 Technology peripherals
Technology peripherals
 AI
AI
 Musk open sourced Twitter recommendation algorithm, GitHub reached 10,000 stars in seconds, and promised to evolve every 24-48 hours
Musk open sourced Twitter recommendation algorithm, GitHub reached 10,000 stars in seconds, and promised to evolve every 24-48 hours
Musk open sourced Twitter recommendation algorithm, GitHub reached 10,000 stars in seconds, and promised to evolve every 24-48 hours
Musk’s “open source commitment” finally came true.
Just now, Musk officially announced:
Most (Twitter’s) recommendation algorithms will be open source today, and the rest will follow.
#And Musk immediately showed the address of the source code of the Twitter recommendation algorithm on GitHub.
In just a few hours, tens of thousands of Stars were obtained:
In addition, Musk also said:
Push The recommendation algorithm based on user suggestions will be updated every 24 to 48 hours.
#At this point, the true face of this big algorithm that claims to make recommendations from 500 million tweets every day has finally been revealed.
What does Twitter’s recommendation algorithm look like?
According to reports, Twitter’s recommendation system is based on a set of core models and functions that can extract potential information from tweets, users and interaction data.
The role of these models is to answer important questions in the Twitter network, such as, "What is the probability that you will interact with another user in the future?" or, "What communities are there on Twitter and the trending tweets in them are What?"
If you can answer these questions accurately, you can let Twitter provide more relevant recommendations.
Twitter’s recommendation system consists of three parts:
- Get the best tweets from different recommendation sources. This process is called candidate sources.
- Use a machine learning model to rank each tweet.
- Apply heuristics and filters, such as filtering tweets from blocked users, NSFW content, and seen tweets.
The service responsible for building and delivering the "For You" timeline is called "Home Mixer".
"Home Mixer" is built on top of "Product Mixer", a custom Scala framework that helps build dynamic flows of content.
This service serves as the software backbone, connecting different candidate sources, scoring functions, heuristics and filters.
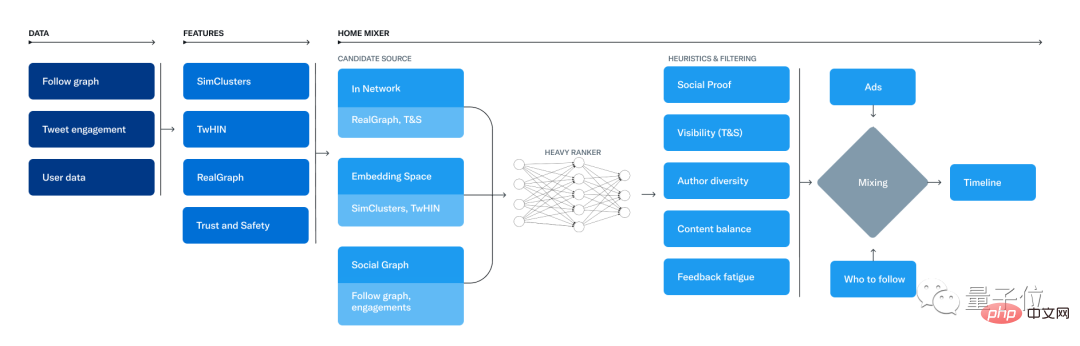
Candidate Sources
Twitter uses multiple candidate sources to retrieve recent and relevant tweets for users.
For each request, Twitter attempts to extract the best 1,500 tweets from a pool of hundreds of millions of tweets from these sources.
Find candidates from people you follow (internal network) and people you don’t follow (external network).
Today, the "Recommended for You" timeline is made up of an average of 50% internal network tweets and 50% external network tweets (although this can vary by user).
In-Network Source
In-Network Source is the largest candidate source and aims to provide the most relevant and latest tweets to the users who follow it.
It uses a logistic regression model to efficiently rank tweets from people you follow, based on their relevance. The top ranked tweets are then sent to the next stage.
