 Technology peripherals
Technology peripherals
 AI
AI
 Three ways artificial intelligence is causing dire cybersecurity threats
Three ways artificial intelligence is causing dire cybersecurity threats
Three ways artificial intelligence is causing dire cybersecurity threats

Artificial intelligence technology is driving some huge changes in digital technology. Many developments brought about by artificial intelligence are beneficial.
However, artificial intelligence also brings some false propositions. One of the biggest issues posed by artificial intelligence is the growing threat to cybersecurity. Increasingly, hackers are finding innovative ways to weaponize artificial intelligence to commit cybercrimes.
As these threats worsen, businesses and the cybersecurity experts they rely on need to be aware of the threat AI poses in the hands of hackers and find ways to leverage AI to bolster their own defenses.
What is the most important way for hackers to use artificial intelligence to attack their targets?
As a company with a strong network influence, it must do its best to ensure that its website and system remain as safe as possible Safety. The biggest concern for businesses is being attacked by cybercriminals and letting business and customer data fall into the wrong hands. To prevent this from happening, it's important to be aware of any current digital security threats.
Unfortunately, artificial intelligence technology will only make cybersecurity threats worse than ever. Industry experts say artificial intelligence technology is used by both cybersecurity experts and black hat hackers. However, cybercriminals appear to benefit the most from AI, which means cybersecurity experts will need to be more diligent and committed to innovation to use AI effectively.
With that in mind, here’s a look at the top three digital threats that are getting worse due to the adoption of artificial intelligence technology, and how to prevent them:
(1) Ransomware Attacks
According to "Forbes", ransomware is one of the top cyber threats currently threatening small and medium-sized enterprises. As the name suggests, hackers will break into a company's network and then demand a ransom to redeem their data. Since most ransomware attacks begin with malware infecting a computer, often via a phishing email, it's important to educate employees on how to identify and delete these emails. Additionally, it is helpful to back up your data regularly; this way, if a breach does occur, the business can recover the data quickly and with minimal downtime.
Industry expert Kyle Alspach wrote an article in May about the threat posed by artificial intelligence-driven ransomware attacks. Renowned cybersecurity expert Mikko Hyppönen noted that these ransomware attacks will become more terrifying as hackers become more adept at using artificial intelligence technology to automate many of their strategies.
(2) Weak network security measures
Another reason why cybercriminals gain access to corporate websites or systems is that the network security of these companies and their employees is poor. Cybersecurity is about how teams in an organization use technology, and how careful or careless people are in protecting sensitive data. Examples of weak cybersecurity measures include not using two-factor authentication to log into company accounts, writing down passwords on sticky notes, using unprotected Wi-Fi networks, and working from personal devices.
As more hackers use artificial intelligence to identify weak targets, this will also become a greater threat. Hackers often try to target those with the weakest security, so they use artificial intelligence to automate the process of finding potential victims.
To help improve cybersecurity posture, start by requiring two-factor authentication, using a password manager, and asking employees not to use personal devices at work. Additionally, to help ensure that hackers cannot access available information, it is important to ensure that your business's SSL certificates are updated. Basically, when you purchase an SSL certificate, it will ensure that the data sent between the customer and the business's website cannot be read by hackers. To make the process of monitoring security certificates as easy as possible, you may want to go through an SSL certificate manager program developed by companies like Sectigo. In addition to SSL certificate authorities, it provides other innovative digital security solutions, including PKI management, private PKI, and private CA services.
(3) Credential stuffing
"Credential stuffing" refers to cybercriminals using credentials stolen from one company to gain access to another company. Hackers usually obtain this data through hacking or purchasing it from the dark web.
They can use artificial intelligence to make these cyberattacks worse. Machine learning tools help them find connections between different companies so they can use credential stuffing more efficiently.
Unfortunately, this type of cyberattack is becoming more common and harder to track, mainly because cybercriminals have obtained a list of valid usernames and passwords, and they then use those credentials to log in Victim's website. Fortunately, credential fraud can be prevented by ensuring employees don't use the same passwords on different websites. Requiring multi-factor authentication also helps prevent successful credential stuffing.
