Why automotive cybersecurity is important
Cybersecurity is becoming a fundamental issue in the development of autonomous vehicle systems, as attacks could have serious consequences for autonomous electric vehicles and potentially endanger human lives. Software attacks can impact data-driven decisions that can negatively impact the autonomy of electric vehicles and undermine the benefits of autonomous vehicles.
With the integration of technologies such as edge computing, 5G, and high-performance processing units, autonomous vehicles have made many advances recently. In autonomous electric vehicles, edge computing helps process large amounts of data at the edge to reduce latency and help vehicles make data-driven decisions in real time. Edge sensors deployed in vehicles have scarce resources but require high computing power to process data. This data is then migrated to edge data centers and clouds to provide IoV communications and services. These communications and services have aroused great interest as potential elements of future intelligent transportation systems.
The Internet of Vehicles promotes communication and interaction between vehicle charging technologies, infrastructure, pedestrians and networks. But these advanced communication systems bring a larger attack area for cyberattacks and disrupt the existing ecosystem, which can lead to serious consequences.
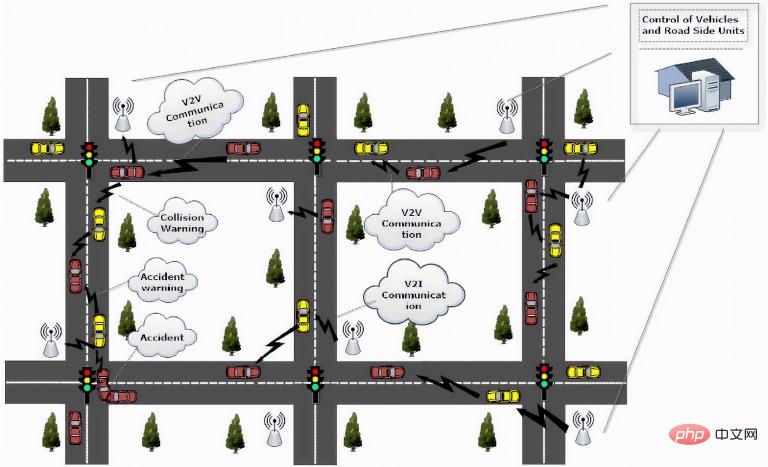
(Internet of Vehicles Communication System)
In the entire autonomous driving ecosystem, Internet of Vehicles communication Responsible for the transmission of edge data between various parts of the transportation system requires multiple communication channels between these edge sensors and other infrastructure. These multiple communication channels make vehicles vulnerable to cyberattacks, which can have severe impacts not only on the vehicle, but also on other connected devices. The increase in the number of connected devices can make these cyberattacks unpredictable and more frequent.
Many different entry points can be used to penetrate the vehicle architecture, including vehicle databases, telematics technology, and vehicle components. In recent years, researchers have focused their attention on vehicular ad hoc networks, which use dedicated short-range communication technology based on the IEEE802.11p standard for wireless access in vehicle networks. Another communication protocol used in connected car communications is mobile cellular networks using long-term evolution technology.
One of the most common Internet of Vehicles communication-related attacks is the vehicle mobile communication network. Since 2008, the vehicle mobile communication network has been widely studied to analyze the external wireless communication of the vehicle system. Transmission security issues. Some of the known attacks on automotive mobile communication networks are man-in-the-middle attacks, disinformation attacks, DoS, location tracking, malicious code, and replay attacks. Another known attack on autonomous vehicles using telematics communications is against the infotainment system and Bluetooth data transmission.