The most important component of ranking internal network tweets is the Real Graph.
Real Graph is a model used to predict the likelihood of interaction between two users. The higher the Real Graph score between the user and the tweet author, the more of their tweets will be included.
Internal network sources have recently become the subject of research by Twitter. Twitter recently stopped using the Fanout service, a 12-year-old service it used to serve internal network tweets from each user's tweet cache.
Out-of-Network Sources
Finding relevant tweets outside a user’s network is a tricky problem.
Because if you don’t follow the author, how do you know if a tweet is relevant to you?
To this end, Twitter has taken two approaches to solve this problem.
One is the Social Graph.
This method is to estimate what you will find relevant by analyzing the activities of people you follow or have similar interests.
Mainly traverse the participating graph and follow the steps below to answer the following questions:
- What messages have the people I follow recently posted on Twitter?
- Who likes similar tweets like me and what else have they liked recently?
The team generated candidate tweets based on the answers to these questions and used a logit model to rank the resulting tweets.
This type of graph traversal is essential for external network recommendations; the team developed GraphJet, a graph processing engine that maintains a real-time interaction graph between users and tweets, to perform these traversals.
While this heuristic for searching Twitter engagement and attention networks has proven useful, the embedded spatial approach has become a greater source of tweets from external networks.
The second one is Embedding Spaces.
The embedded spatial approach aims to answer a more general question about content similarity - what tweets and users share my interests?
Embeddings work by generating digital representations of user interests and tweet content. The similarity between any two users, tweets or user-tweet pairs in this embedding space can then be calculated.
This similarity can be used as a surrogate for correlation as long as accurate embedding is generated.
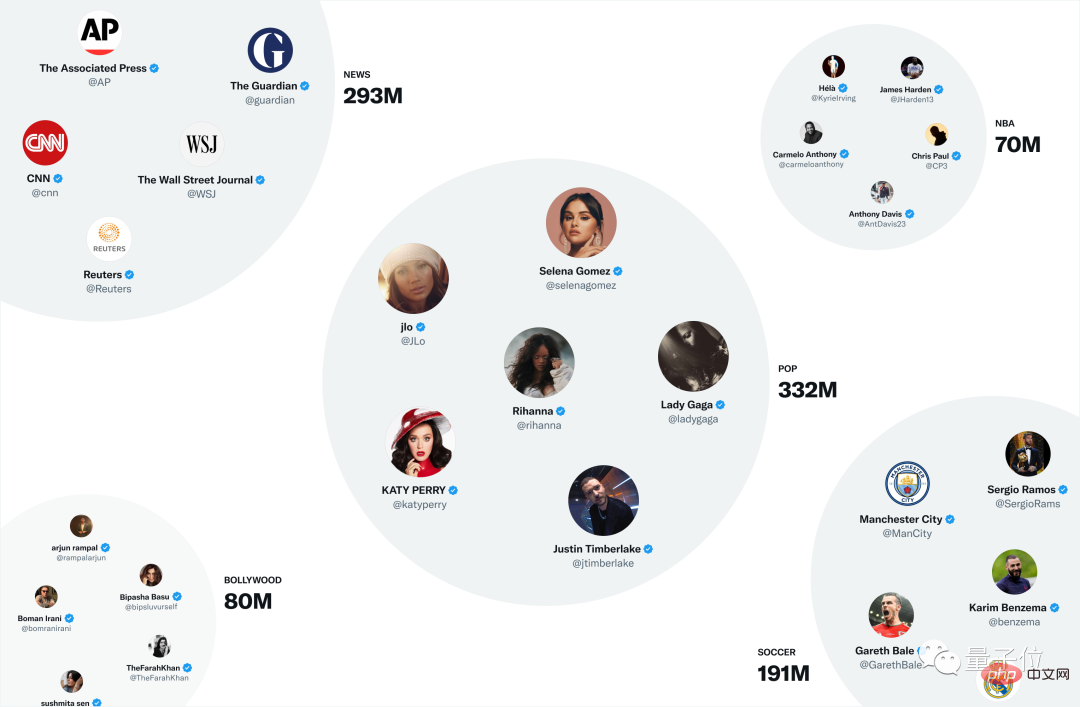
One of Twitter’s most useful embedding spaces is SimClusters.
