Can you recognize fake photos created by AI?
The era of seeing is believing has passed, and AI has learned to create reality.
On August 21, there was a mountain fire in Jinyun Mountain, Beibei, Chongqing. The fire once spread to the villages and towns at the foot of the mountain. The mountain road is steep and sandy, but the motorcycle is nimble enough. The motorcyclists who carried supplies up the mountain bit by bit became the protagonists of this wildfire rescue, and also became the focus of people's attention on social media.
At the same time, netizens pointed out on social media that "8 out of 10 pictures of the Chongqing wildfires were painted by AI, but the comments below were so moved that they cried."
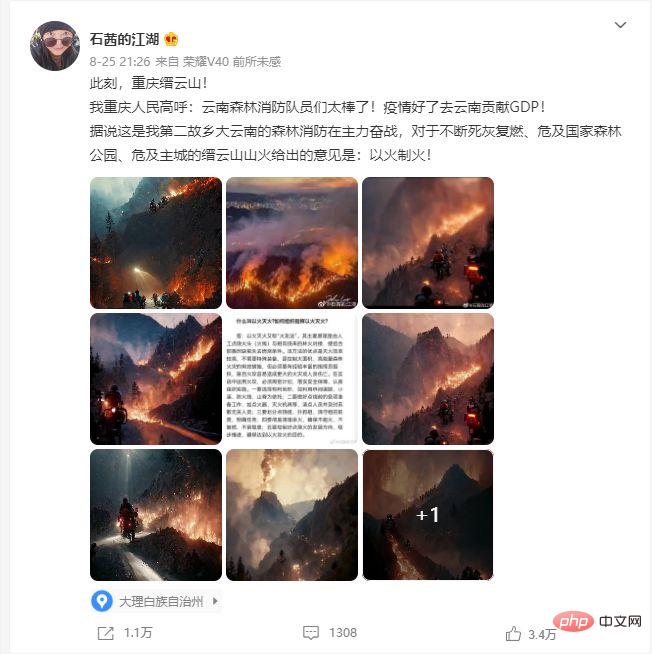
#In fact, it may not be that easy to judge whether such a picture is true or false. Below, you can try it. AI can also draw more. Build a chair made of avocado, open the market into the sky, put a cat in a medieval scene to find Wi-Fi... these are all small things. Jason Allen, the president of an American board game company, used the AI painting tool Midjourney to generate a piece of "Space Opera" that he fine-tuned himself. It also won the first prize in the art competition at the Colorado State Fair. Technology media TechCrunch evaluated the uncensored "AI Painter" as "Deepfakes for all (all-powerful deep fakes)".
What is the AI face-changing used for?
The earlier known AI “fake” technology is deep fake technology, commonly known as AI face-changing. In 2019, a report stated that there were already tens of thousands of videos produced using deepfake technology on the Internet at that time.
The report also writes that 96% of these videos are pornographic videos, and the protagonists of these pornographic videos are all women. The most popular ones are European and American actresses and Korean female idols. The protagonist's video has been viewed millions of times.
Henry Ajder, a researcher involved in the report, said that users of deepfake forums were requesting or discussing face-swapping pornographic videos featuring women they knew (such as ex-girlfriends). They want to see them put in pornographic clips.
AI painting is not just about changing faces.
Opening Pandora's Box
We entered 5 dark instructions to see if AI painting is unlimited?
AI seems to have limited understanding of violence. But the interpretation of sex is spot on - and it thinks so too.
Stable Diffusion, this open source and powerful "AI painter" has set up a "Safety Checker" for itself, which is equivalent to an automatic audit: once it is detected that the generated image is suspected of violating the rules, it will If it is stated in the content policy that "uncomfortable, pornographic, hateful, violent and other images" cannot be used, the machine will block the image.
The "evil photos" we generated were sent for review, and the machine only judged six nude photos of Justin Bieber as "violations." However, we also successfully generated several photos of Trump kissing Churchill through time and space, and the photos were judged as "safe" by the moderator.
Obviously, from the fact that we successfully generated nude photos of Justin Bieber against his will, it can be seen that Stable Diffusion’s automatic review can be turned off. This way, it can no longer reject you.
In order to restrict AI and the bad thoughts that people tend to have when facing Pandora's Box, the most famous "AI painter" DALL·E 2 has stricter censorship.
A netizen collected all the instructions that caused him to receive content policy violation warnings, including "British apes eating fish and chips", "Squid driving a unicycle and getting away" and "Photos of Jesus undergoing nucleic acid testing" . Any description that may involve hatred, violence, pornography, and the names of all well-known figures are among the prohibited words in DALL·E 2. So you can't manipulate DALL·E 2 to draw you a picture of Trump and Biden kissing, but Stable Diffusion can.
Fake photos generated by AI have loopholes
However, the current photos generated by AI are not perfect.
Zheng Shujing, a reporter at Mingcha Studio, a fact-checking project of The Paper, said that AI-generated pictures will have some characteristics, such as bubbles, surreal backgrounds, character tooth sizes, unnatural hair shapes, etc. Early AI face-swapping was prone to problems when presenting continuous and repeated patterns, often with uneven sizes. Nowadays, some companies have used continuously upgraded generative adversarial networks to improve these problems. These problems have become relatively rare, but sometimes they can still be seen from details such as background deformation and body asymmetry.
Details are where AI often falls short. For example, the helicopter in the picture below does not have a tail fin.

