Python task automation tool tox tutorial

- Command line driven CI frontend and development task automation tool
- Command line driven CI frontend and development task automation tool
tox’s project address is: https://github.com/tox-dev/tox
Its core function is to support the creation of an isolated Python environment, in which it can be installed Different versions of Python interpreters and various dependent libraries make it easier for developers to do automated testing, packaging, continuous integration, etc.
Simply put, tox is a command line tool for managing test virtual environments. It has been around for many years and is widely used by developers. For example, the famous cloud computing platform OpenStack also uses it as one of the most basic testing tools.
1. What can tox do?
Segmented uses include:
- Create a development environment
- Run static code analysis and testing tools
- Automated building packages
- Run tests against tox-built packages
- Check whether the package can be successfully installed in different Python versions/interpreters
- Unify continuous integration (CI) and command line based testing
- Create and deploy project documentation
- Publish packages to PyPI or any other Platform
tox official documentation lists more than 40 examples of usage scenarios. The detailed list can be viewed at: https://tox.readthedocs.io/en/latest/examples. html
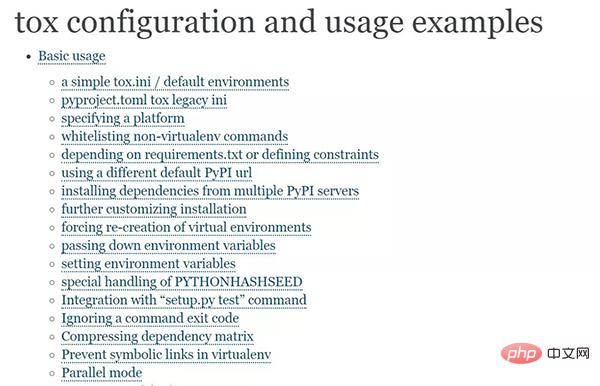
#2. How to configure tox?
About its usage: Use pip install tox to install, use tox to run all test environments, and tox -e envname to run the specified environment. There are also many command line parameters, which can be viewed through tox -h.
The behavior of tox is controlled by its configuration file. Currently it supports 3 configuration files:
- pyproject.toml
- tox.ini
- setup.cfg
Taking the tox project’s own tox.ini configuration content as an example, you can see that it is configured like this (https:// github.com/tox-dev/tox/blob/master/tox.ini):
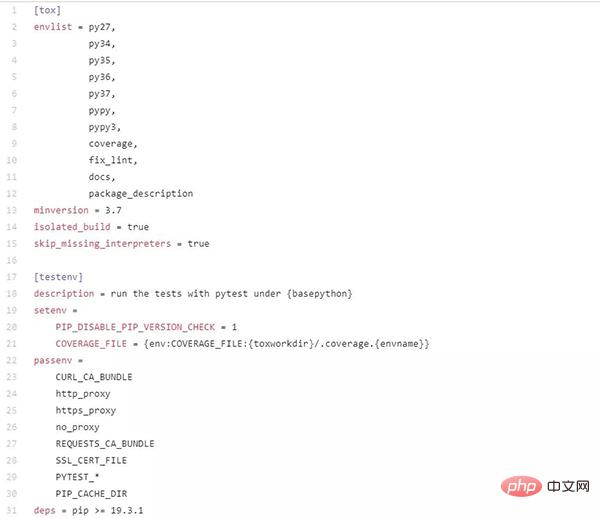
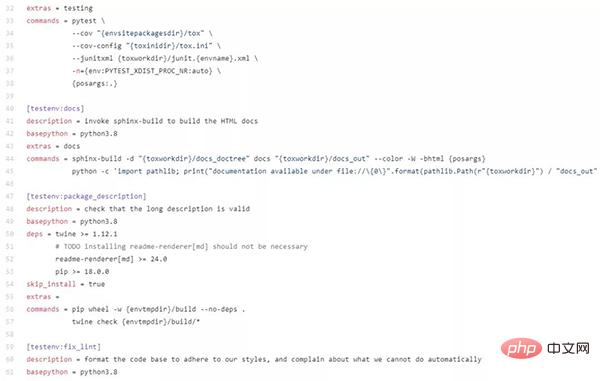
- Get the environment variable of the operating system: {env:KEY}, the effect is the same in os.environ['KEY']. Can be changed to: {env:KEY:DEFAULTVALUE}, the default value is used when the environment variable cannot be obtained; {env:KEY:{env:DEFAULT_OF_KEY}}, to achieve the value effect of if-else
-
- Values passed between chapters: {[sectionname]valuename}, the contents of different chapters can be passed and used.
