 Technology peripherals
Technology peripherals
 AI
AI
 Are AI tools becoming a hot commodity for cybercriminals? Study finds Russian hackers are bypassing OpenAI restrictions to access ChatGPT
Are AI tools becoming a hot commodity for cybercriminals? Study finds Russian hackers are bypassing OpenAI restrictions to access ChatGPT
Are AI tools becoming a hot commodity for cybercriminals? Study finds Russian hackers are bypassing OpenAI restrictions to access ChatGPT
According to industry media reports, OpenAI has restricted the application of ChatGPT, a powerful chatbot, in some countries and regions due to concerns that it may be used for criminal activities. However, the study found that some cybercriminals from Russia have been trying to find new ways to bypass existing restrictions in order to adopt ChatGPT, and found cases including bypassing IP, payment card and phone number restrictions.
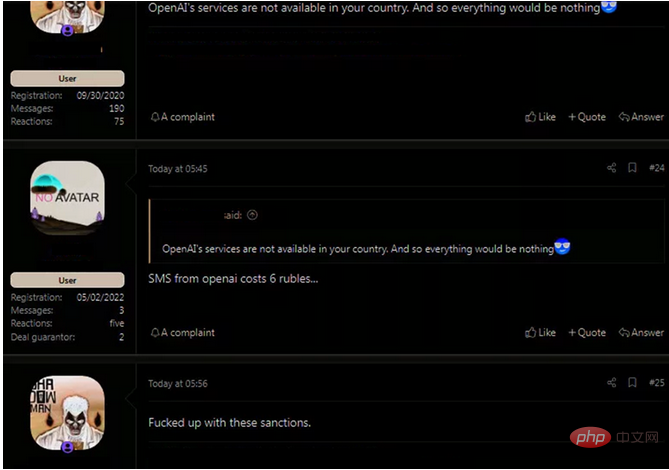
Researchers found evidence on hacker forums that Russian hackers were trying to bypass restrictions to access ChatGPT
Since November 2022 Since its launch, ChatGPT has become an important workflow tool for developers, writers, and students, but it has also become a powerful weapon that can be exploited by cybercriminals, with evidence that hackers use it to write malicious code and improve phishing emails.
ChatGPT may be used for malicious purposes, which means OpenAI needs to limit how the tool is deployed, because hackers using ChatGPT can more quickly carry out malicious attacks. OpenAI uses geo-blocking measures to prevent Russian users from accessing the system.
However, Check Point Software researchers found multiple instances of hackers from Russia talking on underground hacking forums about how to circumvent these restrictions. For example, a hacker group from Russia raised a question on the forum - if they cannot enter ChatGPT normally, how can they use a stolen payment card to pay for an OpenAI account and use the API to access the system? The system is currently in a free-to-use preview, while the API includes text and code generation using tokens for payment during sessions.
Sergey Shykevich, manager of Check Point’s threat intelligence department, said that bypassing OpenAI’s restrictions is not particularly difficult. “We are now seeing some Russian hackers already discussing and examining how to bypass geofences and use ChatGPT with them.” for their malicious purposes. We believe that these hackers are likely trying to test and adopt ChatGPT in their cybercriminal activities. Cybercriminals are increasingly interested in ChatGPT because the artificial intelligence technology behind it can make their cyberattacks more Efficient."
These underground hacking forums also offer tutorials in Russian about semi-legitimate online text messaging services and how to use them to register for ChatGPT, making it appear that ChatGPT is being used in other countries where it is not blocked.
Hackers learn from these forums that they only need to pay 2 cents for a virtual number and then use this number to obtain codes from OpenAI. These temporary phone numbers can come from anywhere in the world, and new numbers can be generated as needed.
Malicious use of Infostealer and ChatGPT
Previous investigations found examples of cybercriminals posting on these hacking forums how to use ChatGPT for illegal activities. This includes creating a very simple Infostealer. As artificial intelligence tools become more widely used, these Infostealers will become more advanced.
Infostealer is an example of the adoption of these "simple tools" and appeared on a hacker forum in a post titled "ChatGPT - The Benefits of Malware". The author of the post notes that hackers can use ChatGPT to recreate the malware by feeding descriptions and reports into an artificial intelligence tool, and then share Python-based stealing code that searches for common file types and copies them to random files. folders and upload them to a hardcoded FTP server.
Shykevich said. "Cybercriminals have found ChatGPT attractive. In recent weeks, we have discovered evidence that hackers have begun using ChatGPT to write malicious code. ChatGPT has the potential to provide a good starting point for hackers and speed up the progress of cyber attacks. As ChatGPT can be used Just as it helps developers write code, it can also be used for malicious purposes."
OpenAI said it has taken steps to limit the use of ChatGPT, including limiting the types of requests that can be made, but some requests may be missed. There is also evidence that its tips are used to "spoof" ChatGPT, providing potentially harmful code examples under the guise of research or as fictitious examples.
ChatGPT and potential misinformation
Meanwhile, OpenAI is working with Georgetown University’s Center for Security and Emerging Technologies and the Stanford Internet Observatory to study large language models ( For example, GPT-3), the basis of ChatGPT, may be used to spread false information.
This model can be used to reduce the cost of operating influence operations, keeping them within the control of new types of cybercriminals, whereas previously only large actors had access to such content. Likewise, recruiters who can automate text production may gain new competitive advantages.
Hackers' use of ChatGPT can also lead to different behaviors, increase the scale of cyber attacks, and allow the creation of more personalized and targeted content compared to manual creation. Ultimately, they found that text generation tools were able to generate more impactful and persuasive messages, compared to most human-generated propaganda documents that hackers may lack the required knowledge of the language or culture of their targets.
