Gartner: China Artificial Intelligence Software Market Guide
Artificial intelligence (AI) software is the focus of investment and attention by Chinese companies. China's AI software market continues to grow rapidly and competition is fierce. AI software companies use one or more AI technologies (see Figure 1) to help companies interpret events, complete decision support and automation, and take corresponding actions. Solutions from these vendors can address the needs of part or the entire life cycle of the AI value chain, including ideation, use case discovery, data collection, data enhancement, AI development, as well as AI deployment, monitoring and calibration.
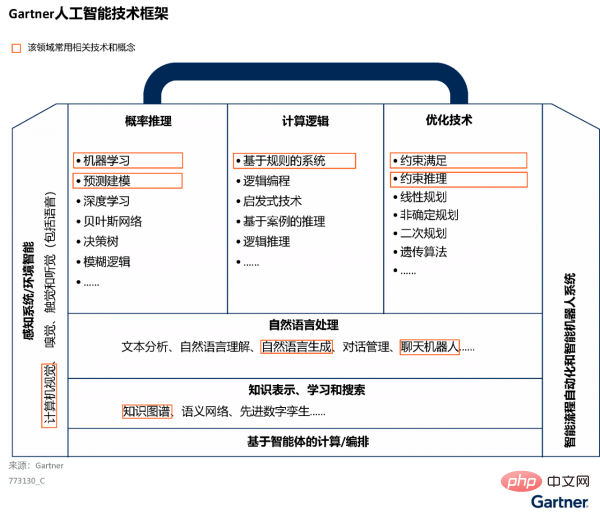
Figure 1: Gartner Artificial Intelligence Technology Framework
It can be seen from Figure 2 that the future of China’s AI software market is affected by three key forces:
- Relevant regulations
- Localization
- Enterprise needs
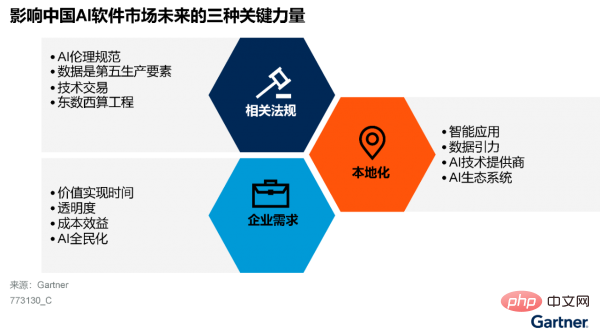
Figure 2: Impact on Chinese AI software Three key forces in the future of the market
Relevant regulations will promote the sustainable development of the market
AI has become a national strategy in China, and its purpose is to promote economic development and enhance social governance. Considering the regulatory environment, data privacy, AI ethics, and explainable AI are key to success. Relevant regulations will also promote changes in the entire AI industry to develop in a sustainable and healthier way.
A guideline set by the Chinese government states that data is the fifth factor of production after land, labor, capital and technology. To support national-level AI development plans, data and analytics leaders need to prioritize improving data exchange, data quality, and data governance, and accelerate the cultivation of data markets. For vendors focused on data integration, data annotation and annotation, this guideline means more opportunities along the AI value chain.
The Eastern Digital and Western Computational Project, officially launched in February 2022, will greatly improve the efficiency of computing power and meet the development needs of AI.
The demand for "localization" will promote the differentiation of the AI software market
A variety of segmented business applications have begun to embed AI functions, resulting in the development of two types of intelligent applications in the market. Among them, one type of smart applications comes from traditional domestic software manufacturers, and these manufacturers will benefit from localization. Another type of smart applications comes from manufacturers that focus on specific fields or vertical industries. As the degree of localization of used software increases, it is expected that more Chinese customers will use the above solutions in the future, and these solutions will gradually mature in various vertical industries.
Diverse enterprise needs will give rise to richer AI delivery methods
In the process of digital transformation, enterprise organizations gradually mature and need to use more data and background information to produce beneficial results. Drive decisions. More and more Chinese enterprises and institutions hope that AI investment can quickly create value. The increasingly complex business environment means that Chinese enterprises and institutions need to use a variety of traditional and advanced AI technologies to adjust their decision-making processes and gain competitive advantages.
China’s AI software market is growing rapidly and competition is fierce
China’s AI software market will continue to grow rapidly. Gartner predicts that the market's revenue will grow from US$4.767 billion to US$13.858 billion in the next five years, with a compound annual growth rate (CAGR) of 28%.
There are more than 3,000 manufacturers in China's AI software market, most of which are AI generalist manufacturers that can independently provide customers with natural language processing (NLP), computer vision (CV) and machine learning (ML). technology. These vendors provide end-to-end personalized enhancement services, consulting services and operational services to solve customers' specific business problems. As the market continues to expand, the number of Chinese AI software companies will also grow.
Market entities have changed from AI generalists to AI technology professional software providers
Figure 3 shows the changing trend of China’s AI software market: suppliers in this market used to be oriented to general needs, but now they are gradually transforming into Oriented to segmented needs.
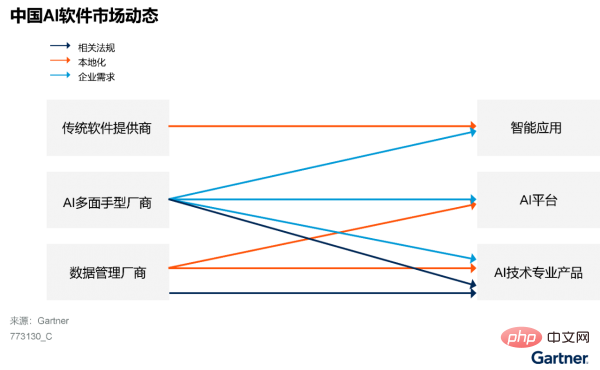
Figure 3: China’s AI software market changing trends
Data and analytics leaders need to transform the hotly-hyped “AI middle platform” concept into strategic solutions
Currently, The value of AI comes mostly from one-time point-to-point solutions. In the 2022 CIO and Technology Executive Survey, only 4% of Chinese respondents deployed MLOps.
