 Technology peripherals
Technology peripherals
 AI
AI
 It's scary to think about it! PimEyes steals photos of dead people to train facial recognition algorithm
It's scary to think about it! PimEyes steals photos of dead people to train facial recognition algorithm
It's scary to think about it! PimEyes steals photos of dead people to train facial recognition algorithm
When you search for your own photos on PimEyes, you will see many photos of yourself and people who look like you.
However, when this tool trains the algorithm, it does not use photos authorized by the user, but based on photos from various platforms across the entire network to perform facial recognition.
So after your photo is recognized, the search results will often show screenshots of videos from many websites.
Not only that, but the website was also revealed to have been stealing photos of dead people to train algorithms.
Don’t spare the dead
Some people are dead, but they are still alive on the Internet.
Cher Scarlett is a software engineer and writer.
Recently, she suddenly discovered that photos of her mother, her great-great-grandmother who had passed away long ago, and her sister who passed away in 18 years all appeared on PimEyes.
All of these photos are pictures that she and her family uploaded to Ancestry themselves, but the site openly prohibits 「from Ancestry in its terms and conditions scrape data, including photos, from our websites and services and resell, copy or publish any content or information found on Ancestry.
## So Scarlett felt Shockingly, not only was this against Ancestry policy, but there was no way her deceased family would have allowed PimEyes to use these photos to train their algorithm.
This sounds similar to the story of Henrietta Lacks: 「 immortal HeLa cells」has been used for decades For medical research and drug development, it is one of the most important medical achievements in hundreds of years. But these studies were actually conducted after her death and without her permission. Without her knowledge, her cells were studied, reproduced, and even her genetic sequence was made public.

#Although these two things are not of the same magnitude. However, it is true that your privacy should be respected after your death.
Daniel Leufer, senior policy analyst at digital rights group Access Now, said: "Although PimEyes says it won't give you the person's identity directly through their website, But you can see the picture website with one click, and your name will indeed appear on the website.
『When I think of everyone photos will be entered into the biometric identifier of the facial recognition software without their knowledge or consent. I believe that no one will easily post photos on social media anymore. 」Scarlett feels Very disappointed.
『My sister is dead and she can’t come back to life to ask this website to take down her photos.』
Scarlett said this for a reason, because she had previously had issues with this website about withdrawing photos.
If you want to delete your nude photos, you can recharge $29.9 per monthWhen Scarlett first heard about this software, she wanted to test how it looked like her Who are the celebrities like.
She found herself somewhat similar to Britney Spears and Kate Hudson.
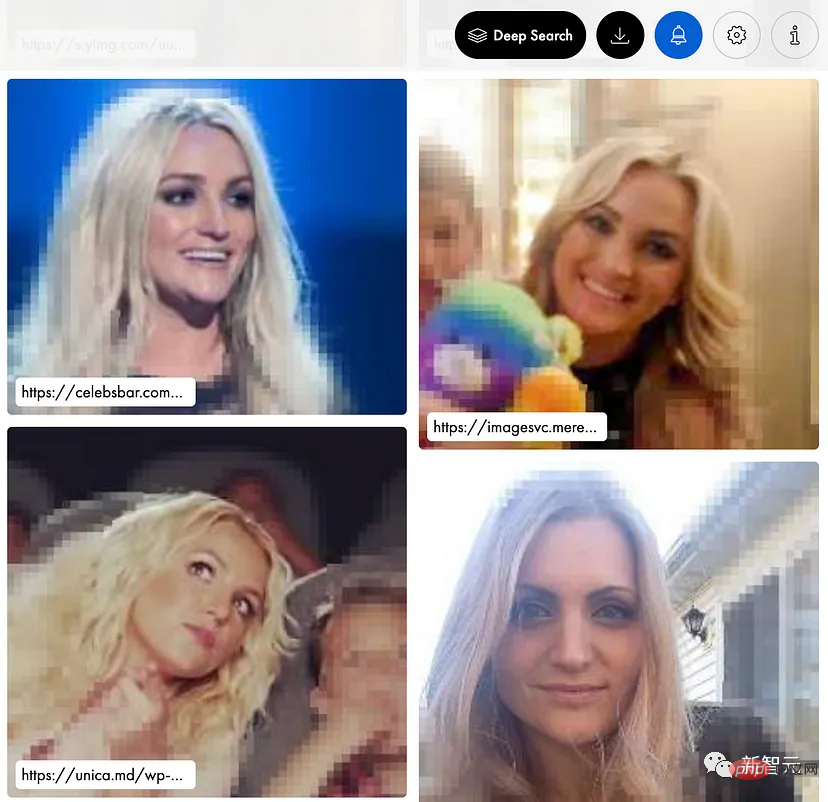
After flipping through the pages, she suddenly found a photo of herself being abused more than ten years ago.
