How to use Jackson serialization to achieve data desensitization in Java
1. Background
Some sensitive information in the project cannot be displayed directly, such as customer mobile phone number, ID card, license plate number and other information. Data desensitization is required to prevent leakage of customer privacy. Desensitization means treating part of the data with desensitization symbols (*).
2. Goal
When the server returns data, use Jackson serialization to complete data desensitization and achieve desensitized display of sensitive information.
Reduce the amount of repeated development and improve development efficiency
Form unified and effective desensitization rules
It can be based on the desensitize method of overriding the default desensitization implementation to realize the desensitization requirements of scalable and customizable personalized business scenarios
3. Main implementation
3.1 Custom desensitized serialization implementation based on Jackson
StdSerializer: The base class used by all standard serializers. This is the recommended base for writing custom serializers. kind.
ContextualSerializer: is another serialization-related interface provided by Jackson. Its function is to customize JsonSerializer through the context information known by the field.
package com.jd.ccmp.ctm.constraints.serializer;
import com.fasterxml.jackson.core.JsonGenerator;
import com.fasterxml.jackson.databind.BeanProperty;
import com.fasterxml.jackson.databind.JsonSerializer;
import com.fasterxml.jackson.databind.SerializerProvider;
import com.fasterxml.jackson.databind.ser.ContextualSerializer;
import com.fasterxml.jackson.databind.ser.std.StdSerializer;
import com.jd.ccmp.ctm.constraints.Symbol;
import com.jd.ccmp.ctm.constraints.annotation.Desensitize;
import com.jd.ccmp.ctm.constraints.desensitization.Desensitization;
import com.jd.ccmp.ctm.constraints.desensitization.DesensitizationFactory;
import com.jd.ccmp.ctm.constraints.desensitization.DefaultDesensitization;
import java.io.IOException;
/**
* 脱敏序列化器
*
* @author zhangxiaoxu15
* @date 2022/2/8 11:10
*/
public class ObjectDesensitizeSerializer extends StdSerializer<Object> implements ContextualSerializer {
private static final long serialVersionUID = -7868746622368564541L;
private transient Desensitization<Object> desensitization;
protected ObjectDesensitizeSerializer() {
super(Object.class);
}
public Desensitization<Object> getDesensitization() {
return desensitization;
}
public void setDesensitization(Desensitization<Object> desensitization) {
this.desensitization = desensitization;
}
@Override
public JsonSerializer<Object> createContextual(SerializerProvider prov, BeanProperty property) {
//获取属性注解
Desensitize annotation = property.getAnnotation(Desensitize.class);
return createContextual(annotation.desensitization());
}
@SuppressWarnings("unchecked")
public JsonSerializer<Object> createContextual(Class<? extends Desensitization<?>> clazz) {
ObjectDesensitizeSerializer serializer = new ObjectDesensitizeSerializer();
if (clazz != DefaultDesensitization.class) {
serializer.setDesensitization((Desensitization<Object>) DesensitizationFactory.getDesensitization(clazz));
}
return serializer;
}
@Override
public void serialize(Object value, JsonGenerator gen, SerializerProvider provider) throws IOException {
Desensitization<Object> objectDesensitization = getDesensitization();
if (objectDesensitization != null) {
try {
gen.writeObject(objectDesensitization.desensitize(value));
} catch (Exception e) {
gen.writeObject(value);
}
} else if (value instanceof String) {
gen.writeString(Symbol.getSymbol(((String) value).length(), Symbol.STAR));
} else {
gen.writeObject(value);
}Note: createContextual can obtain the field type and annotations. When a field has a custom annotation, take the value in the annotation and create a customized serialization method, so that the value can be obtained in the serialize method. The createContextual method will only be called the first time a field is serialized (because the context information of the field will not change during runtime), so there is no need to worry about performance issues.
