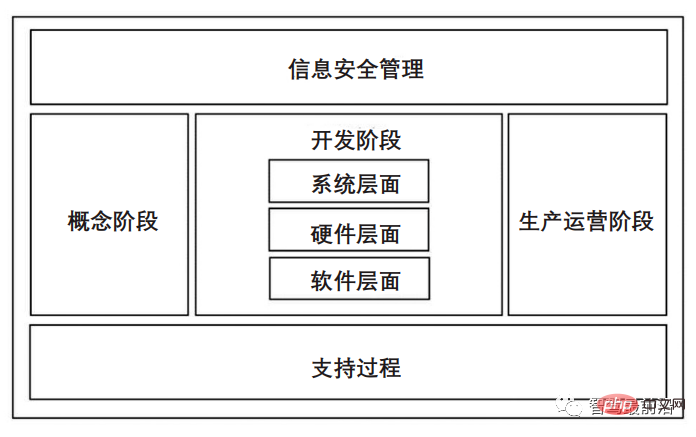
Figure 1 Vehicle information security architecture diagram
Vehicle information security architecture It is mainly composed of three parts: information security management, core information security engineering activities and support processes. Information security management includes comprehensive management and information security management at each stage of the life cycle. Core information security engineering activities include the concept stage, the development stage of the vehicle system, software and hardware levels, and the production and operation stage. Develop the entire security project plan during the conceptual phase, including identification of network security boundaries, system external dependencies, analysis and assessment of potential threats to the system. During the development phase, risk analysis is conducted on the vulnerabilities and threats of the vehicle system, and information security requirements and strategies are formulated. After the development phase is completed, penetration testing is performed to complete the final security audit. The production and operation stage mainly conducts on-site monitoring, incident response and subsequent time tracking management of products. The support process stage mainly provides auxiliary support to the above stages, including corresponding configuration management, document management and supply chain management.
The vehicle information security development framework is shown in Figure 2. The system development and design stage is the basis for vehicle information security implementation, and vehicle information security system design is dependent on automotive electronics/electrical architecture (E/E) system design. Therefore, automotive network information security vulnerabilities should be investigated, including connections to the external environment (such as cloud servers, other vehicles and infrastructure), connections to the in-vehicle network, connections to the ECU level and connections to individual components, etc., to build a security level A higher E/E system improves security from the system level. During the testing phase, the vehicle information security function is inspected and tested, a security assessment is conducted, and the security of the vehicle information security architecture is verified. In the overall vehicle information security development process, hardware design and software design should be coordinated and developed, taking into account the safety and reliability of software and hardware to jointly achieve network security.
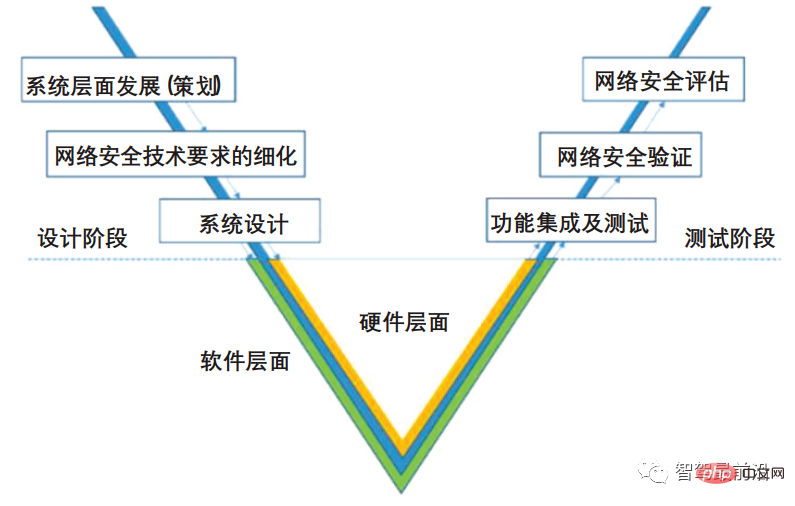
Figure 2 Vehicle information security development framework diagram
Etes Take a car as an example to analyze the car E/E architecture solution. Tesla Motors is the leader in automotive E/E architecture changes. The electronic and electrical architecture of Model 3 is divided into three parts: central computing module (CCM), left body control module (BCM_LH) and right body control module (BCM_RH). CCM directly integrates the two functional domains of driver assistance system (ADAS) and infotainment system (IVI), and also includes the functions of external communication and in-car system domain communication; BCM_LH and BCM_RH are respectively responsible for the body and convenience systems, chassis and safety systems and Some power system functions. The three major modules all use high-performance processors, which can meet a large number of computing needs in the functional domain. The remaining ECUs in the domain only control automotive peripherals. Each system in the domain communicates through the LAN, and the modules communicate through the bus, achieving basic security. isolation.
