 Technology peripherals
Technology peripherals
 AI
AI
 Does the human brain work for AI? Give security guards a brain-computer interface to identify contraband with their eyes and automatically mark the results in 0.3 seconds
Does the human brain work for AI? Give security guards a brain-computer interface to identify contraband with their eyes and automatically mark the results in 0.3 seconds
Does the human brain work for AI? Give security guards a brain-computer interface to identify contraband with their eyes and automatically mark the results in 0.3 seconds
If you are a subway security checker and such an image flashes in front of your eyes three times per second, can you find that a gun is carried in one of the luggage?

Not that hard, right?
#However, the work in reality is not that simple. Seeing it at a glance is not enough. You also need to perform some subsequent operations, such as pressing the pause button or manually reporting. These tend to waste more time.
#At this time you may be thinking, can AI be used?
It is true that AI can now identify dangerous items quickly and accurately. However, even the most advanced AI cannot achieve 100% accuracy. , For some tasks that are not very important, AI may be able to complete it independently, but for important tasks such as security inspection, it can often only rely on manual inspection.
The human brain processes images very quickly. A security inspector with a little training can make a judgment in 0.3 seconds. What really wastes time is It is the operation after judgment.
#In this case, how about handing over this part of the work to AI?
For example, the brain of the security inspector is used as a machine, and brain-computer equipment is used to identify brain signals. When the security inspector sees dangerous items, the brain-computer equipment The signal is recognized and the image is quickly automatically marked.
This atypical AI seems to be a more practical AI.
Use brain signals to improve work efficiency, it doesn’t matter if your mind wanders
In an office in Herzliya, Sergey Vaisman Sit in front of a computer. He was relaxed but attentive, silent, motionless and completely undistracted by the brain-computer device he was wearing. On the computer screen, images appear and disappear rapidly, one after another.
Some of the images had just been tagged by Vaisman's brain, most of which were now revealed to have hidden guns, the process went without any pause, all tagged It is automatically labeled by brain-computer equipment, which greatly improves work efficiency.
Vaisman is the vice president of the R&D department of InnerEye, a newly established company in Israel. Unlike traditional AI companies that focus on replacing the brain with AI, This company is doing the opposite. Instead of replacing the brain, they "understand" it.
InnerEye identifies EEG signals as "targets" and "non-targets", which can be anything a trained human brain can recognize, In addition to developing safety screening, this includes detecting tumors in medical images, identifying diseased plants, discovering product defects, and more.
#For some simple cases, InnerEye found that our brains can process image recognition at a rate of 10 images per second. What's more, Weisman said the company's system produces results that are as accurate as when humans manually identify and label images, InnerEye simply uses EEG as a shortcut into the human brain to dramatically speed up the work.
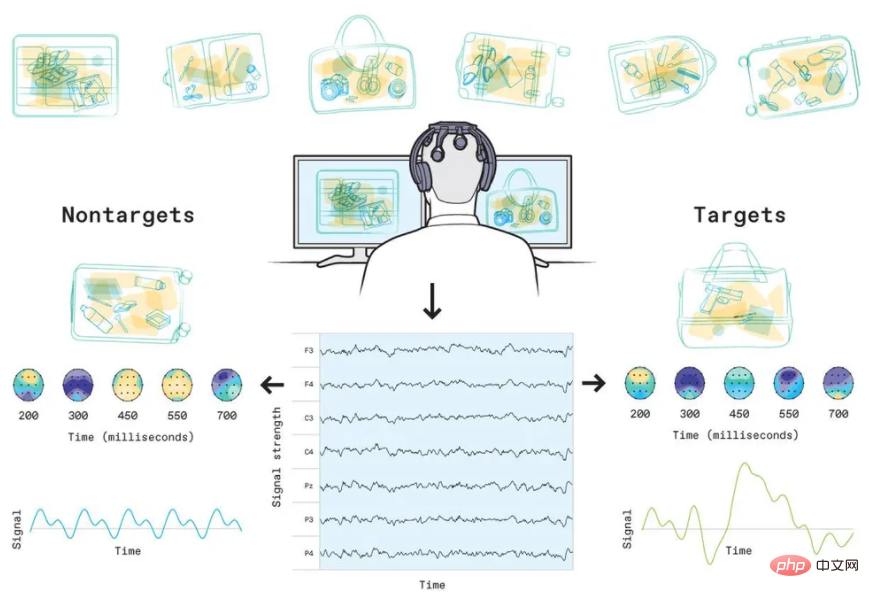
While InnerEye technology does not require active decision-making, it does require training and focus, and the user must be up to the task. experts who are highly trained in identifying specific types of targets, whether guns or tumors.
They also have to pay close attention to what they're seeing - they can't let their mind wander, but that's okay, InnerEye's system can measure focus very precisely, If the user blinks or momentarily stops concentrating, the system detects it and displays the missed image again.
Don’t compete with humans for jobs, give full play to humans’ advantages
People are always worried that the development of AI will gradually replace humans and cause the unemployment of human employees, but InnerEye explores a different path.
The human brain has a very obvious advantage over AI for classifying data, because the human brain can summarize and form new knowledge.
#For example, a trained AI image classifier might be able to determine with reasonable accuracy whether an X-ray image of a suitcase shows a gun, But if you want to tell whether this X-ray image shows something else suspicious, you need human experience, the human ability to detect something unusual, even if they don't entirely know what it is.