3.2 Define desensitization interface and factory implementation
3.2.1 Desensitization interface definition
package com.jd.ccmp.ctm.constraints.desensitization;
/**
* 脱敏器
*
* @author zhangxiaoxu15
* @date 2022/2/8 10:56
*/
public interface Desensitization<T> {
/**
* 脱敏实现
*
* @param target 脱敏对象
* @return 脱敏返回结果
*/
T desensitize(T target);
}3.2.2 Desensitization Device factory implementation
package com.jd.ccmp.ctm.constraints.desensitization;
import java.util.HashMap;
import java.util.Map;
/**
* 工厂方法
*
* @author zhangxiaoxu15
* @date 2022/2/8 10:58
*/
public class DesensitizationFactory {
private DesensitizationFactory() {
}
private static final Map<Class<?>, Desensitization<?>> map = new HashMap<>();
@SuppressWarnings("all")
public static Desensitization<?> getDesensitization(Class<?> clazz) {
if (clazz.isInterface()) {
throw new UnsupportedOperationException("desensitization is interface, what is expected is an implementation class !");
}
return map.computeIfAbsent(clazz, key -> {
try {
return (Desensitization<?>) clazz.newInstance();
} catch (InstantiationException | IllegalAccessException e) {
throw new UnsupportedOperationException(e.getMessage(), e);
}
});3.3 Commonly used desensitizer implementation
3.3.1Default desensitization implementation
can be based on the default implementation, Expand the implementation of personalized scenarios
package com.jd.ccmp.ctm.constraints.desensitization;
/**
* 默认脱敏实现
*
* @author zhangxiaoxu15
* @date 2022/2/8 11:01
*/
public interface DefaultDesensitization extends Desensitization<String> {
}3.3.2 Mobile phone number desensitizer
Achieve desensitization of the middle 4 digits of the mobile phone number
package com.jd.ccmp.ctm.constraints.desensitization;
import com.jd.ccmp.ctm.constraints.Symbol;
import java.util.regex.Matcher;
import java.util.regex.Pattern;
/**
* 手机号脱敏器,保留前3位和后4位
*
* @author zhangxiaoxu15
* @date 2022/2/8 11:02
*/
public class MobileNoDesensitization implements DefaultDesensitization {
/**
* 手机号正则
*/
private static final Pattern DEFAULT_PATTERN = Pattern.compile("(13[0-9]|14[579]|15[0-3,5-9]|16[6]|17[0135678]|18[0-9]|19[89])\d{8}");
@Override
public String desensitize(String target) {
Matcher matcher = DEFAULT_PATTERN.matcher(target);
while (matcher.find()) {
String group = matcher.group();
target = target.replace(group, group.substring(0, 3) + Symbol.getSymbol(4, Symbol.STAR) + group.substring(7, 11));
}
return target;3.4 Annotation definition
Implement custom annotations through @JacksonAnnotationsInside to improve ease of use
package com.jd.ccmp.ctm.constraints.annotation;
import com.fasterxml.jackson.annotation.JacksonAnnotationsInside;
import com.fasterxml.jackson.databind.annotation.JsonSerialize;
import com.jd.ccmp.ctm.constraints.desensitization.Desensitization;
import com.jd.ccmp.ctm.constraints.serializer.ObjectDesensitizeSerializer;