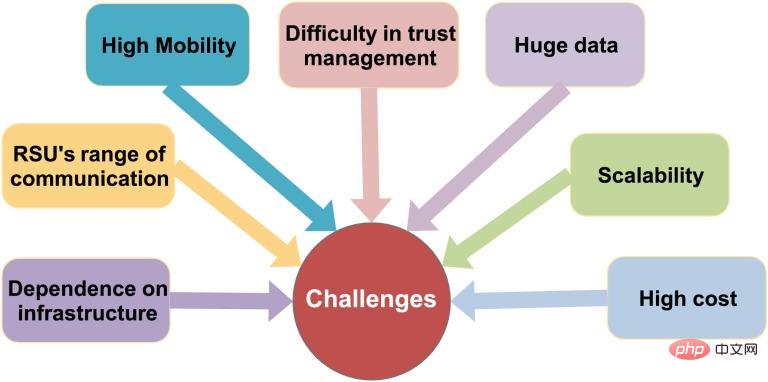
(Security Challenges of Vehicle Mobile Communication Networks)
# As explained in an authoritative industry magazine As such, a three-layer framework can be used to understand the different parts of a self-driving car and how they can be attacked by hackers:
- The sensing layer consists of continuous monitoring of vehicle dynamics and surroundings Environmental sensors. These edge sensors are vulnerable to eavesdropping, jamming, and spoofing attacks.
- The communication layer consists of near-field and far-field communications to facilitate communication between other nearby edge sensors and distant edge data centers, which leads to attacks such as indirect and forged information.
- The control layer at the top of the hierarchy implements autonomous driving functions, such as automatically controlling the vehicle's speed, braking, and steering. Attacks on the sensing and communication layers can propagate upward, affecting functionality and compromising the security of the control layer.
Integrated Cyber Defense
Develops defense solutions to combat increasing cyberattacks on electric vehicles, now works as a security engineer focus areas of research. In order to introduce technological improvements that build autonomous driving software and hardware capabilities, integrated defense mechanisms become an important parameter in the design process. Possible cybersecurity solutions are discussed below.
The electronic control unit is the core of the vehicle processing and communicating data. Information received from the electronic control unit is encrypted to prevent injection and indirect attacks. Recent research shows that encryption and vehicle authentication can be used to prevent spoofing, tampering, masquerading and replay attacks during communications between edge data centers and vehicles.
Specialized intrusion detection systems are required to continuously monitor network systems and detect possible network attacks. To detect network attacks, traditional intrusion detection systems rely on firewalls, or rule-based systems, but cannot effectively detect complex automotive attacks because time series, vehicle network data do not capture complex dependencies. Since edge sensors in vehicles can be used for communication between electronic control units and external systems, AI-based solutions can be used to parse vehicle network data.
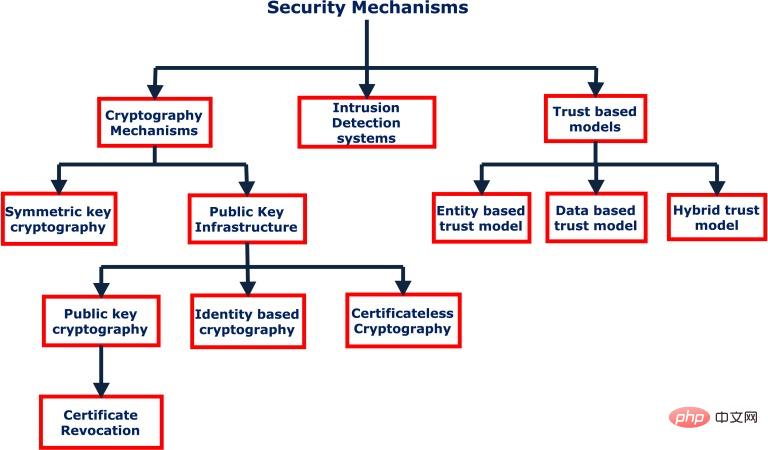
(Defense mechanism of self-driving cars)
Blockchain technology can be used for Internet of Vehicles communications , to facilitate the secure transmission of essential safety information between vehicle systems and the cloud. Blockchain technology provides a decentralized mechanism that allows vehicles to verify the data they receive in a trustless manner. The technology can help establish secure connections between vehicles and payment gateways for faster fuel purchases, transactions at toll plazas and even selling sensor data.
As cyberattacks on the automotive industry increase, defense methods must also come under constant scrutiny. The security technology of CAN network, the security of authentication protocol, and the security of intrusion detection system have always been hot spots of research. In the future, the combination of artificial intelligence and big data analysis will be considered to improve defense methods and propose future-oriented security models.