SimClusters uses a custom matrix factorization algorithm to discover communities anchored by a group of influential users (145,000 communities, updated every three weeks).
Users and tweets are represented in community spaces and can belong to multiple communities. Communities range in size from a few thousand users in a personal friend group to hundreds of millions in news or pop culture:
…
More with For related details, please click on the link at the end of the article~
One More Thing
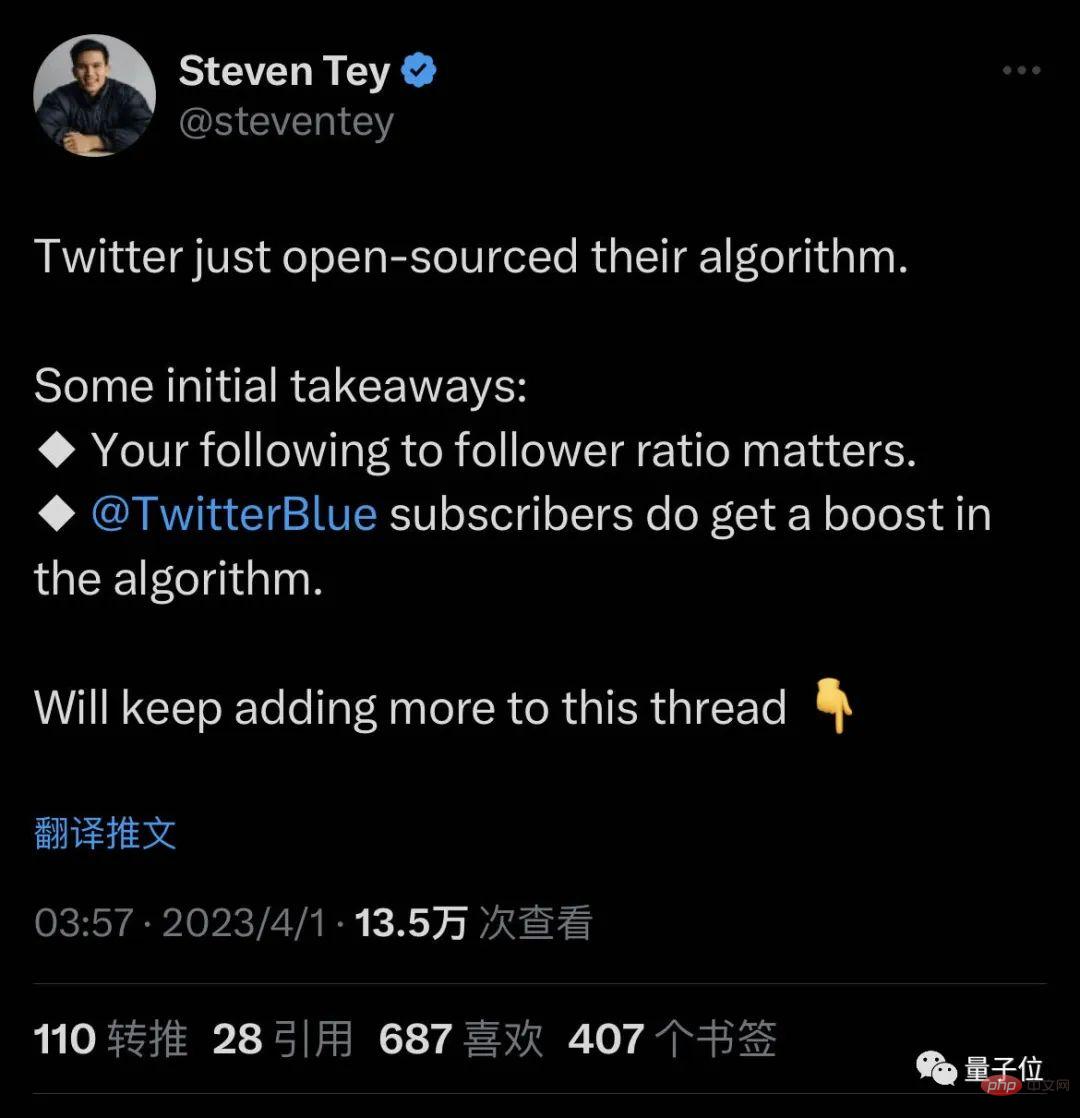
Twitter’s algorithm is open source, and quick netizens...have begun to summarize how to become a big V based on the algorithm :
The ratio of the number of people you follow to the number of people following you is very important. Subscribing to TwitterBlue plays a certain role...
