How to detect Windows Tarrask malware using errors to avoid detection
Microsoft posted information about a new malware on its security website on April 12, 2022. The malware, dubbed Tarrask, exploits a vulnerability in the Windows task scheduling system to evade detection.
Tarrask is used by the hacking group Hafnium, which has targeted telecommunications, internet service providers and data services sectors in the past.
The group exploits zero-day vulnerabilities to attack computer systems. Once a system is successfully compromised, a vulnerability in Windows can be exploited to hide the malware's traces and make detection more difficult. Tarrask uses this bug to create hidden scheduled tasks to avoid detection and possibly for persistence.
Systems and applications use Windows Task Scheduler to initiate tasks, such as checking for updates or running maintenance operations. Applications can add tasks to Task Scheduler, provided they execute with sufficient permissions. According to Microsoft, malware often uses tasks to "maintain persistence in Windows environments."
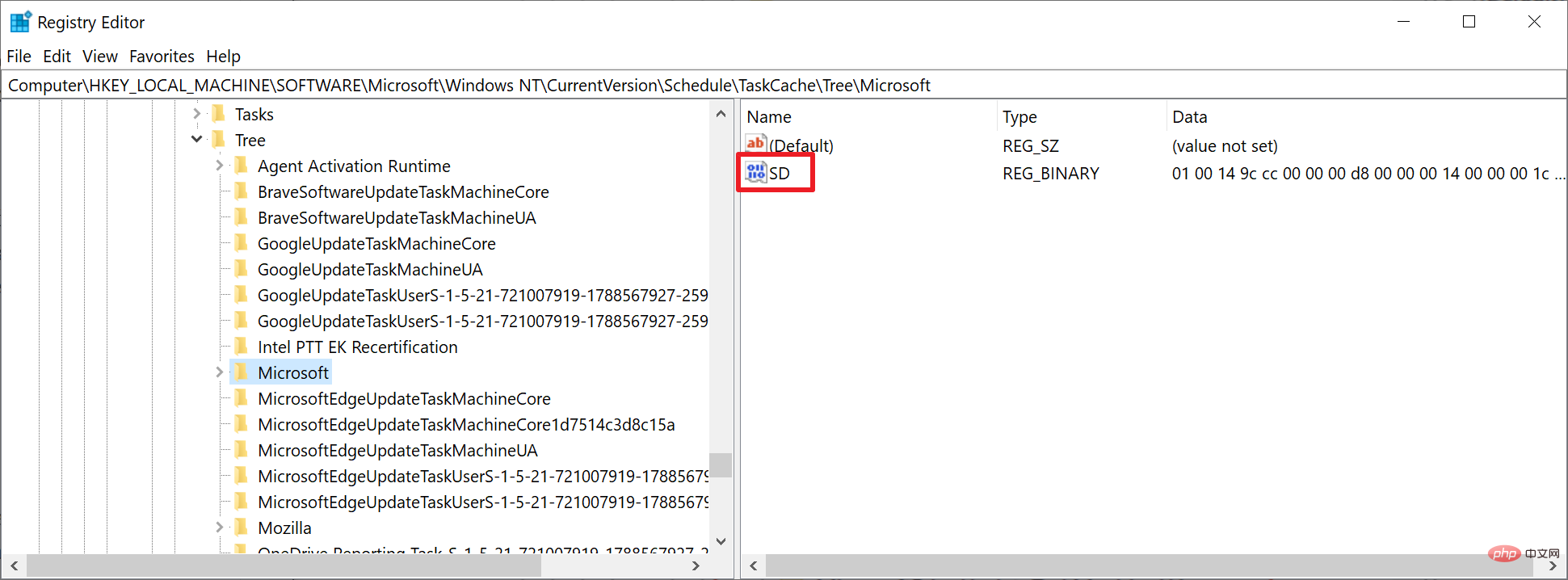
Tasks can be analyzed by launching the Task Scheduler tool on Windows. Tarrask uses an error to hide its tasks, and using the command line option "schtasks /query", it returns a list of existing scheduled tasks. To avoid detection, Tarrask deletes the task's security descriptor value in the Windows registry; this causes the task to disappear from Task Scheduler and command-line tools. In other words: A careful inspection of all tasks using either tool will not reveal a malicious task.