The emergence of centralized electronic and electrical architecture in the automotive domain provides a solution to the problems of information security and insufficient computing power. The centralized electronic and electrical architecture of the automotive domain refers to dividing the car into several functional blocks based on functions. Each functional block is built with a domain controller as the leader. Different types of internal communications in each functional domain can be used according to the communication rate requirements of different functions. Communication bus, such as CAN, LIN, FLEXRAY, MOST and other buses, the communication between each functional domain realizes information exchange through Ethernet with higher transmission rate. The domain centralized electronic and electrical architecture diagram is shown in Figure 3. The domain controller is mainly responsible for delivering communication between the domain and the cloud, between the domain and the domain, and within the domain. The ECU in the domain is only responsible for executing the operating instructions of the device accordingly, and a controller with communication functions can be used.
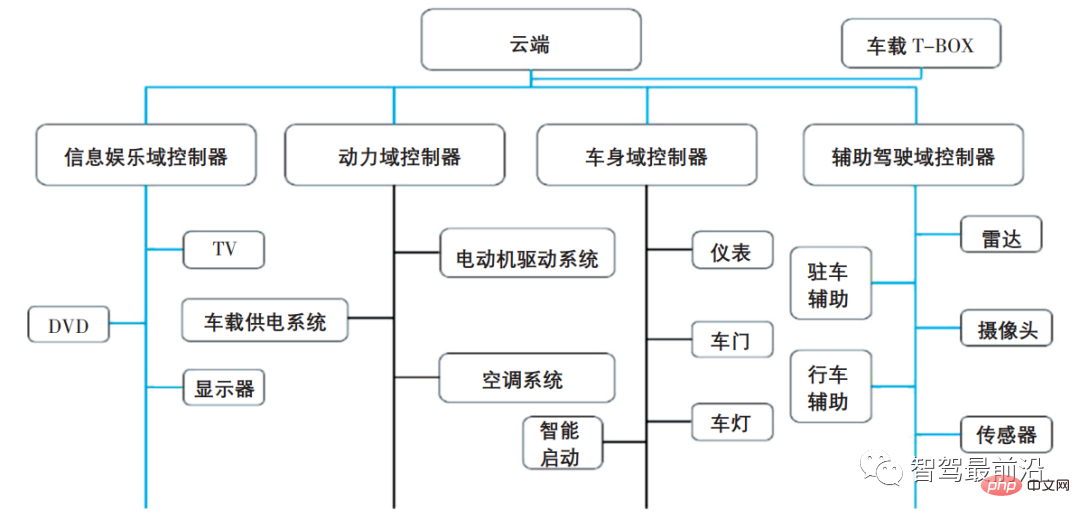
Figure 3 Domain centralized electronic and electrical architecture diagram
According to our country According to national conditions, the centralized electronic and electrical architecture of the intelligent connected vehicle domain combines the three major applications of intelligence, connectivity, and electrification.