This experience once made Scarlett want to commit suicide, so much so that her body's self-protection mechanism made her selectively forget this experience.
Suddenly seeing these photos on the website, she almost collapsed, but she forced herself to investigate the source of these photos and found that she needed to pay a membership fee to view them.
After paying, she found that the photos were scattered on various websites.
What’s even more terrible is that if you want to clear these photos, you not only have to submit an application to verify your identity, but you also have to recharge US$29.9 every month and subscribe to their service so that you can manage the search. As a result, some photos you don't want to be seen are hidden.
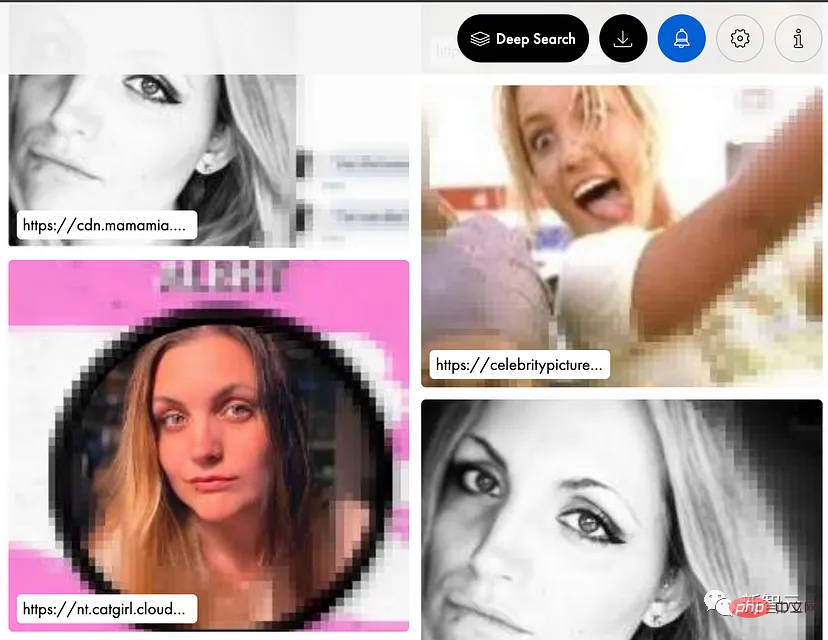
Scarlett has been trying to clear the photos, but there is no way to permanently remove them. She even bought PimEyes' most expensive service, but it didn't help. The website stated that as long as the photo subsequently appears in a link to other websites, it will still be displayed.
In other words, subscribing every month is not enough. You have to become a distinguished annual member and apply for cleanup regularly, and each approval takes a long time.
It wasn’t until April last year, when she shared her experience on social networks, that PimEyes actually approved her deletion request.
Investigate you, track you

PimEyes can find other photos they have published online from a person’s photos. Including pictures posted everywhere on websites, blogs, news, and articles.
By piecing together information related to these images, text from blogs and articles, and photos from your work website, someone who wants to investigate you can find out where you work and track you. your residence.