Detecting Tarrask on Windows systems
The malware does not completely delete task information as its traces are still recorded in the system registry. Microsoft suspects that the hacking group left data in the registry to allow the malware to persist, or that the group was unaware that the task would "keep running" after removing the SD component.
Windows administrators may analyze scheduled task information in the system registry to determine whether the system is infected with Tarrask malware:
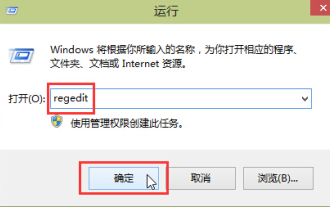
- Use the keyboard shortcut Windows-R to display the run box .
- Type regedit.exe and press Enter.
- Navigate to the path HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tree\. You will get a list of scheduled tasks present on your system.
- Loop through each task to determine if any tasks are listed without an SD value.
If a task is found without an SD value, it is a hidden task and will not show up in Task Scheduler or the command line utility. The task cannot be deleted normally because it is run in the context of the SYSTEM user. Attempts to delete the task will fail with an access denied error message.
The latest version of Microsoft's Windows Defender security application has detected malware. Microsoft has added a new watch event to Windows Defender for detecting hidden tasks; these are marked as Behavior:Win32/ScheduledTaskHide.A and then used by applications.
Microsoft recommends that system administrators adopt the following recommendations and security guidelines to detect malware using attack vectors:
Enumerate your Windows environment registry hives, view HKEY_LOCAL_MACHINE\SOFTWARE \Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tree registry hive and identifies any scheduled tasks that do not have an SD (security descriptor) value in the task key. Analyze these tasks as needed.
Modify your audit policy to identify scheduled task operations by enabling logging "TaskOperational" in Microsoft-Windows-TaskScheduler/Operational. Apply the recommended Microsoft audit policy settings appropriate for your environment.
Enable and centralize the following Task Scheduler logs. Even if tasks are "hidden", these logs will track key events related to them, which may lead you to discover well-hidden persistence mechanisms in the Security.evtx log Microsoft-Windows-TaskScheduler/Operational.evtx log
EventID 4698Threat actors in this campaign use hidden scheduled tasks to maintain access to critical assets exposed on the internet by regularly re-establishing outbound communications with the C&C infrastructure. Stay alert and monitor outbound communications for unusual behavior by ensuring these connections from these critical Tier 0 and Tier 1 assets are monitored and alerted.
The above is the detailed content of How to detect Windows Tarrask malware using errors to avoid detection. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1387
1387
 52
52
 What software is crystaldiskmark? -How to use crystaldiskmark?
Mar 18, 2024 pm 02:58 PM
What software is crystaldiskmark? -How to use crystaldiskmark?
Mar 18, 2024 pm 02:58 PM
CrystalDiskMark is a small HDD benchmark tool for hard drives that quickly measures sequential and random read/write speeds. Next, let the editor introduce CrystalDiskMark to you and how to use crystaldiskmark~ 1. Introduction to CrystalDiskMark CrystalDiskMark is a widely used disk performance testing tool used to evaluate the read and write speed and performance of mechanical hard drives and solid-state drives (SSD). Random I/O performance. It is a free Windows application and provides a user-friendly interface and various test modes to evaluate different aspects of hard drive performance and is widely used in hardware reviews
 What to do if WPS Office cannot open the PPT file - What to do if WPS Office cannot open the PPT file
Mar 04, 2024 am 11:40 AM
What to do if WPS Office cannot open the PPT file - What to do if WPS Office cannot open the PPT file
Mar 04, 2024 am 11:40 AM
Recently, many friends have asked me what to do if WPSOffice cannot open PPT files. Next, let us learn how to solve the problem of WPSOffice not being able to open PPT files. I hope it can help everyone. 1. First open WPSOffice and enter the homepage, as shown in the figure below. 2. Then enter the keyword "document repair" in the search bar above, and then click to open the document repair tool, as shown in the figure below. 3. Then import the PPT file for repair, as shown in the figure below.