# "We can see this uncertainty in the brain waves," said Amir Geva, founder and chief technology officer of InnerEye. "We know when they're uncertain." Humans have a unique ability to recognize and contextualize novelty, which is a substantial advantage.
AmirGeva believes that we “need to combine human expertise with artificial intelligence.”
##This combination improves people's work efficiency and makes work easier.
In security screening, three pictures per second is roughly twice as fast as what experts can do manually, using this system allows for far fewer People are processing far more data, and InnerEye is currently working on pilot projects with a number of airports around the world.
The above is the detailed content of Does the human brain work for AI? Give security guards a brain-computer interface to identify contraband with their eyes and automatically mark the results in 0.3 seconds. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1379
1379
 52
52
 Debian mail server firewall configuration tips
Apr 13, 2025 am 11:42 AM
Debian mail server firewall configuration tips
Apr 13, 2025 am 11:42 AM
Configuring a Debian mail server's firewall is an important step in ensuring server security. The following are several commonly used firewall configuration methods, including the use of iptables and firewalld. Use iptables to configure firewall to install iptables (if not already installed): sudoapt-getupdatesudoapt-getinstalliptablesView current iptables rules: sudoiptables-L configuration
 How debian readdir integrates with other tools
Apr 13, 2025 am 09:42 AM
How debian readdir integrates with other tools
Apr 13, 2025 am 09:42 AM
The readdir function in the Debian system is a system call used to read directory contents and is often used in C programming. This article will explain how to integrate readdir with other tools to enhance its functionality. Method 1: Combining C language program and pipeline First, write a C program to call the readdir function and output the result: #include#include#include#includeintmain(intargc,char*argv[]){DIR*dir;structdirent*entry;if(argc!=2){
 How to implement file sorting by debian readdir
Apr 13, 2025 am 09:06 AM
How to implement file sorting by debian readdir
Apr 13, 2025 am 09:06 AM
In Debian systems, the readdir function is used to read directory contents, but the order in which it returns is not predefined. To sort files in a directory, you need to read all files first, and then sort them using the qsort function. The following code demonstrates how to sort directory files using readdir and qsort in Debian system: #include#include#include#include#include//Custom comparison function, used for qsortintcompare(constvoid*a,constvoid*b){returnstrcmp(*(
 Debian mail server SSL certificate installation method
Apr 13, 2025 am 11:39 AM
Debian mail server SSL certificate installation method
Apr 13, 2025 am 11:39 AM
The steps to install an SSL certificate on the Debian mail server are as follows: 1. Install the OpenSSL toolkit First, make sure that the OpenSSL toolkit is already installed on your system. If not installed, you can use the following command to install: sudoapt-getupdatesudoapt-getinstallopenssl2. Generate private key and certificate request Next, use OpenSSL to generate a 2048-bit RSA private key and a certificate request (CSR): openss
 How to perform digital signature verification with Debian OpenSSL
Apr 13, 2025 am 11:09 AM
How to perform digital signature verification with Debian OpenSSL
Apr 13, 2025 am 11:09 AM
Using OpenSSL for digital signature verification on Debian systems, you can follow these steps: Preparation to install OpenSSL: Make sure your Debian system has OpenSSL installed. If not installed, you can use the following command to install it: sudoaptupdatesudoaptininstallopenssl to obtain the public key: digital signature verification requires the signer's public key. Typically, the public key will be provided in the form of a file, such as public_key.pe
 How Debian OpenSSL prevents man-in-the-middle attacks
Apr 13, 2025 am 10:30 AM
How Debian OpenSSL prevents man-in-the-middle attacks
Apr 13, 2025 am 10:30 AM
In Debian systems, OpenSSL is an important library for encryption, decryption and certificate management. To prevent a man-in-the-middle attack (MITM), the following measures can be taken: Use HTTPS: Ensure that all network requests use the HTTPS protocol instead of HTTP. HTTPS uses TLS (Transport Layer Security Protocol) to encrypt communication data to ensure that the data is not stolen or tampered during transmission. Verify server certificate: Manually verify the server certificate on the client to ensure it is trustworthy. The server can be manually verified through the delegate method of URLSession
 How to do Debian Hadoop log management
Apr 13, 2025 am 10:45 AM
How to do Debian Hadoop log management
Apr 13, 2025 am 10:45 AM
Managing Hadoop logs on Debian, you can follow the following steps and best practices: Log Aggregation Enable log aggregation: Set yarn.log-aggregation-enable to true in the yarn-site.xml file to enable log aggregation. Configure log retention policy: Set yarn.log-aggregation.retain-seconds to define the retention time of the log, such as 172800 seconds (2 days). Specify log storage path: via yarn.n
 Centos shutdown command line
Apr 14, 2025 pm 09:12 PM
Centos shutdown command line
Apr 14, 2025 pm 09:12 PM
The CentOS shutdown command is shutdown, and the syntax is shutdown [Options] Time [Information]. Options include: -h Stop the system immediately; -P Turn off the power after shutdown; -r restart; -t Waiting time. Times can be specified as immediate (now), minutes ( minutes), or a specific time (hh:mm). Added information can be displayed in system messages.