##『Images of anyone, including children, can be searched and tracked on the Internet.』
People who have been domestically abused or abused will lose their sense of security; stalkers will also quietly stalk you, just like in a horror movie; when applying for jobs or entering higher education, this tool can also be used to adjust Reveal all your background information so you have no secrets.
PimEyes has been accused of illegally processing the biometric data of millions of British citizens, arguing that it did not obtain the consent of those whose images were analyzed.
However, faced with accusations of breaching data protection laws, PimEyes argued that it was technically impossible to know how many British citizens’ faces they had analyzed, which amounted to an indirect admission. There is no authorization for this.
Although the platform claims that PimEyes is not designed to monitor others, the platform does not have relevant measures to supervise it, so people are also very dissatisfied with the platform's data security department. trust.

But PimEyes is working hard to reverse the criticism. They say the tool can help journalists with their investigations and say they are working with law enforcement and humanitarian organizations in Germany, Italy, the United Kingdom and the United States to help combat child crime, human trafficking and terrorism.
And, as mentioned above, after the matter was brought to light, PimEyes finally began to help women and began to approve and delete non-consensual nude pornographic photos, which can be regarded as Gain some virtue.
The above is the detailed content of It's scary to think about it! PimEyes steals photos of dead people to train facial recognition algorithm. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1387
1387
 52
52
 CLIP-BEVFormer: Explicitly supervise the BEVFormer structure to improve long-tail detection performance
Mar 26, 2024 pm 12:41 PM
CLIP-BEVFormer: Explicitly supervise the BEVFormer structure to improve long-tail detection performance
Mar 26, 2024 pm 12:41 PM
Written above & the author’s personal understanding: At present, in the entire autonomous driving system, the perception module plays a vital role. The autonomous vehicle driving on the road can only obtain accurate perception results through the perception module. The downstream regulation and control module in the autonomous driving system makes timely and correct judgments and behavioral decisions. Currently, cars with autonomous driving functions are usually equipped with a variety of data information sensors including surround-view camera sensors, lidar sensors, and millimeter-wave radar sensors to collect information in different modalities to achieve accurate perception tasks. The BEV perception algorithm based on pure vision is favored by the industry because of its low hardware cost and easy deployment, and its output results can be easily applied to various downstream tasks.
 Implementing Machine Learning Algorithms in C++: Common Challenges and Solutions
Jun 03, 2024 pm 01:25 PM
Implementing Machine Learning Algorithms in C++: Common Challenges and Solutions
Jun 03, 2024 pm 01:25 PM
Common challenges faced by machine learning algorithms in C++ include memory management, multi-threading, performance optimization, and maintainability. Solutions include using smart pointers, modern threading libraries, SIMD instructions and third-party libraries, as well as following coding style guidelines and using automation tools. Practical cases show how to use the Eigen library to implement linear regression algorithms, effectively manage memory and use high-performance matrix operations.
 How to solve the problem that Windows Hello face camera cannot be found in win11 facial recognition?
Mar 28, 2024 am 09:21 AM
How to solve the problem that Windows Hello face camera cannot be found in win11 facial recognition?
Mar 28, 2024 am 09:21 AM
When we use the win11 system, we have a function called windowshello face. This function is mainly used for face unlocking. However, many users are asking about the solution for win11 facial recognition and cannot find the windowshello face camera? Let this site carefully introduce to users the solution to the problem that Win11 facial recognition cannot find faces. How to solve the problem of Windows 11 facial recognition not being able to find Windows Shello face camera? Solution 1. Roll back the biometric driver 1. Open the device manager - biometric device - right click on Windows helloface software device properties > driver > roll back the driver
 Explore the underlying principles and algorithm selection of the C++sort function
Apr 02, 2024 pm 05:36 PM
Explore the underlying principles and algorithm selection of the C++sort function
Apr 02, 2024 pm 05:36 PM
The bottom layer of the C++sort function uses merge sort, its complexity is O(nlogn), and provides different sorting algorithm choices, including quick sort, heap sort and stable sort.