In addition, background information can also help to distinguish whether a photo is authentic or fake. “For example, if you give me a picture that is from the Chongqing wildfires, if you find the last part of the picture, If the modification date is after the incident, it is definitely a fake picture. We sometimes also contact background information, such as checking the model of the helicopter in the picture, etc."
But most of the tools she comes into contact with are not It will tell you directly whether a photo is real or fake, and it needs to be judged by people based on the specific situation.
As AI painting skills become more and more proficient, it will only take more and more effort to distinguish between true and false. The certainty of reality is loosening. At that time, people may often hear voices like this in their minds: “This photo looks too real, so it’s too fake.”
The above is the detailed content of Can you recognize fake photos created by AI?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1379
1379
 52
52
 Debian mail server firewall configuration tips
Apr 13, 2025 am 11:42 AM
Debian mail server firewall configuration tips
Apr 13, 2025 am 11:42 AM
Configuring a Debian mail server's firewall is an important step in ensuring server security. The following are several commonly used firewall configuration methods, including the use of iptables and firewalld. Use iptables to configure firewall to install iptables (if not already installed): sudoapt-getupdatesudoapt-getinstalliptablesView current iptables rules: sudoiptables-L configuration
 How to set the Debian Apache log level
Apr 13, 2025 am 08:33 AM
How to set the Debian Apache log level
Apr 13, 2025 am 08:33 AM
This article describes how to adjust the logging level of the ApacheWeb server in the Debian system. By modifying the configuration file, you can control the verbose level of log information recorded by Apache. Method 1: Modify the main configuration file to locate the configuration file: The configuration file of Apache2.x is usually located in the /etc/apache2/ directory. The file name may be apache2.conf or httpd.conf, depending on your installation method. Edit configuration file: Open configuration file with root permissions using a text editor (such as nano): sudonano/etc/apache2/apache2.conf
 How debian readdir integrates with other tools
Apr 13, 2025 am 09:42 AM
How debian readdir integrates with other tools
Apr 13, 2025 am 09:42 AM
The readdir function in the Debian system is a system call used to read directory contents and is often used in C programming. This article will explain how to integrate readdir with other tools to enhance its functionality. Method 1: Combining C language program and pipeline First, write a C program to call the readdir function and output the result: #include#include#include#includeintmain(intargc,char*argv[]){DIR*dir;structdirent*entry;if(argc!=2){
 How to optimize the performance of debian readdir
Apr 13, 2025 am 08:48 AM
How to optimize the performance of debian readdir
Apr 13, 2025 am 08:48 AM
In Debian systems, readdir system calls are used to read directory contents. If its performance is not good, try the following optimization strategy: Simplify the number of directory files: Split large directories into multiple small directories as much as possible, reducing the number of items processed per readdir call. Enable directory content caching: build a cache mechanism, update the cache regularly or when directory content changes, and reduce frequent calls to readdir. Memory caches (such as Memcached or Redis) or local caches (such as files or databases) can be considered. Adopt efficient data structure: If you implement directory traversal by yourself, select more efficient data structures (such as hash tables instead of linear search) to store and access directory information
 How to implement file sorting by debian readdir
Apr 13, 2025 am 09:06 AM
How to implement file sorting by debian readdir
Apr 13, 2025 am 09:06 AM
In Debian systems, the readdir function is used to read directory contents, but the order in which it returns is not predefined. To sort files in a directory, you need to read all files first, and then sort them using the qsort function. The following code demonstrates how to sort directory files using readdir and qsort in Debian system: #include#include#include#include#include//Custom comparison function, used for qsortintcompare(constvoid*a,constvoid*b){returnstrcmp(*(
 Debian mail server SSL certificate installation method
Apr 13, 2025 am 11:39 AM
Debian mail server SSL certificate installation method
Apr 13, 2025 am 11:39 AM
The steps to install an SSL certificate on the Debian mail server are as follows: 1. Install the OpenSSL toolkit First, make sure that the OpenSSL toolkit is already installed on your system. If not installed, you can use the following command to install: sudoapt-getupdatesudoapt-getinstallopenssl2. Generate private key and certificate request Next, use OpenSSL to generate a 2048-bit RSA private key and a certificate request (CSR): openss
 How to perform digital signature verification with Debian OpenSSL
Apr 13, 2025 am 11:09 AM
How to perform digital signature verification with Debian OpenSSL
Apr 13, 2025 am 11:09 AM
Using OpenSSL for digital signature verification on Debian systems, you can follow these steps: Preparation to install OpenSSL: Make sure your Debian system has OpenSSL installed. If not installed, you can use the following command to install it: sudoaptupdatesudoaptininstallopenssl to obtain the public key: digital signature verification requires the signer's public key. Typically, the public key will be provided in the form of a file, such as public_key.pe
 How Debian OpenSSL prevents man-in-the-middle attacks
Apr 13, 2025 am 10:30 AM
How Debian OpenSSL prevents man-in-the-middle attacks
Apr 13, 2025 am 10:30 AM
In Debian systems, OpenSSL is an important library for encryption, decryption and certificate management. To prevent a man-in-the-middle attack (MITM), the following measures can be taken: Use HTTPS: Ensure that all network requests use the HTTPS protocol instead of HTTP. HTTPS uses TLS (Transport Layer Security Protocol) to encrypt communication data to ensure that the data is not stolen or tampered during transmission. Verify server certificate: Manually verify the server certificate on the client to ensure it is trustworthy. The server can be manually verified through the delegate method of URLSession