[tox]
envlist = {py27,py36}-django{15,16}Using pip search tox, you can see a large number of libraries starting with "tox-", which are all plug-in packages of tox. Among them are well-known names such as setuptools, pipenv, conda, travis, pytest, and docker.
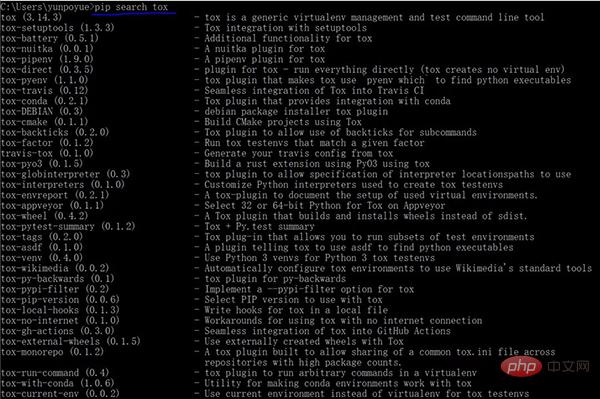
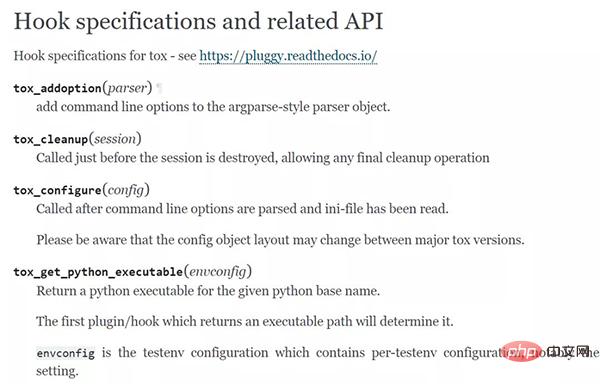
tox has opened a lot of API interfaces to facilitate others to customize and develop plug-ins.
4. The workflow of tox
Let’s take a look at how tox works:
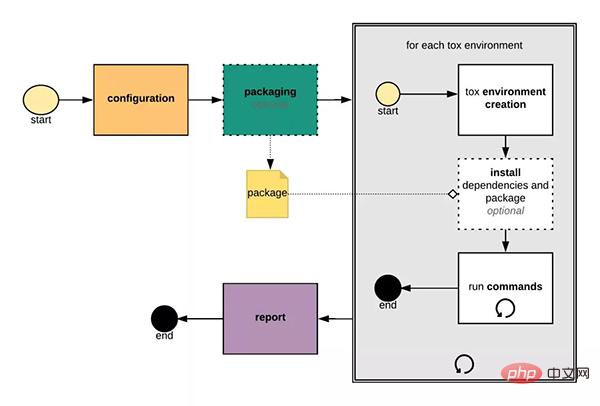
The main links in the workflow are:
- Configuration (from configuration): load the configuration file (such as tox.ini), parse the command Line parameters, read system environment variables, etc.
- Packaging: Optional, for projects with setup.py files, you can generate its source distribution in this step
- Create a virtual environment: Use virtualenv by default to create a virtual environment, install the required dependencies according to "deps" in the configuration item, and then execute the configured commands (commands)
- Report: Summarize the running results of all virtual environments and list them
5. Summary
tox itself is positioned as a testing tool, which tries to make Python testing becomes automated, standardized and streamlined. But unlike testing frameworks such as unittest and pytest, it works beyond the code level and is a project-level tool. Therefore, it needs to be combined with these testing frameworks, or handle multiple automated tasks at the same time (such as running pep8, testing code coverage, generating documentation, etc.), so that it can better exert its value.
One of its major features is the creation/management of virtual environments, but this is only used to facilitate testing, so compared with other tools that can manage virtual environments, such as Virtualenvwrapper, conda, pipenv, poetry, it has shortcomings in some aspects.
tox also has strong configurability and rich plug-in support, which gives it great possibility and freedom in application. Therefore, many loyal developers are still using it. For example, the author of the series of articles I just translated is one of its maintainers.