import java.lang.annotation.*;
/**
* 脱敏注解
*
* @author zhangxiaoxu15
* @date 2022/2/8 11:09
*/
@Target({ElementType.FIELD, ElementType.ANNOTATION_TYPE})
@Retention(RetentionPolicy.RUNTIME)
@JacksonAnnotationsInside
@JsonSerialize(using = ObjectDesensitizeSerializer.class)
@Documented
public @interface Desensitize {
/**
* 对象脱敏器实现
*/
@SuppressWarnings("all")
Class<? extends Desensitization<?>> desensitization();3.4.1 Default desensitization annotation
package com.jd.ccmp.ctm.constraints.annotation;
import com.fasterxml.jackson.annotation.JacksonAnnotationsInside;
import com.jd.ccmp.ctm.constraints.desensitization.DefaultDesensitization;
import java.lang.annotation.*;
/**
* 默认脱敏注解
*
* @author zhangxiaoxu15
* @date 2022/2/8 11:14
*/
@Target({ElementType.FIELD})
@Retention(RetentionPolicy.RUNTIME)
@JacksonAnnotationsInside
@Desensitize(desensitization = DefaultDesensitization.class)
@Documented
public @interface DefaultDesensitize {3.4.2 Mobile phone number desensitization annotation
package com.jd.ccmp.ctm.constraints.annotation;
import com.fasterxml.jackson.annotation.JacksonAnnotationsInside;
import com.jd.ccmp.ctm.constraints.desensitization.MobileNoDesensitization;
import java.lang.annotation.*;
/**
* 手机号脱敏
*
* @author zhangxiaoxu15
* @date 2022/2/8 11:18
*/
@Target({ElementType.FIELD})
@Retention(RetentionPolicy.RUNTIME)
@JacksonAnnotationsInside
@Desensitize(desensitization = MobileNoDesensitization.class)
@Documented
public @interface MobileNoDesensitize {
}3.5 Define desensitization symbols
supports specified desensitization symbols, such as * or ^_^
package com.jd.ccmp.ctm.constraints;
import java.util.stream.Collectors;
import java.util.stream.IntStream;
/**
* 脱敏符号
*
* @author zhangxiaoxu15
* @date 2022/2/8 10:53
*/
public class Symbol {
/**
* '*'脱敏符
*/
public static final String STAR = "*";
private Symbol() {}
/**
* 获取符号
*
* @param number 符号个数
* @param symbol 符号
*/
public static String getSymbol(int number, String symbol) {
return IntStream.range(0, number).mapToObj(i -> symbol).collect(Collectors.joining());
}4 .Usage sample & execution process analysis
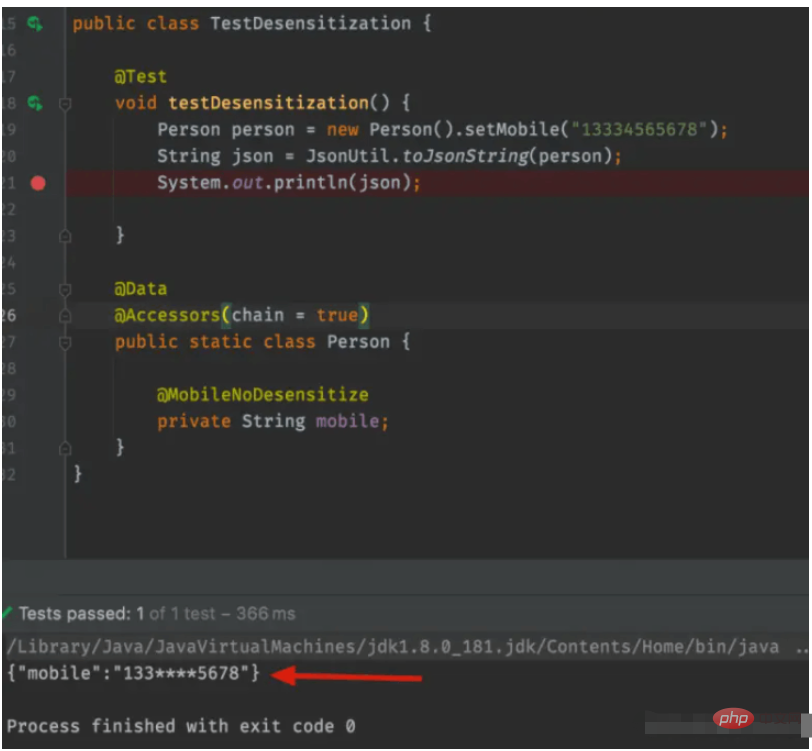
Program class diagram
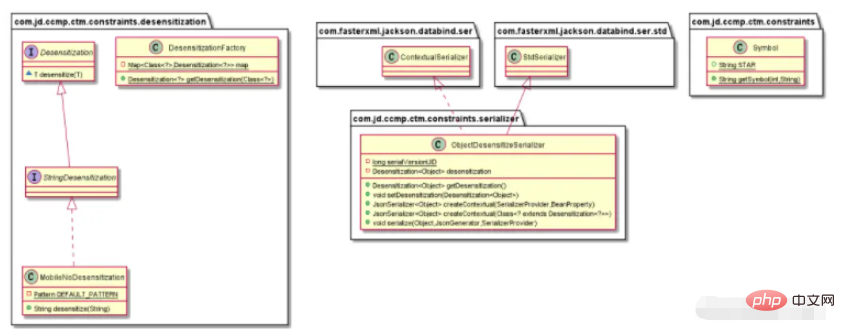
**Execution Process Analysis**
1. Call JsonUtil.toJsonString() to start serialization
2. Identify the annotation @MobileNoDesensitize (3.4.2 above) on the attribute mobile
3. Call ObjectDesensitizeSerializer#createContextual (3.1 & 3.2 above), return JsonSerializer
4. Call the mobile phone number to desensitize MobileNoDesensitization#desensitize (3.3.2 above)
5. Output The serialization result after desensitization, {"mobile":"133****5678"}
It is not difficult to find that the core execution process is step 3, but how are @MobileNoDesensitize and ObjectDesensitizeSerializer connected? Woolen cloth?