Reference link:
[1]https://www.php.cn/link/ce2b9a26bddc32cba5af69372ee14c00
[2]https://www.php.cn /link/e55bc0255c752d1cb05da10c0f1f5026
[3]https://www.php.cn/link/10fe8dc69a0964edc16fed1a1bd55716
[4]https://www.php.cn/link/51f4efbfb3e18f4ea053c4d3d282c4e2
The above is the detailed content of Musk open sourced Twitter recommendation algorithm, GitHub reached 10,000 stars in seconds, and promised to evolve every 24-48 hours. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1378
1378
 52
52
 Implementing Machine Learning Algorithms in C++: Common Challenges and Solutions
Jun 03, 2024 pm 01:25 PM
Implementing Machine Learning Algorithms in C++: Common Challenges and Solutions
Jun 03, 2024 pm 01:25 PM
Common challenges faced by machine learning algorithms in C++ include memory management, multi-threading, performance optimization, and maintainability. Solutions include using smart pointers, modern threading libraries, SIMD instructions and third-party libraries, as well as following coding style guidelines and using automation tools. Practical cases show how to use the Eigen library to implement linear regression algorithms, effectively manage memory and use high-performance matrix operations.
 What are the blockchain data analysis tools?
Feb 21, 2025 pm 10:24 PM
What are the blockchain data analysis tools?
Feb 21, 2025 pm 10:24 PM
The rapid development of blockchain technology has brought about the need for reliable and efficient analytical tools. These tools are essential to extract valuable insights from blockchain transactions in order to better understand and capitalize on their potential. This article will explore some of the leading blockchain data analysis tools on the market, including their capabilities, advantages and limitations. By understanding these tools, users can gain the necessary insights to maximize the possibilities of blockchain technology.
 Explore the underlying principles and algorithm selection of the C++sort function
Apr 02, 2024 pm 05:36 PM
Explore the underlying principles and algorithm selection of the C++sort function
Apr 02, 2024 pm 05:36 PM
The bottom layer of the C++sort function uses merge sort, its complexity is O(nlogn), and provides different sorting algorithm choices, including quick sort, heap sort and stable sort.
 Huangquan Light Cone Recommendation
Mar 27, 2024 pm 05:31 PM
Huangquan Light Cone Recommendation
Mar 27, 2024 pm 05:31 PM
Huang Quan's light cone can effectively increase the character's critical hit damage and attack power in battle. The light cones recommended by Huang Quan are: Walking on the Passing Shore, Good Night and Sleeping Face, Rain Keeps Falling, Just Wait, and Determination Like Beads of Sweat. Shine, below the editor will bring you recommendations for the Underworld Light Cone of the Collapsed Star Dome Railway. Huangquan Light Cone Recommendation 1. Walking on the Passing Bank 1. Huangquan's special weapon can increase the explosive damage. Attacking the enemy can put the enemy into a bubble negative state, which increases the damage caused. The damage of the finishing move is additionally increased. There are both negative states and The damage is increased, it has to be said that it is a special weapon. 2. The exclusive light cone is very unique among many ethereal light cones. It directly increases direct damage, has high damage and improves the critical damage attribute. 3. Not only that, the light cone also provides a negative status effect, which can cause Huangquan itself to react.