Compared with the previous automotive distributed electronic and electrical architecture, in view of the lack of computing power, the domain controller serves as an independent controller for each domain, and it needs to match a core computing power internally. Powerful processors to meet the computing power requirements of intelligent connected cars. Currently, there are solutions from NVIDIA, Huawei, Renesas, NXP, TI, Mobileye, Xilinx, Horizon and other brands in the industry. In terms of security protection, the domain centralized architecture divides the vehicle into several independent functional modules based on functions and communication rate requirements. If an attacker wants to attack the entire vehicle through a certain function, the domain controller where the function is located can monitor it in time. It also eliminates hidden dangers without affecting other functional areas, effectively reducing the possibility of expanding the attack surface.
2 Analysis of information security threats faced by intelligent connected cars
With the great expansion of vehicle connectivity functions, navigation, positioning, automatic Functions such as parking, remote control and diagnosis have gradually become standard features in cars. While these functions bring great convenience to people, they also bring more security risks.
According to the different ways of being attacked, the security risks of intelligent connected cars can be divided into the following four aspects from far to near:
(1) Cloud layer security risks
The cloud platform stores key information about cars and can provide cars with traffic information, positioning and navigation, alarms, remote control, etc. If the cloud platform is attacked by hackers and a large amount of important data is leaked, the consequences will be disastrous.
(2) Network transport layer security risks
Intelligent networked cars realize communication with the cloud through wireless communication Information interaction between platforms, mobile APPs, other vehicles, traffic conditions and other data, and wireless communication methods may have security issues such as identity authentication, data information encryption, and protocols, so cars also have corresponding security risks.
(3) Potential security risks of vehicle communication layer
With the increase of vehicle external interfaces, the vehicle internal communication process Potential security risks in the firmware of electronic control units and security risks in the data transmission process have also increased.
(4) External interface security risks
There are many third-party APPs on the market, and there are many types of APPs. Its safety protection is also an important part of eliminating hidden dangers. If a hacker hacks into the APP, he or she can even directly control the car remotely. In addition, there are also security risks in the communication interface between the charging gun and the charging pile of electric vehicles. Once attacked, the energy system of the electric vehicle will be destroyed, which may bring life-threatening consequences.
3 Analysis of vehicle information security risks
(1) Vehicle-mounted intelligent terminal (vehicle T-BOX) attack
Vehicle-mounted T-BOX is mainly used for communication between vehicles and the Internet of Vehicles service platform, with functions such as vehicle remote control, remote query, and alarm. Under normal circumstances, the vehicle T-BOX reads the vehicle's internal CAN communication data information and transmits the information to the cloud platform or APP through wireless communication. The security risks of vehicle-mounted T-BOX mainly include three aspects: First, firmware reversal, in which attackers analyze the vehicle-mounted T-BOX firmware through reverse engineering, obtain keys, and decrypt communication protocols; second, read through the reserved debugging interface of vehicle-mounted T-BOX. Get the internal data and analyze it, and decrypt the communication protocol; third, by counterfeiting the control instructions of the cloud platform, send the instructions to the interior of the car to achieve remote control of the car.
(2) In-vehicle infotainment system (IVI) attack
In-vehicle infotainment system is used for navigation and road conditions Applications in broadcasting, vehicle information, communications, assisted driving, CD/radio, etc. Due to the rich functions of the vehicle infotainment system, attackers can attack through USB, Bluetooth, Wi-Fi and other communication methods, or gain access through software upgrades to attack the system.
(3) Diagnostic interface OBD-Ⅱ attack
Automobile diagnostic interface OBD-Ⅱ is the connection between the automotive ECU and the external The main function of the interactive interface is to read vehicle data information and fault codes for vehicle maintenance. Once the OBD-II interface is attacked, not only can the internal communication protocol of the car be cracked through this interface, but also the vehicle can be controlled by implanting malicious hardware to send control instructions.
(4) Sensor attack
#Intelligent networked cars have a large number of sensor devices for vehicle-to-vehicle , communication between cars and people, cars and roads, and cars and clouds. If the sensors are attacked by malicious information injection, eavesdropping, etc., highly automated vehicles may not be able to correctly judge the behavior of the surrounding environment, causing serious consequences.