Finally, I need to add that tox uses configuration files as drivers, but the configuration files are still quite cumbersome, so someone developed a nox that is similar to tox. Use Python files for configuration. This project is also very popular, attracting many projects to invest under its umbrella, such as pipx, urllib3, Salt, etc. If you are interested in this project, please check out: https://nox.thea.codes/en/stable.
The above is the detailed content of Python task automation tool tox tutorial. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1378
1378
 52
52
 Python: Exploring Its Primary Applications
Apr 10, 2025 am 09:41 AM
Python: Exploring Its Primary Applications
Apr 10, 2025 am 09:41 AM
Python is widely used in the fields of web development, data science, machine learning, automation and scripting. 1) In web development, Django and Flask frameworks simplify the development process. 2) In the fields of data science and machine learning, NumPy, Pandas, Scikit-learn and TensorFlow libraries provide strong support. 3) In terms of automation and scripting, Python is suitable for tasks such as automated testing and system management.
 The 2-Hour Python Plan: A Realistic Approach
Apr 11, 2025 am 12:04 AM
The 2-Hour Python Plan: A Realistic Approach
Apr 11, 2025 am 12:04 AM
You can learn basic programming concepts and skills of Python within 2 hours. 1. Learn variables and data types, 2. Master control flow (conditional statements and loops), 3. Understand the definition and use of functions, 4. Quickly get started with Python programming through simple examples and code snippets.
 Navicat's method to view MongoDB database password
Apr 08, 2025 pm 09:39 PM
Navicat's method to view MongoDB database password
Apr 08, 2025 pm 09:39 PM
It is impossible to view MongoDB password directly through Navicat because it is stored as hash values. How to retrieve lost passwords: 1. Reset passwords; 2. Check configuration files (may contain hash values); 3. Check codes (may hardcode passwords).
 How to use AWS Glue crawler with Amazon Athena
Apr 09, 2025 pm 03:09 PM
How to use AWS Glue crawler with Amazon Athena
Apr 09, 2025 pm 03:09 PM
As a data professional, you need to process large amounts of data from various sources. This can pose challenges to data management and analysis. Fortunately, two AWS services can help: AWS Glue and Amazon Athena.
 How to start the server with redis
Apr 10, 2025 pm 08:12 PM
How to start the server with redis
Apr 10, 2025 pm 08:12 PM
The steps to start a Redis server include: Install Redis according to the operating system. Start the Redis service via redis-server (Linux/macOS) or redis-server.exe (Windows). Use the redis-cli ping (Linux/macOS) or redis-cli.exe ping (Windows) command to check the service status. Use a Redis client, such as redis-cli, Python, or Node.js, to access the server.
 How to read redis queue
Apr 10, 2025 pm 10:12 PM
How to read redis queue
Apr 10, 2025 pm 10:12 PM
To read a queue from Redis, you need to get the queue name, read the elements using the LPOP command, and process the empty queue. The specific steps are as follows: Get the queue name: name it with the prefix of "queue:" such as "queue:my-queue". Use the LPOP command: Eject the element from the head of the queue and return its value, such as LPOP queue:my-queue. Processing empty queues: If the queue is empty, LPOP returns nil, and you can check whether the queue exists before reading the element.
 How to view server version of Redis
Apr 10, 2025 pm 01:27 PM
How to view server version of Redis
Apr 10, 2025 pm 01:27 PM
Question: How to view the Redis server version? Use the command line tool redis-cli --version to view the version of the connected server. Use the INFO server command to view the server's internal version and need to parse and return information. In a cluster environment, check the version consistency of each node and can be automatically checked using scripts. Use scripts to automate viewing versions, such as connecting with Python scripts and printing version information.
 How secure is Navicat's password?
Apr 08, 2025 pm 09:24 PM
How secure is Navicat's password?
Apr 08, 2025 pm 09:24 PM
Navicat's password security relies on the combination of symmetric encryption, password strength and security measures. Specific measures include: using SSL connections (provided that the database server supports and correctly configures the certificate), regularly updating Navicat, using more secure methods (such as SSH tunnels), restricting access rights, and most importantly, never record passwords.