As hackers become increasingly brazen in their use of artificial intelligence, being proactive can help prevent digital threats
Hackers are always looking for new ways to access sensitive data. Artificial intelligence technology makes these criminals more terrifying. The good news is that with artificial intelligence becoming a greater threat than ever, cybersecurity professionals can take more precautions to strengthen their security defenses. Wise cybersecurity experts will also find ways to leverage AI technology to combat hackers.
Understanding the latest tactics of hackers and then taking a proactive approach can prevent security breaches from affecting your website. By educating your teams to avoid phishing scams, developing two-factor authentication, using SSL certificates and PKI management procedures, and employing sound cybersecurity measures, businesses will make great strides in improving their digital security.
The above is the detailed content of Three ways artificial intelligence is causing dire cybersecurity threats. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1378
1378
 52
52
 Bytedance Cutting launches SVIP super membership: 499 yuan for continuous annual subscription, providing a variety of AI functions
Jun 28, 2024 am 03:51 AM
Bytedance Cutting launches SVIP super membership: 499 yuan for continuous annual subscription, providing a variety of AI functions
Jun 28, 2024 am 03:51 AM
This site reported on June 27 that Jianying is a video editing software developed by FaceMeng Technology, a subsidiary of ByteDance. It relies on the Douyin platform and basically produces short video content for users of the platform. It is compatible with iOS, Android, and Windows. , MacOS and other operating systems. Jianying officially announced the upgrade of its membership system and launched a new SVIP, which includes a variety of AI black technologies, such as intelligent translation, intelligent highlighting, intelligent packaging, digital human synthesis, etc. In terms of price, the monthly fee for clipping SVIP is 79 yuan, the annual fee is 599 yuan (note on this site: equivalent to 49.9 yuan per month), the continuous monthly subscription is 59 yuan per month, and the continuous annual subscription is 499 yuan per year (equivalent to 41.6 yuan per month) . In addition, the cut official also stated that in order to improve the user experience, those who have subscribed to the original VIP
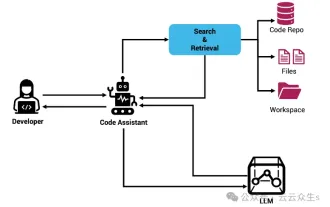 Context-augmented AI coding assistant using Rag and Sem-Rag
Jun 10, 2024 am 11:08 AM
Context-augmented AI coding assistant using Rag and Sem-Rag
Jun 10, 2024 am 11:08 AM
Improve developer productivity, efficiency, and accuracy by incorporating retrieval-enhanced generation and semantic memory into AI coding assistants. Translated from EnhancingAICodingAssistantswithContextUsingRAGandSEM-RAG, author JanakiramMSV. While basic AI programming assistants are naturally helpful, they often fail to provide the most relevant and correct code suggestions because they rely on a general understanding of the software language and the most common patterns of writing software. The code generated by these coding assistants is suitable for solving the problems they are responsible for solving, but often does not conform to the coding standards, conventions and styles of the individual teams. This often results in suggestions that need to be modified or refined in order for the code to be accepted into the application
 Can fine-tuning really allow LLM to learn new things: introducing new knowledge may make the model produce more hallucinations
Jun 11, 2024 pm 03:57 PM
Can fine-tuning really allow LLM to learn new things: introducing new knowledge may make the model produce more hallucinations
Jun 11, 2024 pm 03:57 PM
Large Language Models (LLMs) are trained on huge text databases, where they acquire large amounts of real-world knowledge. This knowledge is embedded into their parameters and can then be used when needed. The knowledge of these models is "reified" at the end of training. At the end of pre-training, the model actually stops learning. Align or fine-tune the model to learn how to leverage this knowledge and respond more naturally to user questions. But sometimes model knowledge is not enough, and although the model can access external content through RAG, it is considered beneficial to adapt the model to new domains through fine-tuning. This fine-tuning is performed using input from human annotators or other LLM creations, where the model encounters additional real-world knowledge and integrates it
 Seven Cool GenAI & LLM Technical Interview Questions
Jun 07, 2024 am 10:06 AM
Seven Cool GenAI & LLM Technical Interview Questions
Jun 07, 2024 am 10:06 AM