OpenAI researchers declare: “Our basic judgment is that language models are useful for brand evangelists and may transform online influence operations. Even the most advanced models are encrypted, or by applying Programming interface (API) access is controlled, and advocates may also be inclined to adopt open source alternatives.”
The above is the detailed content of Are AI tools becoming a hot commodity for cybercriminals? Study finds Russian hackers are bypassing OpenAI restrictions to access ChatGPT. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1385
1385
 52
52
 Centos shutdown command line
Apr 14, 2025 pm 09:12 PM
Centos shutdown command line
Apr 14, 2025 pm 09:12 PM
The CentOS shutdown command is shutdown, and the syntax is shutdown [Options] Time [Information]. Options include: -h Stop the system immediately; -P Turn off the power after shutdown; -r restart; -t Waiting time. Times can be specified as immediate (now), minutes ( minutes), or a specific time (hh:mm). Added information can be displayed in system messages.
 How to check CentOS HDFS configuration
Apr 14, 2025 pm 07:21 PM
How to check CentOS HDFS configuration
Apr 14, 2025 pm 07:21 PM
Complete Guide to Checking HDFS Configuration in CentOS Systems This article will guide you how to effectively check the configuration and running status of HDFS on CentOS systems. The following steps will help you fully understand the setup and operation of HDFS. Verify Hadoop environment variable: First, make sure the Hadoop environment variable is set correctly. In the terminal, execute the following command to verify that Hadoop is installed and configured correctly: hadoopversion Check HDFS configuration file: The core configuration file of HDFS is located in the /etc/hadoop/conf/ directory, where core-site.xml and hdfs-site.xml are crucial. use
 What are the backup methods for GitLab on CentOS
Apr 14, 2025 pm 05:33 PM
What are the backup methods for GitLab on CentOS
Apr 14, 2025 pm 05:33 PM
Backup and Recovery Policy of GitLab under CentOS System In order to ensure data security and recoverability, GitLab on CentOS provides a variety of backup methods. This article will introduce several common backup methods, configuration parameters and recovery processes in detail to help you establish a complete GitLab backup and recovery strategy. 1. Manual backup Use the gitlab-rakegitlab:backup:create command to execute manual backup. This command backs up key information such as GitLab repository, database, users, user groups, keys, and permissions. The default backup file is stored in the /var/opt/gitlab/backups directory. You can modify /etc/gitlab
 Detailed explanation of docker principle
Apr 14, 2025 pm 11:57 PM
Detailed explanation of docker principle
Apr 14, 2025 pm 11:57 PM
Docker uses Linux kernel features to provide an efficient and isolated application running environment. Its working principle is as follows: 1. The mirror is used as a read-only template, which contains everything you need to run the application; 2. The Union File System (UnionFS) stacks multiple file systems, only storing the differences, saving space and speeding up; 3. The daemon manages the mirrors and containers, and the client uses them for interaction; 4. Namespaces and cgroups implement container isolation and resource limitations; 5. Multiple network modes support container interconnection. Only by understanding these core concepts can you better utilize Docker.
 How is the GPU support for PyTorch on CentOS
Apr 14, 2025 pm 06:48 PM
How is the GPU support for PyTorch on CentOS
Apr 14, 2025 pm 06:48 PM
Enable PyTorch GPU acceleration on CentOS system requires the installation of CUDA, cuDNN and GPU versions of PyTorch. The following steps will guide you through the process: CUDA and cuDNN installation determine CUDA version compatibility: Use the nvidia-smi command to view the CUDA version supported by your NVIDIA graphics card. For example, your MX450 graphics card may support CUDA11.1 or higher. Download and install CUDAToolkit: Visit the official website of NVIDIACUDAToolkit and download and install the corresponding version according to the highest CUDA version supported by your graphics card. Install cuDNN library:
 Centos install mysql
Apr 14, 2025 pm 08:09 PM
Centos install mysql
Apr 14, 2025 pm 08:09 PM
Installing MySQL on CentOS involves the following steps: Adding the appropriate MySQL yum source. Execute the yum install mysql-server command to install the MySQL server. Use the mysql_secure_installation command to make security settings, such as setting the root user password. Customize the MySQL configuration file as needed. Tune MySQL parameters and optimize databases for performance.
 How to view GitLab logs under CentOS
Apr 14, 2025 pm 06:18 PM
How to view GitLab logs under CentOS
Apr 14, 2025 pm 06:18 PM
A complete guide to viewing GitLab logs under CentOS system This article will guide you how to view various GitLab logs in CentOS system, including main logs, exception logs, and other related logs. Please note that the log file path may vary depending on the GitLab version and installation method. If the following path does not exist, please check the GitLab installation directory and configuration files. 1. View the main GitLab log Use the following command to view the main log file of the GitLabRails application: Command: sudocat/var/log/gitlab/gitlab-rails/production.log This command will display product
 How to choose the PyTorch version on CentOS
Apr 14, 2025 pm 06:51 PM
How to choose the PyTorch version on CentOS
Apr 14, 2025 pm 06:51 PM
When installing PyTorch on CentOS system, you need to carefully select the appropriate version and consider the following key factors: 1. System environment compatibility: Operating system: It is recommended to use CentOS7 or higher. CUDA and cuDNN:PyTorch version and CUDA version are closely related. For example, PyTorch1.9.0 requires CUDA11.1, while PyTorch2.0.1 requires CUDA11.3. The cuDNN version must also match the CUDA version. Before selecting the PyTorch version, be sure to confirm that compatible CUDA and cuDNN versions have been installed. Python version: PyTorch official branch