(5) In-car network transmission attack
Most car internal network communications use CAN bus transmission, CAN bus It has the characteristics of low cost, moderate communication rate, and strong anti-electromagnetic interference ability, so it is widely used in automotive electronic control systems. However, the CAN bus adopts a non-destructive bus arbitration method, which has the characteristics of simple verification, one-send multiple reads, etc., and the security protection measures are weak. If an attacker attacks through message replay, denial of service, tampering, etc. through the CAN bus, the CAN bus will be attacked. The result is that the driver's control instructions fail and the car cannot drive normally.
4 Automobile communication security solution
In terms of intelligent network-connected vehicle information security protection, active protection, intrusion monitoring, System security protection measures for emergency handling ensure the information security of the car. Before an attack occurs, take active protection, screen and filter the vehicle's communication data, and effectively prevent common attack methods. After an attack occurs, changes in the vehicle communication status are continuously monitored, emergency measures are taken promptly against the attack point and updated in a timely manner to prevent danger from occurring.
Based on the current analysis of the applicability model of automotive information security technology, combined with the new automotive domain centralized electronic and electrical architecture, a vehicle-mounted multi-domain hierarchical intrusion detection model is constructed to target the cloud layer, The domain controller layer, ECU layer, and in-vehicle network transmission layer perform layered intrusion detection and take corresponding active protection measures to achieve precise protection. The schematic diagram of multi-domain hierarchical intrusion detection is shown in Figure 4.
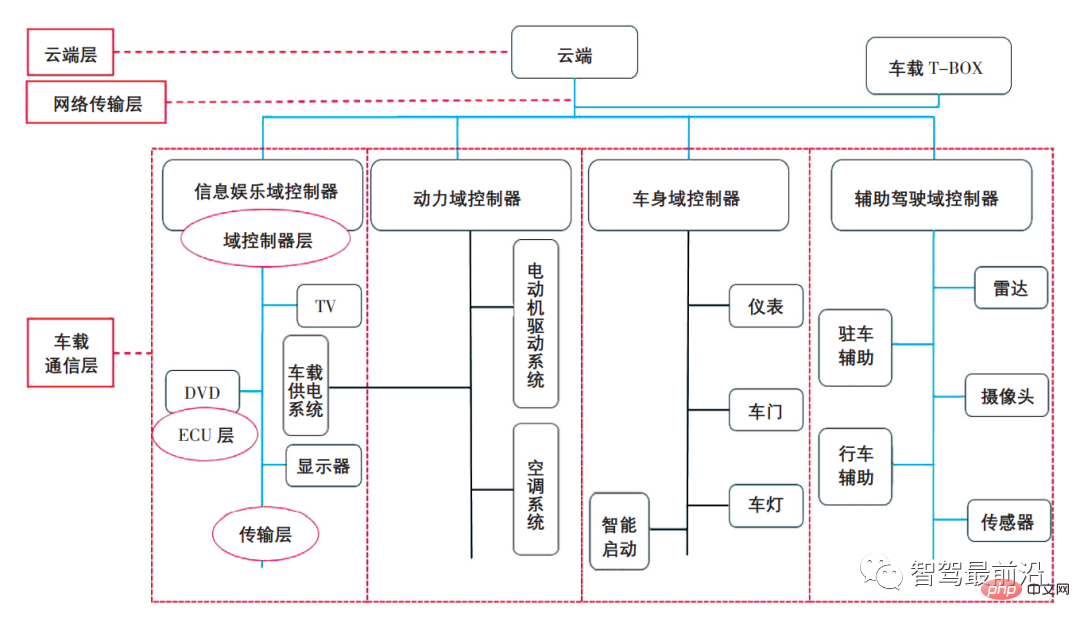
##Figure 4 Schematic diagram of multi-domain hierarchical intrusion detection
(1) Domain controller layer
In the new architecture solution, the domain controller is not only the computing integration platform for the entire domain, but also the communication between domains and between domains and the cloud. Gateway for information exchange. As the security boundary for network information interaction inside and outside the car, the domain controller is the focus of the security protection of the car's on-board network. Therefore, a security firewall should be established at the security boundary to perform security detection, access restrictions, logging and other security detection on data information to achieve security protection.