 Improved detection algorithm: for target detection in high-resolution optical remote sensing images
Jun 06, 2024 pm 12:33 PM
Improved detection algorithm: for target detection in high-resolution optical remote sensing images
Jun 06, 2024 pm 12:33 PM
01 Outlook Summary Currently, it is difficult to achieve an appropriate balance between detection efficiency and detection results. We have developed an enhanced YOLOv5 algorithm for target detection in high-resolution optical remote sensing images, using multi-layer feature pyramids, multi-detection head strategies and hybrid attention modules to improve the effect of the target detection network in optical remote sensing images. According to the SIMD data set, the mAP of the new algorithm is 2.2% better than YOLOv5 and 8.48% better than YOLOX, achieving a better balance between detection results and speed. 02 Background & Motivation With the rapid development of remote sensing technology, high-resolution optical remote sensing images have been used to describe many objects on the earth’s surface, including aircraft, cars, buildings, etc. Object detection in the interpretation of remote sensing images
 Application of algorithms in the construction of 58 portrait platform
May 09, 2024 am 09:01 AM
Application of algorithms in the construction of 58 portrait platform
May 09, 2024 am 09:01 AM
1. Background of the Construction of 58 Portraits Platform First of all, I would like to share with you the background of the construction of the 58 Portrait Platform. 1. The traditional thinking of the traditional profiling platform is no longer enough. Building a user profiling platform relies on data warehouse modeling capabilities to integrate data from multiple business lines to build accurate user portraits; it also requires data mining to understand user behavior, interests and needs, and provide algorithms. side capabilities; finally, it also needs to have data platform capabilities to efficiently store, query and share user profile data and provide profile services. The main difference between a self-built business profiling platform and a middle-office profiling platform is that the self-built profiling platform serves a single business line and can be customized on demand; the mid-office platform serves multiple business lines, has complex modeling, and provides more general capabilities. 2.58 User portraits of the background of Zhongtai portrait construction
 News recommendation algorithm based on global graph enhancement
Apr 08, 2024 pm 09:16 PM
News recommendation algorithm based on global graph enhancement
Apr 08, 2024 pm 09:16 PM
Author | Reviewed by Wang Hao | Chonglou News App is an important way for people to obtain information sources in their daily lives. Around 2010, popular foreign news apps included Zite and Flipboard, while popular domestic news apps were mainly the four major portals. With the popularity of new era news recommendation products represented by Toutiao, news apps have entered a new era. As for technology companies, no matter which one they are, as long as they master the sophisticated news recommendation algorithm technology, they will basically have the initiative and voice at the technical level. Today, let’s take a look at a RecSys2023 Best Long Paper Nomination Award paper—GoingBeyondLocal:GlobalGraph-EnhancedP
 Groundbreaking CVM algorithm solves more than 40 years of counting problems! Computer scientist flips coin to figure out unique word for 'Hamlet'
Jun 07, 2024 pm 03:44 PM
Groundbreaking CVM algorithm solves more than 40 years of counting problems! Computer scientist flips coin to figure out unique word for 'Hamlet'
Jun 07, 2024 pm 03:44 PM
Counting sounds simple, but in practice it is very difficult. Imagine you are transported to a pristine rainforest to conduct a wildlife census. Whenever you see an animal, take a photo. Digital cameras only record the total number of animals tracked, but you are interested in the number of unique animals, but there is no statistics. So what's the best way to access this unique animal population? At this point, you must be saying, start counting now and finally compare each new species from the photo to the list. However, this common counting method is sometimes not suitable for information amounts up to billions of entries. Computer scientists from the Indian Statistical Institute, UNL, and the National University of Singapore have proposed a new algorithm - CVM. It can approximate the calculation of different items in a long list.