The above is the detailed content of Why automotive cybersecurity is important. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1377
1377
 52
52
 Why is Gaussian Splatting so popular in autonomous driving that NeRF is starting to be abandoned?
Jan 17, 2024 pm 02:57 PM
Why is Gaussian Splatting so popular in autonomous driving that NeRF is starting to be abandoned?
Jan 17, 2024 pm 02:57 PM
Written above & the author’s personal understanding Three-dimensional Gaussiansplatting (3DGS) is a transformative technology that has emerged in the fields of explicit radiation fields and computer graphics in recent years. This innovative method is characterized by the use of millions of 3D Gaussians, which is very different from the neural radiation field (NeRF) method, which mainly uses an implicit coordinate-based model to map spatial coordinates to pixel values. With its explicit scene representation and differentiable rendering algorithms, 3DGS not only guarantees real-time rendering capabilities, but also introduces an unprecedented level of control and scene editing. This positions 3DGS as a potential game-changer for next-generation 3D reconstruction and representation. To this end, we provide a systematic overview of the latest developments and concerns in the field of 3DGS for the first time.
 How to solve the long tail problem in autonomous driving scenarios?
Jun 02, 2024 pm 02:44 PM
How to solve the long tail problem in autonomous driving scenarios?
Jun 02, 2024 pm 02:44 PM
Yesterday during the interview, I was asked whether I had done any long-tail related questions, so I thought I would give a brief summary. The long-tail problem of autonomous driving refers to edge cases in autonomous vehicles, that is, possible scenarios with a low probability of occurrence. The perceived long-tail problem is one of the main reasons currently limiting the operational design domain of single-vehicle intelligent autonomous vehicles. The underlying architecture and most technical issues of autonomous driving have been solved, and the remaining 5% of long-tail problems have gradually become the key to restricting the development of autonomous driving. These problems include a variety of fragmented scenarios, extreme situations, and unpredictable human behavior. The "long tail" of edge scenarios in autonomous driving refers to edge cases in autonomous vehicles (AVs). Edge cases are possible scenarios with a low probability of occurrence. these rare events
 Choose camera or lidar? A recent review on achieving robust 3D object detection
Jan 26, 2024 am 11:18 AM
Choose camera or lidar? A recent review on achieving robust 3D object detection
Jan 26, 2024 am 11:18 AM
0.Written in front&& Personal understanding that autonomous driving systems rely on advanced perception, decision-making and control technologies, by using various sensors (such as cameras, lidar, radar, etc.) to perceive the surrounding environment, and using algorithms and models for real-time analysis and decision-making. This enables vehicles to recognize road signs, detect and track other vehicles, predict pedestrian behavior, etc., thereby safely operating and adapting to complex traffic environments. This technology is currently attracting widespread attention and is considered an important development area in the future of transportation. one. But what makes autonomous driving difficult is figuring out how to make the car understand what's going on around it. This requires that the three-dimensional object detection algorithm in the autonomous driving system can accurately perceive and describe objects in the surrounding environment, including their locations,
 This article is enough for you to read about autonomous driving and trajectory prediction!
Feb 28, 2024 pm 07:20 PM
This article is enough for you to read about autonomous driving and trajectory prediction!