The communication message of the car consists of ID, data information, check digit and other parts. The ID determines the transmission priority and destination address of the message, the data information determines the operation instructions, and the check bit ensures that the transmitted data information is complete.
The main function of the security firewall is to implement the access control function. The framework diagram of the automotive security firewall is shown in Figure 5.
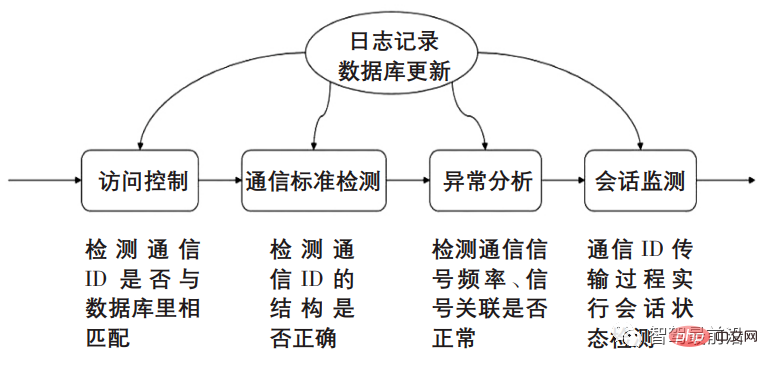
Figure 5 Security Firewall Framework Diagram
Firewall access control function The implementation is mainly based on establishing a whitelist database of automotive communication messages. Once a message request is detected, the message ID is compared with the whitelist database. If the match is successful, it will be passed, and if it fails, it will be discarded.
There are many firewall anomaly detection technologies. Common detection technologies include intrusion anomaly detection methods, based on neural networks, clustering, genetic algorithms, information entropy, association rules, etc. The intrusion anomaly detection method mainly builds a vehicle communication network security model by analyzing the communication data of a large number of normal driving cars, and uses the model to monitor the behavior of users and systems, analyze whether there are abnormal illegal data activities, and alert users and record them. Automobile messages are divided into periodic messages and event-triggered messages. Intrusion anomaly detection technology can build models according to different situations.
Periodic messages build an intrusion detection model by setting the message period threshold, and compare the message period with the threshold for judgment; event-triggered messages do not have a fixed sending period, but most The operation instructions of the message are related to each other. For example, there is a negative correlation between the car's speed signal and the brake signal, and there is a positive correlation between the accelerator pedal signal and the car signal. Therefore, a large amount of data analysis is used to construct a communication packet positive/negative correlation intrusion detection model. Once there is a large deviation in the packet correlation, it will be determined as an intrusion and an alarm will be issued.
Since the computing power of automobile on-board chips is not enough to maximize security and real-time performance at the same time, the intrusion detection method currently used needs to be based on ensuring real-time performance. To effectively detect intrusions, monitoring vehicle message traffic is currently the most effective method. The intrusion detection process of access control, communication standard detection, and anomaly analysis in the security firewall is shown in 6.
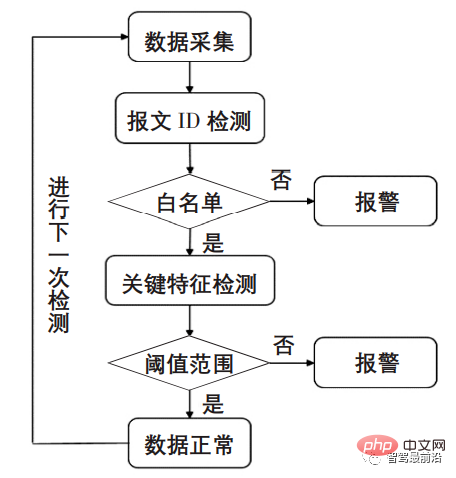
Figure 6 Intrusion detection process
(2) In-vehicle network layer
Network transmission security within each domain is the second line of defense for the security protection mechanism. Depending on the communication requirements required by the functional domain, the vehicle transmission network used is also different. Currently, except for infotainment systems, most systems use CAN bus communication. The broadcast characteristics and non-destructive bus arbitration methods of the CAN bus lead to weak security protection, so a communication security protocol needs to be developed.