To learn more about AIGC, please visit: 51CTOAI.x Community https://www.51cto.com/aigc/Translator|Jingyan Reviewer|Chonglou is different from the traditional question bank that can be seen everywhere on the Internet. These questions It requires thinking outside the box. Large Language Models (LLMs) are increasingly important in the fields of data science, generative artificial intelligence (GenAI), and artificial intelligence. These complex algorithms enhance human skills and drive efficiency and innovation in many industries, becoming the key for companies to remain competitive. LLM has a wide range of applications. It can be used in fields such as natural language processing, text generation, speech recognition and recommendation systems. By learning from large amounts of data, LLM is able to generate text
 To provide a new scientific and complex question answering benchmark and evaluation system for large models, UNSW, Argonne, University of Chicago and other institutions jointly launched the SciQAG framework
Jul 25, 2024 am 06:42 AM
To provide a new scientific and complex question answering benchmark and evaluation system for large models, UNSW, Argonne, University of Chicago and other institutions jointly launched the SciQAG framework
Jul 25, 2024 am 06:42 AM
Editor |ScienceAI Question Answering (QA) data set plays a vital role in promoting natural language processing (NLP) research. High-quality QA data sets can not only be used to fine-tune models, but also effectively evaluate the capabilities of large language models (LLM), especially the ability to understand and reason about scientific knowledge. Although there are currently many scientific QA data sets covering medicine, chemistry, biology and other fields, these data sets still have some shortcomings. First, the data form is relatively simple, most of which are multiple-choice questions. They are easy to evaluate, but limit the model's answer selection range and cannot fully test the model's ability to answer scientific questions. In contrast, open-ended Q&A
 Five schools of machine learning you don't know about
Jun 05, 2024 pm 08:51 PM
Five schools of machine learning you don't know about
Jun 05, 2024 pm 08:51 PM
Machine learning is an important branch of artificial intelligence that gives computers the ability to learn from data and improve their capabilities without being explicitly programmed. Machine learning has a wide range of applications in various fields, from image recognition and natural language processing to recommendation systems and fraud detection, and it is changing the way we live. There are many different methods and theories in the field of machine learning, among which the five most influential methods are called the "Five Schools of Machine Learning". The five major schools are the symbolic school, the connectionist school, the evolutionary school, the Bayesian school and the analogy school. 1. Symbolism, also known as symbolism, emphasizes the use of symbols for logical reasoning and expression of knowledge. This school of thought believes that learning is a process of reverse deduction, through existing
 SOTA performance, Xiamen multi-modal protein-ligand affinity prediction AI method, combines molecular surface information for the first time
Jul 17, 2024 pm 06:37 PM
SOTA performance, Xiamen multi-modal protein-ligand affinity prediction AI method, combines molecular surface information for the first time
Jul 17, 2024 pm 06:37 PM
Editor | KX In the field of drug research and development, accurately and effectively predicting the binding affinity of proteins and ligands is crucial for drug screening and optimization. However, current studies do not take into account the important role of molecular surface information in protein-ligand interactions. Based on this, researchers from Xiamen University proposed a novel multi-modal feature extraction (MFE) framework, which for the first time combines information on protein surface, 3D structure and sequence, and uses a cross-attention mechanism to compare different modalities. feature alignment. Experimental results demonstrate that this method achieves state-of-the-art performance in predicting protein-ligand binding affinities. Furthermore, ablation studies demonstrate the effectiveness and necessity of protein surface information and multimodal feature alignment within this framework. Related research begins with "S
 Laying out markets such as AI, GlobalFoundries acquires Tagore Technology's gallium nitride technology and related teams
Jul 15, 2024 pm 12:21 PM
Laying out markets such as AI, GlobalFoundries acquires Tagore Technology's gallium nitride technology and related teams
Jul 15, 2024 pm 12:21 PM
According to news from this website on July 5, GlobalFoundries issued a press release on July 1 this year, announcing the acquisition of Tagore Technology’s power gallium nitride (GaN) technology and intellectual property portfolio, hoping to expand its market share in automobiles and the Internet of Things. and artificial intelligence data center application areas to explore higher efficiency and better performance. As technologies such as generative AI continue to develop in the digital world, gallium nitride (GaN) has become a key solution for sustainable and efficient power management, especially in data centers. This website quoted the official announcement that during this acquisition, Tagore Technology’s engineering team will join GLOBALFOUNDRIES to further develop gallium nitride technology. G