Try to sort out the reference link: @MobileNoDesensitize -> @Desensitize -> @JsonSerialize -> ObjectDesensitizeSerializer
However, in In the implementation of ObjectDesensitizeSerializer, we seem to have not found the direct calling relationship of the above link
This has to talk about the concept of Jackson meta-annotation
//**Jackson元注解**
//1.提到元注解这个词,大家会想到@Target、@Retention、@Documented、@Inherited
//2.Jackson也以同样的思路设计了@JacksonAnnotationsInside
/**
* Meta-annotation (annotations used on other annotations)
* used for indicating that instead of using target annotation
* (annotation annotated with this annotation),
* Jackson should use meta-annotations it has.
* This can be useful in creating "combo-annotations" by having
* a container annotation, which needs to be annotated with this
* annotation as well as all annotations it 'contains'.
*
* @since 2.0
*/
@Target({ElementType.ANNOTATION_TYPE})
@Retention(RetentionPolicy.RUNTIME)
@JacksonAnnotation
public @interface JacksonAnnotationsInside
{
}It is through the mechanism of "combo-annotations" (combined annotations, bundled annotations) that it is possible to instruct Jackson to use its own meta-annotations instead of using target annotations, thereby achieving custom desensitization to achieve design goals.
The above is the detailed content of How to use Jackson serialization to achieve data desensitization in Java. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1386
1386
 52
52
 Perfect Number in Java
Aug 30, 2024 pm 04:28 PM
Perfect Number in Java
Aug 30, 2024 pm 04:28 PM
Guide to Perfect Number in Java. Here we discuss the Definition, How to check Perfect number in Java?, examples with code implementation.
 Weka in Java
Aug 30, 2024 pm 04:28 PM
Weka in Java
Aug 30, 2024 pm 04:28 PM
Guide to Weka in Java. Here we discuss the Introduction, how to use weka java, the type of platform, and advantages with examples.
 Smith Number in Java
Aug 30, 2024 pm 04:28 PM
Smith Number in Java
Aug 30, 2024 pm 04:28 PM
Guide to Smith Number in Java. Here we discuss the Definition, How to check smith number in Java? example with code implementation.
 Java Spring Interview Questions
Aug 30, 2024 pm 04:29 PM
Java Spring Interview Questions
Aug 30, 2024 pm 04:29 PM
In this article, we have kept the most asked Java Spring Interview Questions with their detailed answers. So that you can crack the interview.
 Break or return from Java 8 stream forEach?
Feb 07, 2025 pm 12:09 PM
Break or return from Java 8 stream forEach?
Feb 07, 2025 pm 12:09 PM
Java 8 introduces the Stream API, providing a powerful and expressive way to process data collections. However, a common question when using Stream is: How to break or return from a forEach operation? Traditional loops allow for early interruption or return, but Stream's forEach method does not directly support this method. This article will explain the reasons and explore alternative methods for implementing premature termination in Stream processing systems. Further reading: Java Stream API improvements Understand Stream forEach The forEach method is a terminal operation that performs one operation on each element in the Stream. Its design intention is
 TimeStamp to Date in Java
Aug 30, 2024 pm 04:28 PM
TimeStamp to Date in Java
Aug 30, 2024 pm 04:28 PM
Guide to TimeStamp to Date in Java. Here we also discuss the introduction and how to convert timestamp to date in java along with examples.
 Java Program to Find the Volume of Capsule
Feb 07, 2025 am 11:37 AM
Java Program to Find the Volume of Capsule
Feb 07, 2025 am 11:37 AM
Capsules are three-dimensional geometric figures, composed of a cylinder and a hemisphere at both ends. The volume of the capsule can be calculated by adding the volume of the cylinder and the volume of the hemisphere at both ends. This tutorial will discuss how to calculate the volume of a given capsule in Java using different methods. Capsule volume formula The formula for capsule volume is as follows: Capsule volume = Cylindrical volume Volume Two hemisphere volume in, r: The radius of the hemisphere. h: The height of the cylinder (excluding the hemisphere). Example 1 enter Radius = 5 units Height = 10 units Output Volume = 1570.8 cubic units explain Calculate volume using formula: Volume = π × r2 × h (4
 Create the Future: Java Programming for Absolute Beginners
Oct 13, 2024 pm 01:32 PM
Create the Future: Java Programming for Absolute Beginners
Oct 13, 2024 pm 01:32 PM
Java is a popular programming language that can be learned by both beginners and experienced developers. This tutorial starts with basic concepts and progresses through advanced topics. After installing the Java Development Kit, you can practice programming by creating a simple "Hello, World!" program. After you understand the code, use the command prompt to compile and run the program, and "Hello, World!" will be output on the console. Learning Java starts your programming journey, and as your mastery deepens, you can create more complex applications.