Feb 28, 2024 pm 07:20 PM
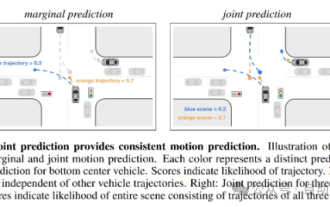
Trajectory prediction plays an important role in autonomous driving. Autonomous driving trajectory prediction refers to predicting the future driving trajectory of the vehicle by analyzing various data during the vehicle's driving process. As the core module of autonomous driving, the quality of trajectory prediction is crucial to downstream planning control. The trajectory prediction task has a rich technology stack and requires familiarity with autonomous driving dynamic/static perception, high-precision maps, lane lines, neural network architecture (CNN&GNN&Transformer) skills, etc. It is very difficult to get started! Many fans hope to get started with trajectory prediction as soon as possible and avoid pitfalls. Today I will take stock of some common problems and introductory learning methods for trajectory prediction! Introductory related knowledge 1. Are the preview papers in order? A: Look at the survey first, p
 SIMPL: A simple and efficient multi-agent motion prediction benchmark for autonomous driving
Feb 20, 2024 am 11:48 AM
SIMPL: A simple and efficient multi-agent motion prediction benchmark for autonomous driving
Feb 20, 2024 am 11:48 AM
Original title: SIMPL: ASimpleandEfficientMulti-agentMotionPredictionBaselineforAutonomousDriving Paper link: https://arxiv.org/pdf/2402.02519.pdf Code link: https://github.com/HKUST-Aerial-Robotics/SIMPL Author unit: Hong Kong University of Science and Technology DJI Paper idea: This paper proposes a simple and efficient motion prediction baseline (SIMPL) for autonomous vehicles. Compared with traditional agent-cent
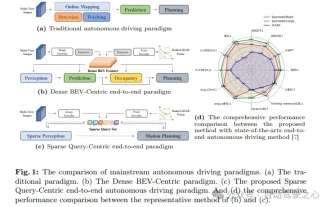 nuScenes' latest SOTA | SparseAD: Sparse query helps efficient end-to-end autonomous driving!
Apr 17, 2024 pm 06:22 PM
nuScenes' latest SOTA | SparseAD: Sparse query helps efficient end-to-end autonomous driving!
Apr 17, 2024 pm 06:22 PM
Written in front & starting point The end-to-end paradigm uses a unified framework to achieve multi-tasking in autonomous driving systems. Despite the simplicity and clarity of this paradigm, the performance of end-to-end autonomous driving methods on subtasks still lags far behind single-task methods. At the same time, the dense bird's-eye view (BEV) features widely used in previous end-to-end methods make it difficult to scale to more modalities or tasks. A sparse search-centric end-to-end autonomous driving paradigm (SparseAD) is proposed here, in which sparse search fully represents the entire driving scenario, including space, time, and tasks, without any dense BEV representation. Specifically, a unified sparse architecture is designed for task awareness including detection, tracking, and online mapping. In addition, heavy
 Let's talk about end-to-end and next-generation autonomous driving systems, as well as some misunderstandings about end-to-end autonomous driving?
Apr 15, 2024 pm 04:13 PM
Let's talk about end-to-end and next-generation autonomous driving systems, as well as some misunderstandings about end-to-end autonomous driving?
Apr 15, 2024 pm 04:13 PM
In the past month, due to some well-known reasons, I have had very intensive exchanges with various teachers and classmates in the industry. An inevitable topic in the exchange is naturally end-to-end and the popular Tesla FSDV12. I would like to take this opportunity to sort out some of my thoughts and opinions at this moment for your reference and discussion. How to define an end-to-end autonomous driving system, and what problems should be expected to be solved end-to-end? According to the most traditional definition, an end-to-end system refers to a system that inputs raw information from sensors and directly outputs variables of concern to the task. For example, in image recognition, CNN can be called end-to-end compared to the traditional feature extractor + classifier method. In autonomous driving tasks, input data from various sensors (camera/LiDAR
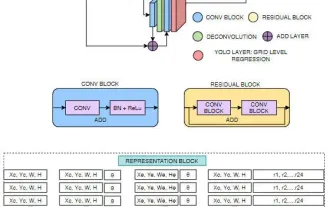 FisheyeDetNet: the first target detection algorithm based on fisheye camera
Apr 26, 2024 am 11:37 AM
FisheyeDetNet: the first target detection algorithm based on fisheye camera
Apr 26, 2024 am 11:37 AM
Target detection is a relatively mature problem in autonomous driving systems, among which pedestrian detection is one of the earliest algorithms to be deployed. Very comprehensive research has been carried out in most papers. However, distance perception using fisheye cameras for surround view is relatively less studied. Due to large radial distortion, standard bounding box representation is difficult to implement in fisheye cameras. To alleviate the above description, we explore extended bounding box, ellipse, and general polygon designs into polar/angular representations and define an instance segmentation mIOU metric to analyze these representations. The proposed model fisheyeDetNet with polygonal shape outperforms other models and simultaneously achieves 49.5% mAP on the Valeo fisheye camera dataset for autonomous driving