The design of the communication security protocol mainly consists of two parts: verification of the ECU node and encryption of the transmitted data information. Before the car drives, the domain controller randomly assigns the identity of each ECU. The ECU sends an authentication request to the domain controller for identity authentication to ensure the legitimacy of the node and complete the verification of the ECU node. While the car is driving, the communication information on the vehicle network needs to be encrypted to prevent attackers from eavesdropping and masquerading. Combined with the high real-time requirements of automobiles, data encryption uses the AES symmetric encryption algorithm. The ECU identity authentication process is shown in Figure 7, and the CAN communication encrypted message format is shown in Figure 8.
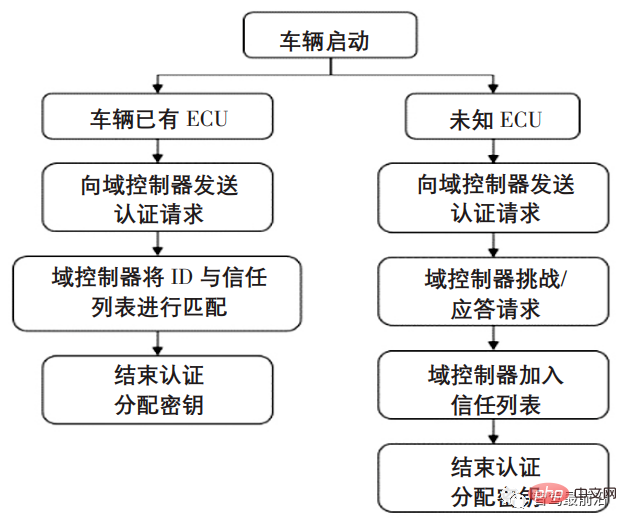
Figure 7 ECU identity authentication process
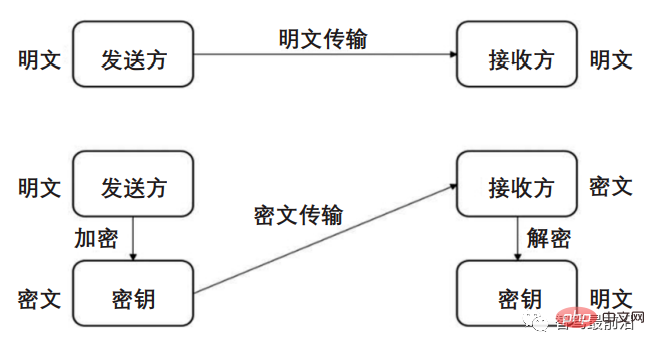
Figure 8 CAN communication encrypted message format
Symmetric encryption has a small amount of calculation and fast speed, and is suitable for automotive big data communication. In the symmetric encryption algorithm, both the encrypting party and the decrypting party must know the encryption key in advance, and both the sending and receiving parties use the key to encrypt and decrypt the data. Based on the security and real-time requirements of car data, an independent encryption table can be established as a key to encrypt the data based on the successfully verified ECU ID and the data sending ECU and receiving ECU, and based on the real-time requirements of the car. Verify and adjust the encryption difficulty of the encryption table accordingly to maximize data security.
(3) ECU layer
The security protection at the ECU level is mainly firmware protection to prevent firmware flashing , external access, malicious changes and other functions. Considering the cost issue, different levels of security protection measures need to be allocated to ECUs with different functions. A hardware security module is a computer hardware device used to protect and manage keys used in strong authentication systems and provide related cryptographic operations. The body domain ECU uses lightweight hardware security modules. The power domain ECU, infotainment domain ECU, and auxiliary driving domains all use medium-weight hardware security modules. The body domain controller, power domain controller, infotainment domain controller, and auxiliary driving domain all use medium-weight hardware security modules. Driving domain controllers all use heavyweight hardware security modules.