Zhongtai is very popular, and different manufacturers use various definitions in marketing. "AI middle platform" is a concept that arises in the promotion of many solutions. China’s data and analytics leaders need to take a clear-eyed view of the AI middle platform and focus on reusable AI artifacts, including data, models and implementation pipelines, in experiments and operations.
The above is the detailed content of Gartner: China Artificial Intelligence Software Market Guide. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1378
1378
 52
52
 How to implement file sorting by debian readdir
Apr 13, 2025 am 09:06 AM
How to implement file sorting by debian readdir
Apr 13, 2025 am 09:06 AM
In Debian systems, the readdir function is used to read directory contents, but the order in which it returns is not predefined. To sort files in a directory, you need to read all files first, and then sort them using the qsort function. The following code demonstrates how to sort directory files using readdir and qsort in Debian system: #include#include#include#include#include//Custom comparison function, used for qsortintcompare(constvoid*a,constvoid*b){returnstrcmp(*(
 How to optimize the performance of debian readdir
Apr 13, 2025 am 08:48 AM
How to optimize the performance of debian readdir
Apr 13, 2025 am 08:48 AM
In Debian systems, readdir system calls are used to read directory contents. If its performance is not good, try the following optimization strategy: Simplify the number of directory files: Split large directories into multiple small directories as much as possible, reducing the number of items processed per readdir call. Enable directory content caching: build a cache mechanism, update the cache regularly or when directory content changes, and reduce frequent calls to readdir. Memory caches (such as Memcached or Redis) or local caches (such as files or databases) can be considered. Adopt efficient data structure: If you implement directory traversal by yourself, select more efficient data structures (such as hash tables instead of linear search) to store and access directory information
 How to set the Debian Apache log level
Apr 13, 2025 am 08:33 AM
How to set the Debian Apache log level
Apr 13, 2025 am 08:33 AM
This article describes how to adjust the logging level of the ApacheWeb server in the Debian system. By modifying the configuration file, you can control the verbose level of log information recorded by Apache. Method 1: Modify the main configuration file to locate the configuration file: The configuration file of Apache2.x is usually located in the /etc/apache2/ directory. The file name may be apache2.conf or httpd.conf, depending on your installation method. Edit configuration file: Open configuration file with root permissions using a text editor (such as nano): sudonano/etc/apache2/apache2.conf
 How debian readdir integrates with other tools
Apr 13, 2025 am 09:42 AM
How debian readdir integrates with other tools
Apr 13, 2025 am 09:42 AM
The readdir function in the Debian system is a system call used to read directory contents and is often used in C programming. This article will explain how to integrate readdir with other tools to enhance its functionality. Method 1: Combining C language program and pipeline First, write a C program to call the readdir function and output the result: #include#include#include#includeintmain(intargc,char*argv[]){DIR*dir;structdirent*entry;if(argc!=2){
 How Debian OpenSSL prevents man-in-the-middle attacks
Apr 13, 2025 am 10:30 AM
How Debian OpenSSL prevents man-in-the-middle attacks
Apr 13, 2025 am 10:30 AM
In Debian systems, OpenSSL is an important library for encryption, decryption and certificate management. To prevent a man-in-the-middle attack (MITM), the following measures can be taken: Use HTTPS: Ensure that all network requests use the HTTPS protocol instead of HTTP. HTTPS uses TLS (Transport Layer Security Protocol) to encrypt communication data to ensure that the data is not stolen or tampered during transmission. Verify server certificate: Manually verify the server certificate on the client to ensure it is trustworthy. The server can be manually verified through the delegate method of URLSession
 How to learn Debian syslog
Apr 13, 2025 am 11:51 AM
How to learn Debian syslog
Apr 13, 2025 am 11:51 AM
This guide will guide you to learn how to use Syslog in Debian systems. Syslog is a key service in Linux systems for logging system and application log messages. It helps administrators monitor and analyze system activity to quickly identify and resolve problems. 1. Basic knowledge of Syslog The core functions of Syslog include: centrally collecting and managing log messages; supporting multiple log output formats and target locations (such as files or networks); providing real-time log viewing and filtering functions. 2. Install and configure Syslog (using Rsyslog) The Debian system uses Rsyslog by default. You can install it with the following command: sudoaptupdatesud
 Debian mail server SSL certificate installation method
Apr 13, 2025 am 11:39 AM
Debian mail server SSL certificate installation method
Apr 13, 2025 am 11:39 AM
The steps to install an SSL certificate on the Debian mail server are as follows: 1. Install the OpenSSL toolkit First, make sure that the OpenSSL toolkit is already installed on your system. If not installed, you can use the following command to install: sudoapt-getupdatesudoapt-getinstallopenssl2. Generate private key and certificate request Next, use OpenSSL to generate a 2048-bit RSA private key and a certificate request (CSR): openss
 Debian mail server firewall configuration tips
Apr 13, 2025 am 11:42 AM
Debian mail server firewall configuration tips
Apr 13, 2025 am 11:42 AM
Configuring a Debian mail server's firewall is an important step in ensuring server security. The following are several commonly used firewall configuration methods, including the use of iptables and firewalld. Use iptables to configure firewall to install iptables (if not already installed): sudoapt-getupdatesudoapt-getinstalliptablesView current iptables rules: sudoiptables-L configuration