 How to improve computer startup speed by modifying Windows 10 registry
Apr 19, 2024 am 08:01 AM
How to improve computer startup speed by modifying Windows 10 registry
Apr 19, 2024 am 08:01 AM
In the process of using the Windows 10 operating system, many users find that it takes a long time to start up their computers, which affects the user experience. In order to optimize the boot speed, some people have suggested that the purpose can be achieved by modifying the system registry. In response to this demand, this article will provide an in-depth analysis of how to effectively improve computer startup speed by properly adjusting Windows 10 registry settings. Let’s take a look below. Operation method 1. Use the "win+R" shortcut key to start running, enter "regedit", and click "OK" to open. 2. After entering the Registry Editor, click "HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurren" in the left column
 CrystalDiskinfo usage tutorial-What software is CrystalDiskinfo?
Mar 18, 2024 pm 04:50 PM
CrystalDiskinfo usage tutorial-What software is CrystalDiskinfo?
Mar 18, 2024 pm 04:50 PM
CrystalDiskInfo is a software used to check computer hardware devices. In this software, we can check our own computer hardware, such as reading speed, transmission mode, interface, etc.! So in addition to these functions, how to use CrystalDiskInfo and what exactly is CrystalDiskInfo? Let me sort it out for you! 1. The Origin of CrystalDiskInfo As one of the three major components of a computer host, a solid-state drive is the storage medium of a computer and is responsible for computer data storage. A good solid-state drive can speed up file reading and affect consumer experience. When consumers receive new devices, they can use third-party software or other SSDs to
 How to set the keyboard increment in Adobe Illustrator CS6 - How to set the keyboard increment in Adobe Illustrator CS6
Mar 04, 2024 pm 06:04 PM
How to set the keyboard increment in Adobe Illustrator CS6 - How to set the keyboard increment in Adobe Illustrator CS6
Mar 04, 2024 pm 06:04 PM
Many users are using the Adobe Illustrator CS6 software in their offices, so do you know how to set the keyboard increment in Adobe Illustrator CS6? Then, the editor will bring you the method of setting the keyboard increment in Adobe Illustrator CS6. Interested users can take a look below. Step 1: Start Adobe Illustrator CS6 software, as shown in the figure below. Step 2: In the menu bar, click the [Edit] → [Preferences] → [General] command in sequence. Step 3: The [Keyboard Increment] dialog box pops up, enter the required number in the [Keyboard Increment] text box, and finally click the [OK] button. Step 4: Use the shortcut key [Ctrl]
 What kind of software is bonjour? Is it useful?
Feb 22, 2024 pm 08:39 PM
What kind of software is bonjour? Is it useful?
Feb 22, 2024 pm 08:39 PM
Bonjour is a network protocol and software launched by Apple for discovering and configuring network services within a local area network. Its main role is to automatically discover and communicate between devices connected in the same network. Bonjour was first introduced in the MacOSX10.2 version in 2002, and is now installed and enabled by default in Apple's operating system. Since then, Apple has opened up Bonjour's technology to other manufacturers, so many other operating systems and devices can also support Bonjour.
 How to resolve an incompatible software attempt to load with Edge?
Mar 15, 2024 pm 01:34 PM
How to resolve an incompatible software attempt to load with Edge?
Mar 15, 2024 pm 01:34 PM
When we use the Edge browser, sometimes incompatible software attempts to be loaded together, so what is going on? Let this site carefully introduce to users how to solve the problem of trying to load incompatible software with Edge. How to solve an incompatible software trying to load with Edge Solution 1: Search IE in the start menu and access it directly with IE. Solution 2: Note: Modifying the registry may cause system failure, so operate with caution. Modify registry parameters. 1. Enter regedit during operation. 2. Find the path\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Micros
 What software is photoshopcs5? -photoshopcs5 usage tutorial
Mar 19, 2024 am 09:04 AM
What software is photoshopcs5? -photoshopcs5 usage tutorial
Mar 19, 2024 am 09:04 AM
PhotoshopCS is the abbreviation of Photoshop Creative Suite. It is a software produced by Adobe and is widely used in graphic design and image processing. As a novice learning PS, let me explain to you today what software photoshopcs5 is and how to use photoshopcs5. 1. What software is photoshop cs5? Adobe Photoshop CS5 Extended is ideal for professionals in film, video and multimedia fields, graphic and web designers who use 3D and animation, and professionals in engineering and scientific fields. Render a 3D image and merge it into a 2D composite image. Edit videos easily