5 Conclusion
This article starts from the development of intelligent connected cars and focuses on the information of intelligent connected cars To address the issue of security risks, the protection of automotive network information security was analyzed, a centralized electronic and electrical architecture for the automotive domain was established, and a preliminary feasibility plan for a complete information security protection model from protection to intrusion detection, from data encryption to hardware encryption was proposed. architecture, the solution still needs to be further demonstrated through examples in the future.
The above is the detailed content of This article takes you through the communication security architecture of smart car in-vehicle networks. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1386
1386
 52
52
 Why is Gaussian Splatting so popular in autonomous driving that NeRF is starting to be abandoned?
Jan 17, 2024 pm 02:57 PM
Why is Gaussian Splatting so popular in autonomous driving that NeRF is starting to be abandoned?
Jan 17, 2024 pm 02:57 PM
Written above & the author’s personal understanding Three-dimensional Gaussiansplatting (3DGS) is a transformative technology that has emerged in the fields of explicit radiation fields and computer graphics in recent years. This innovative method is characterized by the use of millions of 3D Gaussians, which is very different from the neural radiation field (NeRF) method, which mainly uses an implicit coordinate-based model to map spatial coordinates to pixel values. With its explicit scene representation and differentiable rendering algorithms, 3DGS not only guarantees real-time rendering capabilities, but also introduces an unprecedented level of control and scene editing. This positions 3DGS as a potential game-changer for next-generation 3D reconstruction and representation. To this end, we provide a systematic overview of the latest developments and concerns in the field of 3DGS for the first time.
 How to solve the long tail problem in autonomous driving scenarios?
Jun 02, 2024 pm 02:44 PM
How to solve the long tail problem in autonomous driving scenarios?
Jun 02, 2024 pm 02:44 PM
Yesterday during the interview, I was asked whether I had done any long-tail related questions, so I thought I would give a brief summary. The long-tail problem of autonomous driving refers to edge cases in autonomous vehicles, that is, possible scenarios with a low probability of occurrence. The perceived long-tail problem is one of the main reasons currently limiting the operational design domain of single-vehicle intelligent autonomous vehicles. The underlying architecture and most technical issues of autonomous driving have been solved, and the remaining 5% of long-tail problems have gradually become the key to restricting the development of autonomous driving. These problems include a variety of fragmented scenarios, extreme situations, and unpredictable human behavior. The "long tail" of edge scenarios in autonomous driving refers to edge cases in autonomous vehicles (AVs). Edge cases are possible scenarios with a low probability of occurrence. these rare events
 Choose camera or lidar? A recent review on achieving robust 3D object detection
Jan 26, 2024 am 11:18 AM
Choose camera or lidar? A recent review on achieving robust 3D object detection
Jan 26, 2024 am 11:18 AM
0.Written in front&& Personal understanding that autonomous driving systems rely on advanced perception, decision-making and control technologies, by using various sensors (such as cameras, lidar, radar, etc.) to perceive the surrounding environment, and using algorithms and models for real-time analysis and decision-making. This enables vehicles to recognize road signs, detect and track other vehicles, predict pedestrian behavior, etc., thereby safely operating and adapting to complex traffic environments. This technology is currently attracting widespread attention and is considered an important development area in the future of transportation. one. But what makes autonomous driving difficult is figuring out how to make the car understand what's going on around it. This requires that the three-dimensional object detection algorithm in the autonomous driving system can accurately perceive and describe objects in the surrounding environment, including their locations,
 This article is enough for you to read about autonomous driving and trajectory prediction!
Feb 28, 2024 pm 07:20 PM
This article is enough for you to read about autonomous driving and trajectory prediction!