 How to solve the problem of facial recognition not working on Apple mobile phone
Mar 08, 2024 pm 06:28 PM
How to solve the problem of facial recognition not working on Apple mobile phone
Mar 08, 2024 pm 06:28 PM
Facial recognition on Apple phones doesn’t work. Users don’t have to worry if they encounter this situation. It’s not necessarily a problem with the device. You can try many methods to solve it. I’ll introduce it to you today. What should I do if the facial recognition on my Apple phone is not working? Solutions: 1. The FaceID function needs to ensure that there are no foreign objects blocking the face and that the face is unobstructed. Check that the front camera is not blocked. 2. Check the ambient lighting environment: When face recognition is performed, it is necessary to maintain sufficient ambient brightness and avoid interference from strong light sources. 3. Reset FaceID: Open the "Face & Password" option in "Settings" and click "Reset Face ID" to reset FaceID. 4. Upgrade the iOS version: If the iOS version running on the device is too old, it may affect Fac due to insufficient stability.
 Can artificial intelligence predict crime? Explore CrimeGPT's capabilities
Mar 22, 2024 pm 10:10 PM
Can artificial intelligence predict crime? Explore CrimeGPT's capabilities
Mar 22, 2024 pm 10:10 PM
The convergence of artificial intelligence (AI) and law enforcement opens up new possibilities for crime prevention and detection. The predictive capabilities of artificial intelligence are widely used in systems such as CrimeGPT (Crime Prediction Technology) to predict criminal activities. This article explores the potential of artificial intelligence in crime prediction, its current applications, the challenges it faces, and the possible ethical implications of the technology. Artificial Intelligence and Crime Prediction: The Basics CrimeGPT uses machine learning algorithms to analyze large data sets, identifying patterns that can predict where and when crimes are likely to occur. These data sets include historical crime statistics, demographic information, economic indicators, weather patterns, and more. By identifying trends that human analysts might miss, artificial intelligence can empower law enforcement agencies
 Improved detection algorithm: for target detection in high-resolution optical remote sensing images
Jun 06, 2024 pm 12:33 PM
Improved detection algorithm: for target detection in high-resolution optical remote sensing images
Jun 06, 2024 pm 12:33 PM
01 Outlook Summary Currently, it is difficult to achieve an appropriate balance between detection efficiency and detection results. We have developed an enhanced YOLOv5 algorithm for target detection in high-resolution optical remote sensing images, using multi-layer feature pyramids, multi-detection head strategies and hybrid attention modules to improve the effect of the target detection network in optical remote sensing images. According to the SIMD data set, the mAP of the new algorithm is 2.2% better than YOLOv5 and 8.48% better than YOLOX, achieving a better balance between detection results and speed. 02 Background & Motivation With the rapid development of remote sensing technology, high-resolution optical remote sensing images have been used to describe many objects on the earth’s surface, including aircraft, cars, buildings, etc. Object detection in the interpretation of remote sensing images
 Application of algorithms in the construction of 58 portrait platform
May 09, 2024 am 09:01 AM
Application of algorithms in the construction of 58 portrait platform
May 09, 2024 am 09:01 AM
1. Background of the Construction of 58 Portraits Platform First of all, I would like to share with you the background of the construction of the 58 Portrait Platform. 1. The traditional thinking of the traditional profiling platform is no longer enough. Building a user profiling platform relies on data warehouse modeling capabilities to integrate data from multiple business lines to build accurate user portraits; it also requires data mining to understand user behavior, interests and needs, and provide algorithms. side capabilities; finally, it also needs to have data platform capabilities to efficiently store, query and share user profile data and provide profile services. The main difference between a self-built business profiling platform and a middle-office profiling platform is that the self-built profiling platform serves a single business line and can be customized on demand; the mid-office platform serves multiple business lines, has complex modeling, and provides more general capabilities. 2.58 User portraits of the background of Zhongtai portrait construction