Feb 28, 2024 pm 07:20 PM
Trajectory prediction plays an important role in autonomous driving. Autonomous driving trajectory prediction refers to predicting the future driving trajectory of the vehicle by analyzing various data during the vehicle's driving process. As the core module of autonomous driving, the quality of trajectory prediction is crucial to downstream planning control. The trajectory prediction task has a rich technology stack and requires familiarity with autonomous driving dynamic/static perception, high-precision maps, lane lines, neural network architecture (CNN&GNN&Transformer) skills, etc. It is very difficult to get started! Many fans hope to get started with trajectory prediction as soon as possible and avoid pitfalls. Today I will take stock of some common problems and introductory learning methods for trajectory prediction! Introductory related knowledge 1. Are the preview papers in order? A: Look at the survey first, p
 SIMPL: A simple and efficient multi-agent motion prediction benchmark for autonomous driving
Feb 20, 2024 am 11:48 AM
SIMPL: A simple and efficient multi-agent motion prediction benchmark for autonomous driving
Feb 20, 2024 am 11:48 AM
Original title: SIMPL: ASimpleandEfficientMulti-agentMotionPredictionBaselineforAutonomousDriving Paper link: https://arxiv.org/pdf/2402.02519.pdf Code link: https://github.com/HKUST-Aerial-Robotics/SIMPL Author unit: Hong Kong University of Science and Technology DJI Paper idea: This paper proposes a simple and efficient motion prediction baseline (SIMPL) for autonomous vehicles. Compared with traditional agent-cent
 Let's talk about end-to-end and next-generation autonomous driving systems, as well as some misunderstandings about end-to-end autonomous driving?
Apr 15, 2024 pm 04:13 PM
Let's talk about end-to-end and next-generation autonomous driving systems, as well as some misunderstandings about end-to-end autonomous driving?
Apr 15, 2024 pm 04:13 PM
In the past month, due to some well-known reasons, I have had very intensive exchanges with various teachers and classmates in the industry. An inevitable topic in the exchange is naturally end-to-end and the popular Tesla FSDV12. I would like to take this opportunity to sort out some of my thoughts and opinions at this moment for your reference and discussion. How to define an end-to-end autonomous driving system, and what problems should be expected to be solved end-to-end? According to the most traditional definition, an end-to-end system refers to a system that inputs raw information from sensors and directly outputs variables of concern to the task. For example, in image recognition, CNN can be called end-to-end compared to the traditional feature extractor + classifier method. In autonomous driving tasks, input data from various sensors (camera/LiDAR
 nuScenes' latest SOTA | SparseAD: Sparse query helps efficient end-to-end autonomous driving!
Apr 17, 2024 pm 06:22 PM
nuScenes' latest SOTA | SparseAD: Sparse query helps efficient end-to-end autonomous driving!
Apr 17, 2024 pm 06:22 PM
Written in front & starting point The end-to-end paradigm uses a unified framework to achieve multi-tasking in autonomous driving systems. Despite the simplicity and clarity of this paradigm, the performance of end-to-end autonomous driving methods on subtasks still lags far behind single-task methods. At the same time, the dense bird's-eye view (BEV) features widely used in previous end-to-end methods make it difficult to scale to more modalities or tasks. A sparse search-centric end-to-end autonomous driving paradigm (SparseAD) is proposed here, in which sparse search fully represents the entire driving scenario, including space, time, and tasks, without any dense BEV representation. Specifically, a unified sparse architecture is designed for task awareness including detection, tracking, and online mapping. In addition, heavy
 FisheyeDetNet: the first target detection algorithm based on fisheye camera
Apr 26, 2024 am 11:37 AM
FisheyeDetNet: the first target detection algorithm based on fisheye camera
Apr 26, 2024 am 11:37 AM
Target detection is a relatively mature problem in autonomous driving systems, among which pedestrian detection is one of the earliest algorithms to be deployed. Very comprehensive research has been carried out in most papers. However, distance perception using fisheye cameras for surround view is relatively less studied. Due to large radial distortion, standard bounding box representation is difficult to implement in fisheye cameras. To alleviate the above description, we explore extended bounding box, ellipse, and general polygon designs into polar/angular representations and define an instance segmentation mIOU metric to analyze these representations. The proposed model fisheyeDetNet with polygonal shape outperforms other models and simultaneously achieves 49.5% mAP on the Valeo fisheye camera dataset for autonomous driving



